Windows 10 Conditional Access with Azure AD Join Intune MDM Auto Enrollment? Windows 10 conditional access is an excellent feature for BYOD scenarios. We wanted to provide BYOD users with an OOBE (Out Of Box Experience) with AAD join and Intune auto-enrollment.
Once the user can log in with their cooperate credentials (using AAD login) to the brand new device, which is not joined to on-prem AD, the device is a complaint as per corp security policies. The user should allow access to corps mail without any blockage (or without any VPN connection).
We struggled to get this working for Windows 10 RTM version 10240. Conditional access didn’t work with the RTM version of Windows 10, but It worked well with Windows 10 versions 10175 and TH2 10586.
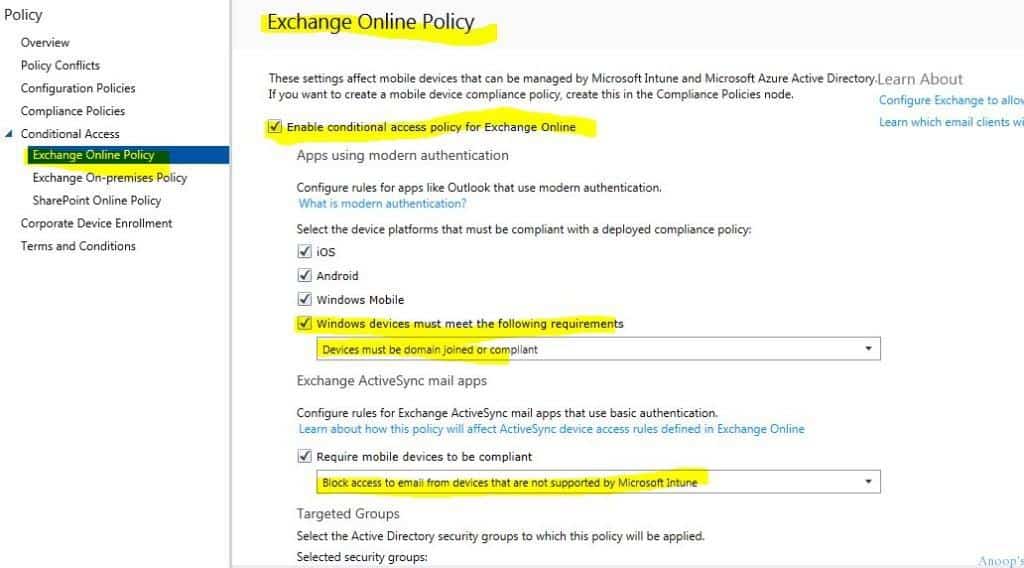
We tested Windows 10 conditional access with different AAD + MDM (Intune) join scenarios. From the tenant side (Intune console), we enabled Conditional Access for Exchange online, as noted in the screenshot below.
Table of Contents
- Filter Application Using Azure AD Conditional Access Policy
- Easiest Method To Enable MFA For Admins Using Azure AD Conditional Access
- Intune Filters For Assigning Apps Policies And Profiles In Intune Portal
Windows 10 Conditional Access with Azure AD Join Intune MDM Auto Enrollment Enforce Policies
Discuss the Windows 10 Conditional Access with Azure AD Join Intune MDM Auto Enrollment Enforce Policies. More details about Azure AD Join here (Azure AD Join: What happens behind the scenes?).
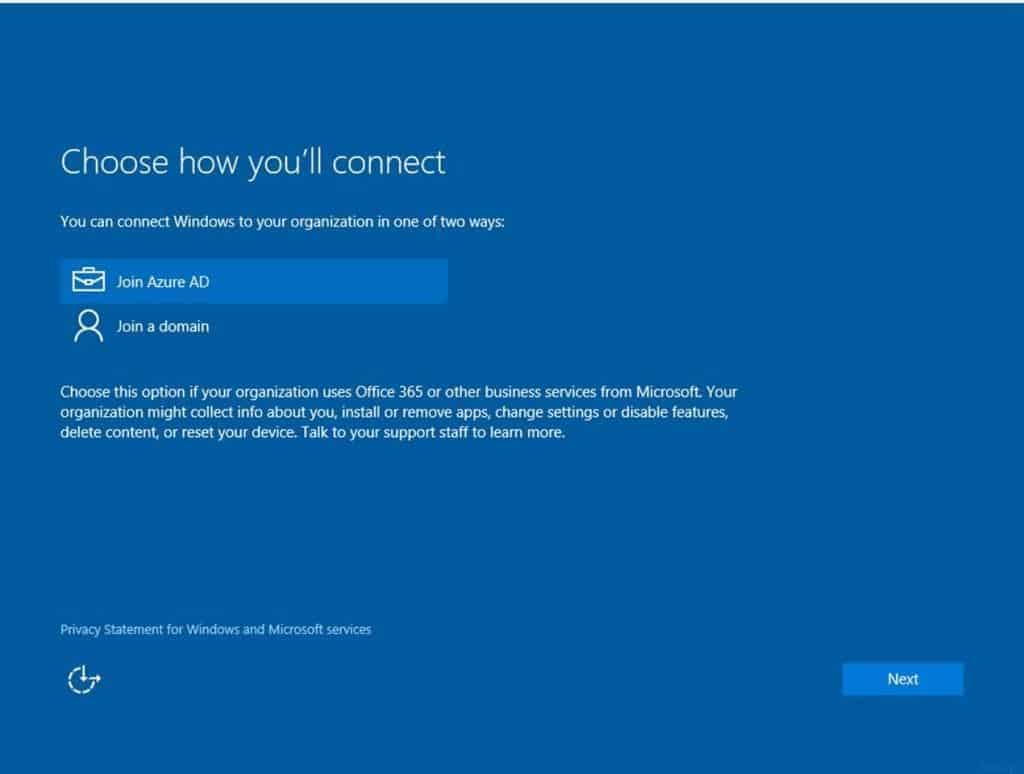
We wanted to give BYOD users an OOBE (Out Of Box Experience) with AAD join and Intune enrollment. Once the users can log in with their cooperate credentials and the device is a complaint, they should be able to access corps data/mail without any blockage.
