Hi, I will discuss how to Block Google Chrome Extensions using the Intune Configuration policy. The present discourse aims to elucidate the process of disallowing the installation of Google Chrome extensions via the Intune Policy. Chrome extensions are software applications developed utilizing web technologies such as HTML, CSS, and JavaScript, which offer users the ability to personalize their browsing experiences in Chrome.
Extensions are software components that can be added to your browser to provide additional functionalities such as note-taking, password management, ad-blocking, and more. However, it’s important to note that extensions can also pose security risks to your browser and computer. So, it’s recommended only to install extensions from reputable sources and to review and remove any unnecessary or unused extensions regularly.
In order to maintain a secure and controlled environment, it is recommended to implement a policy that restricts the installation of extensions to only those that have been approved by the administrator. This approach ensures that the organization’s systems are protected from potential security threats that may arise from the installation of unauthorized extensions.
By limiting the installation of extensions, the administrator can ensure that the organization’s systems remain stable and free from any potential conflicts that may arise from the installation of incompatible extensions. Therefore, it is advisable to adopt a policy that blocks all extension installations and only allows specific extensions that have been approved by the administrator.
What can Browser Extensions do?
Extensions are incredibly versatile and can perform a wide range of functions. They can help you encrypt your emails, block ads, store passwords with a single click, check your spelling, and much more. Think of extensions as specialized assistants that work with the information flowing through your browser. They can help you organize your notes, protect you from hackers, or even change the appearance of the browser window, such as adding Grammarly.

It is essential to bear in mind that browser extensions typically necessitate extensive permissions to function optimally. Certain extensions may even require access to nearly all facets of your browser interaction, ranging from the websites you visit to your keystrokes and passwords. These permissions can present significant risks to your privacy and security, particularly in the event that you unwittingly install a malicious extension or operate a poorly secured browser.
It is of utmost importance to exercise prudence and caution when installing and employing browser extensions, as they may introduce serious privacy and security concerns if not carefully scrutinized and monitored.
- Check the best way to Manage Microsoft Edge Extensions using Intune.
How to Block Google Chrome Extensions using Intune
In this guide, we will see the easiest method for blocking automatic downloads on Microsoft Edge using configuration profiles in Intune.
- Sign in to the Microsoft Intune Admin portal.
- Select Devices > Windows > Configuration Profiles
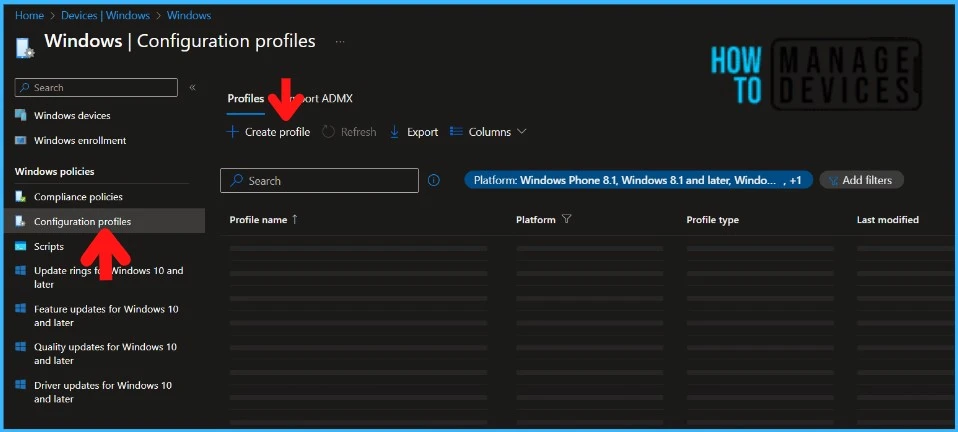
You will open a new window when you click Create Profile. Select Windows 10 and later in Platform, Select Profile Type as Templates
| Platform | Profile Type |
|---|---|
| Windows 10 and later | Templates |
Select Administrative Templates and click on Create
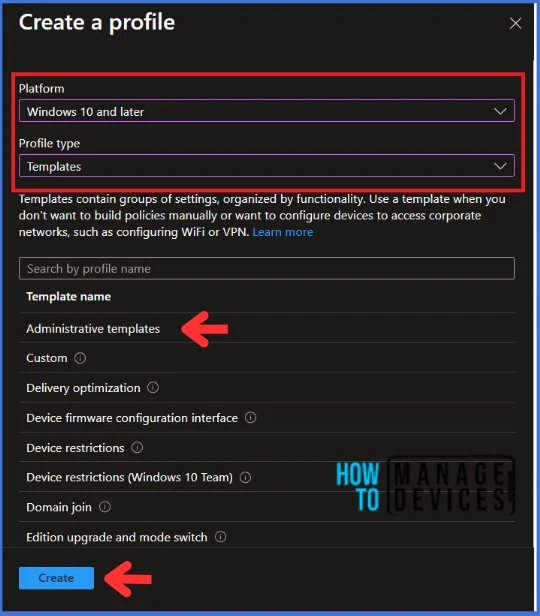
Navigate to the Basics tab and input the Name and Description for the profile. Click Next to go further.
