Microsoft Cloud Security Benchmark Guide (MCSB) with Control Domain Security Principle Azure AWS Guidance. The Microsoft Security Benchmark Guide is a comprehensive resource that provides detailed recommendations and best practices for helping organizations secure their cloud and on-premises environments.
The Microsoft Cloud Security Benchmark (MCSB) is an essential collection of security recommendations designed to help secure your cloud environment. It provides high-impact security controls and service-specific baselines, allowing you to protect your workloads across single or multi-cloud platforms.
Whether working with Azure or planning multi-cloud deployments, MCSB offers best practices for strengthening your security posture and keeping your resources safe from misconfigurations and attacks.
In this post, we’ll explain the Microsoft Security Benchmark Guide to help you understand its importance in securing cloud and on-premises environments. The guide provides a set of high-impact security controls and best practices designed to align with industry standards and ensure consistent security across Microsoft services, particularly in Azure.
Table of Contents
Can we use MCSB with Multi-cloud Environments?

MCSB supports multi-cloud environments, allowing you to manage and monitor security controls across different cloud platforms consistently.
Does MCSB Align with Other Security Frameworks?

MCSB maps to several well-known security frameworks, including CIS, NIST, and PCI-DSS, helping you ensure compliance with industry standards.
Microsoft Cloud Security Benchmark Guide
The screenshot below provides an early preview of the Microsoft Cloud Security Benchmark (MCSB) V1 for the web version of the content. It includes a control mapping between MCSB and industry benchmarks like NIST, CIS, and PCI. This mapping shows how specific Azure features can help meet some or all of the requirements defined by these benchmarks.
However, it’s essential to understand that using these Azure features doesn’t guarantee full CIS, NIST, or PCI compliance. The document is meant to be a helpful guide, but it shouldn’t be the only resource for meeting specific compliance requirements. Customers should consult their organization’s legal team to ensure their implementation meets all necessary regulations.
- 50% of Identities have Access to Full Access as per Microsoft Security Report 2024
- XSPM vs XDR Illustration in Microsoft Security Stack
- Maester Microsoft Security Test Automation Framework
Principles for Multi-Cloud Security Guidance
Let’s discuss the Principles of Multicloud Guidance. The list below will help you to see more details.
- The security guidance for non-Azure platforms will follow the same cloud-neutral security principles at each control level of Azure’s
- The security guidance for non-Azure platforms will provide the same granularity and scope in the technical guidance as Azure’s.
- The non Microsoft cloud service provider’s CSP native solution or feature will usually be recommended as the first preference for each control. However, when a more mature multi-cloud solution is available in Azure, it will be prioritized as the default recommendation.
- If neither the CSP’s native technology nor Azure solutions are available to satisfy a secure principle, Azure or the other CSP’s Marketplace will recommend a third-party solution. However, Microsoft Cloud Security Benchmark will not name any third-party vendor product or solution.
| Guidance | Details |
|---|---|
| ID# | The Microsoft Cloud security Benchmark ID |
| Control Domain | The security control domain |
| Security Principle | The technology agnostic and cloud neutral principle for various security topics in each control domains. |
| Recommendation | The control recommendation in summarized format |
| Azure Guidance | The technical guidance for Azure platforms |
| AWS Guidance | The technical guidance for Amazon Web Service platforms |
| Implementation and Additional Context | The implementation details and other relevant contexts that link to Azure or AWS service-offering documentation articles are also included. |
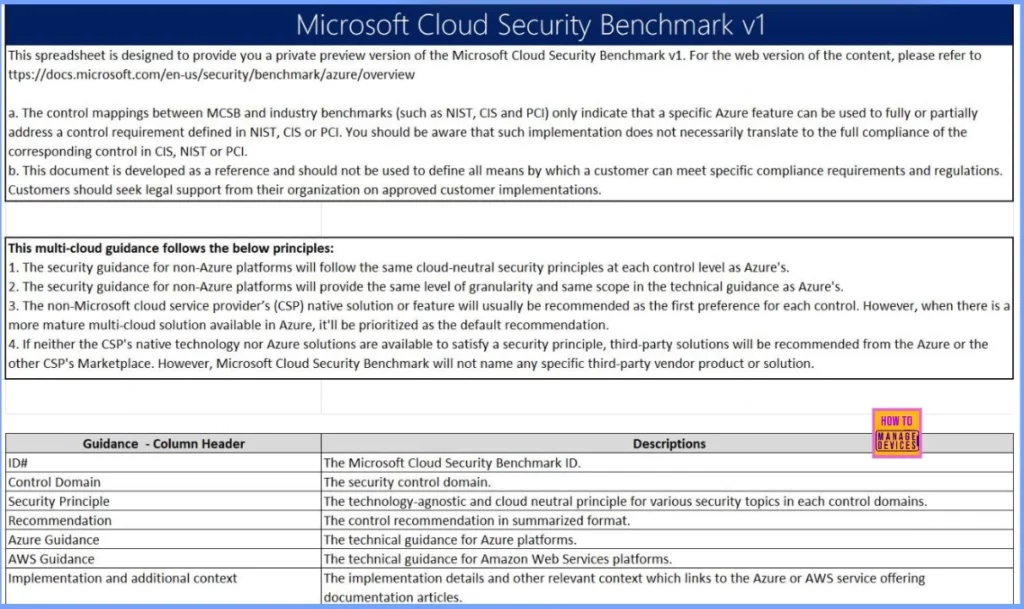
Control Domain Network Security
Here is a summary of the network security controls based on various standards and Azure implementation guidelines. The NS-1: Network Segmentation & Traffic Filtering Controls: CIS: Use approved ports, protocols, and host-based firewalls and deny communication with malicious IPs.NIST: Implement information flow enforcement and boundary protection. PCI: Segment networks and enable firewall filtering. The table below provides more details.
