In this blog post, I am going to explain how to install Microsoft Defender Browser Protection Extension using Microsoft Intune PowerShell Script. Microsoft Defender Browser Protection is a valuable extension for Google Chrome and Microsoft Edge that enhances web security by protecting users from malicious websites and phishing attacks.
For organizations using Microsoft Intune, deploying this extension via PowerShell script ensures a consistent and automated rollout across managed devices, helping to enforce security standards and improve endpoint protection. I’ll try to demostate this feature with Google Chrome Browser Extenstion.
Using a PowerShell script, Intune/IT Admins can silently add the Microsoft Defender Browser Protection extension by writing registry keys that configure the browser to force-install the extension. This method supports both Chrome and Edge Chromium browsers and is commonly used when group policies or ADMX templates are not ideal for cloud-managed devices. By pushing the script via Intune, it simplifies deployment at scale.
Once the script is uploaded as a PowerShell Platform script in Intune, it runs on target devices and configures the necessary settings without user interaction. This approach ensures compliance and eliminates the risk of users disabling or removing the extension. It’s a practical and effective way to secure web browsing across an enterprise environment using Microsoft Defender technology.

Table of Contents
Why Microsoft Defender Browser Protection Extension is Require
Here’s a table outlining why the Microsoft Defender Browser Protection Extension is required, highlighting its key benefits and use cases. This extension is a critical part of a defense-in-depth strategy, complementing antivirus, firewall, and endpoint protection solutions.
| Reason | Description |
|---|---|
| Phishing Protection | Blocks known phishing sites to prevent credential theft and data breaches. |
| Malware Site Blocking | Prevents access to websites that distribute malware or exploit kits. |
| SmartScreen Integration | Leverages Microsoft SmartScreen intelligence to detect unsafe URLs in real time. |
| Browser-Level Defense | Provides an additional security layer directly within Chrome or Edge browsers. |
| Policy Enforcement | Ensures consistent security posture across all managed devices via Intune. |
| Reduced User Risk | Minimizes chances of users clicking on malicious links or downloading threats |
| Cloud-Managed Security | Ideal for remote/hybrid environments where on-prem GPOs are not applicable. |
| Lightweight and Non-Intrusive | Easy to deploy with minimal system impact and no disruption to user workflows. |
- Best Guide to Install Google Chrome Extensions using Intune Policy
- Quick Fix to your Windows OS Issues with Detection and Remediation Scripts with Intune
- Quick and Easy way to Turn on PowerShell Audit using Intune Policy
- Easy way to Enable Fast Startup using Intune PowerShell Script
Create a Platform Script in Intune to Install Microsoft Defender Browser Protection Extension
Follow these steps to install the Microsoft Defender Browser Protection Extension using the Intune PowerShell Script. I will be using the Platform script to configure it. Log in to the Microsoft Intune Admin Center using your admin credentials.
- Navigate to Devices > Windows > Scripts and remediations
- Click on Platform scripts > +Add
In the Basics details pane, we can name the PowerShell script “Microsoft Defender Browser Protection for Google Chrome” If necessary, provide a brief description of the script and click Next.

Write a PowerShell Script to Install the Microsoft Defender Browser Protection Extension
Let’s write a concise PowerShell script from scrach to install the Microsoft Defender Browser Protection extension for Google Chrome, which enhances your browsing security. Save the script in a .ps1 file format.
