Intune RBAC roles and permissions in Intune Admin Center Portal are explained in this post. We will discuss the access rights of the built-in Intune RBAC role called Configuration policy manager.
Ideally, this role should have access to Manage and deploy configuration settings and profiles depending on the scope. Before going into details, let me explain, what is the scope.
Intune RBAC (Role-Based Access Controls) is the workflow that helps organizations segregate the roles and responsibilities of different support teams by providing them with limited access to specific resources. “The users or devices that a specified person (the member) can manage.” If you are an SCCM admin, then the SCOPE option is already there in SCCM 2012 and CB console.
Granular control to delegate the permissions to Level 1, 2, and 3 Intune teams from different operating groups (entities/opcos). Limit assigned permissions of Intune admins to specific user or device groups. Control/Manage the view permissions of Intune objects using RBAC.
- Duplicate Intune RBAC Roles | Endpoint Manager Roles
- Intune Read-Only Admin Experience After RBAC Solution
Intune RBAC Strategic options – Video
In this video, we will explain Intune RBAC Strategic Options | Role-Based Access Controls | Scope Groups | Intune Objects | Roles.
What is Intune RBAC?
RBAC helps Intune Admins to control who can perform various Intune tasks within your enterprise. There are nine (9) built-in Intune roles (RBAC roles). The list of Intune RBAC built-in roles is updated in the table.
In this post, I will try to explain the access right of Intune’s default role called Configuration Policy Manager. I have created a user name Kaith in Azure Active Directory. This user is assigned to Configuration policy manager access and the scope is set to the group “All Bangalore Users”.
Intune configuration policy manager can access Assign, Create, Delete, Read, and Update profiles. However, we will go into deep dive to understand more details about the access rights for this role.
Configuration Policy Manager – Permissions:-
Assign Device settings to AAD security groups
Create Device Settings
Delete Device Settings
Read Device Settings
Update Device Settings
Read More -> Intune Read-Only Experience Learn To Create Read-Only Operators Roles
Intune RBAC – Tired Hierarchy
Azure AD is the primary identity repository for Intune! The Intune Full Admin permissions – Azure AD.
- Global Admin Role (Tier 1)
- Intune Service Admin Role (Tier 2)
- Intune RBAC Permissions – Intune Portal
- Tier 3 Roles – App Admin, Helpdesk Admin, etc…
Updated Built-In Inutune RBAC Roles
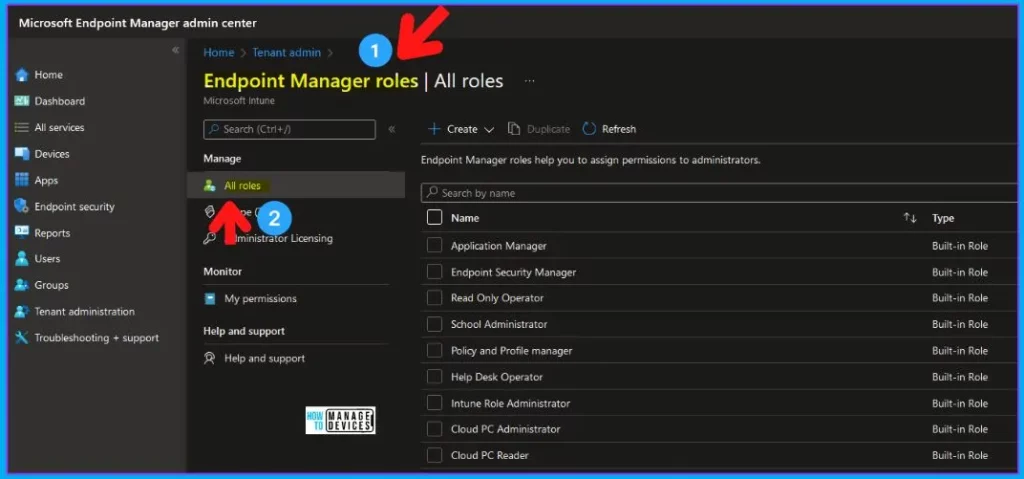
Let’s check the built-in Intune RABC roles (endpoint manager roles) available in the MEM admin center portal.