| ID | Control Domain | CIS Control V7.1 ID(s) | CIS Control V8 ID(s) | NIST SP800-53 r4 ID(s) | PCI-DSS v3.2.1 | Recommendations | Security Principle | Azure Guidance | Implementation and additional context |
|---|---|---|---|---|---|---|---|---|---|
| NS-1 | Network security | 9.2 Ensure only Approved ports, protocols and services are running 9.4 Apply Host- based firewall or port filtering 12.3 Deny communications with known malicious IP addresses 12.4 Deny communication over unauthorised ports 14.1 Segment the Network based on sensitivity 14.2 Enable Firewall Filtering between VLANs | 3.12 segment Data processing and storage based on sensitivity 13.4 perform Traffic filtering between Network segments 4.4 Implement and Manage a firewall on servers | Ac-4 Information flow enforcement SC-2:Application partitioning SC-7:Boundary protection | 1.1 1.2 1.3 | Establish network segmentation boundaries | Ensure that your virtual network deployment aligns with your enterprise segmentation strategy defined in the GS-2 security control. Any workload that could incur higher risk for the organization should be in an isolated virtual networks. Examples of high-risk workloads include: An application storing or processing highly sensitive data. An external network-facing application accessible by the public or users outside of your organization. An application using insecure architecture or containing vulnerabilities that cannot be quickly remediated. To enhance your enterprise segmentation strategy, restrict or monitor traffic between internal resources using network controls. For specific, well-defined applications (such as a 3-tier app), this can be a highly secure “deny by default, permit by exception” approach by restricting the ports, protocols, source, and destination IPs of the network traffic. If you have many applications and endpoints interacting with each other, blocking traffic may not scale well, and you may only be able to monitor traffic. | Create a virtual network (VNet) as a fundamental segmentation approach in your Azure network, so resources such as VMs can be deployed into the VNet within a network boundary. To further segment the network, you can create subnets inside VNet for smaller sub-networks. Use network security groups (NSG) as a network layer control to restrict or monitor traffic by port, protocol, source IP address, or destination IP address. Refer to NS-7 Simplify network security configuration to use Adaptive Network Hardening to recommend NSG hardening rules based on threat intelligence and traffic analysis result. You can also use application security groups (ASGs) to simplify complex configuration. Instead of defining policy based on explicit IP addresses in network security groups, ASGs enable you to configure network security as a natural extension of an application’s structure, allowing you to group virtual machines and define network security policies based on those groups. | Azure Virtual Network concepts and best practices: https://docs.microsoft.com/azure/virtual-network/concepts-and-best- practices Add, change, or delete a virtual network subnet: https://docs.microsoft.com/azure/virtual-network/virtual-network- manage-subnet How to create a network security group with security rules: https://docs.microsoft.com/azure/virtual-network/tutorial-filter- network-traffic Understand and use application security groups: https://docs.microsoft.com/azure/virtual-network/network-security- groups-overview#application-security-groups |
