Let’s discuss the Windows LAPS Integration with the Local Device MaximumPasswordAge Policy. A cool new feature in Windows Local Administrator Password Solution (LAPS), also known as Windows LABS.
It focuses on improving things when working with a managed device’s local Maximum Password Age policy. This feature enhances how LAPS connects with the policy, determining how long a password stays valid on a device.
With this feature, LAPS works more effectively with the local device’s password age policy. It is good because it automatically updates the local administrator password, keeping things secure. The best part is that it’s simpler for users.
Users don’t need to worry about changing passwords frequently, as LAPS takes care of it smoothly based on the rules set by the local Maximum Password Age policy. This new feature improves security and reduces the burden on users. This feature makes it more convenient for users to log in with the Windows LAPS credentials.
- Windows LAPs Smart-Card-only Policy Integration
- Windows LAPs Automatic Account Management
- Enable Windows LAPS Managed Account in WinRE or Safemode
- Windows LAPS Configurations from Azure AD and Intune
What is the Windows Local Administrator Password Solution (LAPS)?
LAPS is the short form for Local Administrator Password Solution. It is a Windows tool designed to enhance security by automatically managing and updating the passwords of local administrator accounts on devices.
Windows LAPS Integration with Local Device MaximumPasswordAge Policy
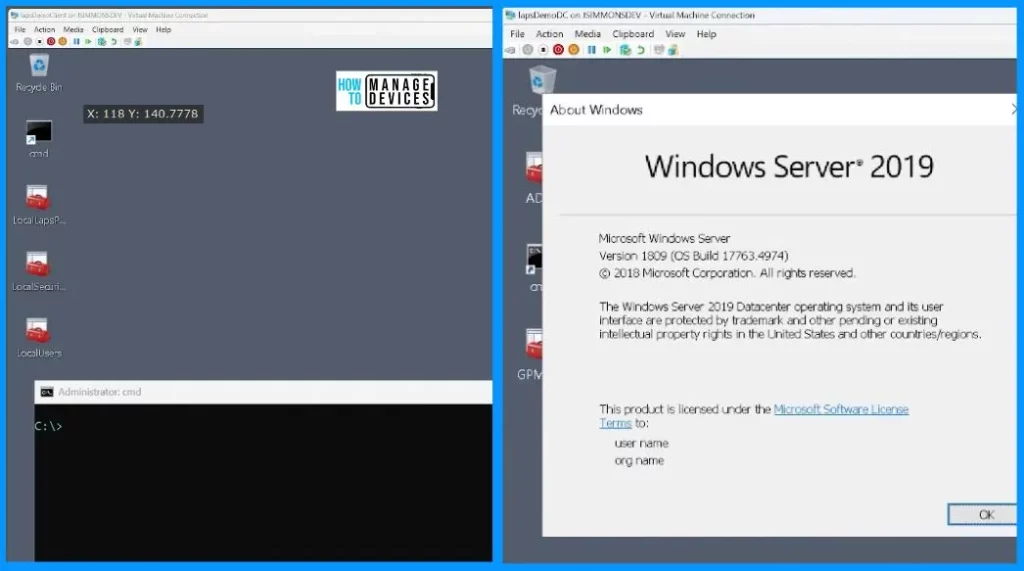
In the screenshot below, you can see two different setups. On the left side is a computer running a pre-release version of Windows 11. It’s part of a particular test domain, which means it’s connected to a network designed for testing purposes.
On the right side, there’s another computer, but this one is a Windows Server 2019. This particular computer acts as a domain controller. It manages and controls things for the other computers and devices in that test domain.