###############################################################################
#Microsoft Defender Browser Protection - Google Chrome Browser Extension
#Author : Vaishnav K
#LinkedIn : https://www.linkedin.com/in/vaishnav-k-957b0589/
#Website : https://www.anoopcnair.com/author/vaishnavkuruvaikandy
###############################################################################
# Define extension ID and update URL
$ExtensionId = "bkbeeeffjjeopflfhgeknacdieedcoml"
$UpdateURL = "https://clients2.google.com/service/update2/crx"
$ExtensionValue = "$ExtensionId;$UpdateURL"
$RegPath = "HKLM:\SOFTWARE\Policies\Google\Chrome\ExtensionInstallForcelist"
# Ensure the main Chrome policy key exists
if (-not (Test-Path "HKLM:\SOFTWARE\Policies\Google\Chrome")) {
New-Item -Path "HKLM:\SOFTWARE\Policies\Google\Chrome" -Force | Out-Null
}
# Create key if not present
if (-not (Test-Path $RegPath)) {
New-Item -Path $RegPath -Force | Out-Null
Write-Host "Created registry path: $RegPath"
}
# Check for existing values
$existing = Get-ItemProperty -Path $RegPath
$matchFound = $false
foreach ($property in $existing.PSObject.Properties) {
if ($property.Value -eq $ExtensionValue) {
$matchFound = $true
Write-Host "Extension already present in registry under key: $($property.Name)"
break
}
}
# Add only if not found
if (-not $matchFound) {
$index = 1
while ($existing.PSObject.Properties.Name -contains "$index") {
$index++
}
New-ItemProperty -Path $RegPath -Name "$index" -Value $ExtensionValue -PropertyType String -Force
Write-Host "Added extension to registry with key $index"
}Note! I’ve uploaded the PowerShell Script to my GitHub Repo, so feel free to check it out for your needs. Download from here : MicrosoftDefenderBrowserProtection_Google Chrome_New.ps1
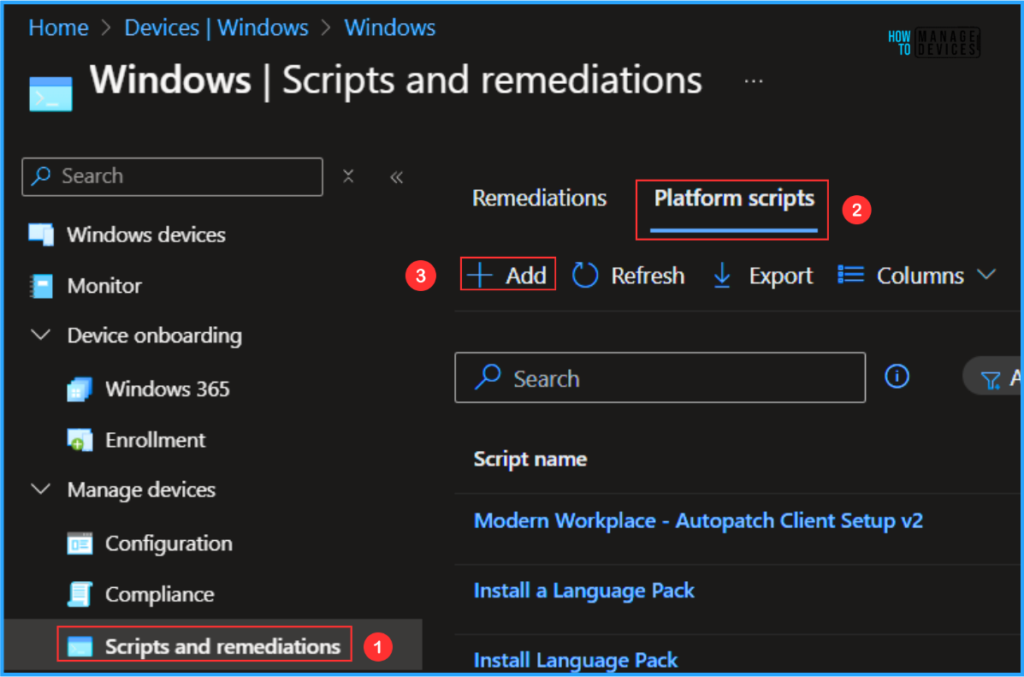
In the Script settings pane, we can set the configurations according to our requirements. The first option is mandatory, we must browse and select our saved PS Script here.
- Script location – Browse and select the saved script MicrosoftDefenderBrowserProtection_Google Chrome.ps1
- Run this script using the logged on credentials – No
- Enforce script signature check – No
- Run script in 64 bit PowerShell Host – Yes
On the next page, keep the default scope tags. If any custom scope tags are available based on your requirements, you can select them for this script deployment.
