Let’s check Endpoint Security Reports for Tenant Attached Devices in Intune. Endpoint security reports cover a range of security aspects, such as device compliance, inventory, security, and threat protection.
Endpoint security reports in Intune provide organizations with valuable insights into the security of their tenant-attached devices. These reports can help organizations identify potential security threats, such as malware infections or unauthorized access attempts, and take corrective action to protect their networks and data.
You need endpoint security reports to stay up-to-date on the security status of networks and devices. Specifically, tenant-attached devices in Intune necessitate diligent surveillance to check company policies.
By regularly reviewing endpoint security reports for tenant-attached devices in Intune, you can proactively identify and address potential security issues before they become major problems. This can help organizations protect their networks and data, as well as maintain compliance.
If you have not yet attached to the SCCM cloud Tenant Attach, In the Configure upload tab, select Upload to Microsoft Endpoint Manager admin center, you can sign up for this function when configuring the Cloud Attach wizard. After enabling in SCCM, the data will become accessible after 4 hours.
- New Built-in LAPs Client For Windows 11 And 10 | Conflict With Old Version Of LAPs
- Easy Method To Force Safari Patch Updates On MacOS Using Intune
Endpoint Security Reports for Tenant Attached Devices in Intune
To check endpoint security reports for tenant-attached devices in Intune, follow these steps: From here, you can view different endpoint security reports such as device compliance, device inventory, device security, and threat protection reports. Choose the report you wish to view.
- Sign in to the Microsoft Intune admin center https://intune.microsoft.com/.
- Click on the Endpoint security, and navigate to Antivirus.
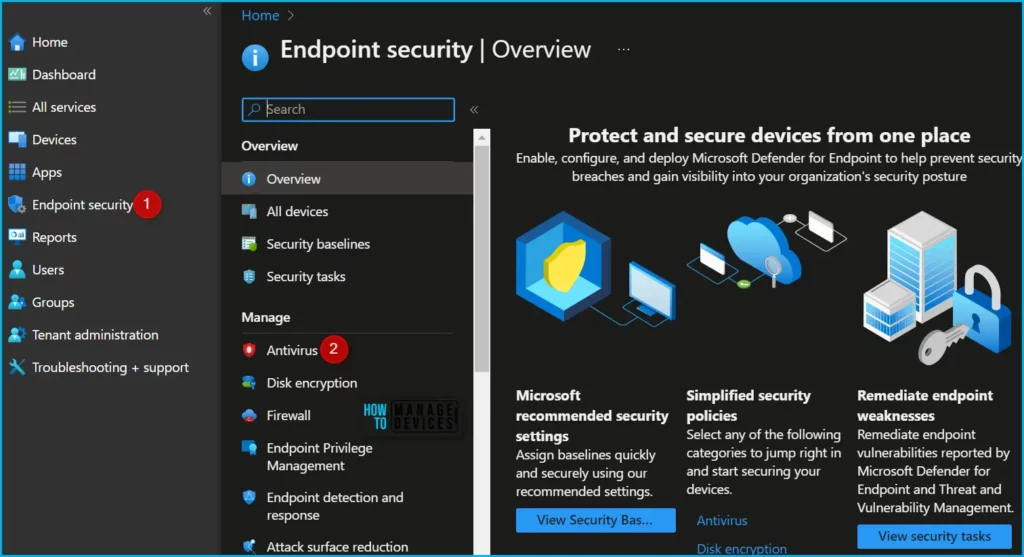
The Antivirus summary aggregates and operational reports to help you monitor the devices that need your attention.
The Summary tab provides aggregate information for the count of devices with a given threat agent status and the active malware category. With SCCM 2303 release, this chart will also include data from the tenant attached devices.
Both aggregates show the top eight categories (Active malware across categories), which correspond to the operational reports on the other tabs. If there are no devices in any of the states, there will be no results to display.
