Let’s understand how to perform Intune Enrollment Using Group Policy. This is a way to automatically enroll hybrid Azure AD-joined Windows devices in Intune. You can use the Intune (MDM) enrollment group policy with Hybrid Azure AD-joined and domain-joined + Azure AD-registered devices.
I’ve explained the manual process of Windows 10 Intune enrollment for the BYOD scenario and the Windows 10 Azure AD Join Manual Process—CYOD scenario. For more information, refer to my detailed guide to Learn Intune Device Management (Intune Starter Kit).
The Intune group policy is used mainly for AVD (Azure Virtual Desktop) scenarios. It would be best to use this group policy to enrol AVD VMs in Microsoft Endpoint Manager(MEM) Intune.
The Intune Group policy from Windows 10 and Windows 11 ADMX templates is here to help you.
Table of Contents
Video Intune Group Policy for Enrollment
The following video teaches how to create a group policy to enrol Windows 10 devices into Intune automatically.
- Intune Supported Enrollment Methods for Windows iOS Android MacOS Linux ChromeOS
- Migrate Group Policies GPOs to Intune Settings Catalog policy
Prerequisites – Intune Enrollment using Group Policy
Let’s understand the prerequisite for automatic Intune enrollment of Windows 10 devices.
- Ensure the user who enrols in the device has a valid Intune license.
- Ensure that auto-enrolment is activated for those users who enrol the devices into Intune.
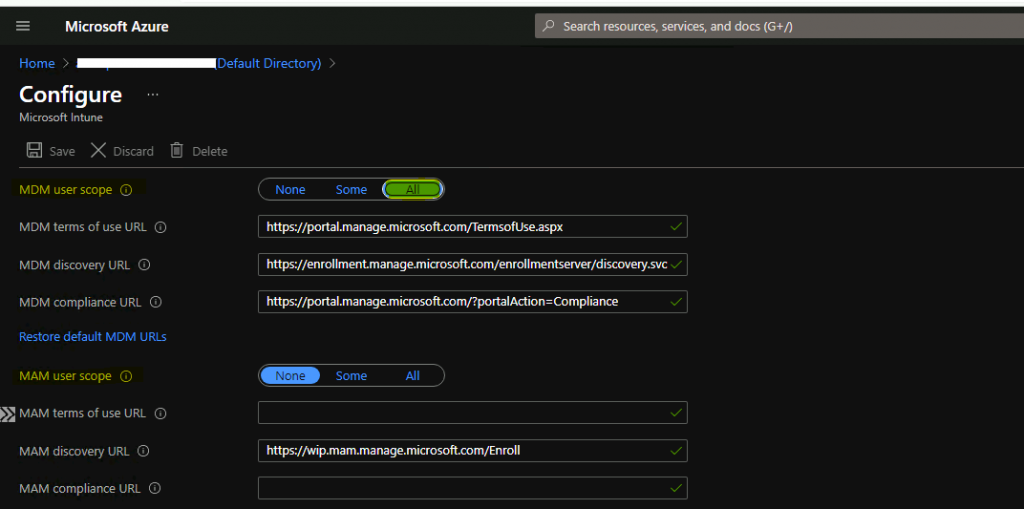
Ensure that the device OS version is Windows 10, version 1709, or later.
- Auto-enrollment into Intune via Group Policy is valid only for hybrid Azure AD joined devices.
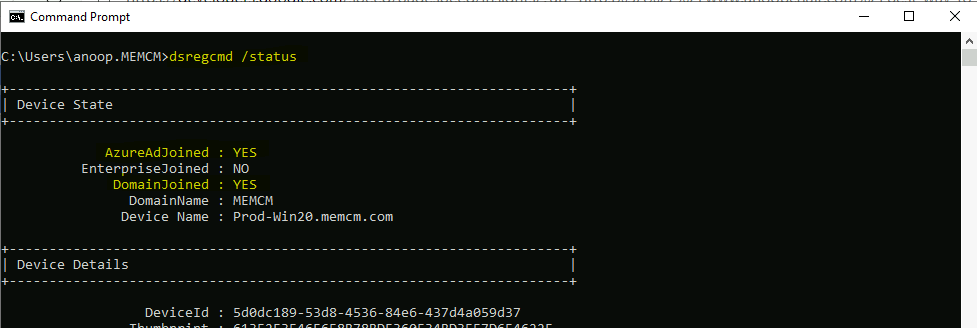
- Run the following command to confirm dsregcmd /status
- AzureAdJoined: YES
- DomainJoined: YES
- Ensure you can configure Group Policies in the on-prem Active Directory.
