Hello, let’s discuss how to Implement Windows 11 Hotpatching using Intune. First, this new enhancement was announced at the Ignite event. Microsoft announced it will test Hotpatching updates for Windows 11 24H2 and Windows 365. Also, Microsoft announced the new enchantment for Windows 11 users.
This new feature, Hotpatching, is now in preview for Windows 11 24H2 and Windows 365 users. It will be one of the best improvements, and many users’ wishes are about to come true. As we all know, system updates are significant for the system and its users.
One primary reason for updates is to fix security vulnerabilities, so we can’t skip this for better performance and productivity. Do you know when the Hotpatch updates will help users? The updates do not affect any users’ workflows.
Microsoft removed the restart option after updates with the help of Hotpatching. It is a method that applies security updates immediately without interrupting user workflows, and it is entirely different from traditional updates. So, let’s look into Hotpatch on Windows 11 24H2.
Table of Contents
What are the Hotpatching Benefits?
The main benefit of Hotpatching is that there is no need to reboot the system after the update, which is a compulsory process in traditional updates. Also, the user gets a smooth workflow during the ongoing updates. It may reduce the necessary reboots and allow users to focus on their Work.
Who can use Windows Hotpatching?
Windows Hotpatching is available to Autopatch customers and can also be accessed through the regular Windows quality update policy in Intune. This feature is designed to improve how users receive updates on Windows devices.
What Microsoft 365 Licenses Offer Hotpatching?
Hotpatching is available with certain Microsoft 365 licenses, like A3+, E3+, and F3. These plans provide advanced features that improve security, system uptime, and update efficiency. With hotpatching, Windows updates happen in memory, reducing downtime and minimizing security risks.
How to Implement Windows 11 Hotpatching using Intune
Above, we discussed an overall view on Microsoft’s Announcement that Hotpatching on Windows 11 24H2 is and Windows 365. Microsoft has announced that a new Hotpatching feature is now available in the public preview for Windows 365 and Windows 11 Enterprise 24H2 client devices.
