This post discusses 50% of Identities have access to Full Access as per Microsoft Security Report 2024. Recently, Microsoft’s 2024 State of Multicloud Security Risk Report has reconfirmed the essential requirement for strong control in the multiclouds.
With the new technology and options, many security issues may occur. Many companies use a mix of different technologies on various devices and clouds. This recent report on cloud security shows that it’s very important to secure multicloud systems and companies that use different cloud services together.
A multicloud system means using cloud services from multiple cloud service providers. It helps the business run separate projects in different cloud environments. The New report found that out of 51000 special access permissions given to users and services, only 2% were used, and many are used for risky environments.
This risky environment is crucial, which means there are too many unwanted permissions; if it is not controlled, it is badly affected, and malicious acts may occur. This blog post can overview Microsoft’s recent report on cloud security in 2024. This report shows insight into a whole year of actual data.
- Microsoft Introducing Multi-Tenant Organization Capabilities in Microsoft 365
- Windows Cloud Login App Conditional Access Policies in Entra ID
- Windows 365 Cloud PC Action Status Report

What is the Complexity of Threat Protection?
Threat protection is a very important factor in an organization. When organizations use different cloud services, it becomes more difficult to protect security. The cloud environment gives a chance to spread cloud workloads like data and services, through cloud environment and it has a high chance for cyber security.
1. There 2 types of cloud security called API protection and Storage protection
2. Suppose a compromised API link to data storage, API security and data storage protection cannot communicate or integrate effectively
3. The complexity between these different types of workload interactions can increase your attack surface
50% of Identities have access to Full Access as per Microsoft Security Report 2024
The use of Multiple cloud services is common in business nowadays. About 86% of them use different clouds because it’s more flexible and gives them more options. But, if thinks it’s ok? No, keeping the data secure and following the rules is very challenging. Microsoft has used data from its security tools to find the biggest security risks for using services like Azure, AWS, and GCP.
Integrating Security into DevOps
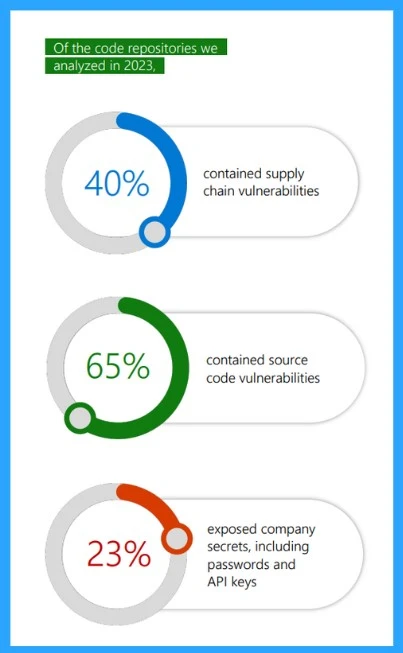
Hackers will always find a weak point in software, so security is very important at the beginning of the development process before making the code. Many companies do not give any importance to coding security, so what happens next? It exposes them to greater risk. In 2023, about 23% of places where code is stored had sensitive info like passwords and API keys exposed.
Download the Report – https://lnkd.in/dRVeDRf8
| Code Repositories Insights of 2023 | Info |
|---|---|
| 40% | contained supply 40% chain vulnerabilities |
| 65% | In 2023, 65% contained source code vulnerabilities |
| 23% | There are 25% exposed company secrets, including passwords and API keys |
Importance Of Common Vulnerabilities and Exposures
Common Vulnerabilities and exposures (CVEs) will prevent security issues during software development. However, finding and fixing CVEs is essential because they can cause issues during development and deployment.
A Cloud-Native Application Protection Platform (CNAPP) is a common platform for security administrators and developers. It will ensure strong security teams and manage security across various DevOps pipelines.
- CVEs stay in code for 58 days
- 57 days to fix high-severity CVEs
- 58 days for Medium-severity CVEs
- 64 days is for fixing low-severity CVEs
- 25% of high-risk vulnerabilities are exploited on the same day they’re published
- When security weaknesses happen, hackers take advantage of them.