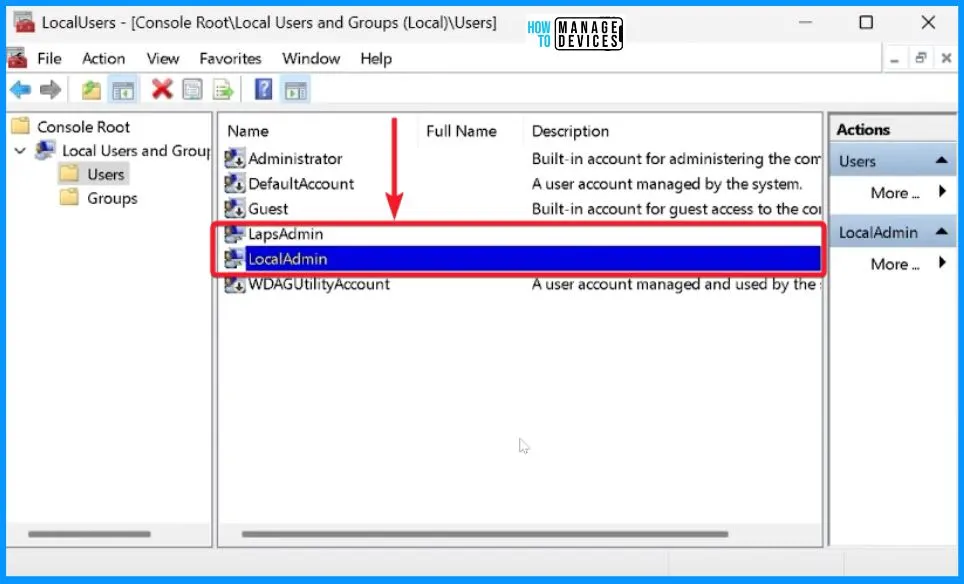
Let’s take a look at the local users on this device. There is a random Local admin account used to compare and contrast. And also a local account called the LAPS admin account. This is the Windows LAPS-managed account.
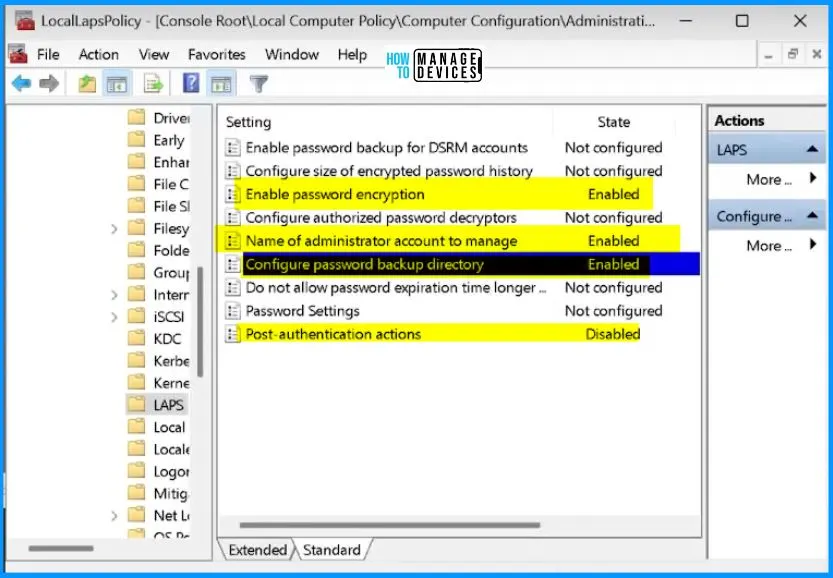
Looking at the LocalLapsPolicy, you will find many settings with their current status. Here, the Enable Password Encryption policy is Enabled. The administrator account name to manage and the Configure password backup directory are enabled. The post-authentication action is Disabled.
| Settings | State |
|---|---|
| Enable password backup for DSRM accounts | Not configured |
| Configure the size of the encrypted password history | Not configured |
| Enable password encryption | Enabled |
| Configure authorized password decryptors | Not configured |
| Name of administrator account to manage | Enabled |
| Configure password backup directory | Enabled |
| Password Settings | Not configured |
| Post-authentication actions | Disabled |
Looking at the Administrator Command Prompt window below, you can notice that the local admin account’s password was either set or last changed approximately 5 days ago.
Similarly, if you check the LAPS admin account, its password was set or changed around 5 days ago. This tells you when these password updates took place for both accounts.
