Let’s Configure SCCM Active Directory System Discovery. Once I have a post to build New ConfigMgr Primary Server, you can discover systems and users in your network.
Active directory system and user discovery are some of the first steps you perform to configure the new SCCM infrastructure. Once SCCM discovers all these users and systems, it can manage them and systems.
SCCM AD system discovery is a must for proper management of Windows 11 or Windows 10 devices using ConfigMgr. You can also create SCCM Collections based on the Active Directory OU using AD system discovery.
ConfigMgr Client Install – Install SCCM Client Manually Using Command Line
Related Post – Extend AD Schema for SCCM | ConfigMgr. More details “Learn How to Extend AD Schema for SCCM | ConfigMgr | MEMCM.”
What is SCCM Discovery?
In SCCM, you use one or more discovery methods to find device and user resources that you want to manage. Several methods exist for discovering users and resources from your network parameters. I recommend using Active Directory as your source for SCCM discovery.
SCCM discovery methods find different devices on your network, devices, and users from AD or users from Azure AD). I don’t recommend using network discovery. Heartbeat discovery is switched ON by default. I don’t recommend disabling heartbeat discovery.
Related Topic – ConfigMgr Client Action Discovery Data Collection Cycle
When an SCCM discovery method successfully finds information about a resource, it puts that information into a file called a discovery data record (DDR). A primary or CAS site then processes that file. Processing a DDR creates a new record in the site database for newly discovered resources or updates existing records with new information.
The SCCM server will check some prerequisites before creating DDR for each discovered object. One of them is a valid DNS record for the device object if it’s a device resource.
How to Configure SCCM Active Directory System Discovery
ConfigMgr discovery methods find different devices on your network, devices, and users from Active Directory or users from Azure Active Directory (Azure AD).
Use the AD System Discovery discovery method to search the specified Active Directory Domain Services locations for computer resources. Once the resources are discovered and created, a corresponding record is created in SCCM that can be used to create collections and queries.
NOTE! – You can also install the Configuration Manager client on a discovered device by using client push installation.
Configure Active Directory System Discovery
Let’s start the Configuration Manager discovery process to manage AD system records.
As part of AD system discovery, you must ensure that there is a valid DNS record for all the devices discovered from AD. Otherwise, SCCM won’t create device records for those discovered systems from AD.
Launch Configuration Manager Console. Navigate via \Administration\Overview\Hierarchy Configuration\Discovery Methods.
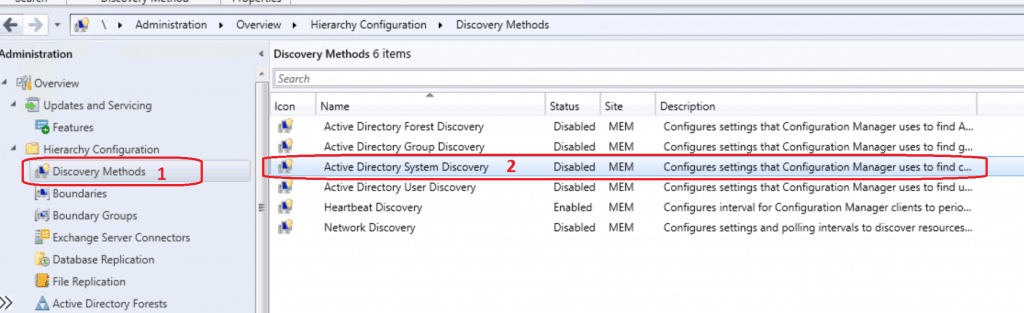
Right, Click on Active Directory System Discovery. Click on Properties.
