In this blog post, I will explain how to Create an EPM Elevation Rules Policy from an Elevation Request with Microsoft Intune policy. My previous article described the Support Approved EPM Elevation Policy scenario for the VLC media player. Here, we can check how to create an EPM Elevation Rules Policy with the Elevation request we got from an existing Elevation settings policy.
In Microsoft Endpoint Privilege Management (EPM), the Elevation Rules Policy plays a critical role in managing how elevation requests are handled within an enterprise. Elevation Rules allow IT administrators to define the conditions under which standard users can temporarily elevate their permissions to perform specific tasks requiring administrative privileges.
Users who need elevated privileges to complete a task can submit an Elevation Request. This request is automatically evaluated against the predefined Elevation Rules Policy. The elevation can be automatically granted without manual intervention if the request matches the policy criteria, such as being a trusted app.
The Elevation Rules Policy facilitates flexibility for end-users and enhances security and compliance for organizations. Every elevation request is logged and monitored, providing a detailed audit trail for security teams. This audit capability ensures that any misuse or potential risks can be tracked and mitigated in real time.

Table of Contents
What is the EPM Elevation Rules Policy and Elevation Request Policy
In Microsoft Endpoint Privilege Management (EPM), the Elevation Rules Policy and Elevation Request Policy are two key components used to manage how users request and receive elevated privileges for specific tasks without requiring permanent admin rights on their devices. Here’s how they relate to each other:
These rules can be tailored to automatically approve trusted applications or processes, streamlining workflow while maintaining security controls. Elevation Rules are typically based on application paths, file hashes, publishers, and digital signatures to ensure only trusted or pre-approved applications are eligible for elevation.
| Elevation Rules Policy | Elevation Request Policy |
|---|---|
| This policy allows administrators to predefine rules that automatically elevate specific applications or tasks based on conditions such as file path, publisher, or hash. Elevation Rules are typically used to automatically grant admin privileges to applications without user intervention if they meet the set criteria. Use Case: An organization may want to allow a specific application (like a software installer or system update utility) to run with elevated privileges on all devices without Intune Admin approval every time. | The Elevation Request Policy allows users to request elevated privileges for tasks that fall outside predefined Elevation Rules. The requests are subject to approval by an admin, ensuring that users only get elevated privileges when absolutely necessary, and with oversight. Use Case: Users who need to run an application or process that isn’t covered by the automatic rules can request temporary elevation, and an administrator can approve or deny the request based on policy. |
- Easily Create New Intune EPM Rules directly from the Elevation Reports
- Easy Method to Hide Search on Windows 11 Taskbar Using Intune Policy Settings Catalog
- The Best Method to Enable Windows Passwordless Experience using Intune
Create an EPM Elevation Rules Policy from Elevation Request
Administrators can set time-based constraints for these policies, limiting how long elevated permissions are active and ensuring that the elevated rights are not misused beyond the intended task. By combining automation with strict oversight, EPM’s Elevation Rules Policy creates a balanced approach to privilege management, empowering users while safeguarding organizational resources. Here, we will check how to make an EPM Elevation Rules Policy from an existing Elevation Request.
This automated approval process significantly improves user productivity by minimizing delays while adhering to organizational security policies. For applications or tasks not covered by predefined rules, the request can enter a manual approval process where an administrator evaluates and grants or denies the elevation request.
Follow the steps below to create an EPM Elevation Rules Policy from Elevation Request from scratch. In this, I took an existing vlc-3.0.21-win64.exe elevation request as an example.
