Let’s learn Microsoft Defender for Endpoint Onboarding Process using Intune. Intune provides a seamless device onboarding experience for Microsoft Defender for Endpoints. By leveraging the power of Intune, you can effortlessly establish a connection between your devices and Microsoft Defender for Endpoints. Learn Intune Integration with Microsoft Defender for Endpoint.
This process involves creating specific policies within Intune and deploying them to the desired devices. To achieve seamless integration between Intune and Microsoft Defender for Endpoint, the first step is to navigate to the Microsoft Defender portal. Once there, you can enable the Microsoft Intune connection to bridge the two platforms.
By enabling this connection, you unlock a multitude of benefits. It allows you to manage policies and devices with enhanced controls directly from within the Intune console. This integration empowers you with more advanced and granular management capabilities, ensuring comprehensive security across your organization’s devices.
Microsoft 365 Defender is a unified solution that works across Endpoints, Identities, Emails, Apps, and Cloud Applications. Microsoft Defender for Endpoint (MDE) is an enterprise endpoint security platform. MDE integrates with Intune to support End to End Device Management.
- Secure Android Devices using Microsoft Defender for Endpoint in Intune
- Latest Microsoft Defender Antivirus Configuration Policy Settings in Intune
What is Intune Integration with Microsoft Defender for Endpoint?
Intune Integration with Microsoft Defender for Endpoint refers to the seamless connection and collaboration between Microsoft Intune, a cloud-based device management platform, and Microsoft Defender for Endpoint, an advanced endpoint security solution.
Video – Microsoft Defender for Endpoint Onboarding Process using Intune
Welcome to the second part of our video series on Microsoft Defender for the Endpoint onboarding process using Intune. Suppose you haven’t had a chance to watch the first part. In that case, we highly recommend checking out the previous video, discussing the seamless integration of Intune with Microsoft Defender for Endpoint.
In this episode, we’ll dive deeper into the specific steps involved in onboarding Windows devices to Microsoft Defender for Endpoint through Intune. Following this process can enhance your organization’s security posture and gain valuable insights into potential threats.
Microsoft Defender for Endpoint Onboarding Process using Intune
The Windows Defender Advanced Threat Protection (WDATP) configuration service provider (CSP) empowers IT administrators to seamlessly onboard, configure, assess the health status, and offboard endpoints for WDATP, thereby enabling the robust endpoint detection and response capability of Microsoft Defender for Endpoint.
- With the WDATP CSP, IT admins can efficiently onboard devices onto the Microsoft Defender for Endpoint platform.
- This process establishes a secure connection between the devices and the cloud-based security service, enabling real-time threat detection, proactive monitoring, and response capabilities.
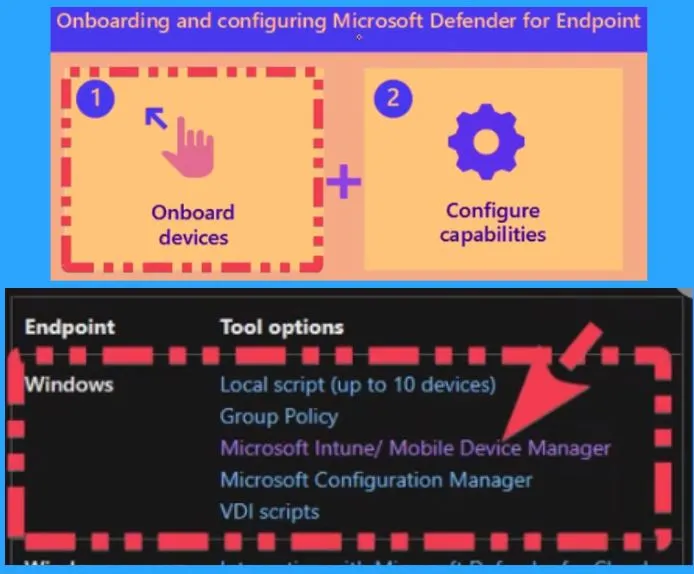
Let’s check how to use MS Defender for the endpoint Onboarding process using Intune. Log in to the Microsoft Intune admin center to create an onboarding policy for MD onboarding from endpoint security.
