Let’s see how to start with AVD Troubleshooting Options Tips Tricks. I have seen many scenarios where I could not connect to the WVD host pool (VM), and host pools are not appearing.
Since I’m new to AVD, I didn’t know how to start AVD Troubleshooting. AVD stands for Azure Virtual Desktop.
A PowerShell script can collect all the AVD Troubleshooting logs. Robert Viktor Klemencz @ Microsoft built this tool and shared it with the community.
More details about AVD-Collect are below the section of the post.
In this post, I’m trying to help the AVD community begin the troubleshooting process. WVD is GA’d Generally Available World Wide with App Attach Feature? The following posts provide more detailed troubleshooting steps.
- AVD VM RD Client Connection Error 0x83886181
- AVD VM Force Restart Issue with reason code 0x80000000
- FIX: AVD Azure AD Joined VM Login Issue with Error Code 0x9735
Introduction
There could be many ways to perform AVD troubleshooting. However, I’m going to share my experience in this blog. These are random tips to troubleshoot AVD issues.
The AVD Error codes are available in Microsoft documentation.
What are the AVD Troubleshooting Options?
- Azure Portal – Check whether VMs are up and Running
- Try to run the Remote commands from Azure Portal -> Virtual Machines -> Operations -> Run Command.
- Evaluate Group Policies from AD to check whether those policies block access to the AVD Host Pool VM.
- Confirm whether the user is assigned to the appropriate AVD host pool application groups
- PowerShell, PowerShell, and PowerShell
- Event Logs – Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational
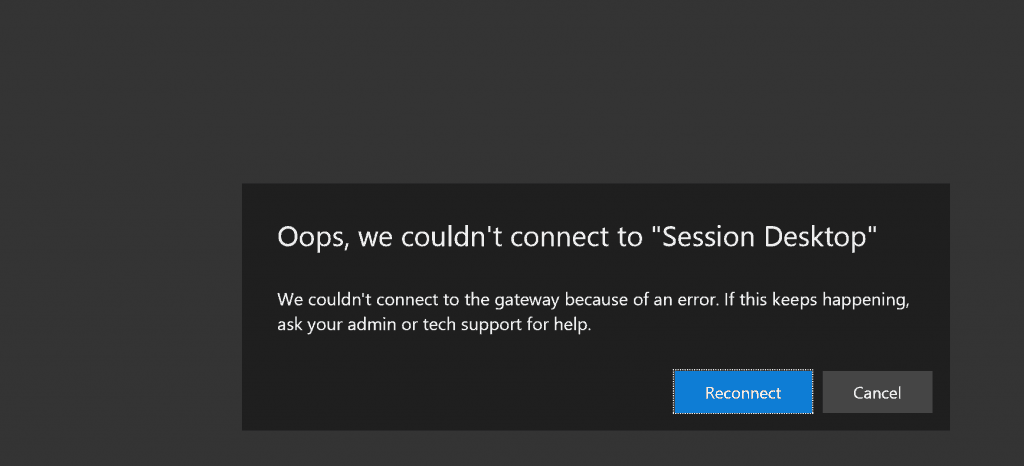
Oops, we couldn’t connect to “Session Desktop” – We couldn’t connect to the gateway because of an error.
If this keeps happening, ask your admin or tech support for help. Reconnect / Cancel – “Can’t log in to HostPool” AVD Troubleshooting Tips.
Azure VM Run Commands – AVD Troubleshooting
What are RUN Commands? Run Command uses the VM agent to run PowerShell scripts within an Azure Windows VM. More details about Azure Windows VM Run commands.
NOTE! – You can’t connect to Azure Windows VM because AVD host pool VMs don’t have public IP and RDP ports enabled for external connectivity.
Run PowerShell Commands
The most useful run command for AVD troubleshooting is RunPowerShellScript.It allows you to execute a PowerShell script or any other PS commands.
As you can see in the following, I’m trying to get the list of Group Policies applied to that VM.