- Make sure Windows 10 ADMX is installed to enable the group policy.
Configure Intune Group Policy for Enrollment for AVD VMs
Now, let’s consider implementing the Group Policy for automatic Intune enrollment. Hopefully, you have already taken care of all the prerequisites explained above. Otherwise, the MDM group policy will not help you enrol the Windows 10 devices into Intune management.
Launch Group Policy Management (gpmc. msc) from the start menu (Domain controller or any other remote management server).
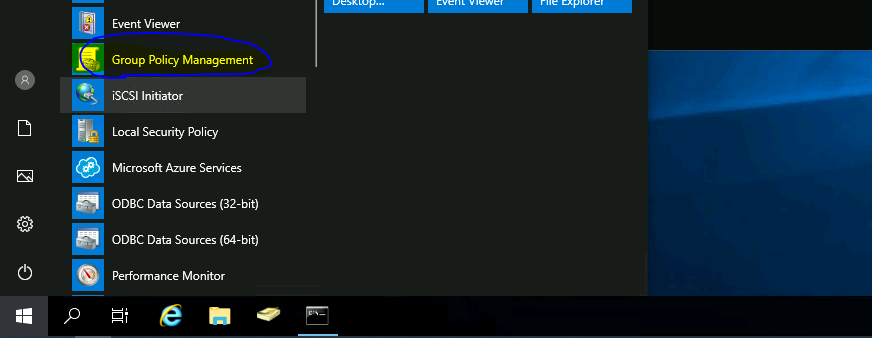
- Right-click on Group Policy Object and Select NEW.
NOTE! – Make sure Windows 10 ADMX is installed to GPO as mentioned in the above prerequisite section.
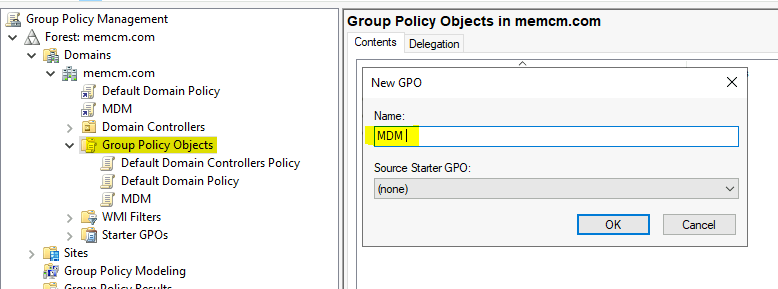
Enter the name of the GPO that you want to deploy to Windows 10 clients for Intune enrollment.
- Name = MDM
- Click OK
Right-click on the newly created policy MDM and select Edit.
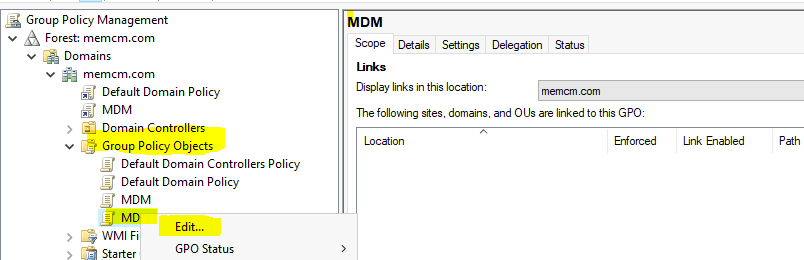
Navigate to policy nodes as shown in the below screenshot.