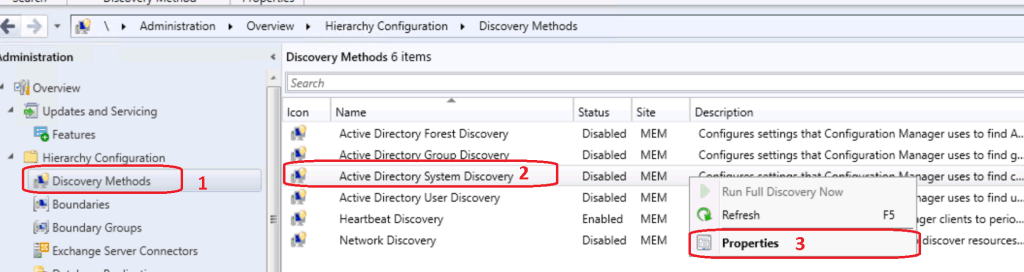
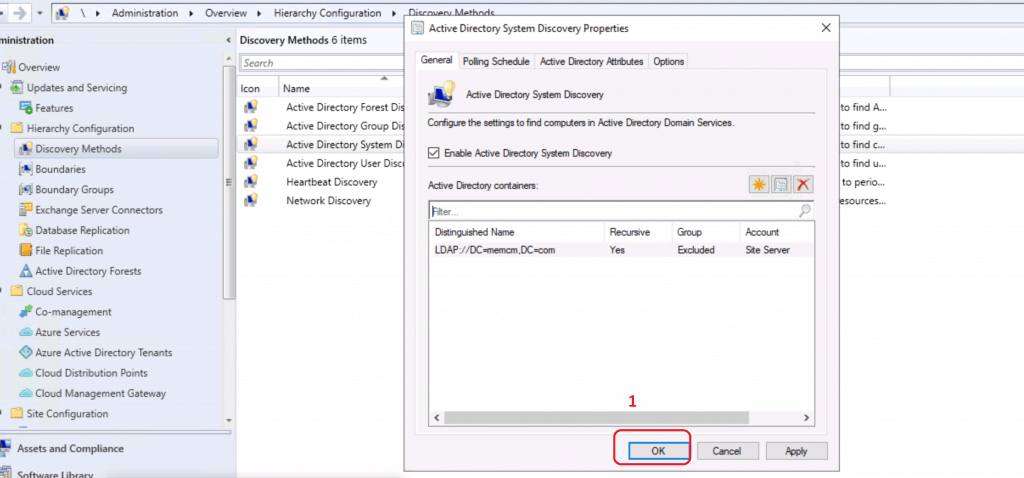
Enable Active Directory System Discovery. Click on the * button to select the Active Directory OU or discover the systems from all active directories.
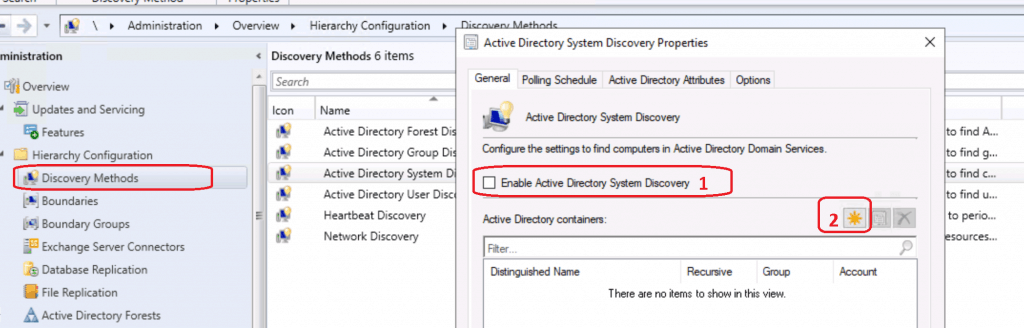
Click on BROWSE from Active Directory Container. Select the OU from where you want to discover the computer.
Select MEMCM and Click OK to discover all the computers in the Active directory for my test lab.
NOTE! For the production environment, I recommend selecting a particular OU rather than the entire Active Directory domain.
Click OK to continue.