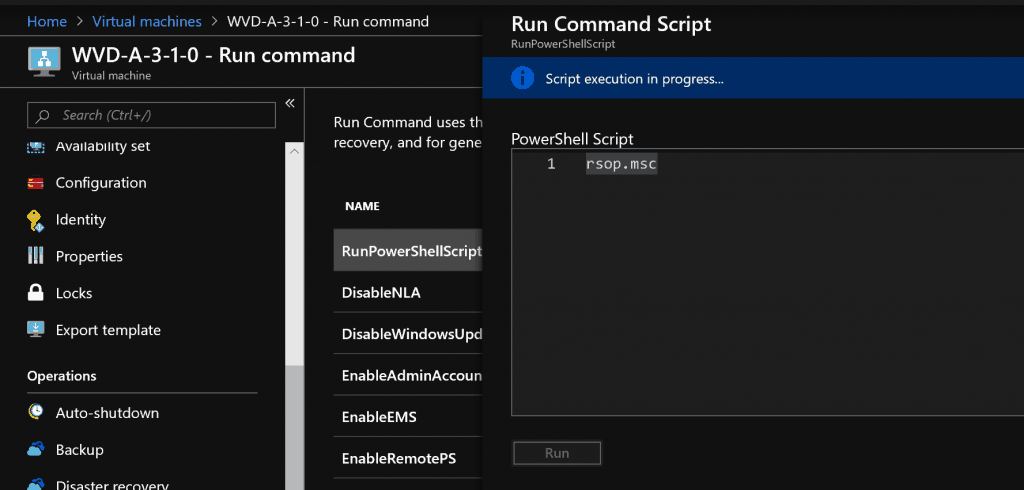
AVD Qwinsta Command
The command Qwinsta will help to understand whether the RD client is working fine on the VM or not. If it’s not, that is the problem with the AVD host pool.
We could get connection or gateway errors when the AVD RD Client is not listening.
PS C:\Users\ACNWinENTImage> qwinsta
SESSIONNAME USERNAME ID STATE TYPE DEVICE services 0 Disc
console 1 Conn
>rdp-tcp#1 ACNWinENTImage 2 Active
31c5ce94259d4... 65536 Listen
rdp-tcp 65537 Listen
Check Event Logs Using Run Commands – RemoteDesktopServices
You can also run a Powershell command to get the Remote Desktop Services logs. PowerShell commands to collect event logs are available in Microsoft Docs.
Get-EventLog -logname RemoteDesktopServices
NOTE! – Also, you can try to get the AVD-related event logs from Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational.
AVD Log Collector PowerShell Script
The following script can collect all the AVD Troubleshooting logs. More details about AVD-Collect are below the post. Robert Viktor Klemencz @ Microsoft owns the script, and all credits go to him.
You can download the AVD Collector Script from here -> https://aka.ms/avd-collect.
“Core” (suitable for troubleshooting issues that do not involve Profiles or Teams or MSIX App Attach)
• Collects core troubleshooting data without including Profiles/FSLogix/OneDrive or Teams or MSIXAA or Smart Card-related data
• Runs Diagnostics. Diagnostics results will be logged
"Core + Profiles" (suitable for troubleshooting Profiles issues)
• Collects all Core data
• Collects Profiles/FSLogix/OneDrive related information, as available
• Runs Diagnostics. Diagnostics results will be logged
"Core + Teams" (suitable for troubleshooting Teams issues)
• Collects all Core data
• Collects Teams related information, as available
• Runs Diagnostics. Diagnostics results will be logged
"Core + MSIX App Attach" (suitable for troubleshooting MSIX App Attach issues)
• Collects all Core data
• Collects MSIX App Attach related information, as available
• Runs Diagnostics. Diagnostics results will be logged
"Core + MSRA" (suitable for troubleshooting Remote Assistance issues)
• Collects all Core data
• Collects Remote Assistance related information, as available
• Runs Diagnostics. Diagnostics results will be logged
"Core + SCard" (suitable for troubleshooting Smart Card issues)
• May prompt for smartcard PIN during data collection
• Collects all Core data
• Collects Smart Card and RD Gateway/KDC Proxy related information, as available
• Runs Diagnostics. Diagnostics results will be logged
"DiagOnly" • Skips Core and all scenario-based data collection and runs Diagnostics only (regardless of whether any other parameters have been specified)
• Runs Diagnostics. Diagnostics results will be logged
The default scenario is “Core.”
Available command line parameters (to preselect the desired scenario)
"-Core" - Collects Core data + Runs Diagnostics
"-Profiles" - Collects all Core data + Profiles/FSLogix/OneDrive data + Runs Diagnostics
"-Teams" - Collects all Core data + Teams data + Runs Diagnostics
"-MSIXAA" - Collects all Core data + MSIX App Attach data + Runs Diagnostics
"-MSRA" - Collects all Core data + Remote Assistance data + Runs Diagnostics
"-SCard" - Collects all Core data + Smart Card/RDGW data + Runs Diagnostics
"-DiagOnly" - The script will skip all data collection and will only run the diagnostics part (even if other parameters have been included).