Computer Configuration – Policies –Administrative Templates: Policy Definitions –Windows Components.
NOTE! If you don’t install Windows 10 ADMX, you won’t be able to see the group policy we are looking for.
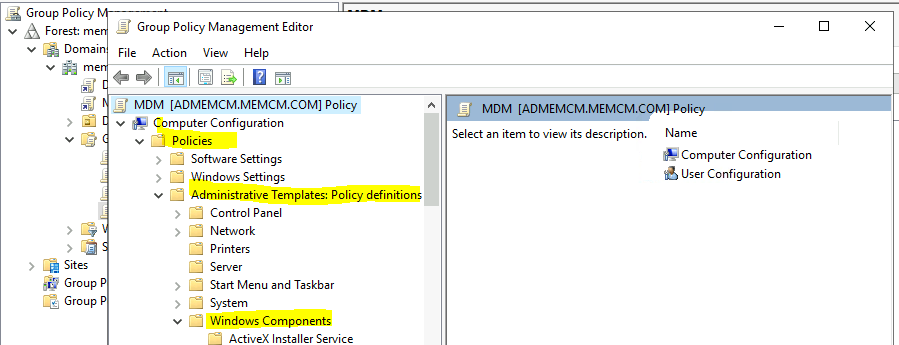
- Scroll down until you find the MDM folder.
- Click on the MDM folder.
- Select the following policy from the policies displayed on the right pane of MMC.
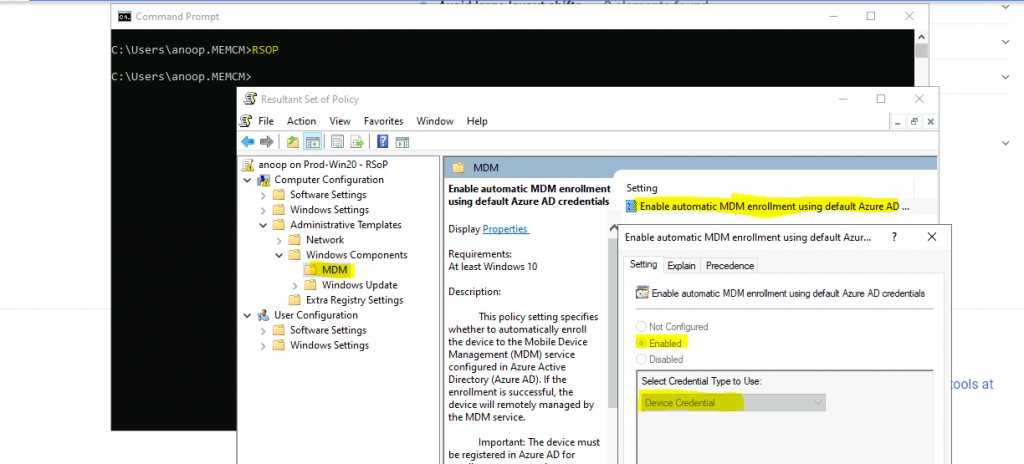
- Double-click on Enable Automatic MDM Enrollment Using Default Azure AD Credentials.
This policy specifies whether to automatically enrol the device in the Mobile Device Management (MDM) service configured in Azure Active Directory (Azure AD). If the enrollment is successful, the MDM service will manage the device remotely.
- Important: The device must be registered in Azure AD for enrollment to succeed.
- If you do not configure this policy setting, automatic MDM enrollment will not be initiated.
- If you enable this policy setting, a task is created to initiate device enrollment to the MDM service specified in the Azure AD.
- If you disable this policy setting, MDM will be unenrolled.
- Click the Enable option to enable the Intune enrollment option for Hybrid AD joined Windows 10 devices.
- Selecting the Credential Type to Use option is essential. The default option is to use User Credentials.
NOTE from Microsoft Docs – In Windows 10, version 1903, the MDM.admx file was updated to include an option to select which credential is used to enroll the device. Device Credential is a new option that will only have an effect on clients that have installed Windows 10, version 1903, or later. The default behavior for older releases is to revert to User Credential. Device Credential is not supported for enrollment type when you have a ConfigMgr Agent on your device.