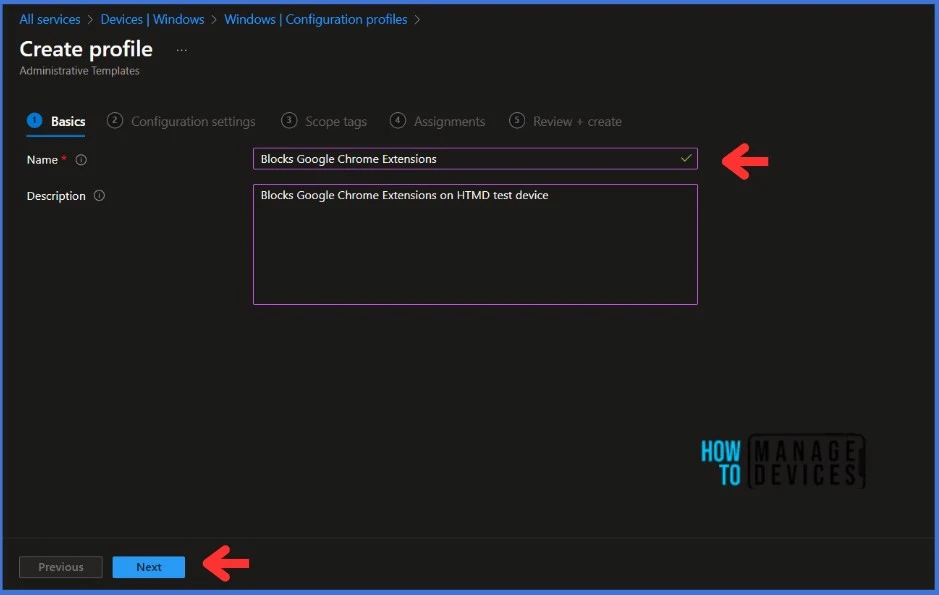
Go to Computer Configuration > Google > Google Chrome > Extensions folder in the Configuration Settings section. Search for Configure extension installation blocklist in the search bar.