"-AcceptEula" - Silently accepts the Microsoft Diagnostic Tools End User License AgreementUsage example with parameters:
To collect only Core data (excluding Profiles/FSLogix/OneDrive, Teams, MSIX App Attach, MSRA, Smart Card):
.\AVD-Collect.ps1 -Core
To collect Core + Profiles + MSIX App Attach data
.\AVD-Collect.ps1 -Profiles -MSIXAA
To collect Core + Profiles data
.\AVD-Collect.ps1 -Profiles
To run Diagnostics without collecting Core or scenario-based data
.\AVD-Collect.ps1 -DiagOnly
If you are missing any of the data that the script should normally collect (see “Data being collected”), check the content of “_AVD-Collect-Log.txt” and “_AVD-Collect-Errors.txt” files for more information. Some data may not be present during data collection and thus not picked up by the script. This should be visible in one of the two text files.
PowerShell ExecutionPolicy
If the script does not start, complaining about execution restrictions, then in an elevated PowerShell console run:
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Force -Scope Processand verify with “Get-ExecutionPolicy -List” that no ExecutionPolicy with higher precedence is blocking the execution of this script.
The script is digitally signed with a Microsoft Code Sign certificate.
After that, run the AVD-Collect script again.
Once the script has started, please read the “IMPORTANT NOTICE” message and confirm if you agree to continue with the data collection.
Depending on the amount of data that needs to be collected, the script may need to run for a few minutes. Please wait until the script finishes collecting all the data.
====================
Data being collected
The collected data is stored in a subfolder under the same folder where the script is located, and at the end of the data collection, the results are archived into a .zip file. No data is automatically uploaded to Microsoft.
Data collected in the “Core” scenario:
• Log files
o C:\Packages\Plugins\Microsoft.Powershell.DSC\\Status\
o C:\Packages\Plugins\Microsoft.Compute.JsonADDomainExtension\\Status\
o C:\Packages\Plugins\Microsoft.EnterpriseCloud.Monitoring.MicrosoftMonitoringAgent\\Status\
o C:\Program Files\Microsoft RDInfra\AgentInstall.txt
o C:\Program Files\Microsoft RDInfra\GenevaInstall.txt
o C:\Program Files\Microsoft RDInfra\SXSStackInstall.txt
o C:\Program Files\Microsoft RDInfra\WVDAgentManagerInstall.txt
o C:\Users\AgentInstall.txt
o C:\Users\AgentBootLoaderInstall.txt
o C:\Windows\debug\NetSetup.log
o C:\Windows\Temp\ScriptLog.log
o C:\WindowsAzure\Logs\WaAppAgent.log
o C:\WindowsAzure\Logs\MonitoringAgent.log
o C:\WindowsAzure\Logs\Plugins\
• Geneva Scheduled Task information
• “set MON” output (Monitoring Agent)
• Local group membership information
o Remote Desktop Users
• Registry keys
o HKEY_CURRENT_USER\Control Panel\International
o HKEY_CURRENT_USER\Keyboard Layout
o HKEY_CURRENT_USER\SOFTWARE\Microsoft\RdClientRadc
o HKEY_CURRENT_USER\SOFTWARE\Microsoft\Remote Desktop
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Azure\DSC
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MSRDC\Policies
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\NET Framework Setup\NDP
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\RDAgentBootLoader
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\RDInfraAgent
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\RDMonitoringAgent
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WVDAgentManager
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Terminal Server Client
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Virtual Machine\Guest\Parameters
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Windows Error Reporting
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Terminal Server
o HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Cryptography
o HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CredentialsDelegation
o HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services
o HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\CloudDomainJoin
o HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\CrashControl
o HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Cryptography
o HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa
o HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders
o HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server
o HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RdAgent
o HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RDAgentBootLoader
o HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WVDAgent
o HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WVDAgentManager
o HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\TermService
o HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\UmRdpService
o HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\WinRM
o HKEY_LOCAL_MACHINE\SYSTEM\Keyboard Layout
• Event Logs
o Application
o Microsoft-Windows-CAPI2/Operational
o Microsoft-Windows-DSC/Operational
o Microsoft-Windows-PowerShell/Operational
o Microsoft-Windows-RemoteDesktopServices
o Microsoft-Windows-RemoteDesktopServices-RdpCoreCDV/Admin
o Microsoft-Windows-RemoteDesktopServices-RdpCoreCDV/Operational
o Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Admin
o Microsoft-Windows-RemoteDesktopServices-RdpCoreTS/Operational
o Microsoft-Windows-TaskScheduler/Operational
o Microsoft-Windows-TerminalServices-LocalSessionManager/Admin
o Microsoft-Windows-TerminalServices-LocalSessionManager/Operational
o Microsoft-Windows-TerminalServices-PnPDevices/Admin
o Microsoft-Windows-TerminalServices-PnPDevices/Operational
o Microsoft-Windows-TerminalServices-RemoteConnectionManager/Admin
o Microsoft-Windows-TerminalServices-RemoteConnectionManager/Operational
o Microsoft-Windows-WinINet-Config/ProxyConfigChanged
o Microsoft-Windows-WinRM/Operational
o Microsoft-WindowsAzure-Diagnostics/Bootstrapper
o Microsoft-WindowsAzure-Diagnostics/GuestAgent
o Microsoft-WindowsAzure-Diagnostics/Heartbeat
o Microsoft-WindowsAzure-Diagnostics/Runtime
o Microsoft-WindowsAzure-Status/GuestAgent
o Microsoft-WindowsAzure-Status/Plugins
o Security
o System
• “gpresult /h” and “gpresult /r /v” output
• “flame filters” output
• Details of the running processes and services
• Networking information (firewall rules, ipconfig /all, profiles, netstat -anob, proxy configuration)
• “Qwinsta /counter” output
• PowerShell version
• “Get-Hotfix” output
• “Get-DscConfiguration” and “Get-DscConfigurationStatus” output
• File versions of the currently running binaries
• File information about the AVD desktop client binaries (“msrdc.exe” and “msrdcw.exe”)
• File versions of key binaries:
o Windows\System32*.dll
o Windows\System32*.exe
o Windows\System32*.sys
o Windows\System32\drivers*.sys
• Basic system information
• .NET Framework information
• Msinfo32 output (in .nfo and .txt format)
• WinRM configuration information
• Certificate My store information
• Certificate thumbprint information
• DxDiag output in .txt format with no WHQL check
• “dsregcmd /status” output
• The content of the “C:\Users\%username%\AppData\Local\Temp\DiagOutputDir\RdClientAutoTrace” folder (available on devices used as source clients to connect to AVD hosts) from the past five days, containing:
o AVD remote desktop client connection ETL traces
o AVD remote desktop client application ETL traces
o AVD remote desktop client upgrade log (MSI.log)
• Convert existing .tsf files on AVD hosts from under “C:\Windows\System32\config\systemprofile\AppData\Roaming\Microsoft\Monitoring\Tables” into .csv files and collect the resulting .csv files
• “route print” output
• “Azure Instance Metadata service endpoint” request info
• api/health and api/health status
• Output of “Test-DscConfiguration -Detailed.”
• Output of “C:\Program Files\NVIDIA Corporation\NVSMI\nvidia-smi.exe” (if the NVIDIA GPU drivers are already installed on the machine)
• Output of “C:\Program Files\Microsoft Monitoring Agent\Agent\TestCloudConnection.exe.”