I selected Device Credentials, and it worked fine with the latest version of Windows 10 2004 and the ConfigMgr 2010 client. However, I’m unsure whether some updates are missing from Microsoft Docs.
- Click OK to complete the Group policy creation.
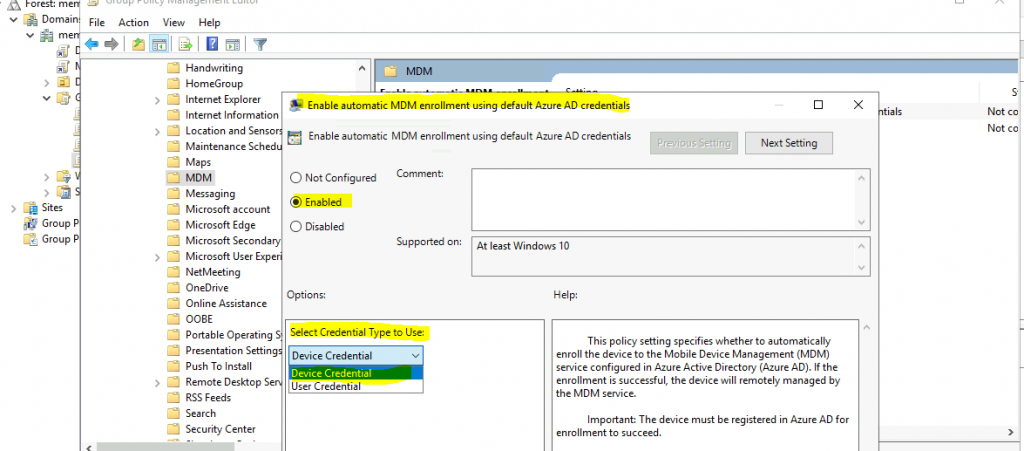
Assign Intune Enrollment Group Policy to OU
I have created the group policy for MDM/Intune enrollment. The next step is to link the group policy to an Organizational Unit (OU) in Active Directory. I want to assign this MDM/Intune enrollment GPO to only one OU, AVD.
- Launch the command prompt and type in DSA.MSC (Assuming you can create OU and know what you are doing).
- Right-click Domain and select New – Organizational Unit.
- Enter the Name of the OU = WVD.
- Click OK to complete the OU creation process.
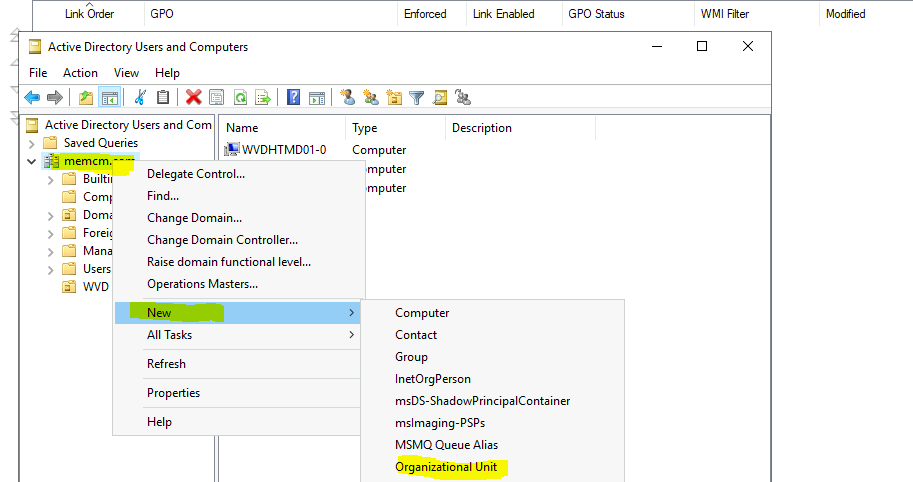
Go back to the Group Policy Management console.
You can see a new OU there called WVD.