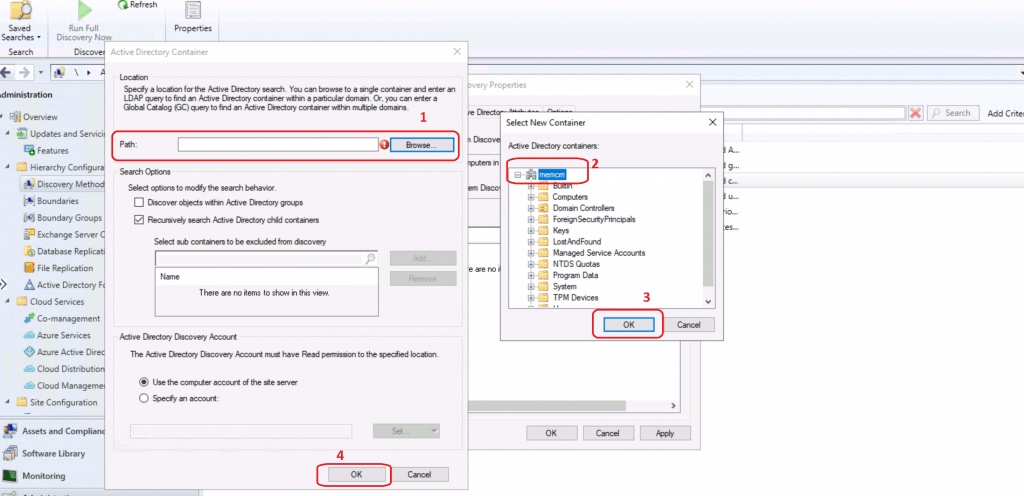
Click OK to continue to complete the SCCM configuration Active Directory System Discovery.
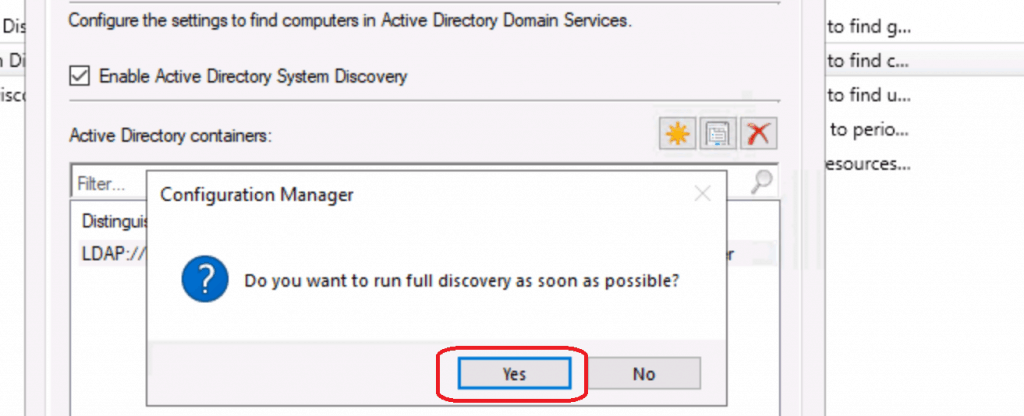
Select YES to continue with FULL discovery. “Do you want to run FULL discovery as soon as possible?”