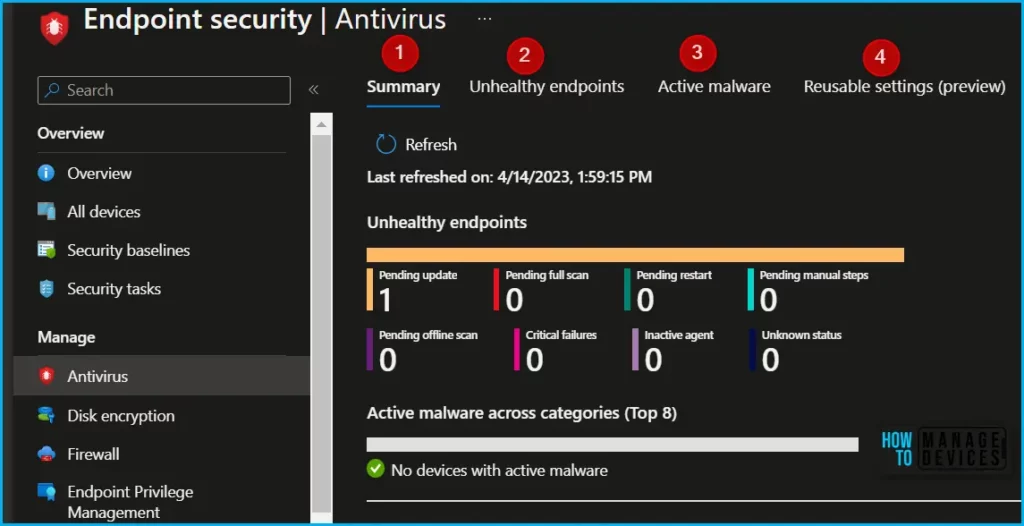
To view the operational report for the thread agent status on devices and users that require attention, click on the “Unhealthy endpoints” report.
This report provides information on whether malware protection, real-time protection, and network protection are enabled or disabled for each device. Additionally, the report includes extra columns with more detailed information to help identify the next steps for troubleshooting.
You can filter the devices based on the management agent by using the “Managed By” column, which includes MDM, Co-managed, or ConfigMgr (tenant attached devices), and you can export the report in CSV format for further analysis.
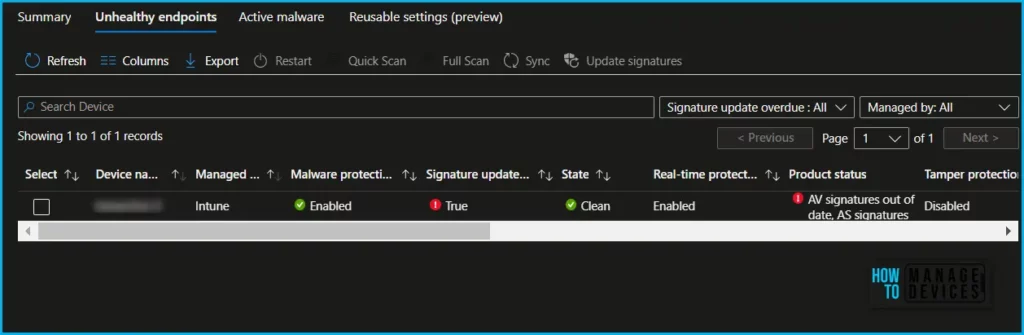
The Active Malware tab allows you to view the operational report to see the list of devices and users with active malware and includes details of the malware category.
Here you can access the Active Malware report to view the operational report that lists devices and users with detected malware, including details on the malware category. This report shows the type of malware, the state of the device, and the number of instances of malware found on the device.
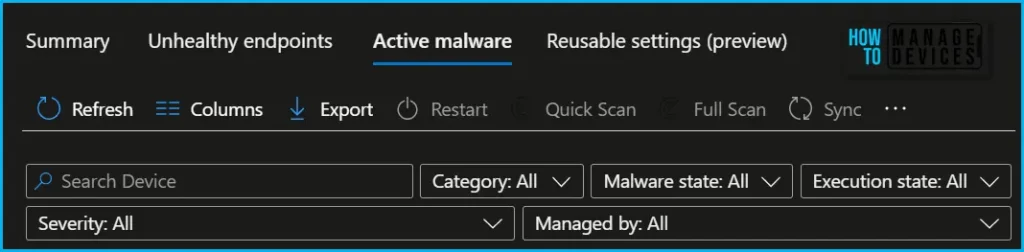
This shows the malware state and counts of malware found on the device. You can now filter the devices list based on Managed by (MDM, Co-managed, ConfigMgr and many more) and take remote actions, including restart, quick scan, and full scan, or update signatures to help remediate your devices.
Author
About Author – Jitesh, Microsoft MVP, has over six years of working experience in the IT Industry. He writes and shares his experiences related to Microsoft device management technologies and IT Infrastructure management. His primary focus is Windows 10/11 Deployment solution with Configuration Manager, Microsoft Deployment Toolkit (MDT), and Microsoft Intune.