| Application Manager | Built-in Role |
| Endpoint Security Manager | Built-in Role |
| Read-Only Operator | Built-in Role |
| School Administrator | Built-in Role |
| Policy and Profile manager | Built-in Role |
| Help Desk Operator | Built-in Role |
| Intune Role Administrator | Built-in Role |
| Cloud PC Administrator | Built-in Role |
| Cloud PC Reader | Built-in Role |
Endpoint Manager Roles
Let’s understand what are the different types of roles available within Intune RBAC workflow. There are built-in roles and custom roles. I have given examples of custom roles in the previous posts.
Read More -> Create Custom Intune Helpdesk Operator Role
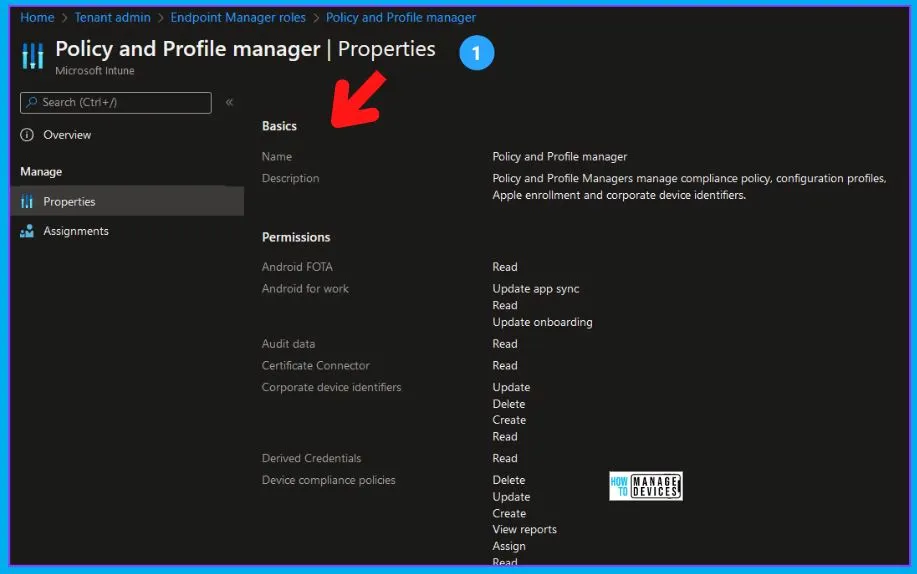
Intune RBAC Policy and Profile Manager
Assign administrators to Endpoint Manager Roles. Create and configure custom Endpoint Manager Roles. Allowed to edit the Intune Policy and Profile Manager.
- Even the profile is ONLY deployed to out-of-scope users/groups. Intune Role-Based Access (RBA) rules don’t respect the scope of the editing profile.
This should be NOT allowed. Editing should be allowed only to those profiles which are assigned ONLY to Intune policy manager’s scope of users or devices (Intune policy manager = Kaith). Intune RBAC roles are still in development.
Access is denied to remove and add assignments to a profile that is already deployed to users who are not in the scope. Addition and removal of Assignments should be allowed if the admin is trying to deploy profiles to users in scope.
- Access is denied to remove assignments to profiles that are targeted to the users or groups in scope. This should be allowed!
Allowed to delete all the profiles even if those profiles are targeted to out-of-scope users. This should NOT be allowed! If the profile is assigned only to in-scope users, then the deletion of the profile should be allowed.
Allowed to enable/disable certificate authority connector for SCEP or PFX profile deployment. Intune RBAC roles are still in development.
- Login to MEM Admin Center (Intune).
- Navigate to tenant admin -> Roles -> Endpoint Manager Roles.