- Select the Endpoint security tab from the MS Intune admin center
- Select Endpoint Detection and Response from the Endpoint Security tab
- Select Create Policy option from the below window
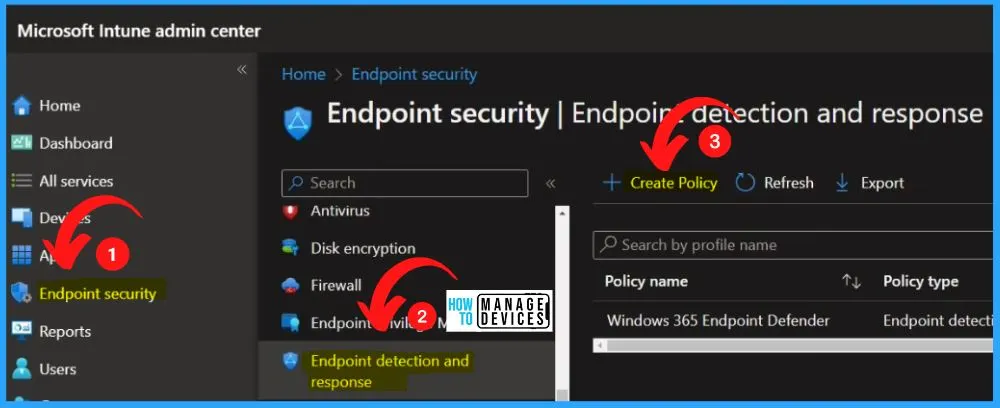
Microsoft Defender for Endpoint detection and response capabilities provides advanced attack detections that are near real-time and actionable. Security analysts can prioritize alerts effectively, gain visibility into the full scope of a breach, and take response actions to remediate threats.
- Select Platform as Windows 10, Windows 11, and Windows Server
- Select profile as Endpoint detection and response
- Select the Create button from the below window
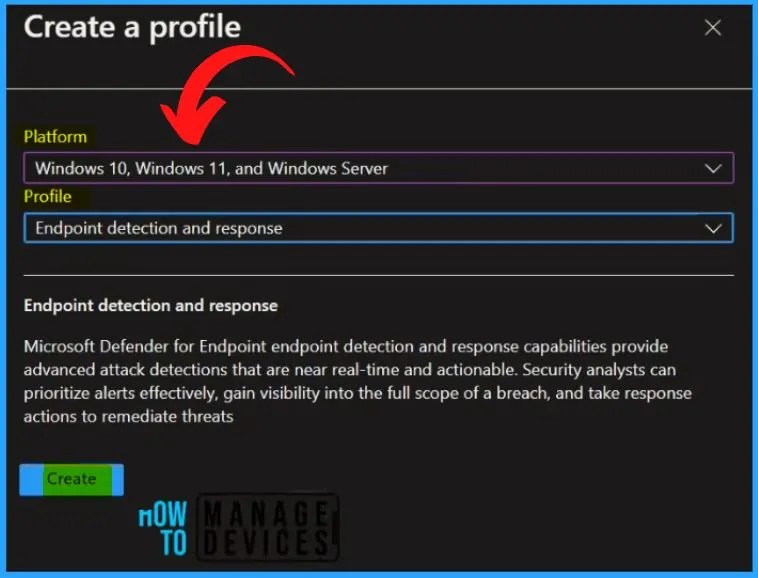
Enter the Name and Description as MDE Onboarding package for HTMD Windows on the Basic tab. Select the Platform as Windows 10 and later. Click the Next button from the below window.