| Choose How You Will Connect |
|---|
| Join Azure AD |
| Join a Domain |
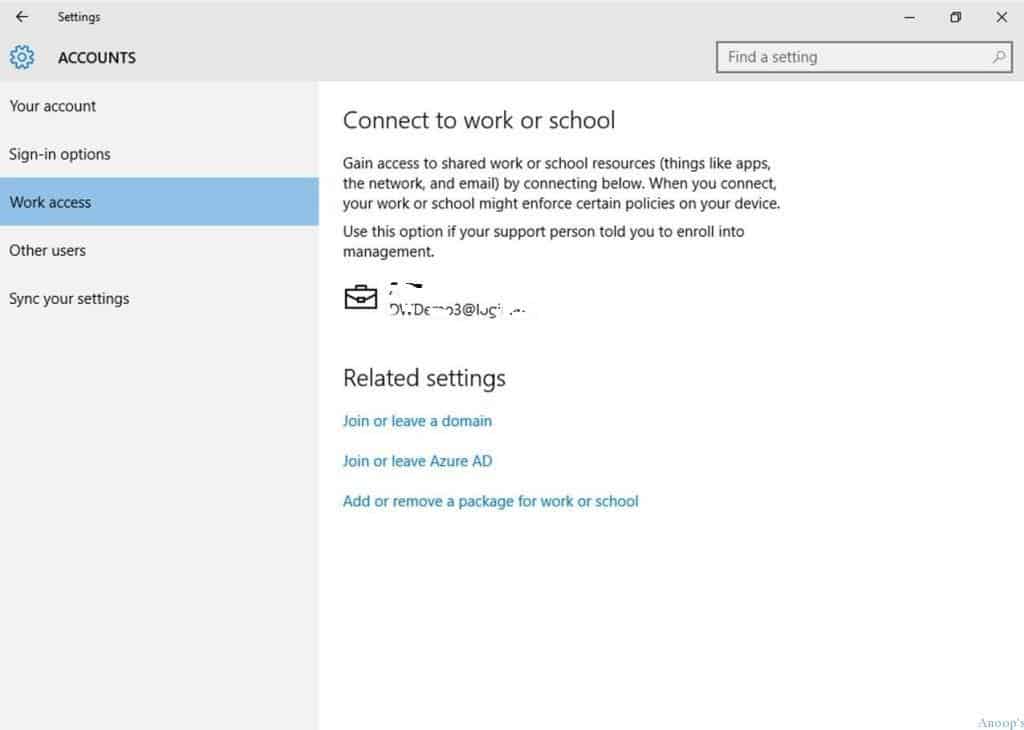
We can confirm whether the device has successfully joined AAD and is enrolled in MDM (Intune) by checking the work access option on the Windows 10 device’s settings page.