net user LocalAdmin LocalAdmin
net user LapsAdmin LapsAdmin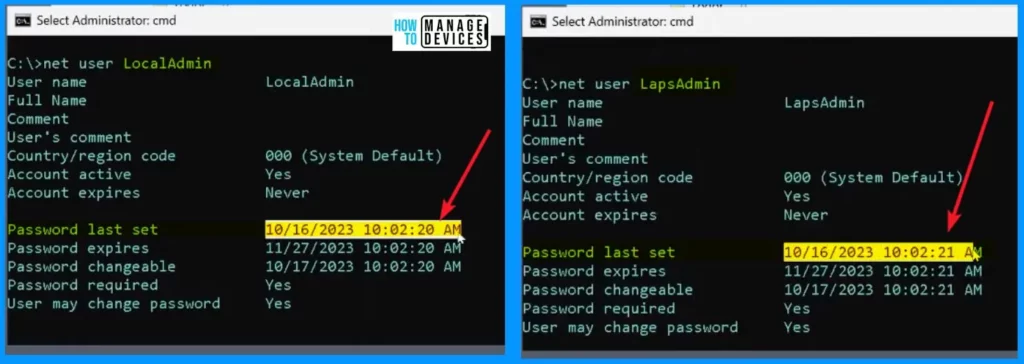
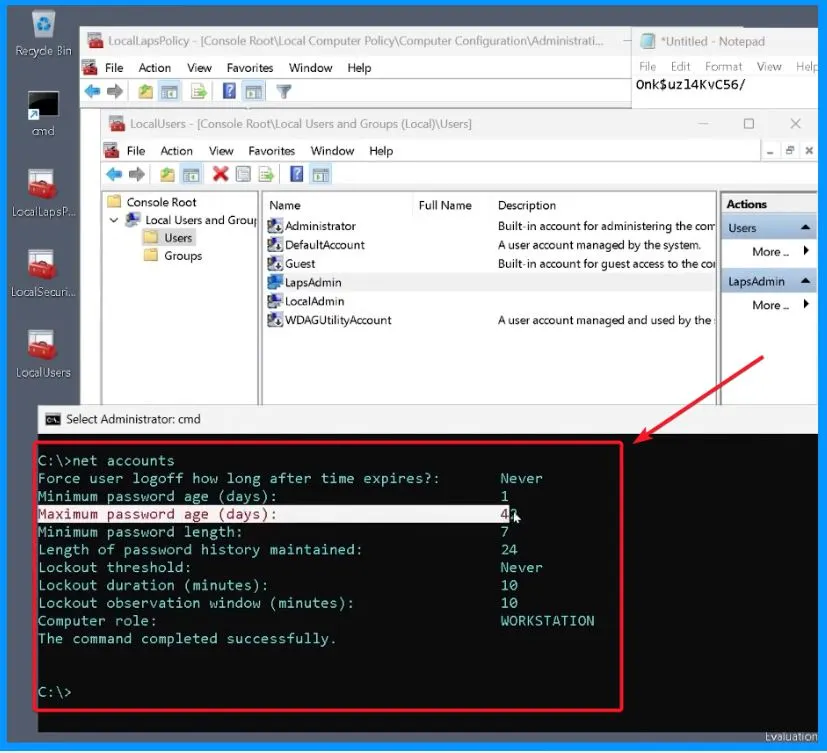
When you look at LapsAdmin and LocalAdmin accounts, there’s one more detail to discuss: the maximum password age policy. This policy essentially decides how long a password stays valid before it needs to be changed.
According to the default domain policy, the local and LAPS accounts will follow this rule, requiring a password change every 42 days. This gives you an insight into how often these passwords will be automatically updated for security reasons.
- Enter the command in the command prompt net accounts
- Click Enter
- It provides a set of information, as shown in the screenshot below
Let’s check that the local admin account and the particular LAPS admin account work authentication-wise. Looking at the screenshot below, you can see that both accounts are good to go regarding authentication.
When you use the command “runas.exe /u: LocalAdmin cmd.exe,” it prompts you to enter the LocalAdmin password. Once you enter the password, the result will show as “Attempting to start cmd.exe as user ‘LAPSDEMOCLIENT\LocalAdmin’.”
When you use the command “runas.exe /u: LapsAdmin cmd.exe,” it prompts you to enter the LapsAdmin password. Once you enter the password, the result will show as “Attempting to start cmd.exe as user “LAPSDEMOCLIENT\LapsAdmin”‘.”