- Navigate to Endpoint Security> Manage > Endpoint Privilege Management > Click on Elevation Requests tab
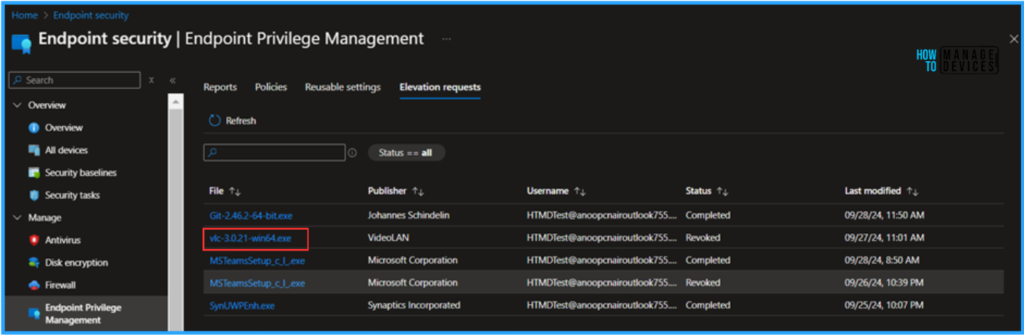
Click on the “vlc-3.0.21-win64.exe” hyperlink for the Elevation settings policy request, which we already got from one of our policy-targeted machines in our Tenant. This will pop up the Elevation request properties.
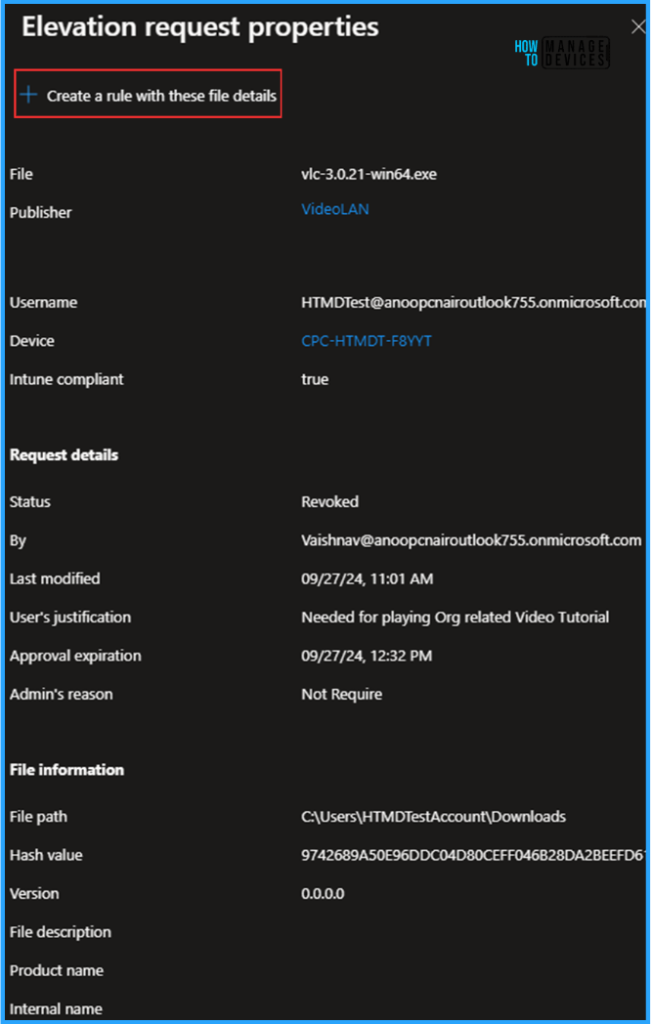
Click +Create a rule with these file details and Select Create a new policy. We can also add to an existing policy. For Type, we have two other options: Automatic and Support-approved. We can also see the Require rule to elevate and Deny all options for child process behaviour.