Confirmation | Verification – Configure SCCM Active Directory System Discovery
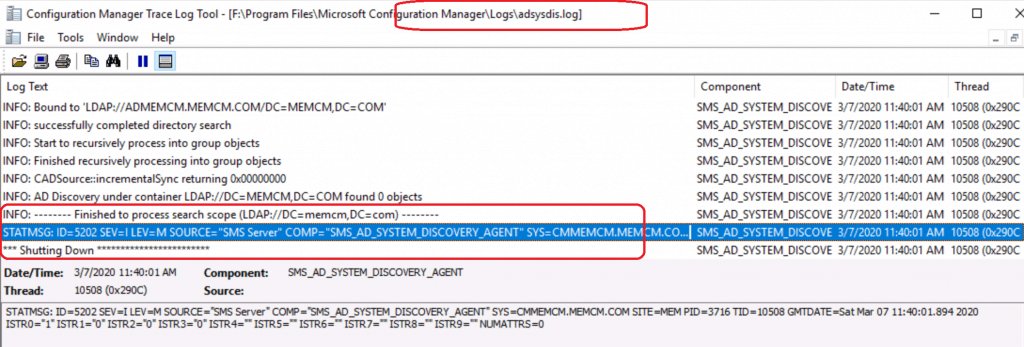
Let’s check the SCCM log file called ADSYSDIS.log to confirm whether configuring Active Directory system discovery works fine.
Some of the important steps are noted in the log file snippet below:
- Valid Search Scope Name: LDAP://DC=memcm,DC=com
- Starting the data discovery
- Full synchronization requested
- discovered object with ADsPath
- DDR was written for the system ‘ADMEMCM’
- successfully completed directory search~
SMS_EXECUTIVE started SMS_AD_SYSTEM_DISCOVERY_AGENT as thread ID 8144 (0x1FD0) ** Service Thread is starting **~ Connecting to site server's (\CMMEMCM.memcm.com) registry~ Inbox source is local on CMMEMCM.MEMCM.COM Component setting of ACTIVE was specified in the site control file.~ Removing redundant containers and validating them…~ INFO: No AD Containers Exclusions property list specified in site control file. The Run Count value in the site control file is 1.~ The Schedule token value in the site control file is 000120000010A000.~ Incremental synchronization is enabled.~ The Full Synchronization Schedule token value in the site control file is 0001170000100038.~ Filtering Last Logon Timestamp is disabled.~ Days of Logon Timestamp is 90.~ Filtering Last Password Set is disabled.~ Days of Last Password Set is 90.~ Optional attributes count = 0 !!!!Valid Search Scope Name: LDAP://DC=memcm,DC=com Search Path: LDAP://DC=MEMCM,DC=COM IsValidPath: TRUE Starting the data discovery.~ Connecting to site server's (\CMMEMCM.memcm.com) registry~ INFO: Succeed to clean up meta data in DB. INFO: -------- Starting to process search scope (LDAP://DC=memcm,DC=com) -------- INFO: Processing search path: 'LDAP://DC=MEMCM,DC=COM'.~ INFO: Full synchronization requested~ INFO: New DC DNS name = 'ADMEMCM.memcm.com'~ INFO: New highest committed USN = '55699'~ 0> INFO: New service object invocation Id = '3706bc8949381a48b752fcdd2b31454b'~ INFO: Search provider = 'LDAP'~ INFO: discovered object with ADsPath = 'LDAP://ADMEMCM.MEMCM.COM/CN=ADMEMCM,OU=Domain Controllers,DC=memcm,DC=com'~ INFO: DDR was written for system 'ADMEMCM' - F:\Program Files\Microsoft Configuration Manager\inboxes\auth\ddm.box\adse9mg1.DDR at 3/7/2020 11:29:30. INFO: discovered object with ADsPath = 'LDAP://ADMEMCM.MEMCM.COM/CN=SQLMEMCM,CN=Computers,DC=memcm,DC=com'~ $$<03-07-2020 11:29:30.889+00> INFO: successfully completed directory search~ INFO: -------- Finished to process search scope (LDAP://DC=memcm,DC=com) STATMSG: ID=5202 SEV=I LEV=M SOURCE="SMS Server" COMP="SMS_AD_SYSTEM_DISCOVERY_AGENT" SYS=CMMEMCM.MEMCM.COM SITE=MEM PID=3716 TID=8144 GMTDATE=Sat Mar 07 11:29:31.001 2020 ISTR0="1" ISTR1="5" ISTR2="5" ISTR3="0" ISTR4="" ISTR5="" ISTR6="" ISTR7="" ISTR8="" ISTR9="" NUMATTRS=0 *** Shutting Down **~
Results – Configure SCCM Active Directory System Discovery
Let’s check the console to see whether the System or Computer records are available under ALL SYSTEMS nodes.