• Remote Desktop License Server database information (if RDLS role is installed – for Server OS deployments):
o Win32_TSLicenseKeyPack under ‘_RDS*_rdls_LicenseKeyPacks.html’ o Win32_TSIssuedLicense under ‘_RDS*_rdls_IssuedLicenses.html’
Data collected additionally to the “Core” dataset, depending on the selected scenario or command line parameter(s) used:
• Log files
o C:\ProgramData\FSLogix\Logs
o %appdata%\Microsoft\Teams\logs.txt
o %userprofile%\Downloads\MSTeams Diagnostics Log DATE_TIME.txt
o %userprofile%\Downloads\MSTeams Diagnostics Log DATE_TIME_calling.txt
o %userprofile%\Downloads\MSTeams Diagnostics Log DATE_TIME_cdl.txt
o %userprofile%\Downloads\MSTeams Diagnostics Log DATE_TIME_cdlWorker.txt
o %userprofile%\Downloads\MSTeams Diagnostics Log DATE_TIME_chatListData.txt
o %userprofile%\Downloads\MSTeams Diagnostics Log DATE_TIME_sync.txt
o %userprofile%\Downloads\MSTeams Diagnostics Log DATE_TIME_vdi_partner.txt
• Registry keys
o HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office
o HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive
o HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Office
o HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\OneDrive
o HKEY_LOCAL_MACHINE\SOFTWARE\FSLogix
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Search
o HKEY_LOCAL_MACHINE\SOFTWARE\Policies\FSLogix
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Exclusions\Extensions
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender\Exclusions\Processes
o HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Exclusions\Extensions
o HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Exclusions\Paths
o HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Exclusions\Processes
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Teams
o HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Remote Assistance
o HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RDWebRTCSvc
• Event Logs
o Microsoft-FSLogix-Apps/Admin
o Microsoft-FSLogix-Apps/Operational
o Microsoft-Windows-AppXDeploymentServer/Operational
o Microsoft-Windows-Kerberos-KDCProxy/Operational
o Microsoft-Windows-RemoteAssistance/Admin
o Microsoft-Windows-RemoteAssistance/Operational
o Microsoft-Windows-SmartCard-Audit/Authentication
o Microsoft-Windows-SmartCard-DeviceEnum/Operational
o Microsoft-Windows-SmartCard-TPM-VCard-Module/Admin
o Microsoft-Windows-SmartCard-TPM-VCard-Module/Operational
o Microsoft-Windows-SMBClient/Connectivity
o Microsoft-Windows-SMBClient/Operational
o Microsoft-Windows-SMBClient/Security
o Microsoft-Windows-SMBServer/Connectivity
o Microsoft-Windows-SMBServer/Operational
o Microsoft-Windows-SMBServer/Security
o Microsoft-Windows-User Profile Service/Operational
o Microsoft-Windows-VHDMP/Operational
• FSLogix tool output
o frx list-redirects
o frx list-rules
o frx version
• Local group membership information
o FSLogix ODFC Exclude List
o FSLogix ODFC Include List
o FSLogix Profile Exclude List
o FSLogix Profile Include List
• Local group membership information
o Distributed COM Users
o Offer Remote Assistance Helpers
• “certutil -scinfo -silent” output
• RD Gateway information when run on the KDC Proxy server and the RD Gateway role is present
o Server Settings, Resource Authorization Policy, Connection Authorization Policy
========
AVD-Diag
AVD-Collect also performs diagnostics for common known issues, regardless of the selected scenario.
Based on your requirements, you may want to skip specific data collection or run diagnostics only. See the scenario descriptions above.
New diagnostics checks may be added in each new release, so always use the latest version of the script.
Important Notes:
“Diagnostics” is not a replacement for full data analysis. It only gives you basic diagnostics of some common scenarios and facilitates further troubleshooting. Depending on the scenario, other data collection and analysis will be needed.
Version 210730.16 of the script can perform the following diagnostics:
• Brief check of the system the script is running on (from an AVD point of view): FQDN, OS, OS Build, OS SKU, VM Size, VM Location
o Check if the VM is part of an AVD host pool: SessionHostPool name, Ring, Geography
o Check if the running OS is supported when the VM is part of an AVD host pool
o Check for the last machine boot uptime, with an extra notification if it occurred >= 25 hours ago
o Check for the number of vCPUs available on the machine
o Check for the “LmCompatibilityLevel” registry key value
o Check for Time Zone Redirection policy configuration
• Check for GPU configuration when using NV* or NC* VM series (checks required policy configuration and lists available video controllers and their driver versions)
• Check for Azure AD-join configuration
• Check the status of key services: RdAgent, RDAgentBootLoader, WVDAgent (Win7 only), WVDAgentManager (Win7 only), TermService, SessionEnv, UmRdpService, AppReadiness, AppXSvc, WinRM, frxsvc, frxdrv, frxccds, OneDrive Updater Service, msi server (Windows Installer)
• Check for current and previous AVD Agent and Stack versions and their installation dates (Windows 10 and Server OS hosts)