- If 25% of the most dangerous CVEs are attacked within 24 hours after they’re known.

Risk-Based Approach with Attack Path Analysis
This is another important tool for protecting cloud-based apps and systems. Organizations that understand attack path analysis will remediate and find the main security issues. With the attack path analysis, you can track the attackers.
- You can uncover these hidden risks using a CSPM (Cloud Security Posture Management) tool.
- With this organizations can know how attackers could exploit weaknesses.
| Comprehensive Security Protocols |
|---|
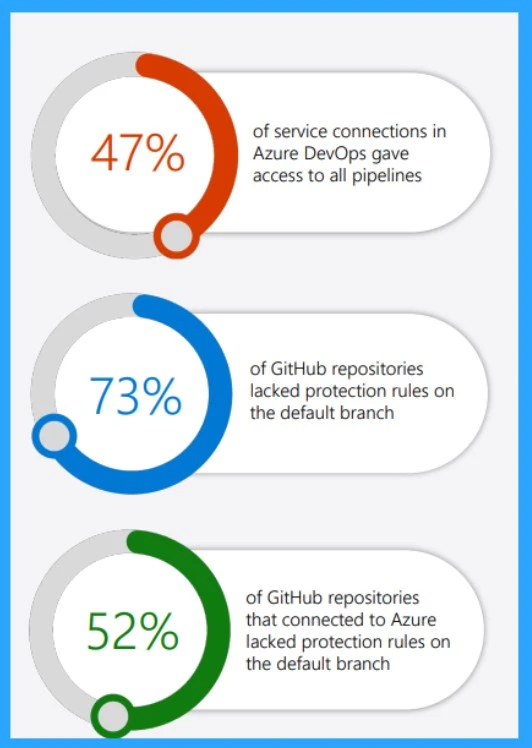
| 47% of service connections in Azure DevOps gave access to all pipelines |
| 73% of GitHub repositories lacked protection rules on the default branch |
| 52 % of GitHub repositories that connected to Azure lacked protection rules on the default branch |
Overview of Attack Path Analysis
Above, I mentioned that the Attack path is essential for organizations. This allows users to analyse how attackers exploit vulnerabilities. Without attack path analysis, organizations have no idea whether their data is exploited. Microsoft Security Exposure Management helps organizations find and prioritize potential security risks.
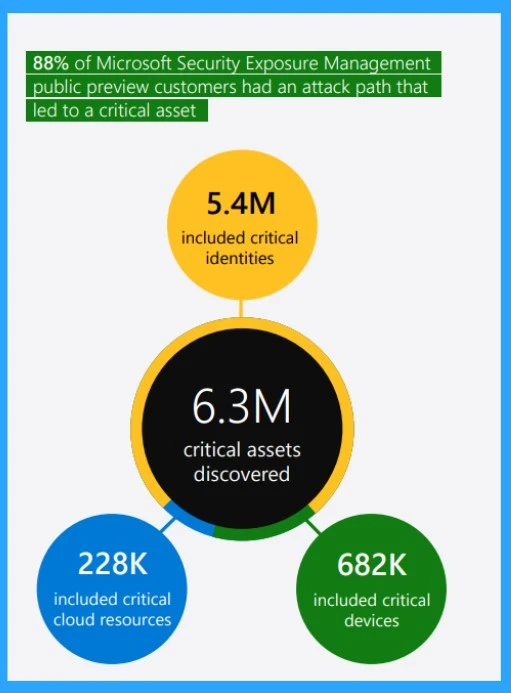
- Public preview customers have 88% on an attack path
- It will allow to a critical asset more than 6.3M critical assets to be discovered in this device identities, and Cloud resources are also included.