Intune RBAC Access rights – Application Manager
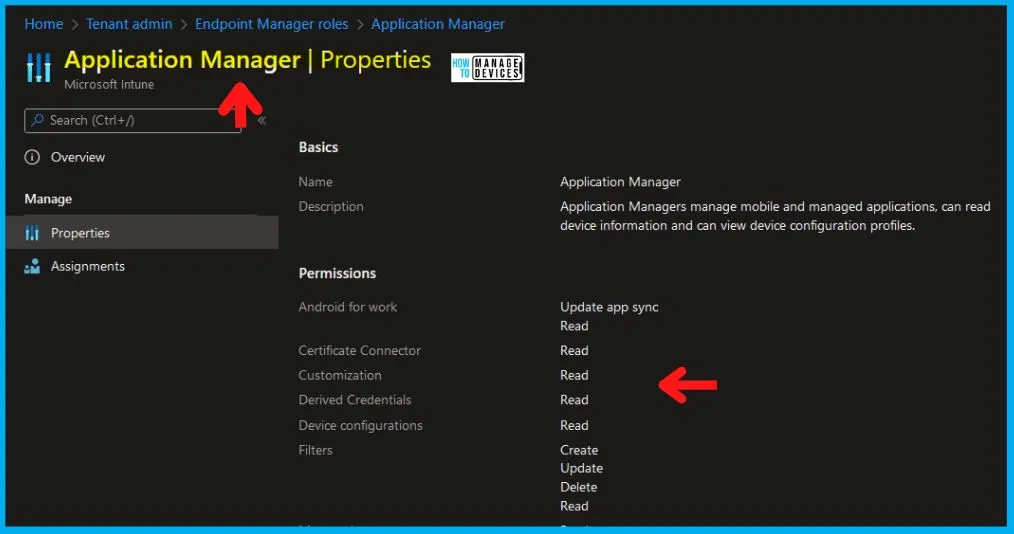
Allowed to remove assignments of applications that are already targeted to the users NOT in the scope of an Intune Application Manager. This should NOT be allowed. If it’s deployed/assigned to the users who are in scope, then removal of the assignment should be allowed.
Allowed to add assignments to the application, even if the user’s Intune application manager is targeting is out of scope for him/her. This should NOT be allowed. Assign administrators to Endpoint Manager Roles and Create and configure custom Endpoint Manager Roles.
The addition of assignment to the Application policy should be allowed only when the targeted users are within the scope of an Intune application manager.
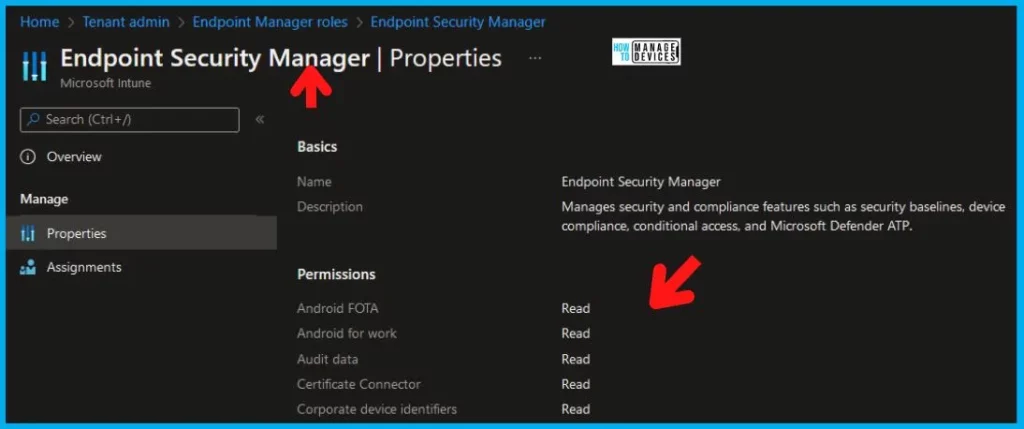
Intune RBAC – Endpoint Security Manager
Let’s discuss, Intune RBAC – Endpoint Security Manager. You can assign administrators to Endpoint Manager Roles. Create and configure custom Endpoint Manager Roles.