• Check for the following registry keys:
o HKLM\SOFTWARE\Microsoft\RDInfraAgent\IsRegistered
o HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services\fQueryUserConfigFromDC
o HKLM\System\CurrentControlSet\Control\Terminal Server\fDenyTSConnections
o HKLM\SYSTEM\Setup\OOBEInProgress
o HKLM\SOFTWARE\FSLogix\Profiles\RedirXMLSourceFolder
• Check for all available RD listeners and their configuration: fEnableWinStation, fReverseConnectMode, ReverseConnectionListener
• Check for API/health and API/health availability
• Check for the Screen Capture Protection policy configuration
• Check for Session Time Limit policy settings
• Check for device and resource redirection policy configuration
• Check for camera and microphone privacy settings (general and desktop apps)
• Check for required URLs
• Check for proxy configuration
• Check for basic Test-NetConnection reply
• Check for Process crashes that occurred within the last five days
• Check for SSL/TLS configuration
• Check if the Remote Desktop Session Host role is installed on the VM when running a Server OS
• Check if reg key “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\DisableAntiSpyware” is enabled on Server OS
• Check for FSLogix best practice settings for enterprises
• Check for FSLogix registry key “HKLM\SOFTWARE\FSLogix\Profiles\NoProfileContainingFolder”
• Check if the FSLogix storage location defined under ‘VHDLocations’ is reachable (Test-NetConnection) for Profile and Office containers
• Check for “frxsvc” service recovery settings
• Check for Cloud Cache “CCDLocations” registry key for Profile and Office Container
• Check the availability and value of the “CleanupInvalidSessions” registry key when FSLogix is present on the system
• Check for the Presence of the recommended Windows Defender Antivirus exclusion values when FSLogix is present on the system
• Check OneDrive configuration/requirements when FSLogix is present on the system
• Check media optimization configuration for Teams when Teams is present on the system
• Check for the Multimedia Redirection for AVD configuration (MsMmrHostMri installation only)
• Check the availability and value of the reg key: ‘DeleteUserAppContainersOnLogoff’ for firewall rules bloating scenarios
• Check WinRM configuration / requirements
o Presence of “WinRMRemoteWMIUsers__” group
o IPv4Filter and IPv6Filter values
o Presence of firewall rules for ports 5985 and 5986
• Check for RDP ShortPath configuration (Windows 10 and Server OS hosts)
• Check for AVD agent issues over the past five days:
o “INVALID_REGISTRATION_TOKEN” (Event 3277)
o “INVALID_FORM” (Event 3277)
o “InstallationHealthCheckFailedException” (Event 3277)
o “ENDPOINT_NOT_FOUND” (Event 3277)
o “NAME_ALREADY_REGISTERED” (Event 3277)
o “InstallMsiException” (Event 3277)
o “DownloadMsiException” (Event 3277)
o “Transport received an exception” (Event 3019)
o “RD Gateway Url” (Event 3703)
o “MissingMethodException” (Event 3389)
o “SessionHost unhealthy” (Event 0)
o “IMDS not accessible” (Event 0)
o “Monitoring Agent Launcher file path was NOT located” (Event 0)
o “NOT ALL required URLs are accessible!” (Event 0)
o “Unable to connect to the remote server” (Event 0)
o “Unhandled status [ConnectFailure] returned for url” (Event 0)
o “System.ComponentModel.Win32Exception (0x80004005)”
• Check for MSIX App Attach issues over the past five days:
o “A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider.”
o “MountDisk: Error occurred during mount.”
o “SysNtfyLogoff: Package deregistration for MSIX app attach failed during user logoff.”
O “Failed to get the minimum OS version supported for app attach: System.AggregateException: One or more errors occurred”
o “AppAttachStageAsync: Failed to get packages to staging.”
o “DeregisterPackages: Failed to get packages to deregister.”
o “InnerRestException: Error accessing virtual disk.”
• Check for FSLogix issues over the past five days:
o “Failed to open virtual disk” (Event 26 – FSLogix-Apps/Operational)
o “FindFile failed for path” (Event 26 – FSLogix-Apps/Operational)
o “LoadProfile failed” (Event 26 – FSLogix-Apps/Operational)
o “The Kerberos client received a KRB_AP_ERR_MODIFIED error from the server” (Event 4 – System)
The script generates an *_AVD-Diag.txt and an *_AVD-Diag.html output file with the results of the above checks. Additional output files may be generated if the process crashes, AVD Agent, or MSIX App Attach issues have been identified.
==========
Tool Owner
Robert Viktor Klemencz @ Microsoft Customer Service and Support
If you have any feedback about the tool or want to report any issues with it, please reach out to AVDCollectTalk@microsoft.com
Group Policies
Group policies create trouble with VMs in the AVD host pool. Evaluate the group policies applied to the OU where the AVD VMs are part.
I have seen scenarios in which removing some group policies helped regain access to VMs in the host pool. So, group policies are one of the main AVD troubleshooting steps.
Don’t apply all the security policies to the VMs without testing them thoroughly.