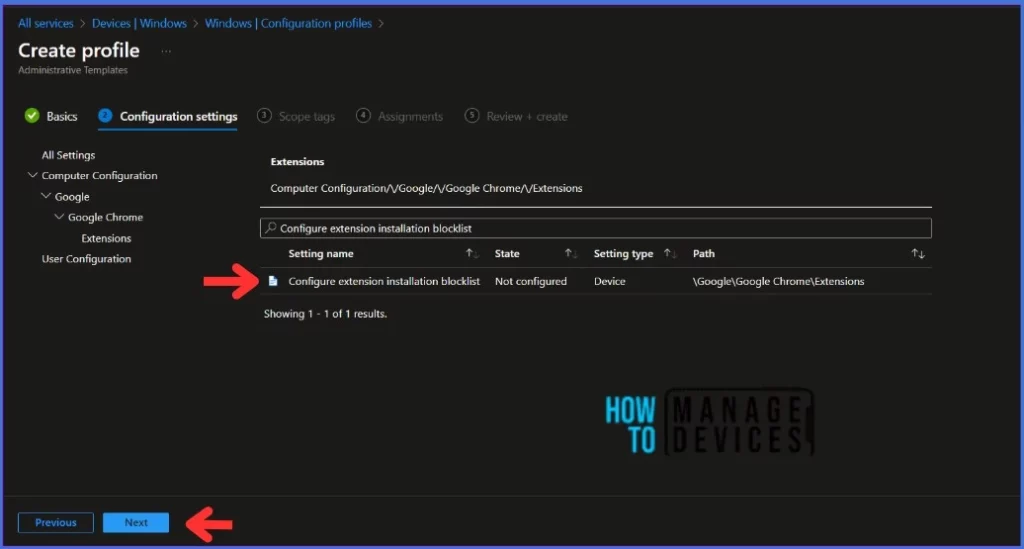
A new window will open up once you click on the Configure extension installation blocklist setting. It seems that this feature allows you to limit the extensions that users can install by specifying which ones they are not allowed to install. If a user tries to install a blocked extension, it will be disabled without their permission. However, if the blocklist is removed from an extension, it will automatically get re-enabled. If this policy is not set, the user can install any extension in Google Chrome.
NOTE : A blocklist value of '*' means all extensions are blocked unless they are explicitly listed in the allowlist.Refer to the Google document to learn the external extensions and their installation. You must select Enabled here and click OK.
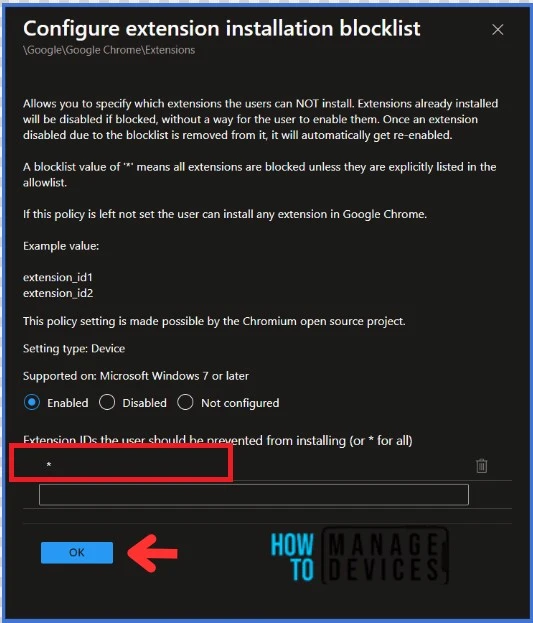
In this scenario, all extensions are being blocked using the Configure extension installation blocklist setting. However, suppose you want to allow specific extensions to be installed by users in Chrome. In that case, you can use the Configure extension installation allow list setting and add the extension ID to the list of allowed extensions.
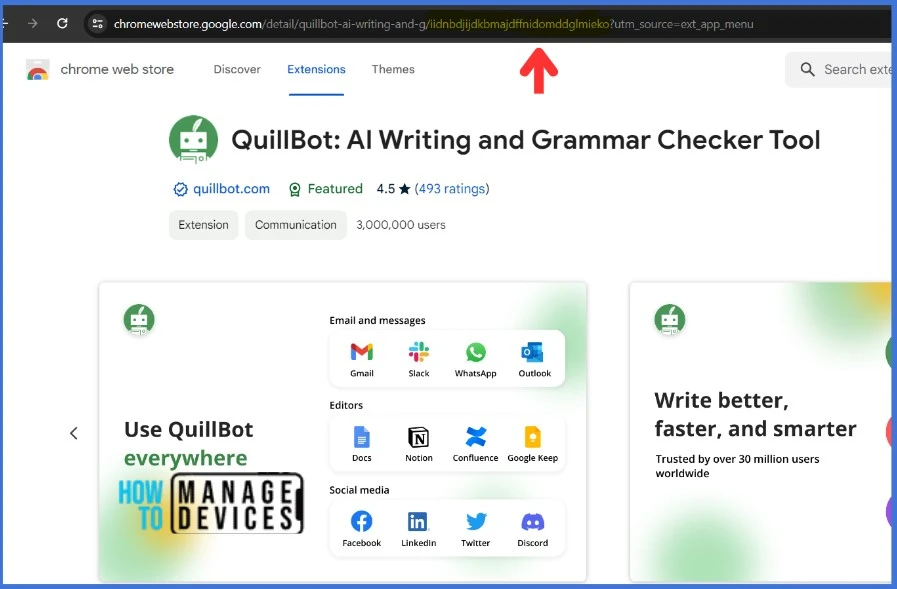
It’s important to find the extension ID of an extension by visiting the Chrome Web Store and searching for the extension. Open Google Chrome, Go to the Chrome Web Store, search for an extension you want to allow and collect the Extension ID.