Intune Read-Only Operator
Name – Read-Only Operator. Description – Read-Only Operators view user, device, enrollment, configuration, and application information and cannot make changes to Intune.
More details -> Intune Read-Only Admin Experience After RBAC Solution
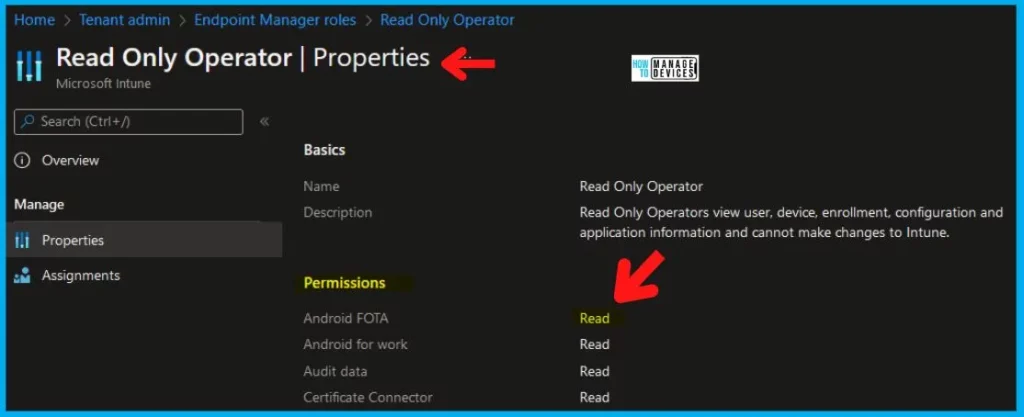
Intune School Administrator
Name – School Administrator. Description – School Administrators can manage apps and settings for their groups. They can take remote actions on devices, including remotely locking them, restarting them, and retiring them from management.
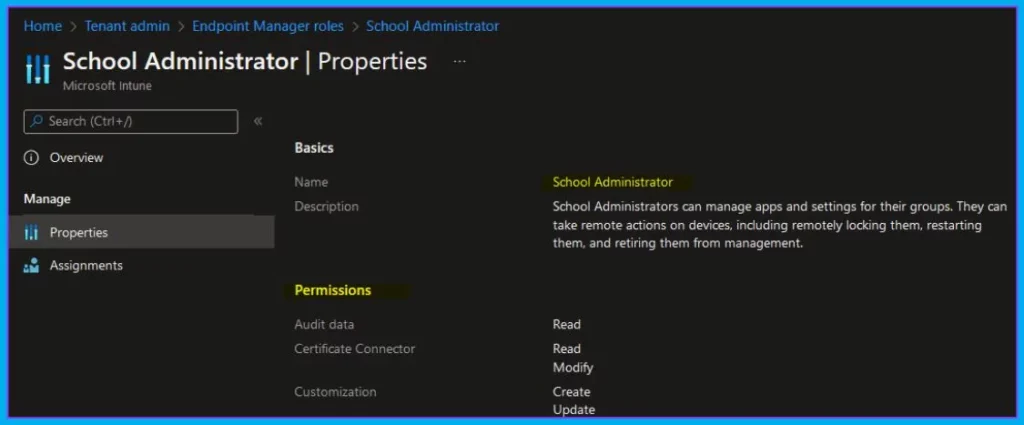
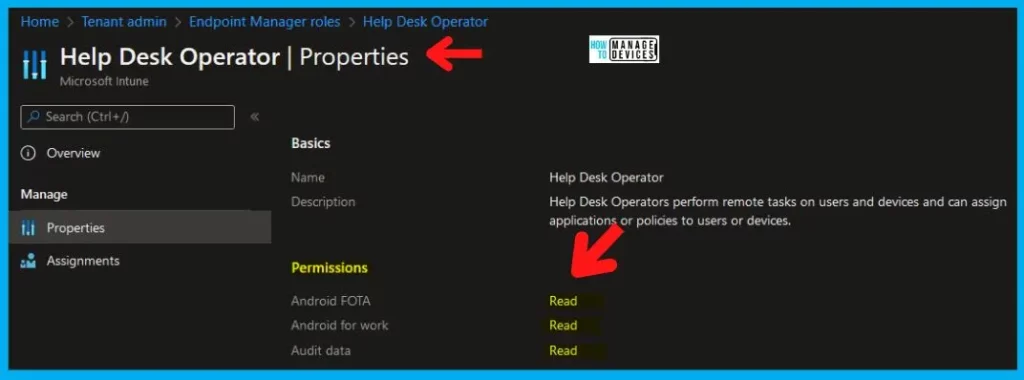
Intune RBAC – Help Desk Operator
Name – Help Desk Operator. Description – Help Desk Operators perform remote tasks on users and devices and can assign applications or policies to users or devices.