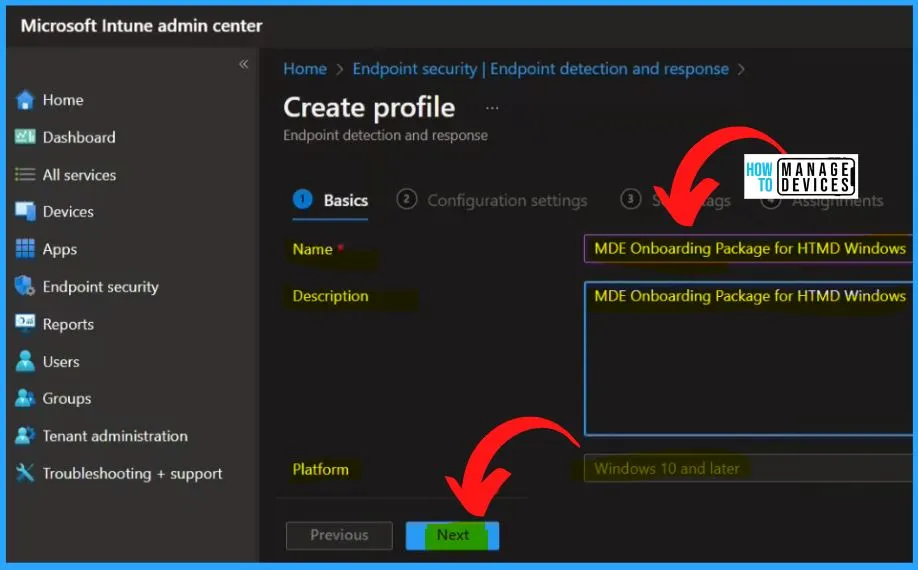
The below window shows the Configuration Settings, the main configuration settings page. It includes Microsoft Defender for Endpoint options such as Microsoft Defender for Endpoint client configuration package type, Sample sharing, etc.
| Microsoft Defender for Endpoint Options | Used to |
|---|---|
| Microsoft Defender for Endpoint Client Configuration Package Type | Microsoft Defender for Endpoint endpoint detection and response capabilities provide advanced attack detections that are near real-time and actionable. Security analysis can prioritize alerts effectively, gain visibility into the full scope of a breach, and take response actions to remediate threats |
| Sample Sharing | Return or set Windows Defender Advanced Threat Protection Sample Share configuration parameter: None – 0, All – 1. |
- Select Microsoft Defender for Endpoint client configuration package type as Auto from Connector.
- Select Sample sharing as All
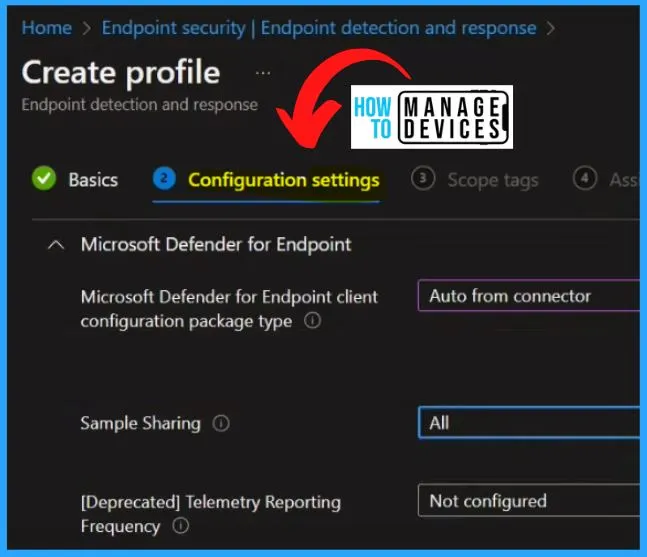
Scope tags are crucial in determining the visibility of objects for administrators within Microsoft Intune. They ensure that every object in the Intune environment has at least one scope tag assigned to it. By selecting the default scope tags, you can proceed to the next step by clicking the “Next” button in the window provided.
