In this post, we will explore Intune Win32 App Requirement Rules. Application deployment has rules, such as detection methods and requirements. These rules specify when and how the client installs the software.
Intune verifies these requirements on devices before installing the deployed applications. You can also use Intune Win32 App requirement rules to further refine and control the devices or users that receive this application.
There are some built-in and custom requirements rules you can choose from when creating your Win32 application. That will help you to manage the deployment of the app without building multiple assignments.
Here’s how you can use the script in an Intune Win32 App requirement rules, Mark Thomas has written a PowerShell script that gets the device enrollment date from the registry on the client. This can then be used as a requirement rule on a Win32 app. More details to post Targeting Intune Win32 apps and PowerShell Scripts based on the Enrollment Date.
You can also use the requirements tab while creating a win32 app, where you need to specify the requirements that devices must meet before the app is installed.
- Migrate Group Policies GPOs to Intune Settings Catalog policy
- Intune Application Deployment using MSI EXE IntuneWin Formats
- Easy Steps to Configure Company Portal Icon of an Application
Intune Win32 App Requirement Rules
You can use the following steps to add or modify requirement rules for the app installation from the MEM Admin Portal. In this section, I’m modifying the existing apps to show you the details of Win32 app requirement rules. you can also use the option while creating an app from scratch –
- Sign in to the Microsoft Endpoint Manager admin center https://endpoint.microsoft.com
- Select Apps > Windows > Windows apps. Select the existing Win32 application from the list.
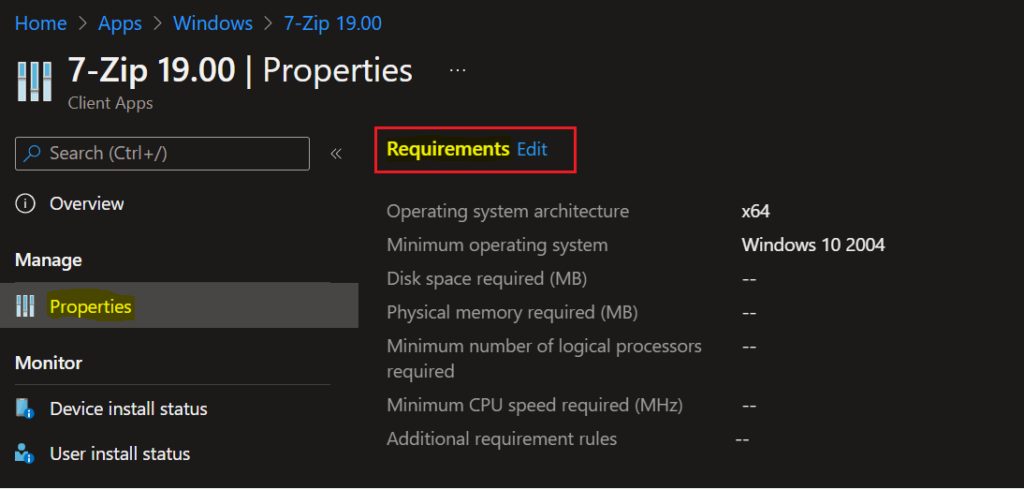
Select the application and select Properties. Scroll down and click on Edit in the Requirements.
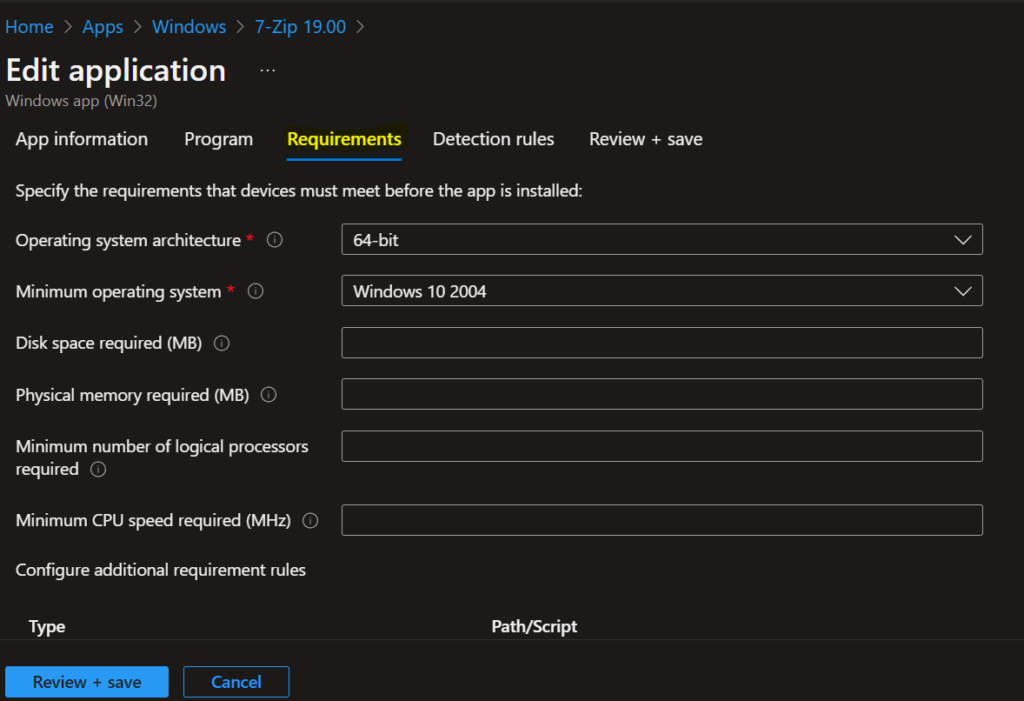
On the Requirements page, specify the requirements that devices must meet before the app is installed:
- Operating system architecture: Choose the architectures needed to install the app.