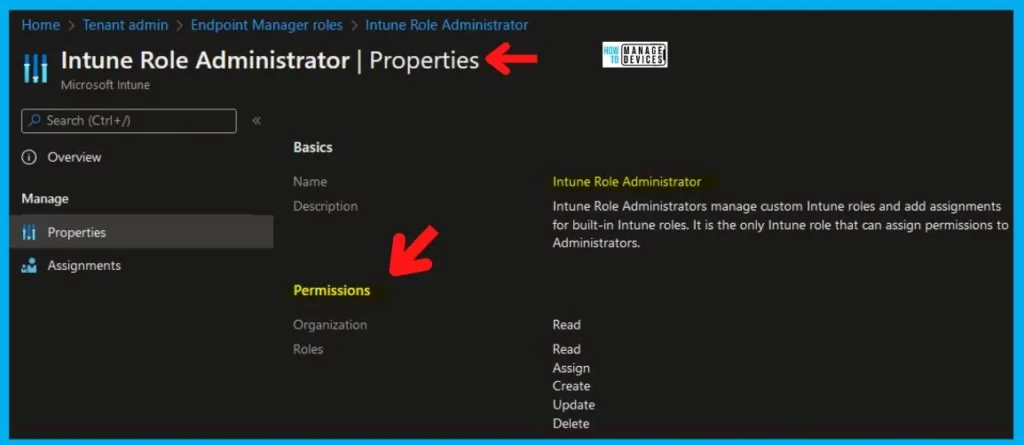
Intune Role Administrator
Name – Intune Role Administrator. Description – Intune Role Administrators manage custom Intune roles and add assignments for built-in Intune roles. It is the only Intune role that can assign permissions to Administrators.
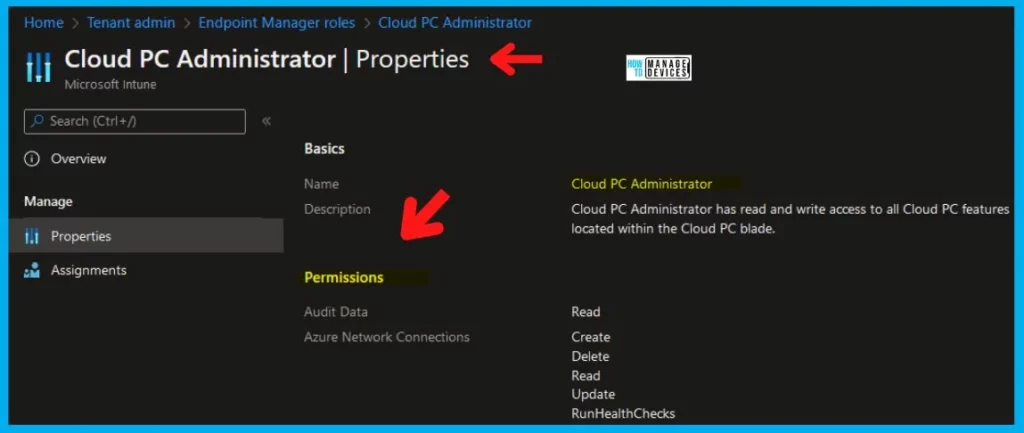
Cloud PC Administrator
Name – Cloud PC Administrator. Description – Cloud PC Administrator has read and write access to all Cloud PC features located within the Cloud PC blade.
More Details on Cloud PC (Windows 365) Provisioning -> Windows 365 Cloud PC Deployment Provisioning Process Step By Step Guide
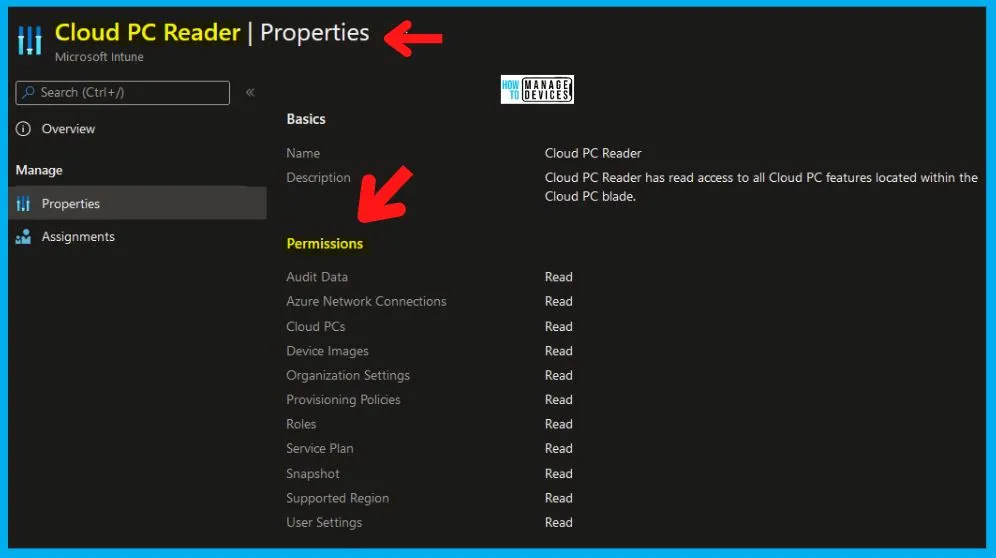
Intune RBAC – Cloud PC Reader
Name – Cloud PC Reader. Description – Cloud PC Reader has read access to all Cloud PC features located within the Cloud PC blade.
Video Tutorial – Intune RBAC Roles
A more detailed explanation is in the above Youtube video or you can click here.
Overall Access Rights of Intune tiles
Allowed to perform some administrative activities in configuring devices, and Setting device compliance tiles. Allowed to view details about users and groups in managing users’ tile.
- Access is denied to perform any activities in Manage Apps, Conditional Access, Device Enrollment, Device and Groups, and Access control tiles.
- Allowed to view objects in the Manage Users tile – Users and Groups.
- Access is denied to create/delete new/existing groups. It doesn’t matter Intune policy manager is editing the groups which are in SCOPE or not.
- Access is denied to change device and user settings in the Manage user tile.
- Access is denied to Intune Silverlight console.