PowerShell Command-lets
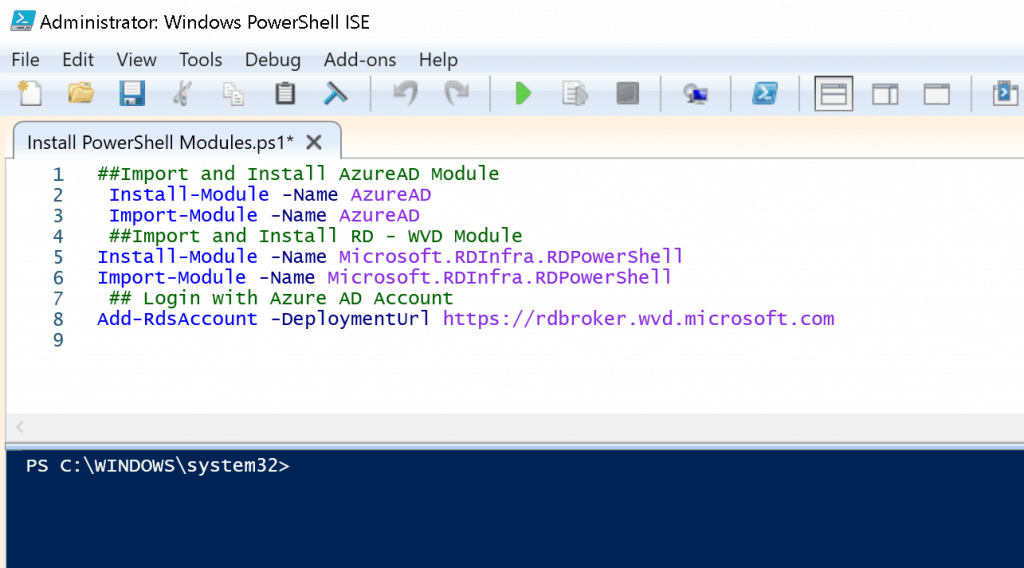
The AVD troubleshooting with Powershell command-lets is another useful way to resolve the issue. Ensure you have all the required PowerShell modules installed and imported onto the machine before starting the AVD troubleshooting.
##Install & Import AzureAD Module
Install-Module -Name AzureAD
Import-Module -Name AzureAD
##Install & Import RD - WVD Module
Install-Module -Name Microsoft.RDInfra.RDPowerShell
Import-Module -Name Microsoft.RDInfra.RDPowerShell
## Login with Azure AD Account
Add-RdsAccount -DeploymentUrl https://rdbroker.wvd.microsoft.com
Rds Diagnostic Activities
Ensure you access Azure AD and AVD Tenant appropriately before running the following PowerShell commands. Use the following command commands:
Get-RdsDiagnosticActivities -UserName “acn@howtomanagedevices.com” -TenantName $tenant -Detailed“
The output with failures – This error was because of GPO policies! I had to remove the security-related group policies to get the WVD VM connectivity issue fixed.
AVD Troubleshooting Event Logs
AVD RD Application troubleshooting can be done via event viewer. You can follow the event log path:
| AVD RD Application | Event Log path |
|---|---|
| Activity ID | be333145-645e-4767-9df7-13a7246f0000 |
| ActivityType | Connection |
| StartTime | 8/16/2019 6:08:12 PM |
| EndTime | 8/16/2019 6:08:16 PM |
| User Name | acn@howtomanagedevices.com |
| RoleInstances | rdwebclient;mrs-eus2r1c002- |
| Outcome | Failure |
| Status | Completed |
| Details | {[ClientOS, Win32 IE 11.0], [ClientVersion, 1.0.19.2], [ClientType, HTML], [PredecessorConnectionId, ]…} |
| LastHeartbeatTime | 8/16/2019 6:08:16 PM |
| Checkpoints | {OnClientDisconnected} |
| Errors | {Microsoft.RDInfra.Diagnostics.Common.DiagnosticsErrorInfo}ActivityId: a802a7c4-f6e6-40ee-86a5-c58e78160000 |
| ActivityType | Connection |
| StartTime | 8/16/2019 6:07:59 PM |
| End Time | 8/16/2019 6:08:03 PM |
| User name | acn@howtomanagedevices.com |
| RoleInstances | rdwebclient;mrs-eus2r1c002- |
| Outcome | Failure |
| Status | completed |
| Details | {[ClientOS, Win32 IE 11.0], [ClientVersion, 1.0.19.2], [ClientType, HTML], [PredecessorConnectionId, ]…} |
| LastHeartbeatTime | 8/16/2019 6:08:03 PM |
| Checkpoints | {OnClientDisconnected} |
| Errors | {Microsoft.RDInfra.Diagnostics.Common.DiagnosticsErrorInfo} |