In the Microsoft Ingnite Event 2024, Mr. Lior Bela and Mr. Rob York discussed this announcement. They mainly discussed Intune Cloud-native Management, Prepare for AI and Next-Gen Cloud PCs. In that topic, they discussed the Hotpatch update, which they explained very well with demos.
| Before Hotpatch Update | After Hotpatch Update |
|---|---|
| The Traditional updates will be downloaded and installed; a restart is required to complete the installation. | Hot patching lets Windows install security updates in the background without needing to restart |
| With Traditional updates, users may experience interruptions when they need to restart, which can affect their tasks. | Hotpatch Update doesn’t make any interruptions during the ongoing tas of users. |

- Fix File Explorer Menu Appear Outside Screen Issue for Windows 11 24H2
- Best Method to Enable Virtualization Based Security Using Microsoft Intune
- Best Way for Windows 11 24H2 Upgrade using Intune and Windows Update for Business WUfB Deployment
- Windows 11 24H2 Monthly Patching Got Faster Installation Reboot and Less CPU usage with the new Client Servicing Stack
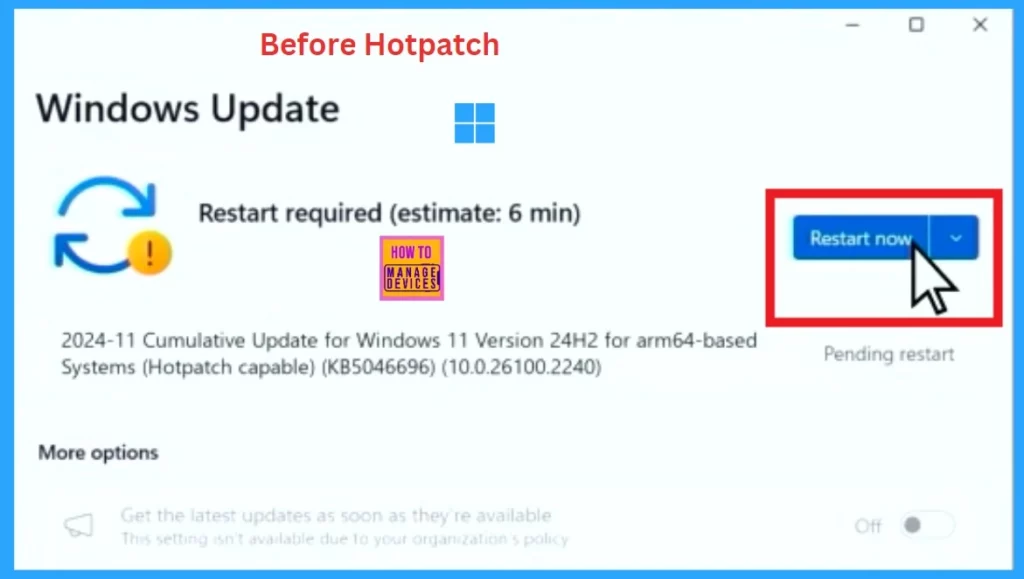
Before Hotpach
Hotpatch updates focus only on security fixes and don’t include any new features. The key benefit is that these updates take effect immediately without restarting your device. In the first month of each quarter, devices will get an update, including the latest security patches, new features, and improvements.
- When we get Updates, we update them immediately.
- When clicking on the Check for the update option, our system starts downloading Updates for our system.
- We know the critical part of this installation.
- After completing the installation, the system needs a Reboot.
- This is very frustrating because restarting is not a good option for users, especially during critical tasks or meetings.
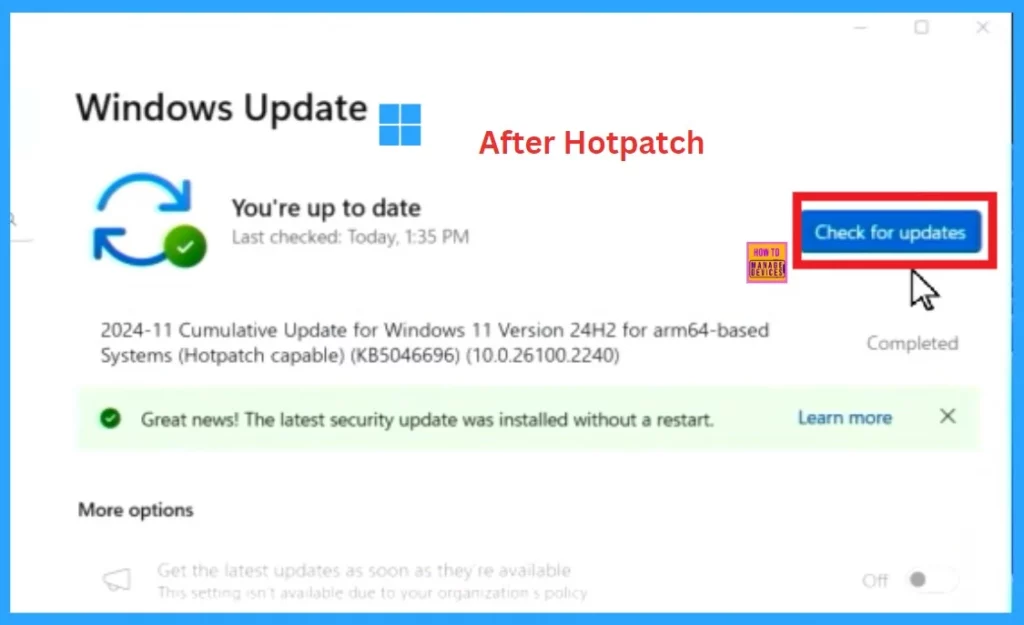
After Hotpach
This update does not change anything on your device, and it’s completely different from traditional Hotpatch, which removes the restart option after the update. In the case of Hotpach, the update eliminates the need for frequent reboots, allowing users to continue working without interruptions. After the update, the user receives a green notification confirming the update was completed.