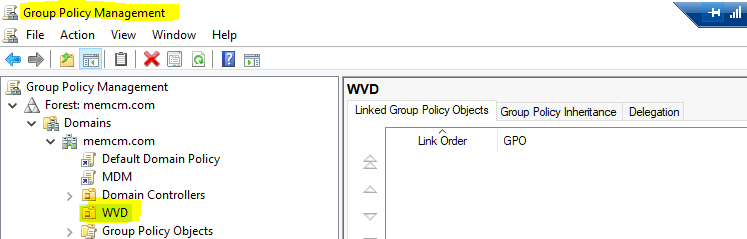
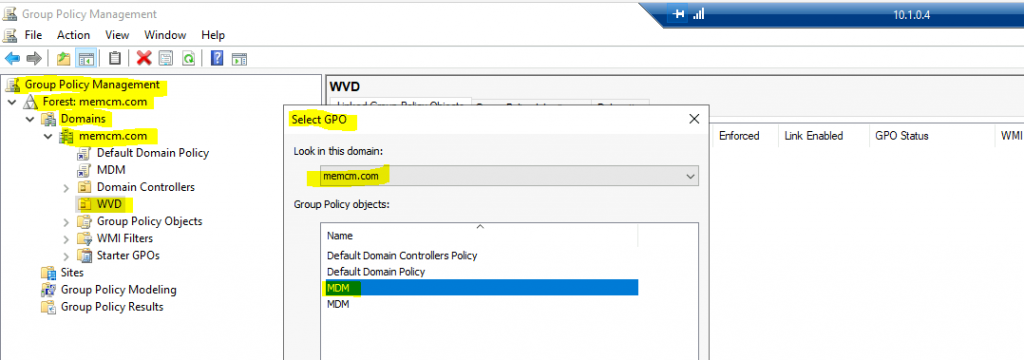
Right-click on the new OU in the Group Policy management console. Select Link an Existing GPO option.
Select the MDM group policy from the list. Click OK to complete the GPO assignment.
Results
Once the Windows 10 MDM/Intune enrollment group policy is applied on the device, you can see the Intune policy details on the accounts page from the settings page.
- Click on the Info tab to check Intune policies.
You can also run RSOP to confirm the MDM/Intune Group policy.
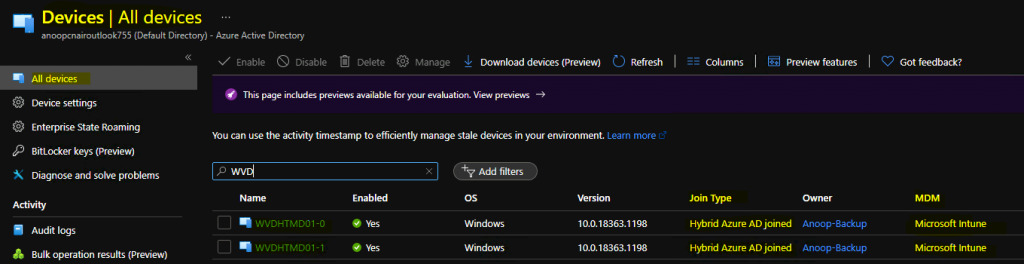
You can confirm this Hybrid AD Join + Windows 10 Intune enrollment from portal.azure.com – Azure Active Directory.
Resources
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here – HTMD WhatsApp.
Author
Anoop C Nair has been Microsoft MVP for 10 consecutive years from 2015 onwards. He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.

Nice article, I have a query. Domain network will need to white list all Intune urls n ports for this to be successful.
Yes, please follow article
https://docs.microsoft.com/en-us/mem/intune/fundamentals/intune-endpoints
whether it is applied or personal vdi devices or pooled as weel
Yes this works for both single and multi-session AVDs.
is it the same thing using azure connect and enable device registration?
I think AAD Connect sync is one of the prerequisites for the group policy to work.
Hi Anoop.
Question, have you tried the disable-function of the GPO? (If you disable this policy setting, MDM will be unenrolled).