I have highlighted the Extension ID in the image below. In this example, iidnbdjijdkbmajdffnidomddglmieko is the Extension ID.
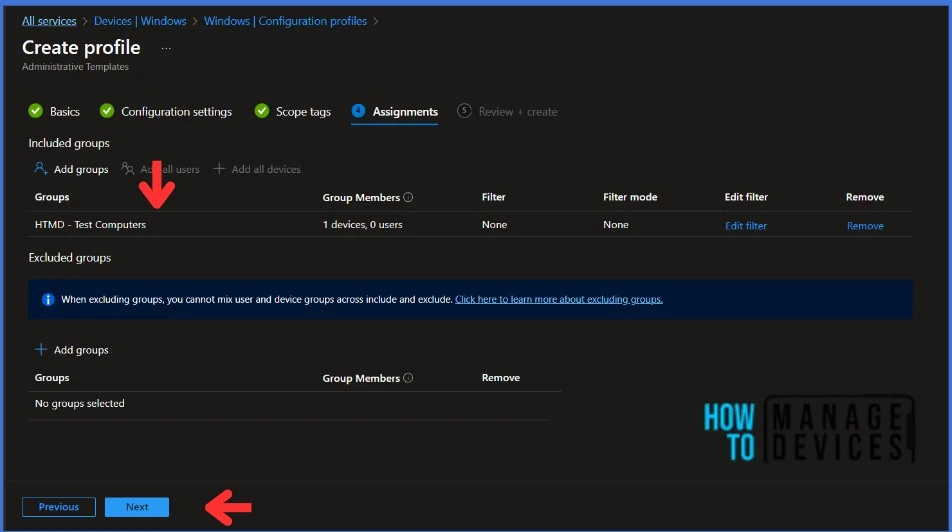
Click Next to display the Scope tags page. Add the Scope tags if you wish and click Next to assign the policy to computers. I will deploy it to the HTMD – Test Computers Group.
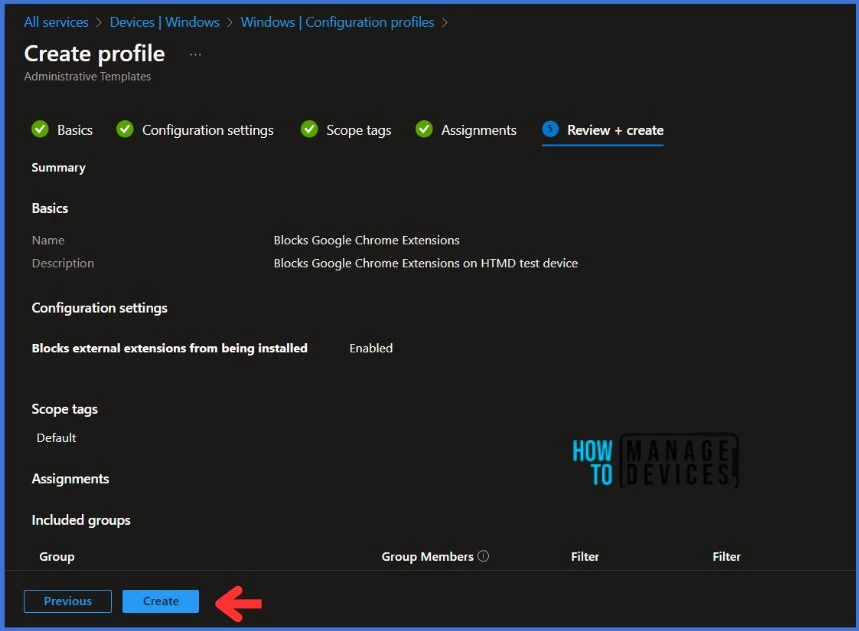
On the Review + Create page, carefully review all the settings you’ve defined to block Google Chrome Extensions. Once you’ve confirmed that everything is correct, select Create to implement the changes.