| NS-2 | Network security | 14.1 – Segment the Network Based on Sensitivity | 3.12 – Segment Data Processing and Storage Based on Sensitivity 4.4 – Implement and Manage a Firewall on Servers | AC-4: INFORMATION FLOW ENFORCEMENT SC-2: APPLICATION PARTITIONING SC-7: BOUNDARY PROTECTION | 1.1 1.2 1.3 | Secure cloud services by establishing a private access point for the resources. You should also disable or restrict access from public network when possible. | Secure cloud services by establishing a private access point for the resources. You should also disable or restrict access from public network whenpossible. | Deploy private endpoints for all Azure resources that support the Private Link feature, to establish a private access point for the resources. Using Private Link will keep the private connection from routing through the public network. Note: Certain Azure services may also allow private communication through the service endpoint feature, though it is recommended to use Azure Private Link for secure and private access to services hosted on Azure platform. For certain services, you can choose to deploy VNet integration for the service where you can restrict/isolate the VNET to establish a private access point for the service. You also have the option to configure the service native network ACL rules or simply disable public network access to block access from the public network. For Azure VMs, unless there is a strong use case, you should avoid assigning public IPs/subnet directly to the VM interface and instead use gateway or load balancer services as the front-end for access by the public network. | Understand Azure Private Link: https://docs.microsoft.com/azure/private-link/private-link-overview Integrate Azure services with virtual networks for network isolation: https://learn.microsoft.com/en-us/azure/virtual-network/vnet- integration-for-azure-services |
| NS-3 | Network security | 9.2 – Ensure Only Approved Ports, Protocols and Services Are Running 9.4 – Apply Host-Based Firewalls or port filtering 12.3 – Deny | 4.4 – Implement and Manage a Firewall on Servers 4.8 – Uninstall or Disable Unnecessary services on enterprise Assets and Software | AC-4: INFORMATION FLOW ENFORCEMENT SC-7: BOUNDARY PROTECTION CM-7: LEAST FUNCTIONALITY | 1.1 1.2 1.3 | Deploy firewall at the edge of enterprise network | Deploy a firewall to perform advanced filtering on network traffic to and from external networks. You can also use firewalls between internal segments to support a segmentation strategy. If required, use custom routes for your subnet to override the system route when you need to force the network traffic to go through a network appliance for security control purpose. | Use Azure Firewall to provide fully stateful application layer traffic restriction (such as URL filtering) and/or central management over a large number of enterprise segments or spokes (in a hub/spoke topology). If you have a complex network topology, such as a hub/spoke setup, you may need to create user-defined routes (UDR) to ensure the traffic goes through the desired route. For example, you have the option to use an UDR to redirect egress internet traffic through a specific Azure. | How to deploy Azure Firewall: https://docs.microsoft.com/azure/firewall/tutorial-firewall-deploy- portal Virtual network traffic routing: https://docs.microsoft.com/azure/virtual-network/virtual-networks- udr-overview |
You can download the spreadsheet from the GitHub repository mentioned in the post below.
- Microsoft Security Exposure Management Using Defense Techniques
- Free Microsoft Copilot for Security Training in Audit Mode | 5 Modules
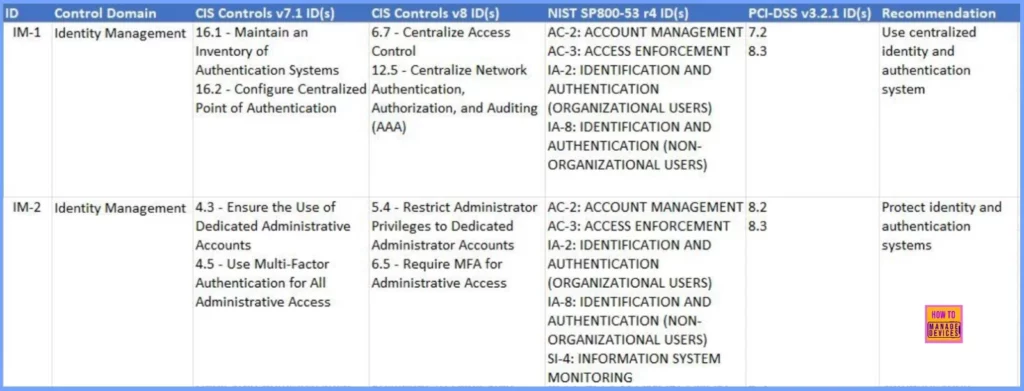
Control Domain Identity Management
Here is a structured summary of the Identity Management Control (IM-1, IM2, etc), focusing on best practices, relevant controls, and Azure guidance. The table below helps you show more details.