If you have enrolled your hybrid devices, will they automatically unenroll from Intune if you put the GPO to “Disabled”?
Looking at migration from one AD/Intune to a new AD/Intune, and cant find any that used that function (only reinstall or scripts to remove regvalues etc).
I have never tried this for the removal of the MDM enrollment. As per documentation, the PCs should get unenrolled and Also I don’t know what will happen if the license is removed from the user.
Thank you for fast reply Anoop. Will try my luck on Twitter, or setup an env. When there is time 🙂
Hi Anoop, I tried this but for some reason I am getting the below message in EventVwr:
Automatic certificate enrollment for local system failed (0x80094012) The permissions on the certificate template do not allow the current user to enroll for this type of certificate.
Are there any more pre-requisites that need considering related to Certificate enrollment? Many thanks
I think this is because (probably) AAD device registration does not happen for this device. Can you check the command dsregcmd /status?
Also, check whether the device record is available in the AAD portal.
This is the prerequisite.
MDM GPO Settings is not showing server 2012 OS ?
There is a note in the post NOTE! If you don’t install Windows 10 ADMX, you won’t be able to see the group policy we are looking for. How to install Windows 10 ADMX sample install -> https://www.anoopcnair.com/download-microsoft-edge-admx-group-policy-templates/
I am using “Device Credential” to enrol PCs with a ConfigMgr agent already installed. Seems to be working fine, contrary to what you wrote. Thoughts?
I recommend Device Credentials as mentioned below. Sorry but I’m confused with your statement “Seems to be working fine, contrary to what you wrote.”
“I have selected Device Credentials and it worked fine for me with the latest version of Windows 10 2004 and ConfigMgr 2010 client.”
Hi,
Will the end users get Admin privileges on these hybird azure joined machines by default?
HI Anoop
can this be done using a powershell, as GPO is not in site and we required to enable the Autoenrollment MDM using user credentails on the device.
Hello Anoop,
I am having some issues auto enrolling a device into Intune. The device is Hybrid Azure AD Joined and I have created a GPO which I linked with security filtering to a security group which the machine is a member of. I have also linked the GPO to the OU that the machine is in and the GPO is set to enabled.
I am signing in as an enrollment manager and I have a valid Intune license (Business Premium)
Here is the error code: Auto MDM Enroll: Device Credential (0x0), Failed (Unknown Win32 Error code: 0xcaa90014)
When I set up the GPO I do not have a dropdown selection for user or device credentials, is that an issue? I tried updating the admx and still no option to select those.
Any thoughts on how I can start to troubleshoot this issue?
Update, we jus had an error when updating the ADMX files.
I am struggling with this error. EVENT ID 90
Auto MDM Enroll Get AAD Token: Device Credential (0x0), Resource Url (NULL), Resource Url 2 (NULL), Status (Unknown Win32 Error code: 0x8018002b)
Event ID 76
Auto MDM Enroll: Device Credential (0x0), Failed (Unknown Win32 Error code: 0x8018002b)
This device was enrolled using Company Portal App and then removed. I applied Intune via GPO on all other devices and every device works ok except this one.
I have tried this https://learn.microsoft.com/en-us/troubleshoot/mem/intune/device-enrollment/windows10-enroll-error-80180002b and reset the device , performed above steps but still getting same error.
Few things to check:
1.Intune License
2.Azure AD registration status. try to delete the already registered object from Azure AD and check whether it is reappearing automatically, etc.
3.Manual installation of Company Portal instead of GPO works or not?
Hi Anoop
Thanks for looking into this
User got the license. Hybrid environment. Device appear as hybrid in azure ad if I reconnect as local AD after deleting from Azure and on premises AD. If I connect via company portal device register immediately. But via group policy AzureAdPrt status is No. Azure adjoin and domain join is Yes
When setting this up, it only populates azure and not my intune management. Is there a step I am missing?
For Azure AD devices,
Do we have this method to enroll Bulk of Device. (completely cloud envirnment)
Hello All,
Is it possible to join a device as a hybrid azure ad join without an Intune license?
Thanks in advance..!!