| Hotpatch Supporting Devices |
|---|
| Devices must be on the latest baseline release version to qualify for Hotpatch updates. |
| Devices must be running Windows 11 24H2 Build 26100.2033 or later |
| VBS must be enabled for secure Hotpatch updates installation. |
| Windows 365 and Azure Virtual Desktop (AVD), including Windows 11 Multi-Session. |
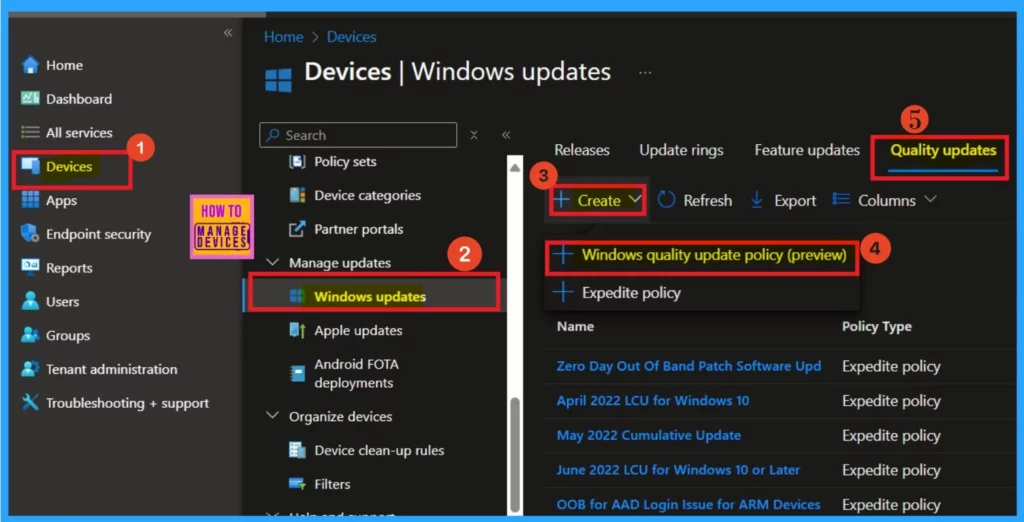
How to Enable the Hotpatch Policy through Intune
You can easily enable the hotpatch policy at the end for that first. You must sign in to the Microsoft Intune Admin Center and navigate to Devices> Windows updates (under the manage update) option.
When you click on the Windows update, you will get an option to create a policy. Click on that, and you will get 2 options. Windows quality update policy preview and expedite policy. Click on the Windows quality update policy preview.
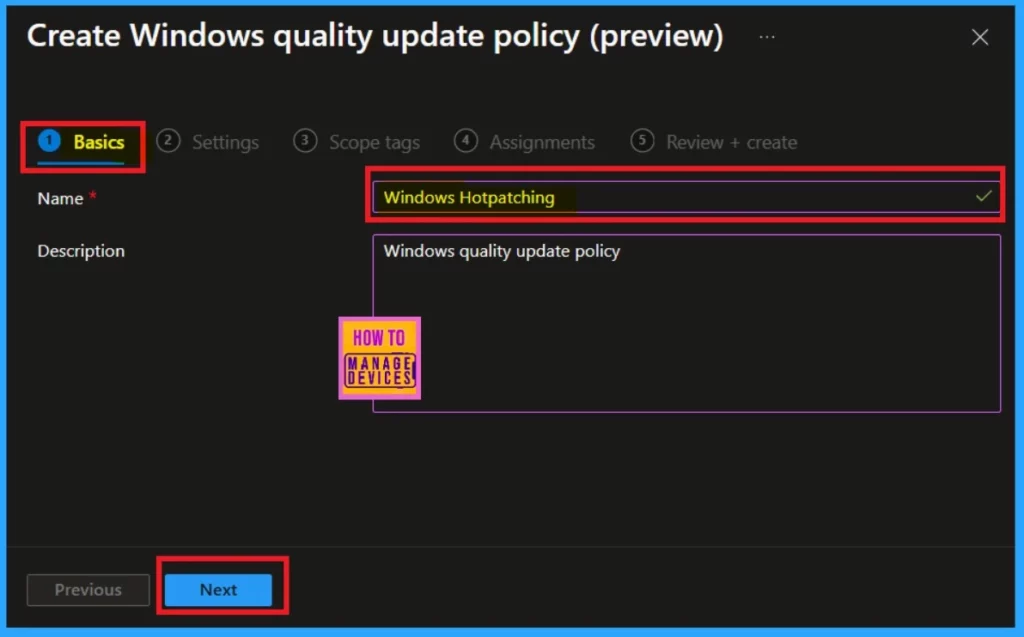
Basics
To create a policy, enter the Basic details, including the name and description. Then, click on “Next.” for an example I have named this policy Windows Hotpatching.