| ID | Control Domain | CIS Controls v7.1 ID(s) | CIS Controls v8 ID(s) | NIST SP800-53 r4 ID(s) | PCI-DSS v3.2.1 ID(s) | Recommendation | Security Principle | Azure Guidance | Implementation and additional context |
|---|---|---|---|---|---|---|---|---|---|
| IM-1 | Identity Management | 16.1 – Maintain an Inventory of Authentication Systems 16.2 – Configure Centralized Authentication, Point of Authentication | 6.7 – Centralize Access Control 12.5 – Centralize Network Authorization, and Auditing (ORGANIZATIONAL USERS) (AAA) | AC-2: ACCOUNT MANAGEMENT 7.2 AC-3: ACCESS ENFORCEMENT IA-2: IDENTIFICATION AND AUTHENTICATION IA-8: IDENTIFICATION AND AUTHENTICATION (NON- ORGANIZATIONAL USERS) | 7.2 8.3 | Use centralized identity and authentication system | Use a centralized identity and authentication system to govern your organization’s identities and authentications for cloud and non-cloud resources. | Azure Active Directory (Azure AD) is Azure’s identity and authentication management service. You should standardize on Azure AD to govern your organization’s identity and authentication in: Microsoft cloud resources, such as Azure Storage, Azure Virtual Machines (Linux and Windows), Azure Key Vault, PaaS, and SaaS applications. Your organization’s resources, such as applications on Azure, third-party applications running on your corporate network resources, and third-party SaaS applications. Your enterprise identities in Active Directory by synchronization to Azure AD to ensure a consistent and centrally managed identity strategy. For the Azure services that apply, avoid use of local authentication methods and instead use Azure Active Directory to centralize your service authentications. Note: As soon as it is technically feasible, you should migrate on-premises Active Directory-based applications to Azure AD. This could be an Azure AD Enterprise Directory, Business to Business configuration, or Business to consumer configuration. | Tenancy in Azure AD: https://docs.microsoft.com/azure/active-directory/develop/single-and-multi- tenant-apps How to create and configure an Azure AD instance: https://docs.microsoft.com/azure/active-directory/fundamentals/active- directory-access-create-new-tenant Define Azure AD tenants: https://azure.microsoft.com/resources/securing-azure-environments-with- azure-active-directory/ Use external identity providers for an application: https://docs.microsoft.com/azure/active-directory/b2b/identity-providers |
| IM-2 | Identity Management | 4.3 – Ensure the Use of Dedicated Administrative Accounts 4.5 – Use Multi-Factor Authentication for All Administrative Access | 5.4 – Restrict Administrator Privileges to Dedicated Administrator Accounts 6.5 – Require MFA for Administrative Access | AC-2: ACCOUNT MANAGEMENT AC-3: ACCESS ENFORCEMENT IA-2: IDENTIFICATION AND AUTHENTICATION (ORGANIZATIONAL USERS) IA-8: IDENTIFICATION AND AUTHENTICATION (NON- ORGANIZATIONAL USERS) SI-4: INFORMATION SYSTEM MONITORING | 8.2 8.3 | Protect identity and authentication systems | Secure your identity and authentication system as a high priority in your organization’s cloud security practice. Common security controls include: Restrict privileged roles and accounts Require strong authentication for all privileged access Monitor and audit high risk activities | Use the Azure AD security baseline and the Azure AD Identity Secure Score to evaluate your Azure AD identity security posture, and remediate security and configuration gaps. The Azure AD Identity Secure Score evaluates Azure AD for the following configurations: Use limited administrative roles Turn on user risk policy Designate more than one global admin Enable policy to block legacy authentication Ensure all users can complete multi-factor authentication for secure access Require MFA for administrative roles Enable self-service password reset Do not expire passwords Turn on sign-in risk policy Do not allow users to grant consent to unmanaged applications Use Azure AD Identity Protection to detect, investigate, and remediate identity-based risks. To similarly protect your on-premises Active Directory domain, use Defender for Identity. Note: Follow published best practices for all other identity components, including your on- premises Active Directory and any third party capabilities, and the infrastructure (such as operating systems, networks, databases) that host them. | What is the identity secure score in Azure AD: https://docs.microsoft.com/azure/active-directory/fundamentals/identity- secure-score Best Practices for Securing Active Directory: https://docs.microsoft.com/windows-server/identity/ad-ds/plan/security- best-practices/best-practices-for-securing-active-directory What is Identity Protection? https://learn.microsoft.com/en-us/azure/active-directory/identity- protection/overview-identity-protection What is Microsoft Defender for Identity? https://learn.microsoft.com/en-us/defender-for-identity/what-is |
More Details
- Intro: Microsoft cloud security benchmark introduction | Microsoft Learn
- Docu: Microsoft Cloud Security Benchmark | Microsoft Learn
- Repo: GitHub – MicrosoftDocs/SecurityBenchmarks: Supplemental information and resources for the Security Benchmark documentation available at https://docs.microsoft.com/azure/security/benchmarks/.
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Anoop C Nair has been Microsoft MVP from 2015 onwards for 10 consecutive years! He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is also a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.