- In this chart, you can see that 5.4M critical identities, 228k critical cloud resources and also 682 critical devices are included
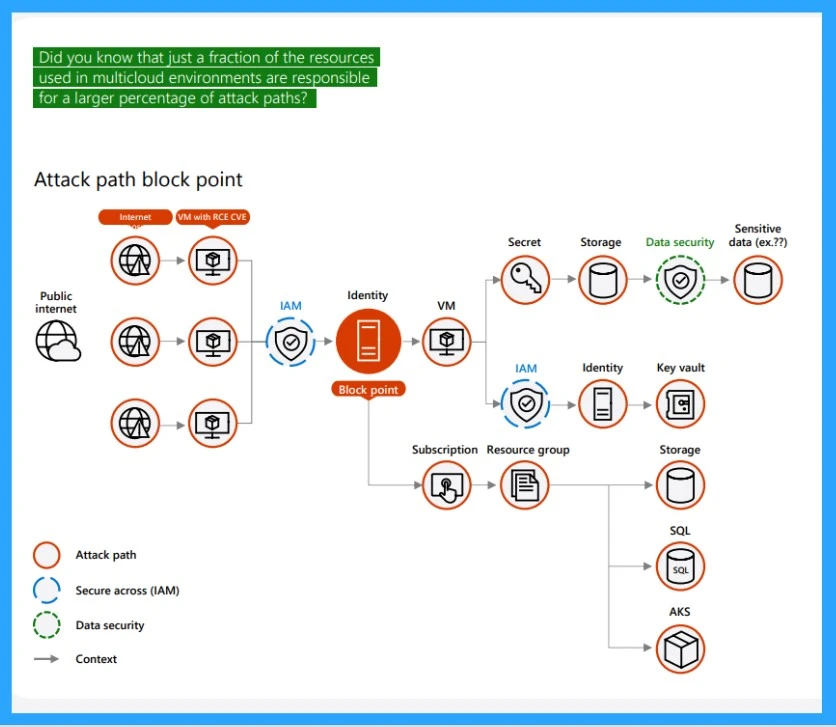
Understand The Attack Path Block Point
An attack path refers to the vulnerable sequence of steps that an attacker can exploit to gain unauthorized access to a system. A fraction of the resources is used in multicloud environments, which is the main issue with attack paths.
- In the screenshot below, you can see the diagrams that actually mean multiple attack paths that belong to the public internet
- There are 3 virtual machines (VMs) affected by a Remote code execution (RCE) vulnerability
- Advertisements may exploit these CVEs to access the identity and move laterally to access sensitive data, a key vault, or an AKS cluster
- To secure block points, organizations can use CNAPP
- New M365 Cloud.Microsoft.com URLs | New Subdomain URLs | Firewall Proxy changes Required
- High-Level Overview of Identity Protection in Microsoft Entra ID
- Passkeys Now Available in Microsoft Entra ID
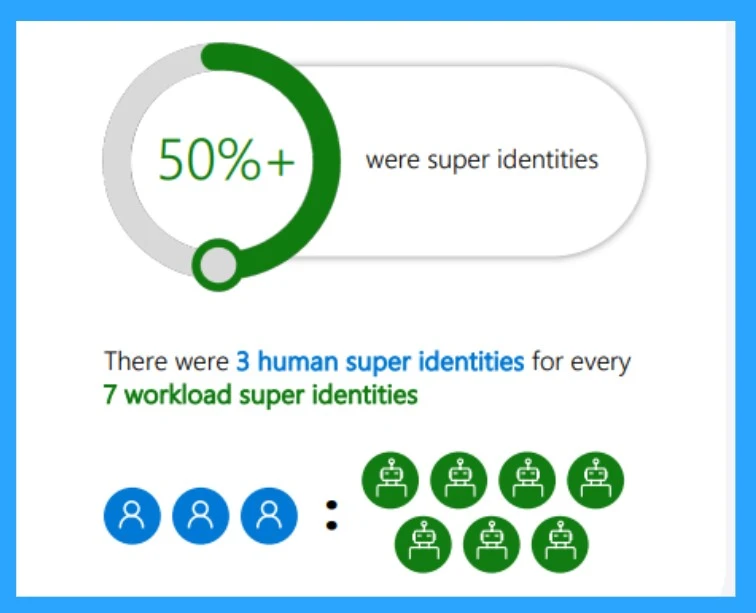
Unused Permissions Always Bring Risk
In 2023, Microsoft Entra Permissions Management granted 51000 permissions for human and workload identities. When more permissions were created, there was a chance for attacks even if the permissions were not active.