runas.exe /u: LocalAdmin cmd.exe
runas.exe /u: LapsAdmin cmd.exe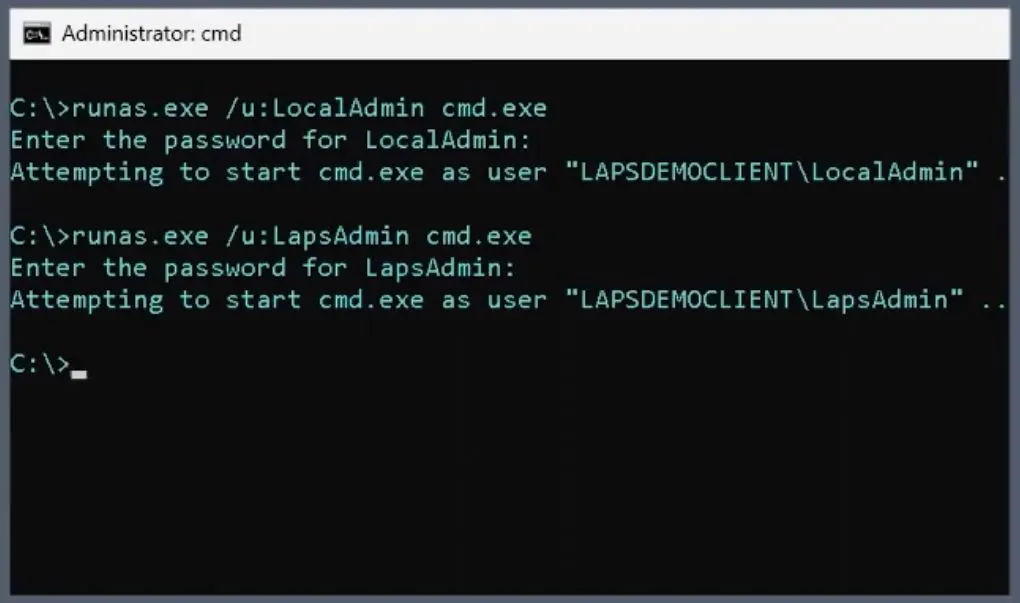
Let’s quickly change the maximum password age policy to 3 days. After that, you can see how this change impacts things. So, let’s head back to the managed device to update the policy.
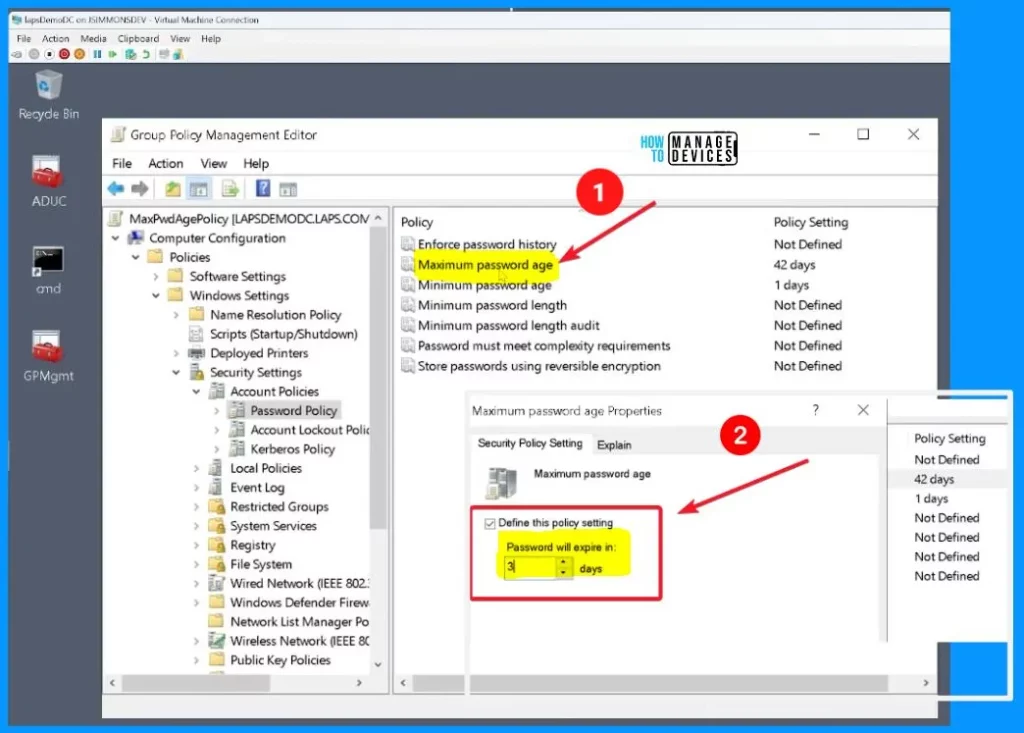
Now that we have updated the maximum password age policy to just 3 days, it’s time to see the impact. Checking the LocalAdmin and LapsAdmin accounts, you will notice that the password is set to expire within the next 3 days.