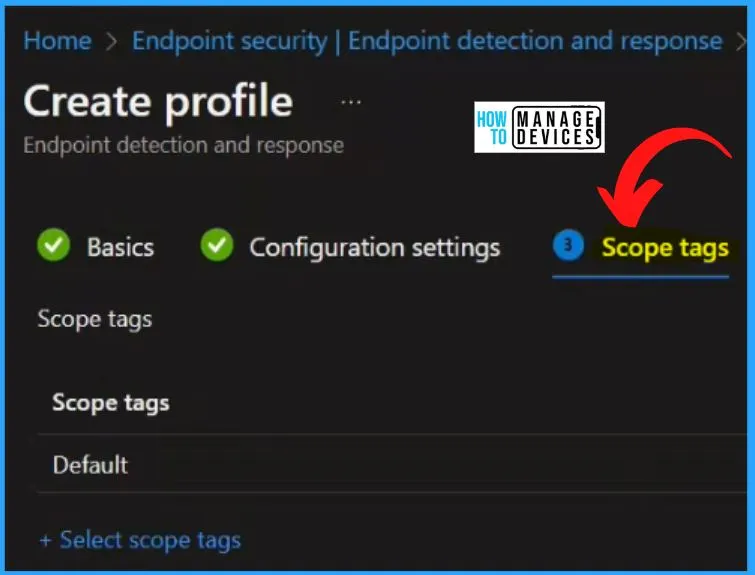
You can add all the Included and excluded groups in the Assignments section. You can easily add a group by clicking the Add Groups option from the below window.
The Review + Create tab helps you to show all the details, such as name, Description, configuration settings, scope tags, assignments, etc. Click the Create button from the below window.
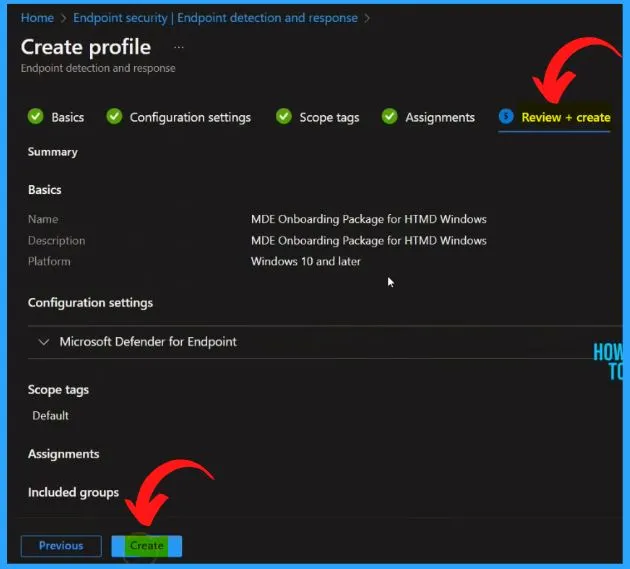
The below window shows that the policy is created successfully. It also helps you to show the details such as policy name, Policy type, assigned details, platform, target, and last modified details, etc.
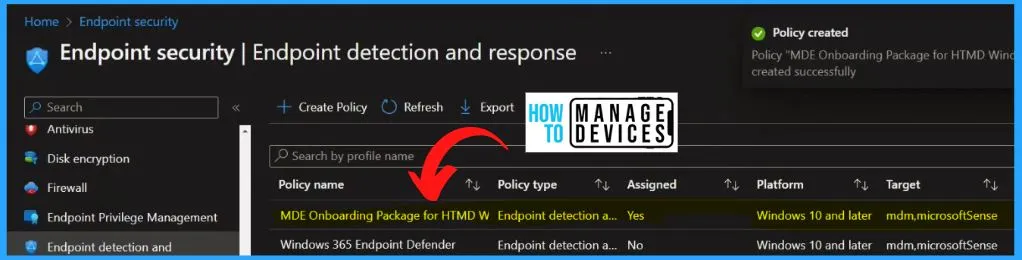
Intune Reports for MDE Onboarding Package for HTMD Windows
The below window shows the Intune Reports for MDE Onboarding Package for HTMD Windows. The device assignment status report shows all the devices targeted by the policy, including devices in a pending policy assignment state.
- By checking the device and user check-in status, they can verify the successful application of the policy.
- For a more comprehensive view, clicking on “View Report” provides access to additional details.