Navigate to \Assets and Compliance\Overview\Devices\All Systems
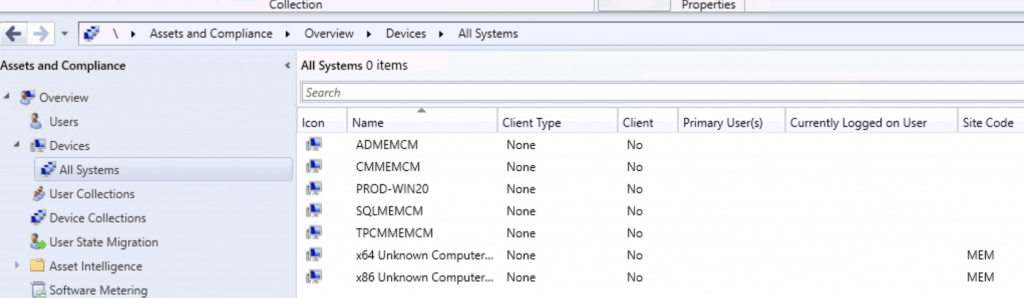
NOTE! – Now, the system or computer records there in SCCM DB, you can install ConfigMgr Client on these computer records. ConfigMgr Client Install – Install SCCM Client Manually Using Command Line
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here –HTMD WhatsApp.
Author
Anoop C Nair is Microsoft MVP! He is a Device Management Admin with more than 20 years of experience (calculation done in 2021) in IT. He is a Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc.

We recently may have had a password change. but for system discovery, we get this in the logs.
ISTR0=”LDAP://DC=AIIG,DC=LOCAL” ISTR1=”The user name or password is incorrect.~~” ISTR2=”” ISTR3=”” ISTR4=”” ISTR5=”” ISTR6=”” ISTR7=”” ISTR8=”” ISTR9=”” NUMATTRS=0 LE=0X0 $$
I am thinking the password had been changed by Thycotic. Is there a password for this I can update inside configuration manager or do we need to just ensure the correct password exists in AD. We are leveraging a service account to impersonate a user. Doesn’t appear to be permission related but rather AD account access. It’s the area where it says Active Directory Discovery Account, Specify an account.
Thank you.
If in case Ad domain is not connected to Sccm console how can i solve the issue
You just need to have read-only access and you will need to open the firewall ports to reach AD domain from SCCM servers.
Anoop – can LDAP 389 be disabled (b/c of vulnerabilities) and LDAPS 636 be used in it’s place for this?
Chris – As per the logs LDAP://DC=MEMCM,DC=COM always use LDAP. But if LDAP is not reachable I don’t know whether SCCM will try to use LDAPS or not. I never tested this scenario. So Ican’t confirm.
can i use my work or school AD account for azure AD setup how to setup that
Are you referring to the Manual Process for joining devices to Azure AD? https://www.anoopcnair.com/windows-11-azure-ad-join-manual-process-10/
Discover config
Hi,
I get this:
ERROR: directory search failed (0x8007202C)
INFO: CADSource::fullSync returning 0x8007202C
ERROR: Failed to enumerate directory objects in AD container LDAP://DC=HIDDEN,DC=HIDDEN,DC=HIDDEN
STATMSG […] ISTR1=”The server does not support the requested critical extension.~~” […]
Are there any permissions to check?
Any ideas?
Tnx in advance.
can we get this data in any sql table?
How to do you enable System discovery on Entra ID only joined computers (NOT Hybrid), we only see Entra ID users when we setup Cloud Attach within SCCM Console