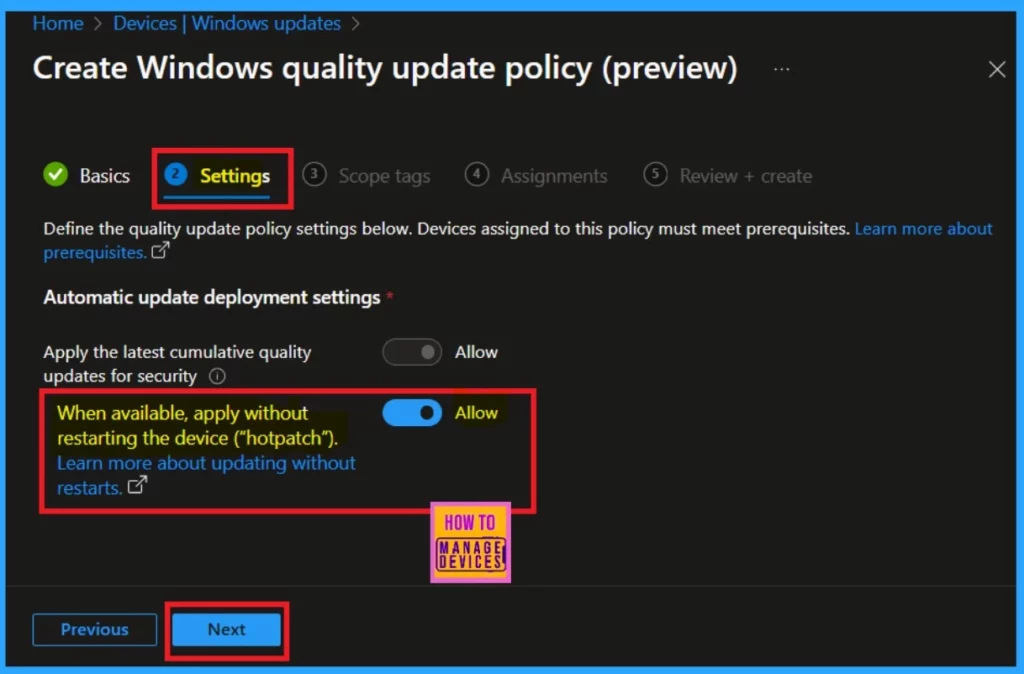
Settings
After completing the basic steps, navigate to the settings tab. Here, enable the policy titled “When available, apply without restarting the device (hotpatch).” To enable it, toggle the switch from left to right. Once you have made these adjustments, click on Next.
Note: Next, you’ll need to go through the scope tags. This step is mandatory, so I skipped this section, so you don’t need to take any action there.