- Minimum operating system: Select the minimum operating system needed to install the app.
- Disk space required (MB): Optionally, add the free disk space needed on the system drive to install the app.
- Physical memory required (MB): Optionally, add the physical memory (RAM) required to install the app.
- Minimum number of logical processors required: Optionally, add the minimum number of logical processors required to install the app.
- Minimum CPU speed required (MHz): Optionally, add the minimum CPU speed required to install the app.
- Configure additional requirement rules:
Configure Additional Requirement Rules for Win32 Apps
Choose the type of detection method used to determine how a requirement is validated. You will get different sets of options to validate Win32 App requirement rules.
Select Add to display the Add a Requirement rule pane and configure more requirement rules. Select the Requirement type value to choose the type of rule that you’ll use to determine how a requirement is validated.
Requirement rules can be based on file system information, registry values, or PowerShell scripts.
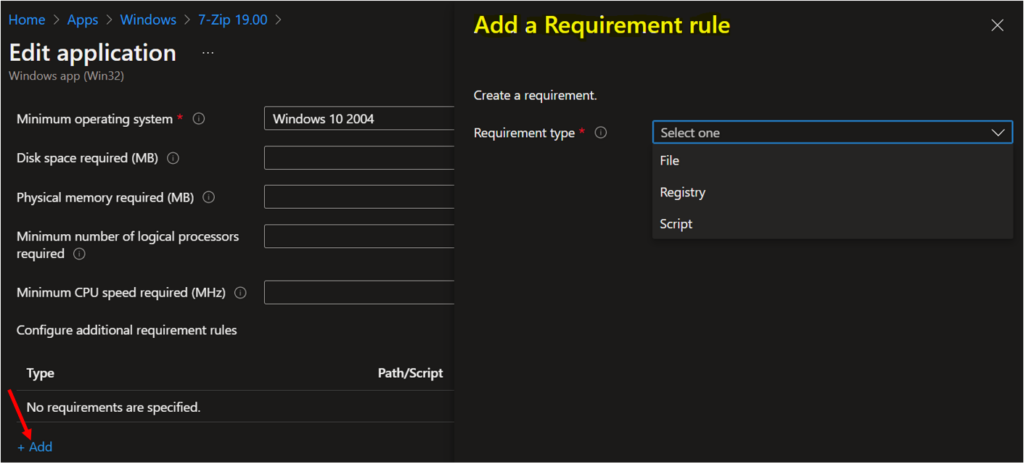
The next, Selected Requirement type File: Verify requirements based on file or folder detection, date, version, or size.
- Path: Enter the full path of the folder that contains the file or folder to detect.
- File or folder: Enter the file or folder to detect.
- Detection method: Select the type of detection method used to validate the presence of the app. The following detection methods are available in file based detection rules.
- File or folder exists.
- Date modified
- Date created
- String (version)
- Size in MB
- Associated with a 32-bit app on 64-bit clients: Select Yes to expand any path environment variables in the 32-bit context on 64-bit clients. Select No (default) to expand any path variables in the 64-bit context on 64-bit clients. 32-bit clients will always use the 32-bit context.