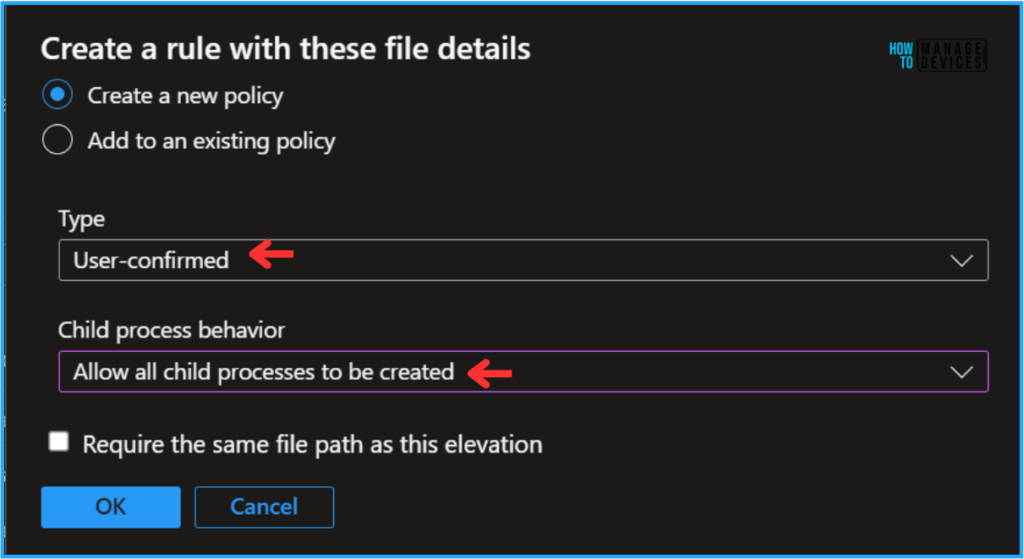
- Type – User-confirmed
- Child process behavior – Allow all child processes to be created
- Require the same file path as this elevation – Uncheck
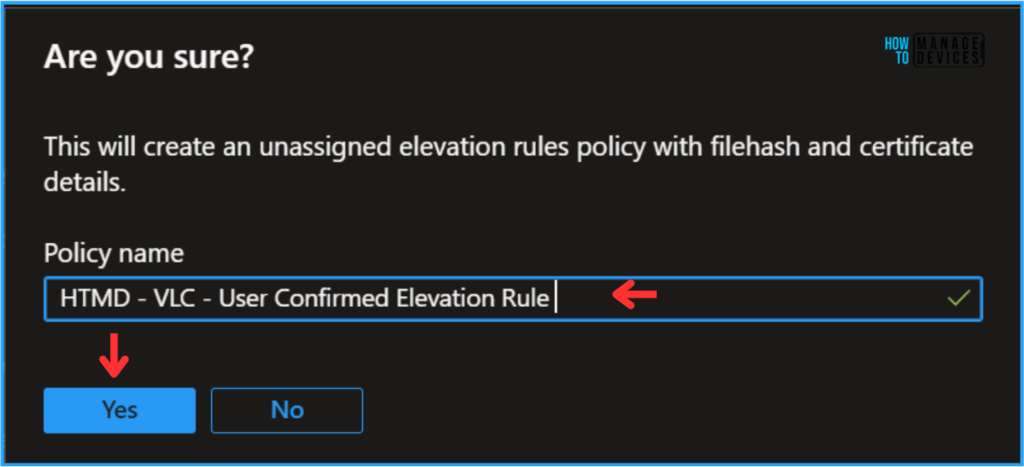
Click on OK and provide the policy name. Here, I am giving it as HTMD – VLC – User Confirmed Elevation Rule and select Yes. The Privilege Management Configuration settings will be defaulted based on our inputs.