net accounts
net user LocalAdmin
User's comment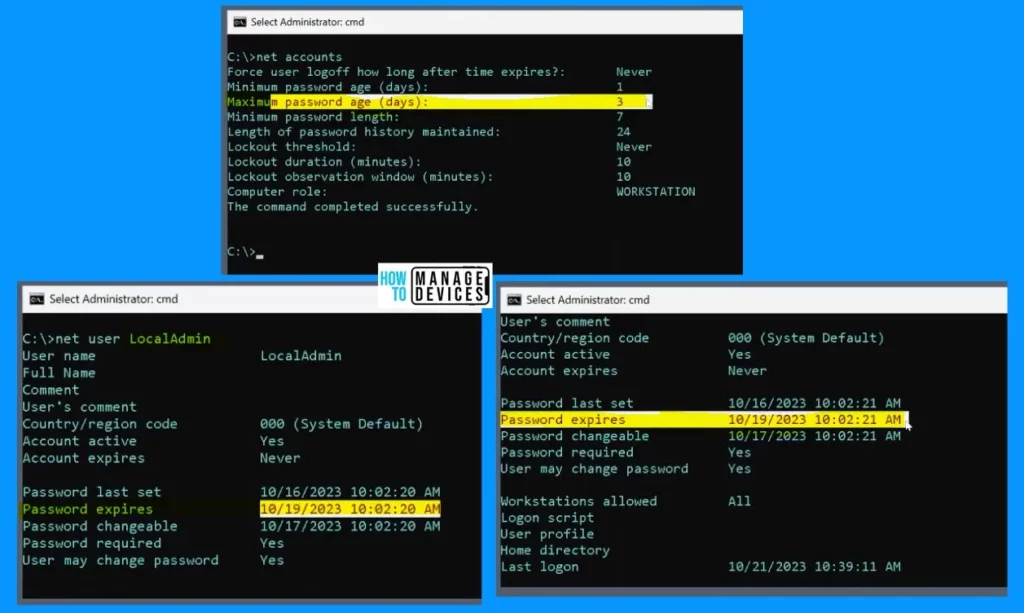
Let’s check into some runas examples to understand the impact of reducing the maximum password age policy to 3 days. As a result of this change, if we try to log in using the local admin account interactively, a prompt for a password change will immediately pop up. Essentially, we have blocked the ability of the local admin account to log in.
When you enter the runas.exe /u: LocalAdmin cmd.exe, it will ask you to enter the password. Once entering the password, it shows the result as Attempting to start cmd.exe as user “LAPSDEMOCLIENT\LocalAdmin” RUNAS ERROR: Unable to run – cmd.exe 1327: Account restrictions are preventing this user from signing in. For example: blank passwords aren’t allowed, sign-in times are limited, or a policy restriction has been enforced.
runas.exe /u: LocalAdmin cmd.exeLet’s test it out with a LapsAdmin account, and you’ll observe that it still works smoothly. This is small, but this is a nice improvement. Windows LAPS is now an integral part of the Windows operating system.
runas.exe /u: LapsAdmin cmd.exe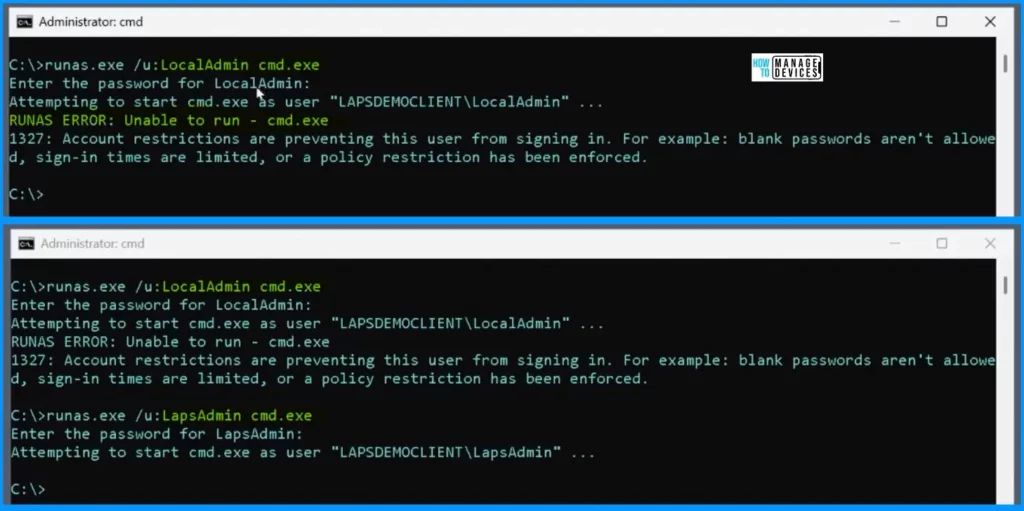
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here. HTMD WhatsApp.
Author
About the Author – Vidya is a computer enthusiast. She is here to share quick tips and tricks with Windows 11 or Windows 10 users. She loves writing on Windows 11 and related technologies. She is also keen to find solutions and write about day-to-day tech problems.