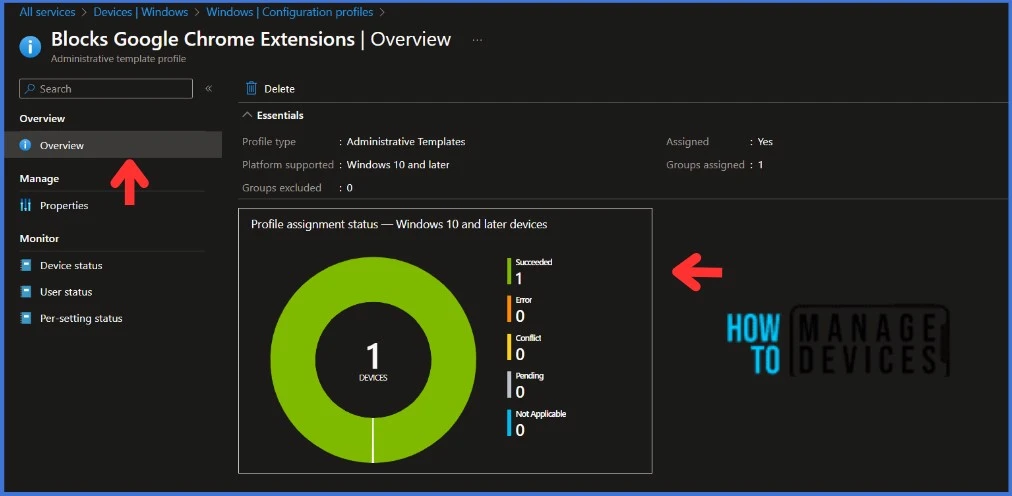
Monitor the Configuration Profile Deployment in Microsoft Intune
The configuration profile is deployed to Azure AD groups. Let’s see how we can monitor the deployment and status of installation from the Intune portal. To monitor the Intune policy assignment, follow these steps:
- Navigate to the list of Configuration Profiles and select the policy you targeted.
- Check the device and user check-in status from here.
- If you click “View Report,” you can see additional details.
- You can also quickly check the update as devices/users check status reports.
Event Log to Verify the Policy’s Deployment Status
To verify the successful implementation of String or integer policies on Windows 10 or 11 devices through Intune, you can leverage event IDs 813 and 814. These event IDs provide valuable insights into the application status of the policy as well as the specific value assigned to the policy on those devices. In the case of this particular policy, the value is String and is linked to the event ID 814.
By analyzing these event IDs, you can gain a clear understanding of the policy’s application status and the corresponding value associated with it on the devices in question.
To confirm this, you can check the Event log path – Applications and Services Logs – Microsoft – Windows – Devicemanagement-Enterprise-Diagnostics-Provider – Admin.