- File hash – 9742689A50E96DDC04D80CEFF046B28DA2BEEFD617BE18166F8C5E715EC60C59
- Elevation type – User confirmed
- Validation – Not configured
- Signature source – Uploaded a certificate file
Note! Certificate Details —–BEGIN CERTIFICATE—– MIIHOzCCBSOgAwIBAgIQCdCOvaBr4HyBXqevJe9odTANBgkqhkiG9w0BAQsFADBpMQswCQYDVQQGEwJVUzEXMBUGA1UEChMORGlnaUNlcnQsIEluYy4xQTA/BgNVBAMTOERpZ2lDZXJ0IFRydXN0ZWQgRzQgQ29kZSBTaWduaW5nIFJTQTQwOTYgU0hBMzg0IDIwMjEgQ0ExMB4XDTI0MDYwNzAwMDAwMFoXDTI3MDYwODIzNTk1OVowQzELMAkGA1UEBhMCRlIxDjAMBgNVBAcTBVBhcmlzMREwDwYDVQQKEwhWaWRlb0xBTjERMA8GA1UEAxMIVmlkZW9MQU4wggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCj/5moFhYE5xPL0EIx7EjFMGri6d7pTpEDhEsqyanmqSenYG1vWpQtOasmK0iLE9uQFvg3EYUjqSJcJBdzSSk8u4bJFCntj1KMcM3ir/Re2ThMzpxsumr+1qbOaBMiieH4hi4/53cGyyJd5wsYvjzhr4ao8h6DbFcRyZBu6F42OgjCVIa+e3xCrIZRQjzbZMz0wd6KeqVFlDh+o1j0k6sMaw23QeiNAwJn8PNKpBNZBgO6NQf4VFJpi9PC58CPMPh1fcoy6zzXvD4nCQ3rB+I4jLcurb+z3Of/oFziizZqWp9kuK1L2Uf6Zq5REhffhd8wPqfw4tz6VUVjsZgu5Yl/P1qXLZCX0wioBO5FIC++xroQC+65oVTVfTcGm8cw65liC3twdu15t+WZb0xiJy2SfGy1axQdWFOPKdf3zS81U7o4c7HkMWg6i87JLjYprs1cj2S1L+q51y5yxZPsnBO8NfrTB2ftWtzQbUiMk2L8SzbjVqilr1eOKr1z9S94mP9HHXv4l8K8mjSNeubiAyv0M/kSO4c00kT6Yrbmg+zBJyPPnRH3WeBH4QKxNn9DP44oGtzU9GREL4yGJjMGOJ7Fg+UQR056U0z56soTwHKKcZCHYYV2cgMovhkPYqahFs3IeoZOp6dB10/mjdPPrq4Y2baVgs2sqbpOB1ayOut6BwIDAQABo4ICAzCCAf8wHwYDVR0jBBgwFoAUaDfg67Y7+F8Rhvv+YXsIiGX0TkIwHQYDVR0OBBYEFNT0ws2jlrR9TnmSlBYB8o7rxrfRMD4GA1UdIAQ3MDUwMwYGZ4EMAQQBMCkwJwYIKwYBBQUHAgEWG2h0dHA6Ly93d3cuZGlnaWNlcnQuY29tL0NQUzAOBgNVHQ8BAf8EBAMCB4AwEwYDVR0lBAwwCgYIKwYBBQUHAwMwgbUGA1UdHwSBrTCBqjBToFGgT4ZNaHR0cDovL2NybDMuZGlnaWNlcnQuY29tL0RpZ2lDZXJ0VHJ1c3RlZEc0Q29kZVNpZ25pbmdSU0E0MDk2U0hBMzg0MjAyMUNBMS5jcmwwU6BRoE+GTWh0dHA6Ly9jcmw0LmRpZ2ljZXJ0LmNvbS9EaWdpQ2VydFRydXN0ZWRHNENvZGVTaWduaW5nUlNBNDA5NlNIQTM4NDIwMjFDQTEuY3JsMIGUBggrBgEFBQcBAQSBhzCBhDAkBggrBgEFBQcwAYYYaHR0cDovL29jc3AuZGlnaWNlcnQuY29tMFwGCCsGAQUFBzAChlBodHRwOi8vY2FjZXJ0cy5kaWdpY2VydC5jb20vRGlnaUNlcnRUcnVzdGVkRzRDb2RlU2lnbmluZ1JTQTQwOTZTSEEzODQyMDIxQ0ExLmNydDAJBgNVHRMEAjAAMA0GCSqGSIb3DQEBCwUAA4ICAQCCrCoO7GE9BxlhmaAqK2QtkruOBVnc8OpiZglKhVAJ5rT5pSuuZqrxE8SYIqnlcM0tOVl02cgxkEndmfhbValO+nnvswHJXORqF0Jq1zn3ImPw4G0KULUPHjRESxLS7kMJE6uGnpPJ91aOjQphG76vswgc1b6VsqkEpK3GmRWzgdPijUVG8MYCu/SO72/UYaGm8ggCvT8eI50c71uYYqXLs3jSjuYfiobO0WRWkz7YAkx3+wWyW+3R5pc6ayXk0I9E1QByglVchUtUwMvID94v1QTvOYoKo/w6ihsa+5+egn4PVitqQh9n0DpDfMrBLmHx52rKYgo5Z24m2qlM8dmSyTQjffvj5+UgyHfO0N4GqNlvsDeNJ8Uy2hMR830GGDe5h4gNQJ5oyMG3Nl7x6SPGadrp6kuUvxnhXxUeox8KnKiZc74C+9p1N1pIlRjfam/Cl0H53vZ+4bic4SI/4XCM71DEW/A9W9b9Ztv5AMwblQFcuvfq6QAagtlp3+AiE2uSXGdr2UPRzkUtuXghgTG57Y/jP5Lko8JxMedFcb8GXSyGOjcysk2JEAT8/R2JWALRTqzgsoy1cukhB33o7P9HxYd3IgLi0VPO+ctb/PTGkDwYSvhhY8/61tJmMgcB3x5oUvJq+1trQSDrAmRSu59taieLKTAHbhNBaXg1RnVFng== —–END CERTIFICATE—–
- Certificate type – Publisher
- File upload – Certificate Uploaded
- Child process behavior – Allow all child processes to run elevated
- Rule name – vlc-3.0.21-win64.exe rule
- File name – vlc-3.0.21-win64.exe
Our EPM Elevation Rules policy has been created based on VLC file elevation. Please verify its successful creation using the path below.
- Navigate to Endpoint Security > Endpoint Privilege Management > Policies > HTMD – VLC – User Confirmed Elevation Rule.
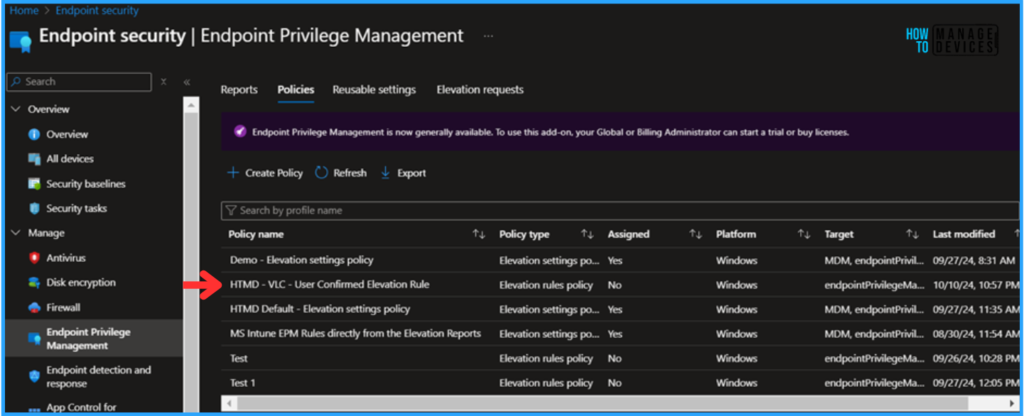
The newly created Elevation rules policy is not assigned to any groups. Now Select the policy, go to the Assignments section, and Target it to one of the Entra ID groups. I am choosing HTMD – Test Computers Device Group and clicking the Review+Save option. The policy is successfully targeted now.