Event Viewer (EventVwr)-> Application and Service Logs > Microsoft > Windows> RemoteDesktopServices-RdpCoreTS/Operational
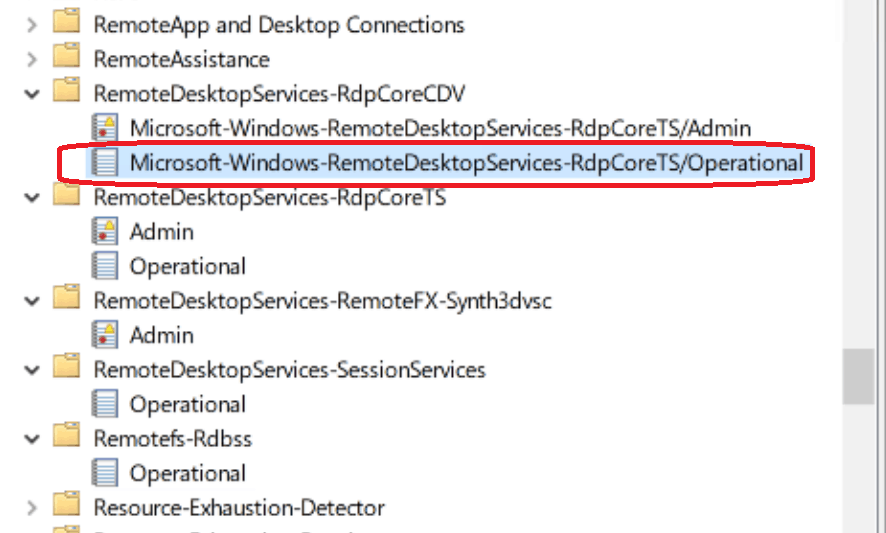
Sample AVD Troubleshooting Event Logs
Disconnect trace:CUMRDPConnection Disconnect trace:'calling spGfxPlugin->PreDisconnect()' in CUMRDPConnection::PreDisconnect at 4983 err=[0xb], Error code:0xB
Interface method called: PreDisconnect(11)
Interface method called: SetErrorInfo(0xb)
Interface method called: DisconnectNotify
Interface method called: GetServerAutoReconnectInfo
The disconnect reason is 11
Channel rdpdr has been closed between the server and the client on transport tunnel: 0.
Channel cliprdr has been closed between the server and the client on transport tunnel: 0.
Channel rail has been closed between the server and the client on transport tunnel: 0.
Channel railenc has been closed between the server and the client on transport tunnel: 0.
'WINHTTP_CALLBACK_STATUS_REQUEST_ERROR WebSocket operation 'WINHTTP_WEB_SOCKET_RECEIVE_OPERATION'' in CHttpIoRequestWinHttp::StatusCallback at 2257 err=[0x2efe]
Websocket WINHTTP_CALLBACK_STATUS_REQUEST_ERROR
'Forcing Websocket shutdown.' in CHttpIoRequestWinHttp::Shutdown at 1048 err=[0x0]
'Closing Websocket Handle=0x160ef360' in CHttpIoRequestWinHttp::Shutdown at 1058 err=[0x0]
WSSSTATETRANSITION: An error was encountered when transitioning from WSStateDisconnecting in response to WSSGenericEvent (error code 0x80072EFE).
'WINHTTP_CALLBACK_STATUS_HANDLE_CLOSING called Handle=0x6f4fef98' in CHttpIoRequestWinHttp::StatusCallback at 2063 err=[0x0]
'Handle closing - stream type: 3' in CHttpIoRequestWinHttp::ContinueProcessingCallback at 2926 err=[0x0]
Interface method called: OnDisconnected(server initiated)
Resources
- AVD Video PlayList ➡➡https://aka.ms/WVDPlaylist
- WVD AMA 28th Aug 2019 Windows Virtual Desktop Microsoft WVD FAQs from AMA
- Microsoft VDI Story WVD Concept Setup Guide Myths Known Issues
- SCCM Intune Support for Persistent Non-Persistent VDI VMs
- How to Connect WVD Remote Desktop Resources Client or Browser?
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here –HTMD WhatsApp.
Author
Anoop C Nair is Microsoft MVP! He is a Device Management Admin with more than 20 years of experience (calculation done in 2021) in IT. He is a Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc