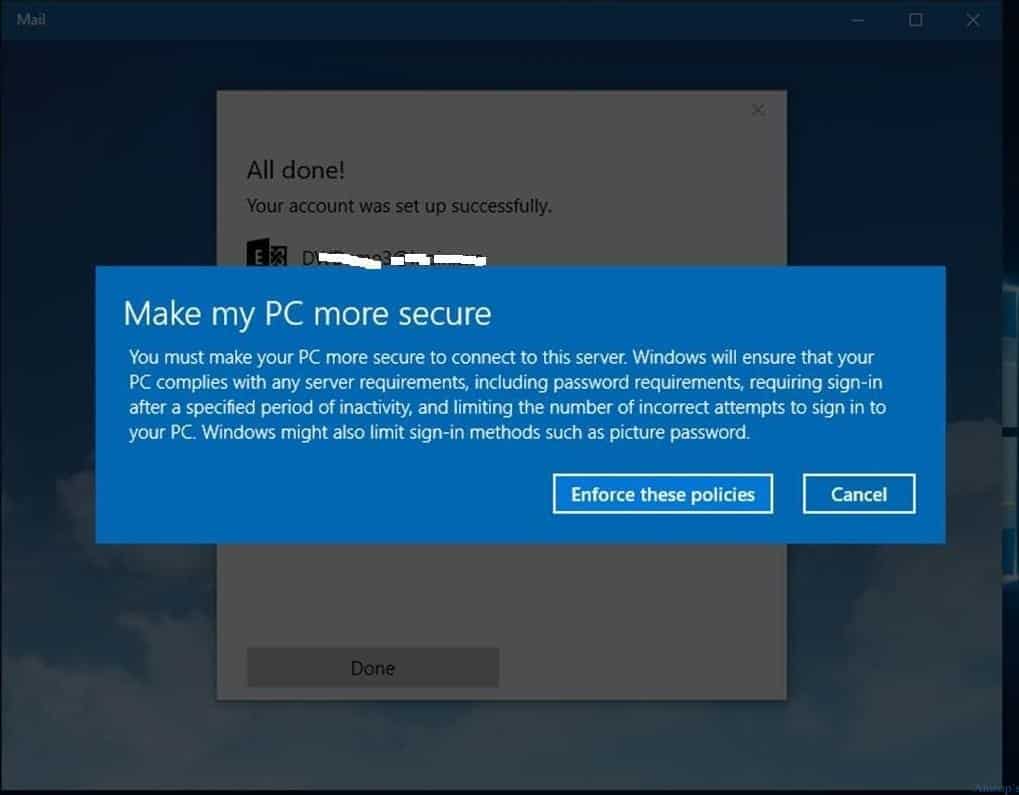
We must ensure compliance policies are applied to the Windows 10 device to secure corporate environment data. Once Intune tries to apply compliance policies on the device, we will get a popup stating that we need to enforce these policies. We may get mail access once MDM (Intune) policies are applied to the Windows 10 device.
When using Office 2013 on a Windows 10 machine for conditional access, you need to enable modern authentication for Outlook. We must do this using the registry keys mentioned in the following document.
Modern authentication is also enabled for Office 2016 (Outlook 2016), so conditional access for Windows 10 with AAD and Intune will work seamlessly for the Office 2016 version.
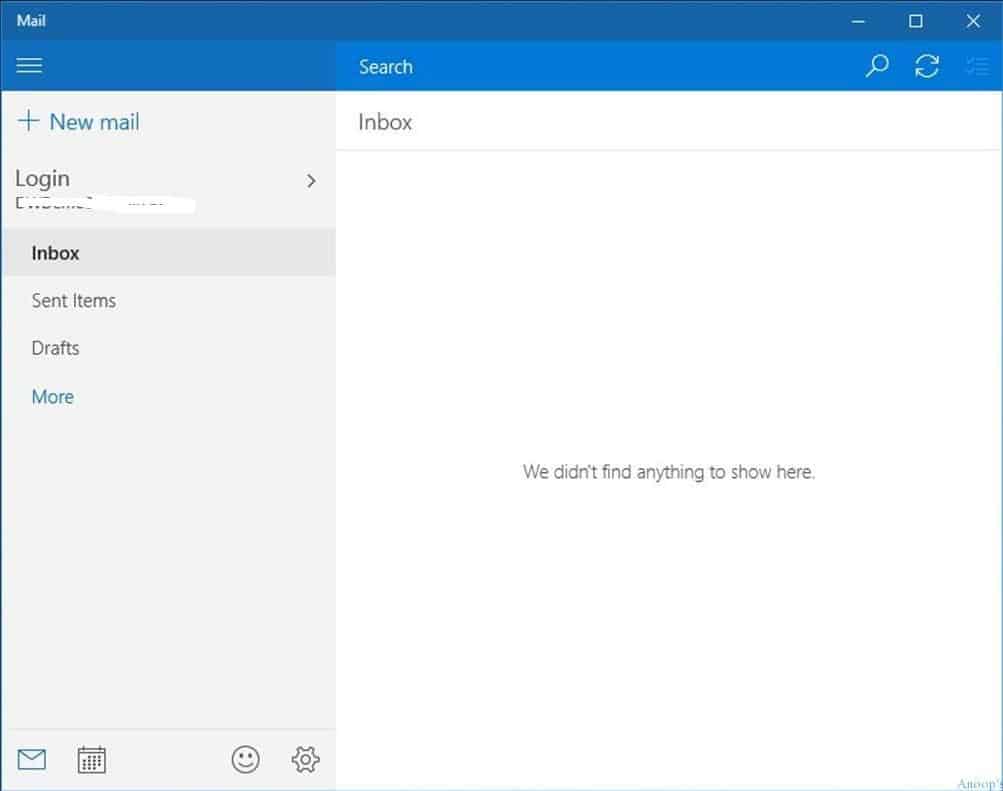
When you use a native mail application (of Windows 10) for corporate mail access, you don’t need to make any unique settings. The default mail app in Windows 10 will work with conditional access.
Resources
Learn Microsoft Intune Related Posts Real World Experiences (anoopcnair.com)
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here. HTMD WhatsApp.
Author
Anoop C Nair is Microsoft MVP! He is a Device Management Admin with more than 20 years of experience (calculation done in 2021) in IT. He is a Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc.