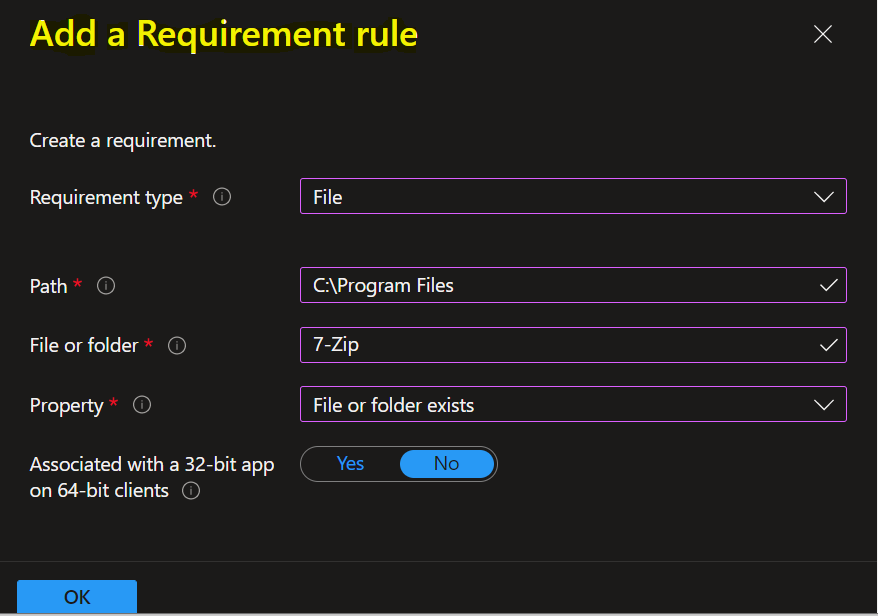
When you choose Registry as the Requirement type value, the requirement rule must detect a registry setting based on value, string, integer, or version.
- Key path: The full path of the registry entry that contains the value to detect.
- Value name: The name of the registry value to detect. If this value is empty, the detection will happen on the key. The (default) value of a key will be used as a detection value if the detection method is other than file or folder existence.
- Registry key requirement: Select the type of registry key comparison that’s used to determine how the requirement rule is validated.
- Associated with a 32-bit app on 64-bit clients: Select Yes to search the 32-bit registry on 64-bit clients. Select No (default) to search the 64-bit registry on 64-bit clients. 32-bit clients will always search the 32-bit registry.
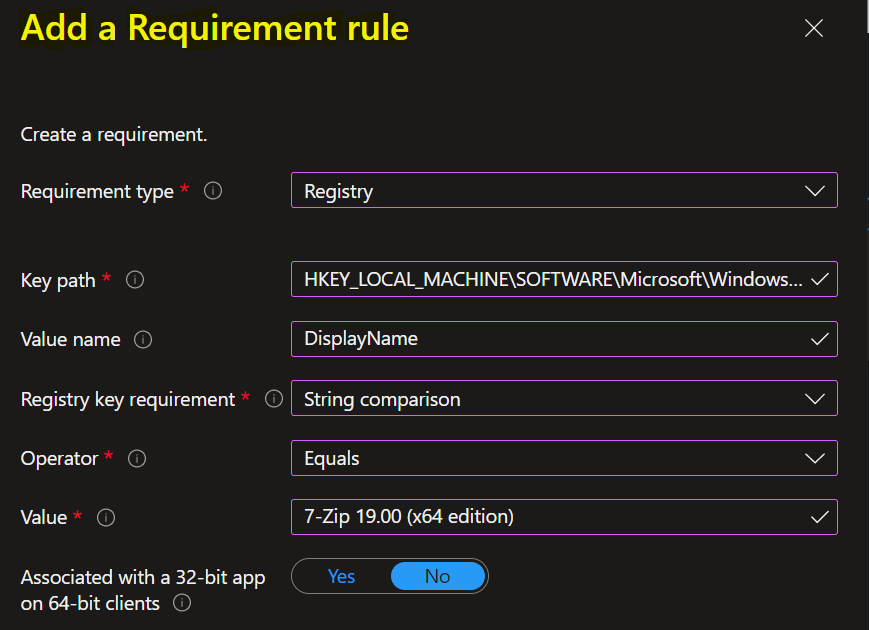
Here I chose Script as the Requirement type value when you can’t create a requirement rule based on the file, registry, or other methods available to you in the Intune console.
- Script file: For a rule based on a PowerShell script requirement, if the existing code is 0, we’ll detect the standard output (STDOUT) in more detail. For example, we can detect STDOUT as an integer that has a value of 1.
- Run script as 32-bit process on 64-bit clients: Select Yes to run the script in a 32-bit process on 64-bit clients. Select No (default) to run the script in a 64-bit process on 64-bit clients. 32-bit clients run the script in a 32-bit process.