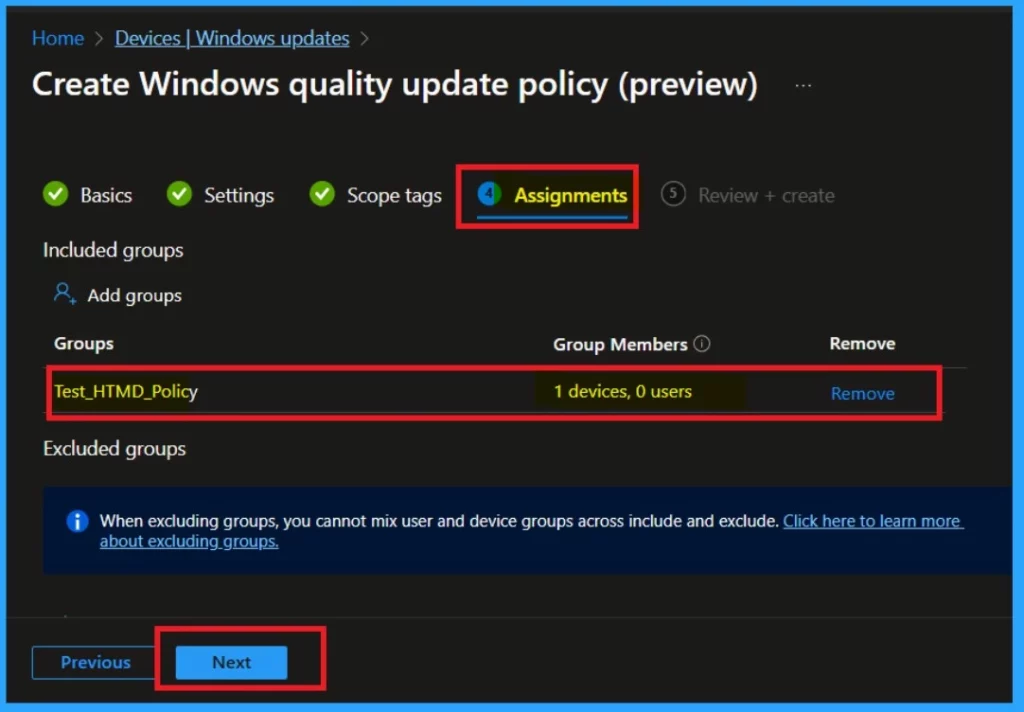
Assignments
After the scope tag section, you will now proceed to the important section known as “Assignments.” In this section, you can assign devices to the policy. You will see an option to “Add Group.” Click on this option, select the group you want to assign to the policy, and then click Next.
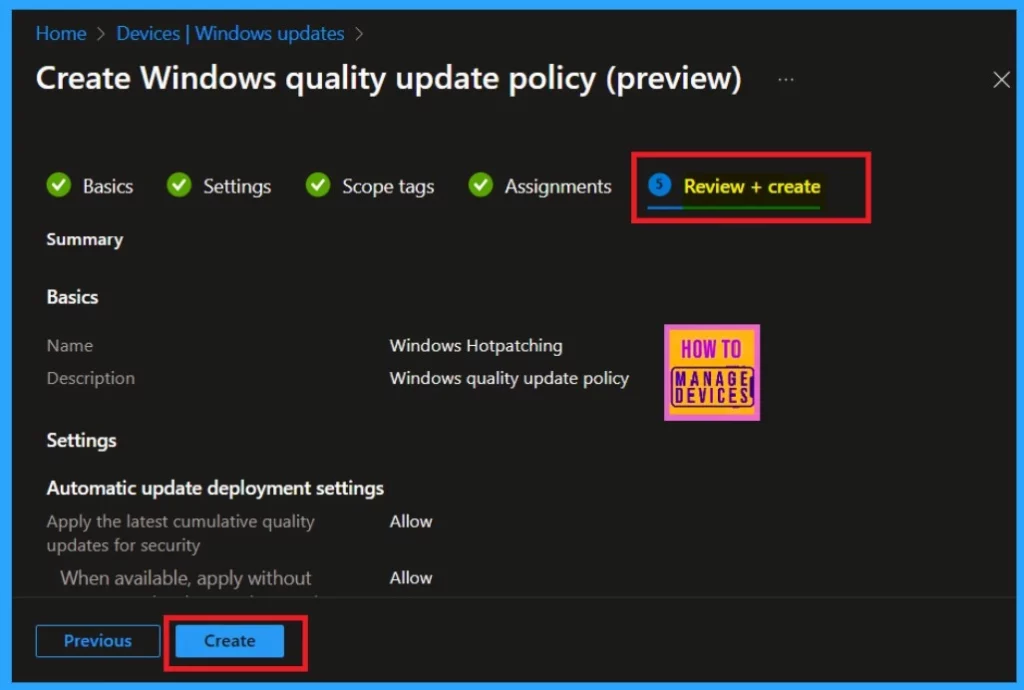
Review+Create
The final session is a Review + Create option. This acts as a summary page where you can review all the information you provided, including the basics and settings. Once you have checked everything, you can finalize the policy by clicking the “Create” option.
