Let’s learn how you can manage macOS Updates using Intune Policy. With policies for macOS software updates, you can remotely manage how downloads and installations are by specifying a schedule that determines when the update installs.
Starting with Intune Service release 2210, you can now use Intune policies to manage macOS software updates for devices that enrolled using Automated Device Enrollment (ADE).
Do you have supervised macOS devices macOS 12 and later? If so, you can use Intune to manage software updates. macOS that enroll through one of the methods Automated Device Enrollment (ADE) (using either Apple Business Manager, or Apple School Manager) are supervised.
You will able to manage and configure the updates for macOS, Intune supports the following macOS update types:
- Critical updates
- Firmware updates
- Configuration file updates
- All other updates (OS, built-in apps)
By default, devices check in with Intune about every 8 hours. If an update is available through an update policy, the device downloads the update. The device then installs the update upon the next check-in within your scheduled configuration.
- How To Schedule IOS Automatic Updates Using Intune Policies
- Configure Intune Enrollment Setup for iOS macOS Devices
Manage macOS Updates Using Intune Policy
Let’s follow the steps to configure update policies for macOS in Intune Portal. Here are the processes for macOS updates using Intune policies.
- Sign in to the Microsoft Intune admin center https://endpoint.microsoft.com.
- Select Devices > Update policies for macOS > Create profile.
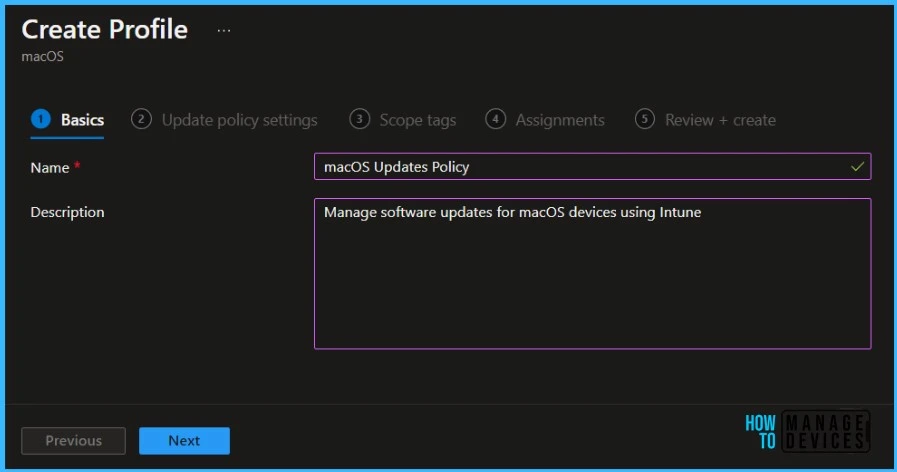
On the Basics tab, specify a name for this policy, specify a description (optional), and then select Next.
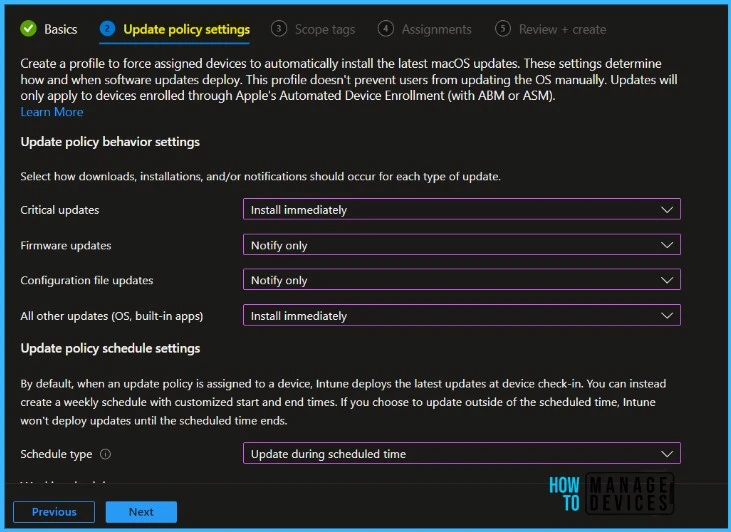
On the Update policy settings tab, configure the following options by selecting how downloads, installations, and/or notifications should occur for each type of update.
- For Critical, Firmware, Configuration file, and All other updates (OS, built-in apps), the following installation actions can be configured for each update:
- Download and install: Download or install the update, depending on the current state.
- Download only: Download the software update without installing it.
- Install immediately: Download the software update and trigger the restart countdown notification.
- Notify only: Download the software update and notify the user through the App Store.
- Install later: Download the software update and install it later.
- Not configured: No action taken on the software update.
By default, when an update policy is assigned to a device, Intune deploys the latest updates at device check-in. You can instead create a weekly schedule with customized start and end times. If you choose to update outside of the scheduled time, Intune won’t deploy updates until the scheduled time ends.