MDM PolicyManager: Set policy string, Policy: (ExtensionInstallBlocklist), Area: (chromeIntuneV1~Policy~googlechrome~Extensions), EnrollmentID requesting merge: (B1E9301C-8666-412A-BA2F-3BF8A55BFA62), Current User: (Device), String: (<enabled/><data id="ExtensionInstallBlocklistDesc" value="1 *"/>, Enrollment Type: (0x6), Scope: (0x0).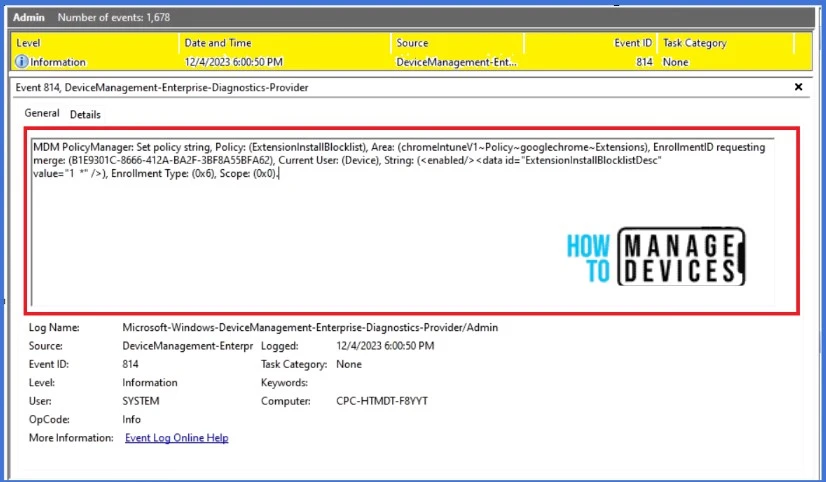
End-User Experience after Blocking the Google Chrome Extensions
Let’s verify if the policy is applied to devices and what happens when users try to add an extension to Google Chrome. Open Google Chrome, Go to the Chrome Web Store and search for any extension that you want to install. In this example, I’m trying to install the Google Translate extension.
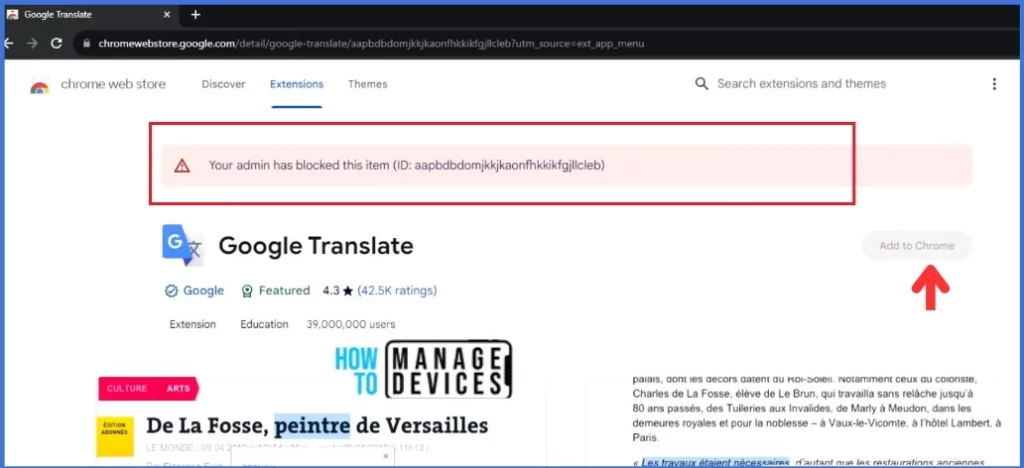
I received a warning message stating, Your admin has blocked this item when I clicked on the extension. Additionally, the Add to Chrome button was greyed out. So, Once the policy applies to the device, users will not install any other Extensions from the Store except the allowed extension
Thank you for your patience in reading this post. See you in the next post. Keep supporting the HTMD Community.
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here – HTMD WhatsApp.
Author
About Author – Sujin Nelladath has over 10 years of experience in device management technologies and Automation solutions. He writes and shares his experiences related to Microsoft device management technologies, Azure, and PowerShell automation.

Administrative templates are now retired, are you able to update the article to let us all know how to achieve this in the current (2025) Intune admin centre please
Thanks for the post. The user above is correct. Administrative Templates have been retired.