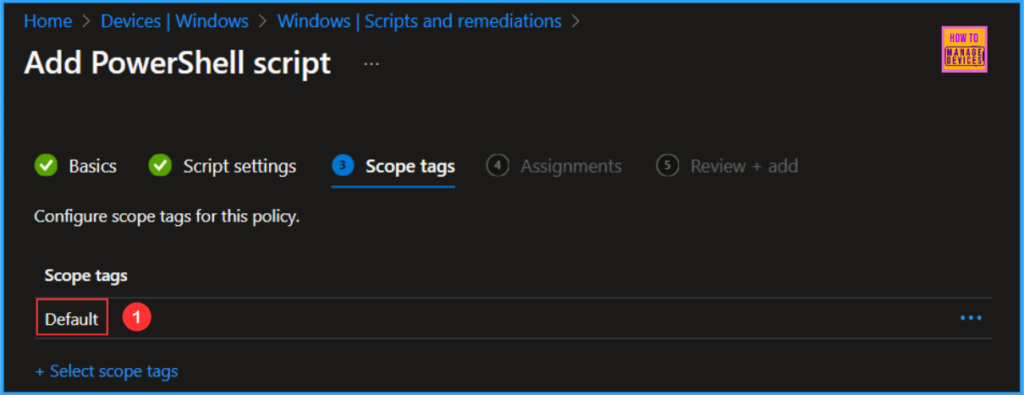
Click on Next and assign the script to HTMD – Test Computers. You can click Add groups and select the desired device group in the Included groups section.
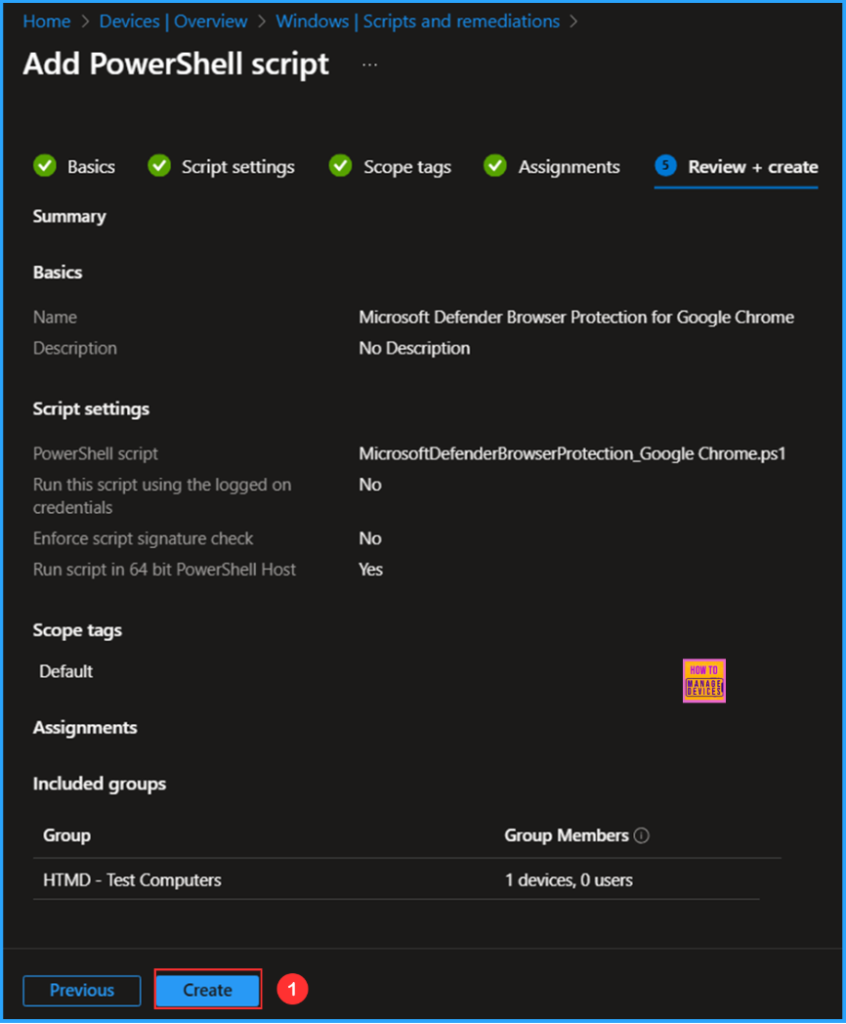
On the Review + Add pane, thoroughly check all the settings you have defined for Microsoft Defender Browser Protection for Google Chrome. Once you confirm everything is correct, select Create to implement the changes.