- Your Hotpatch policy is now created, ready for use.
End User Experience – Windows 11 24H2 Hotpatching
Once you successfully deployed the Hotpatching Windows quality update policy. Log in to one of the policy-targeted devices.
- Navigate to Settings > Windows Update > Check for Updates
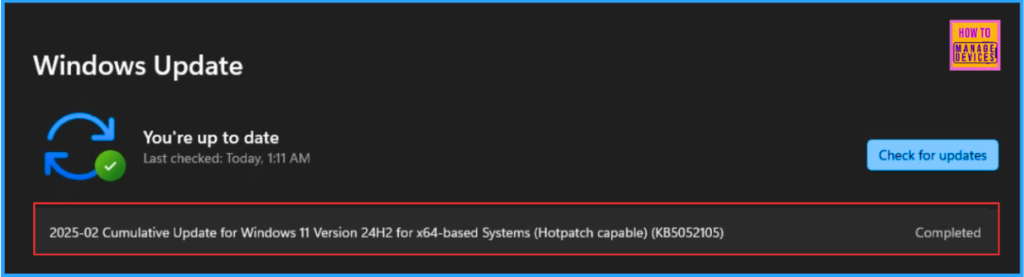
In the Hotpatch calendar of 2025, the February month security update was delivered to the device as a Hotpatch update. After the successful installation, it does not ask for a system reboot. You also identify whether the update is capable of hotpatching by checking the security patch name.
2025-02 Cumulative Update for Windows 11 Version 24H2 for x64-based Systems (Hotpatch capable) (KB5052105)
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Pad and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Vaishnav K has over 11 years of experience in SCCM, Device Management, and Automation Solutions. He writes and imparts knowledge about Microsoft Intune, Azure, PowerShell scripting, and automation. Check out his profile on LinkedIn.

We have installed this Hotpatch, but Tennable is mentioning vulnerabilities now, because it says we are missing KB5051987. But we don’t get that offered by Microsoft Update, because we already have had KB5052105 I suppose.
Is this a known problem?
Hi Marcel Ruiters,
It sounds like Tenable is flagging a missing KB (KB5051987) that isn’t being offered via Microsoft Update because you’ve already installed a later or equivalent Hotpatch (KB5052105). This can happen because vulnerability scanners sometimes rely on static KB lists rather than dynamically checking installed mitigations.
Follow the below steps :-
1) Run PowerShell command “Get-HotFix | Sort-Object InstalledOn -Descending” to verify installed updates
Ensure KB5052105 is listed, as this might already contain the fixes from KB5051987
2) Check the Microsoft Update Catalog to verify if KB5052105 supersedes KB5051987
3) Review the official Microsoft security advisory or support pages to see if KB5052105 includes all fixes from KB5051987.
Other Actions :-
If KB5052105 supersedes KB5051987, you can mark the alert as a false positive in Tenable.
If KB5051987 is required separately, but not appearing in Windows Update, you might need to manually install it from the Microsoft Update Catalog.
Please let me know if you have any further quires.