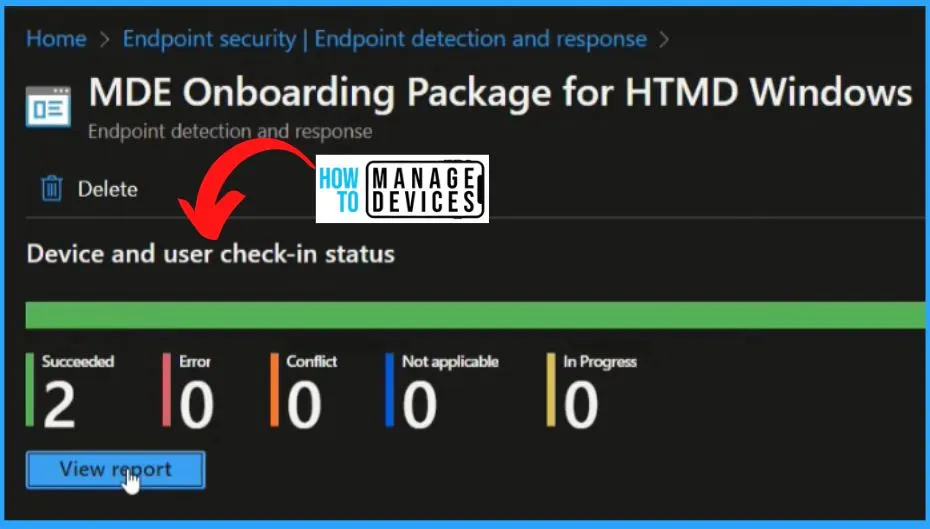
The Device is Onboarded Successfully to MS Defender Endpoint
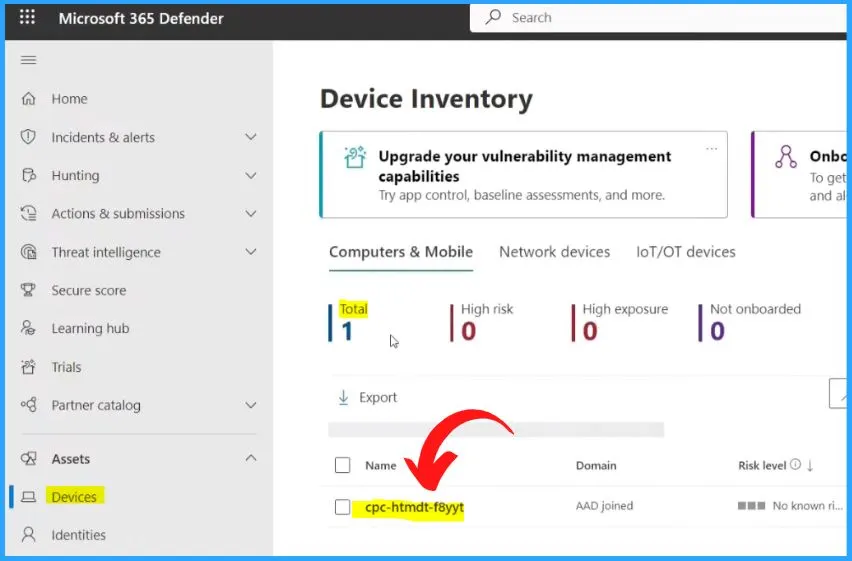
Login to Microsoft 365 Defender portal. You can go to the Devices tab under Assets on the left side of the Microsoft 365 Defender window. Here you can see the onboarded device. The Total number is 1. The Onboarding device shows the following details.
| Name | Domain | Risk level | Exposure Level | OS Platform | Windows Version | Sensor Health State | Onboarding Status | Last Device Update | Tags |
|---|---|---|---|---|---|---|---|---|---|
| Cloud PC | AAD joined | No known risk | Medium | Windows 11 | 22H2 | Active | Onboarded | Shows the last Updated Date | Shows the scope tags |
WindowsAdvancedThreatProtection CSP – Windows Client Management | Microsoft Learn
Author
About Author – Vidya is a computer enthusiast. She is here to share quick tips and tricks with Windows 11 or Windows 10 users. She loves writing on Windows 11 and related technologies. She is also keen to find solutions and write about day-to-day tech problems.