- Easy Way to Install a Language Pack using Intune PowerShell Script
- Simple Method to Disable Office Online Repair with Intune PowerShell Script
- Intune Automation Collection Community Solution Helps to Build Workflows with PowerShell Scripts and More
Monitor the Microsoft Defender Browser Protection for Google Chrome Deployment
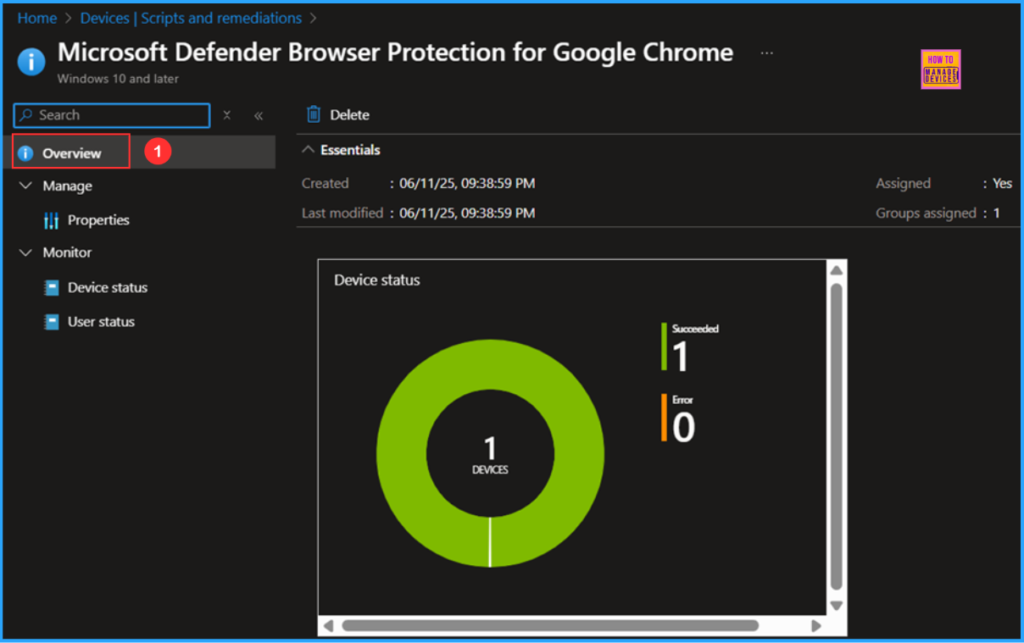
This Intune PowerShell Script has been deployed to the Microsoft Entra ID group (HTMD – Test Computers). The policy will take effect as soon as possible once the device is synced. To monitor the policy deployment status from the Intune Portal, follow the steps below.
- Navigate to Devices > Windows > Scripts and remediations > Platform scripts
Search for the “Microsoft Defender Browser Protection for Google Chrome” Script. The deployment status for this script can be seen under the Overview status. We can see that both the Device and User statuses have succeeded.
End User Experience
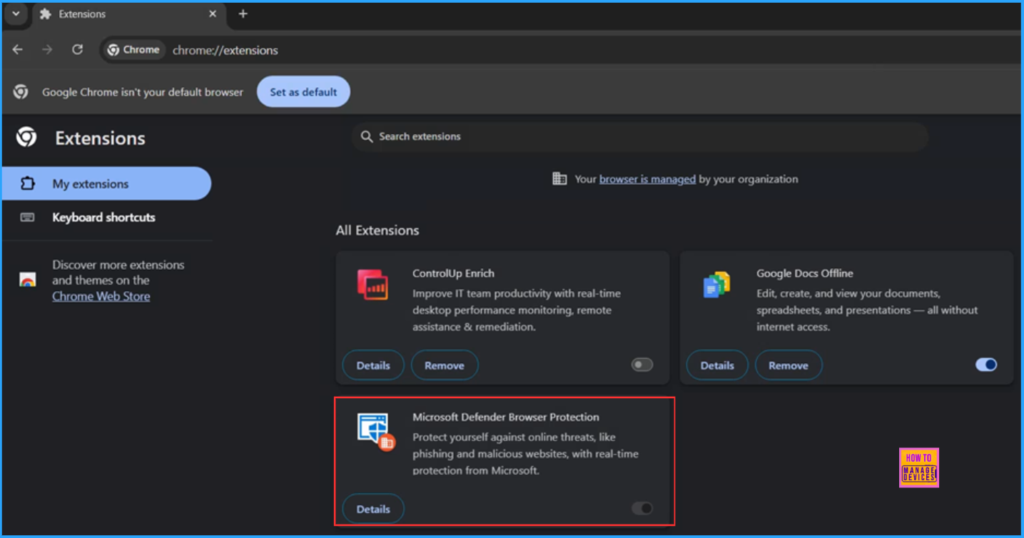
We need to verify if the Intune PowerShell Script has installed the Google Chrome Microsoft Defender Browser Protection Extension. Log in to one of the targeted devices for the policy. Open the Google Chrome browser and follow the path below.