Intune administrator Role permissions
Let’s check Intune administrator Role permissions from the following table.
| Actions | Description |
|---|---|
| microsoft.directory/bitlockerKeys/key/read | Read bitlocker metadata and key on devices |
| microsoft.directory/contacts/create | Create contacts |
| microsoft.directory/contacts/delete | Delete contacts |
| microsoft.directory/contacts/basic/update | Update basic properties on contacts |
| microsoft.directory/devices/create | Create devices (enroll in Azure AD) |
| microsoft.directory/devices/delete | Delete devices from Azure AD |
| microsoft.directory/devices/disable | Disable devices in Azure AD |
| microsoft.directory/devices/enable | Enable devices in Azure AD |
| microsoft.directory/devices/basic/update | Update basic properties on devices |
| microsoft.directory/devices/extensionAttributeSet1/update | Update the extensionAttribute1 to extensionAttribute5 properties on devices |
| microsoft.directory/devices/extensionAttributeSet2/update | Update the extensionAttribute6 to extensionAttribute10 properties on devices |
| microsoft.directory/devices/extensionAttributeSet3/update | Update the extensionAttribute11 to extensionAttribute15 properties on devices |
| microsoft.directory/devices/registeredOwners/update | Update registered owners of devices |
| microsoft.directory/devices/registeredUsers/update | Update registered users of devices |
| microsoft.directory/deviceManagementPolicies/standard/read | Read standard properties on device management application policies |
| microsoft.directory/deviceRegistrationPolicy/standard/read | Read standard properties on device registration policies |
| microsoft.directory/groups/hiddenMembers/read | Read hidden members of Security groups and Microsoft 365 groups, including role-assignable groups |
| microsoft.directory/groups.security/create | Create Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/delete | Delete Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/basic/update | Update basic properties on Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/classification/update | Update the classification property on Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/dynamicMembershipRule/update | Update the dynamic membership rule on Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/members/update | Update members of Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/owners/update | Update owners of Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/visibility/update | Update the visibility property on Security groups, excluding role-assignable groups |
| microsoft.directory/users/basic/update | Update basic properties on users |
| microsoft.directory/users/manager/update | Update manager for users |
| microsoft.directory/users/photo/update | Update photo of users |
| microsoft.azure.supportTickets/allEntities/allTasks | Create and manage Azure support tickets |
| microsoft.cloudPC/allEntities/allProperties/allTasks | Manage all aspects of Windows 365 |
| microsoft.intune/allEntities/allTasks | Manage all aspects of Microsoft Intune |
| microsoft.office365.supportTickets/allEntities/allTasks | Create and manage Microsoft 365 service requests |
| microsoft.office365.webPortal/allEntities/standard/read | Read basic properties on all resources in the Microsoft 365 admin center |
- Read, Delete, Wipe, Assign, Create, and Update are Inutne permissions can be assigned for each Intune objects.
Admin Groups – Admin group users are the administrators assigned to this role
Scope Groups – Administrators in this role assignment can target policies, applications, and remote tasks to Azure AD Device/User Groups
Scope tags – Who all can view this RBAC Role
41 Intune Objects List
Let’s check the list of 41 Intune Objects from Intune RBAC perspective.
Android FOTA
Android for work
Audit data
Certificate Connector
Chrome Enterprise (preview)
Cloud attached devices
Corporate device identifiers
Customization
Derived Credentials
Device compliance policies
Device configurations
Device enrollment managers
Endpoint Analytics
Endpoint protection reports
Enrollment programs
Filters
Intune data warehouse
Managed Device Cleanup Settings
Managed Google Play
Managed apps
Managed devices
Microsoft Defender ATP
Microsoft Store For Business
Microsoft Tunnel Gateway
Mobile Threat Defense
Mobile apps
Multi Admin Approval
Organization
Organizational Messages
Partner Device Management
Policy Sets
Quiet Time policies
Remote Help app
Remote assistance connectors
Remote tasks
Roles
Security baselines
Security tasks
Telecom expenses
Terms and conditions
Windows Enterprise Certificate
References:-
- Assigning administrator roles in Azure Active Directory – here
- Role-based access control (RBAC) for Microsoft Intune
Author
Anoop is Microsoft MVP! He is a Solution Architect in enterprise client management with more than 20 years of experience (calculation done in 2021) in IT. He is a blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. E writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc…


At References tab :-Role-based access control (RBAC) for Microsoft Intune – “here” is not hyperlink
Fixed now. Thank you.