- Intune EPM Support Approve Scenario Explained
- 7-Zip Update with Enterprise App Catalog App in Intune Best Step-by-Step Guide
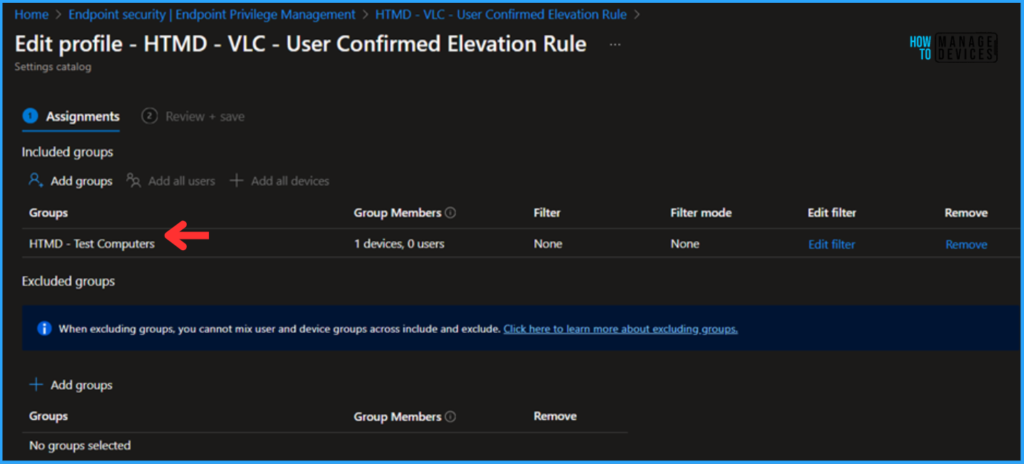
Monitor the EPM Elevation Rules Policy from Elevation Request Policy Deployment
The HTMD – VLC – User Confirmed Elevation Rule Policy has been deployed to the Microsoft Entra ID group. It will take effect as soon as the device is synced.
To monitor the policy deployment status from the Intune Portal, follow the steps below.
- Navigate to Endpoint Security> Manage > Endpoint Privilege Management > Policies.
Search for the HTMD – VLC – User Confirmed Elevation Rule, EPM Elevation Rules Policy from Elevation Request. Click on that to see our policy’s Endpoint check-in status. Selecting View Report allows you to drill through the deployment, device name, logged user, check-in status, etc.
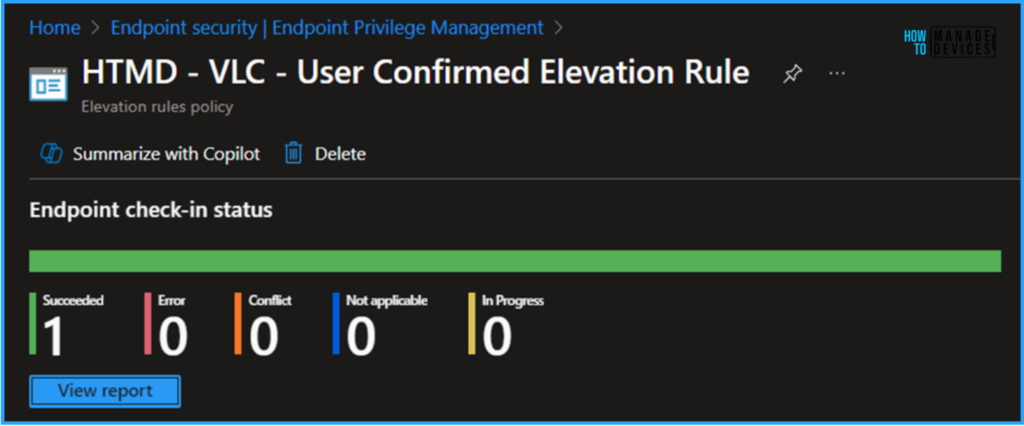
End User Experience – EPM Elevation Rules Policy from Elevation Request
Now, we have to check whether the EPM Elevation Rules Policy is working fine or not. Log in to one of the policy-targeted devices. In this example, I just downloaded and kept vlc-3.0.21-win64.exe and tried to install the VLC Player for a non-admin user. Follow the below steps.
- Right-click on the vlc-3.0.21-win64.exe file and “Run with elevated access. “
- Just Enter a Business justification and Click on Continue
- Currently, you’ll have administrator access to install this app
So, from now on, the non-admin user will have admin rights to install the vlc-3.0.21-win64 application!
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Vaishnav K has over 11 years of experience in SCCM, Device Management, and Automation Solutions. He writes and imparts knowledge about Microsoft Intune, Azure, PowerShell scripting, and automation. Check out his profile on LinkedIn.