- Click on the three dots in the top right corner of the browser > Extensions > Manage Extensions > My Extension
Microsoft Defender Browser Protection is now successfully installed, providing you with enhanced security for your browsing experience.
Functionality Test – Microsoft Defender Browser Protection Extension
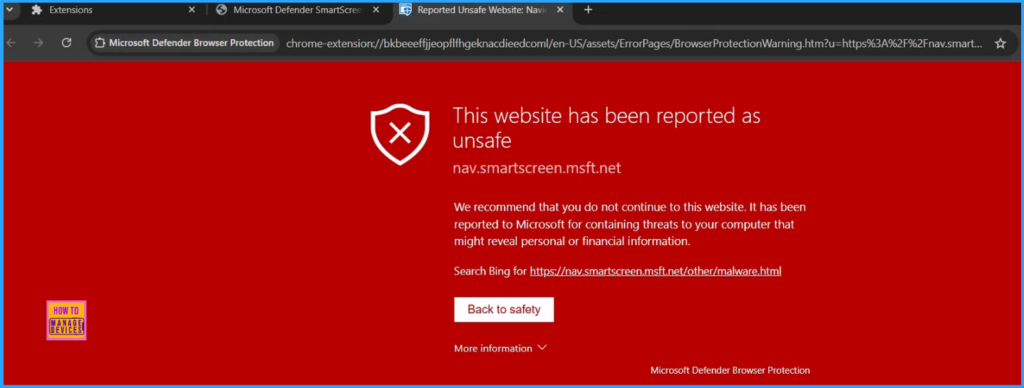
Now we can verify whether the Microsoft Defender Browser Protection Extension is functioning as expected. To test various scenarios, please visit this URL https://demo.smartscreen.msft.net/. You can assess situations such as Is This Phishing, Phishing Page, Malware Page, Blocked Download, Potentially Unwanted Download, and Exploit Page, Malversating etc. among others. Additionally, there are some App Rep Demos available for review.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Vaishnav K has over 11 years of experience in SCCM, Device Management, and Automation Solutions. He writes and imparts knowledge about Microsoft Intune, Azure, PowerShell scripting, and automation. Check out his profile on LinkedIn.



As of 18 June, 2025, this will only work if the workstation is Active Directory domain joined (meaning hybrid joined since this is an Intune policy). What happened for me is the registry entry was successfully created but no extension. Microsoft Edge works. I tweaked the script a bit to work with Edge since this is documented to work with Edge without being Active Directory domain joined. Here is what I changed in the script:
$UpdateURL = https://edge.microsoft.com/extensionwebstorebase/v1/crx
$RegPath = “HKLM:SOFTWARE\Policies\Microsoft\Edge\ExtensionInstallForcelist”
The last line in the script to: Write-Host “Extension $ExtensionId configured for force installation in Microsoft Edge.”
I learned a lot from this article. Thank you for posting
Source for Active Directory status: https://learn.microsoft.com/en-us/deployedge/microsoft-edge-browser-policies/extensioninstallforcelist
Hi Brad, Thank you for your valuable feedback. I have modified the script, and it is now working as expected in the Google Chrome browser. You can download the new script from my GitHub repo: https://github.com/VaishnavKuruvaikandy/Intune/blob/main/MicrosoftDefenderBrowserProtection_Google%20Chrome_New.ps1