- Schedule type: Configure the schedule for this policy when updates will be available to install. Updates made during or outside of scheduled times require additional input.
- Update at next check-in: The update installs on the device the next time it checks in with Intune. This option is the simplest and has no extra configurations.
- Update during scheduled time: You configure one or more windows of time during which the update will install upon check-in.
- Update outside of scheduled time: You configure one or more windows of time during which the updates won’t install upon check-in.
If you don’t configure times to start or end, the configuration results in no restriction and updates can be installed at any time.
- Weekly schedule: If you choose a schedule type other than update at next check-in, configure the following options:
- Time zone: Choose a time zone.
- Time window: Define one or more blocks of time that restrict when the updates install.
- Start day: Choose the day on which the schedule window starts.
- Start time: Choose the time day when the schedule window begins.
- End day: Choose the day on which the schedule window ends.
- End time: Choose the time of day when the schedule window stops.
Scope tags are filtering options provided in Intune to ease the admin jobs. In the scope tag section, you will get an option to configure scope tags for the rules. Click on Next.
On the Assignments tab, choose + Select groups to include and then assign the update policy to one or more groups. Use + Select groups to exclude to fine-tune the assignment. When ready, select Next to continue.
The devices used by the users targeted by the policy are evaluated for update compliance. This policy also supports userless devices.
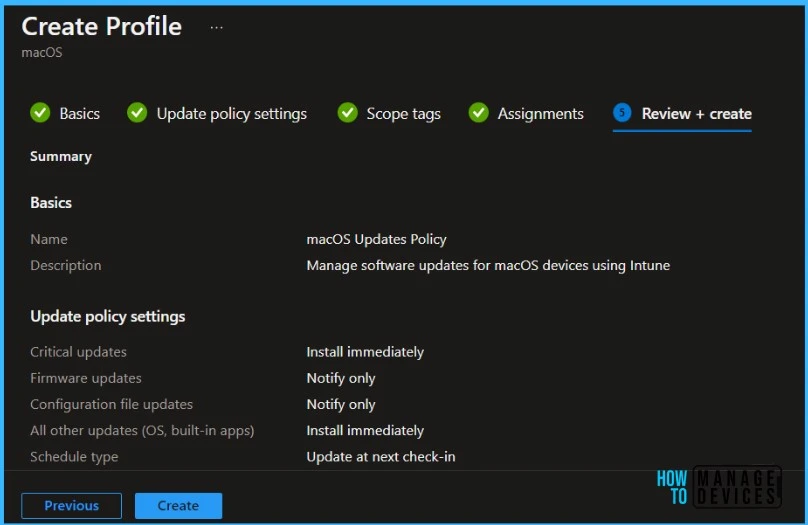
On the Review + create tab, review the settings, and then select Create when ready to save your macOS update policy.
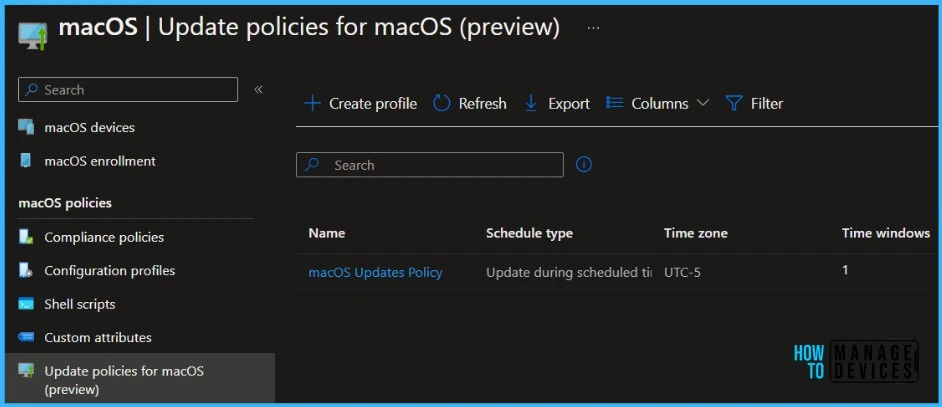
A notification will appear automatically in the top right-hand corner with a message. You can see that the Update policies for macOS created successfully. The policy is displayed in the list of update policies for macOS.
Monitor macOS Update Installation Failures from Intune
In the Microsoft Intune admin center, Navigate to Devices > Monitor > Installation status for macOS devices.
Intune displays a list of supervised macOS devices that are targeted by an update policy. The list doesn’t include devices that are up-to-date and healthy because macOS devices only return information about installation failures.
For each device on the list, the Installation Status displays the error that was returned by the device. To view the list of potential installation status values, on the Installation status for macOS devices page, select Filters and then expand the drop-down list for Installation Status.

Hello
Will this also force the install of updates from apps like chrome, lastpass, zoom etc?
At the moment it seems i have to go into chrome. about chrome and the update is there but needs to be manually restarted,
Thanks for the article