- Run this script using the logged on credentials: Select Yes to run the script by using the signed-in device credentials.
- Enforce script signature check: Select Yes to verify that a trusted publisher has signed the script, which will allow the script to run with no warnings or prompts displayed. The script will run unblocked. Select No (default) to run the script with user confirmation without signature verification.
- Select output data type: Select the data type used for determining a requirement rule match.
You can use Powershell script to validate custom Intune win32 app requirements, More details to post Targeting Intune Win32 apps, and PowerShell Scripts based on the Enrollment Date.
When you’re finished setting the requirement rules, select OK. Select Next to display the Detection rules page. On the Detection rules pane, configure the rules to detect the app’s presence and learn about Intune Win32 App Deployment Detection Methods.
Once you have selected the summary screen will appear. Select Review + save.
A notification will appear automatically in the top right-hand corner with a message. Here you can see, Application “7-Zip 19.00” saved successfully. Here you can see the status message “Windows app (Win32) saved”
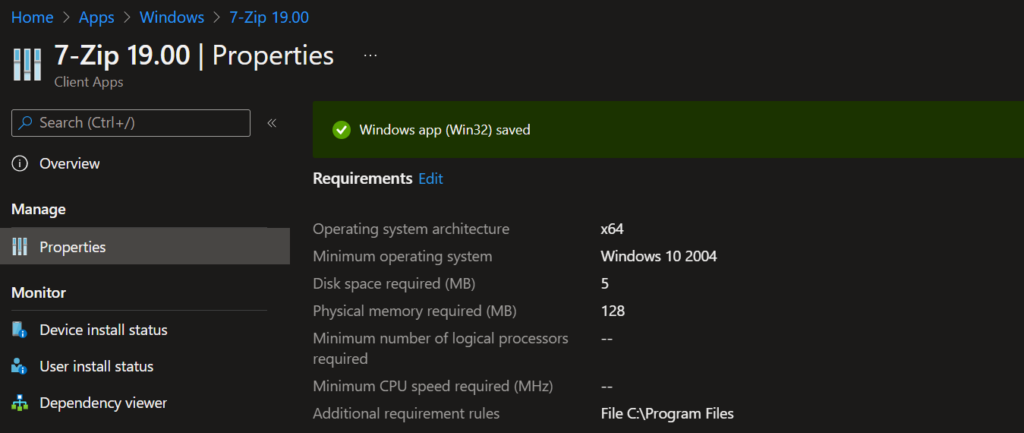
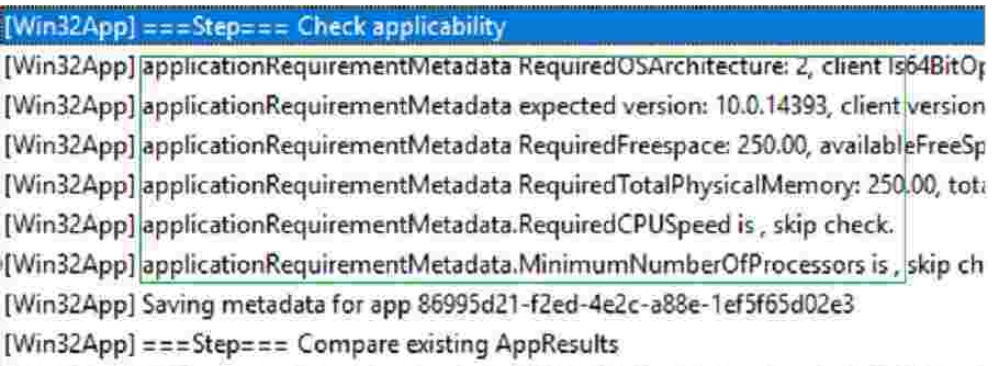
Check Applicability – Intune Win32 App Requirement Rules
Once the application installation starts, the app “Detection rule” will be evaluated. Once it is completed, the next step is “Check Applicability.” Checks were performed against the rules we configured before.
You can track the details logged at IntuneManagementExtension.log located C:\ProgramData\Microsoft\IntuneManagementExtension\Log to review how the requirements are evaluated. For example, here, you can see Check the applicability of an application.
The Intune management extension is the client-side component to manage the MDM Intune Win 32 application deployment. Learn more about Intune Win32 App Issues Troubleshooting Client-Side Process Flow.
You can look at the Level 3 deep dive troubleshooting Intune Management Extension (IME) Level 3 Troubleshooting Guide.