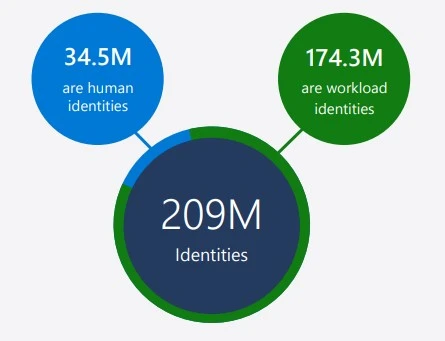
- 209M cloud identities identified in 2023
- There were 3 human super identities for every 7 workload super identity
Protecting Workload Identities
Managing Workload identities is an important factor in securing cloud environments. When a company increases workloads to the cloud, workload identities grow highly. Above, I mention that In 2023, Entra permission management identified 209M identities in cloud environments.
- In those environments, 34.5 M are human identities
- 173.4 M are workload identities
| Protecting workload Identities | Info |
|---|---|
| Workload identities | It is assigned to software workloads, including applications, microservices, and containers. |
| Inactive Identity | An identity that hasn’t logged in or used any of its permissions in the last 90 days |
| Permissions | The ability for an identity to perform an action on a resource |
| High-risk permissions | It can cause data leakage, service disruption or service degradation if misused or exploited |
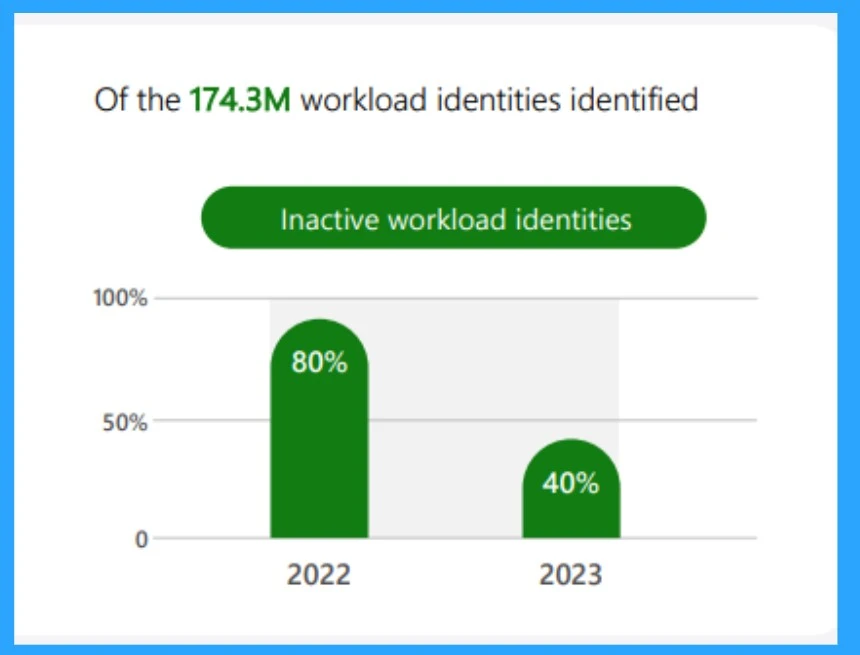
Manage Identities for Securing Access
In the management case, the highest active workloads occurred in 2022; compared to 2023, 40% of workload identities were identified. This clearly shows that permission management has the biggest role in organizations’ better managing inactive workload identities through increased visibility.
Reference
2024 State of Multicloud Security Report
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here –HTMD WhatsApp.
Author
Krishna. R is a computer enthusiast. She loves writing about Windows 11 and Intune-related technologies and sharing her knowledge, quick tips, and tricks about Windows 11 or 10 with the community.
