Hello everyone, today let’s learn how to enroll iOS devices as Account-Driven Apple User Enrolment in Intune. With the release 2305, Intune started supporting Account driven Apple user enrolment. This feature is still in the Preview stage.
With this type of enrolment, users can enroll the iOS/iPadOS devices without requiring a Company portal app. This type of enrolment is faster than with the Company Portal app. Personal and corporate data are separated and protected in this type of enrolment.
The Management capabilities on the devices enrolled with this method are limited to the required capabilities to control the organization’s data. These devices are not supervised devices. This type of enrolment is only for BYOD scenarios. As the devices are owned by users, Apple provides a limited set of payloads and restrictions that are applied to devices by any Mobile device Management Solution.
We have divided this into two parts, the first part of the series. This part will cover how to federate Microsoft Azure with an ABM account and enable Directory sync to create Manage Apple ids with the organization’s accounts.
- How to setup Microsoft Enterprise SSO plug-in for Apple macOS Devices using Intune
- Intune Supports Zebra OEMConfig App for Android Enterprise 11+ Devices
Even though limited capabilities, Intune will control all the managed content and limited control over personal data and settings. In this article, we will discuss the prerequisite for enabling Account Driven user enrolment. Let’s see what the prerequisite are in the below table.
| Prerequisite |
|---|
| Apple Business Manager Account |
| Set Intune as MDM Authority |
| Apple Push Notification Certificate |
| Managed Apple IDs for users |
Apple Business Manager Account
I know what you are thinking, why do we need an ABM account for Account driven User enrolment? Let me explain it to you, for user enrollment, Managed Apple ids are mandatory. Managed Apple ids can be created only from Apple Business Management Account, so the organization must have an ABM account.
Creating an ABM account may take up to a week, as Apple will contact us, validate the organization details provided, and create an account for your organization. We have created a very good video on creating an ABM Account and the requirements for creating the Account; everything is well captured in the video below.
Set Intune as MDM Authority
Setting Intune as MDM Authority is the first and foremost step before starting the rollout of Intune to users. This will determine how devices are managed in Intune. Microsoft supports four types of configurations.
- Intune Standalone
- Intune Co-management
- Basic Mobility and Security for Microsoft 365
- Basic Mobility and Security for Microsoft 365 Coexistence
Based on your organizational requirement, you can configure the MDM Authority. In our case, we are Makig Intune Standalone as MDM Authority. With this, we are choosing Cloud-only management, which provides entire Intune Management capabilities. Let’s see how we can set Intune as MDM Authority.
- Login to Azure Portal with Global administrator account
- Select Azure Active Directory
- Click on Mobility(MDM and MAM)
- Now select Intune MDM Authority and Save
Special thanks to Microsoft for sharing the MDM Authority screenshot.
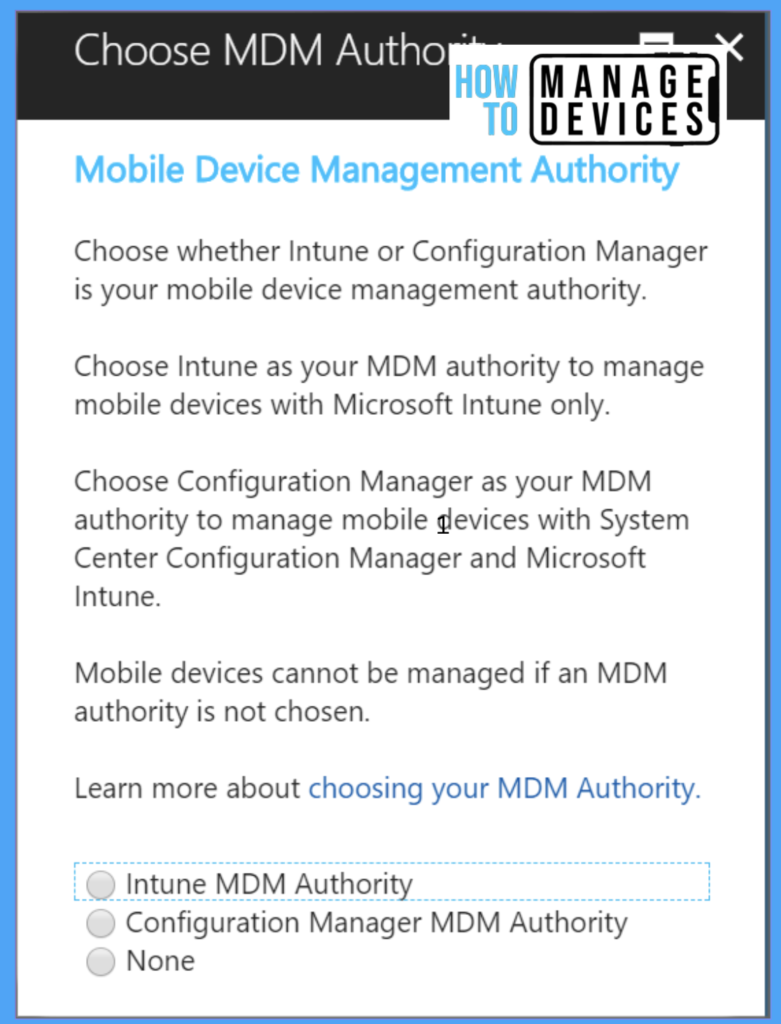
NOTE: Follow the above steps if your tenant is created before the 1911 release. From 1911 and later releases, Microsoft sets MDM Authority automatically to Intune.
Apple Push Notification Certificate
An Apple Push Notification certificate is required for managing iOS/iPadOS/MacOS devices. All the commands, profiles, and configurations sent by the MDM tool will be delivered by APNS. MDM tools maintain continuous communication over a public and private network with Apple devices using APNS. We have created an article on creating an APNS certificate for Intune.
Managed Apple ids for Users
Managed Apple ids are created and owned by your organization. With managed apple ids, users can access Apple services, including 5GB of iCloud. These apple ids are different from personal Apple ids. After creating an ABM account, the Apple administrator can create managed Apple ids for your employees. Managed Apple ids can be created in two ways.
- Create manually
- Create automatically with Federation with Microsft Azure or Google WorkSpace.
When an Apple business administrator creates managed Apple ids manually, the email address for your employees and managed Apple ids email address will be different. The managed apple ids will end with appleid.com. For example, username@yourcompanyname.appleid.com.
When we create Managed apple ids manually, users need to manage two different accounts. To avoid this, we can link the Apple Business Manager account with your Microsoft Azure, users can use the same Account and password of the Domain to login to Apple services. To link your Microsoft account to your ABM account, follow the below section.
Link Domain and Verify
As I mentioned earlier, when we create an ABM account, your Account will be created might be ending with @yourcompanyname.appleid.com. We need to link your organization’s Domain. To link your Domain, please follow the below steps.
- Log in to the Apple Business Manager account with the Administrator account.
- Click on your Account and click on Preferences.
- Click on Domain. You might see a domain already configured, the default one created while creating an ABM account.

Click on Edit and click on Add Domain > enter your domain name. After validation, your Domain will be listed under Domains.
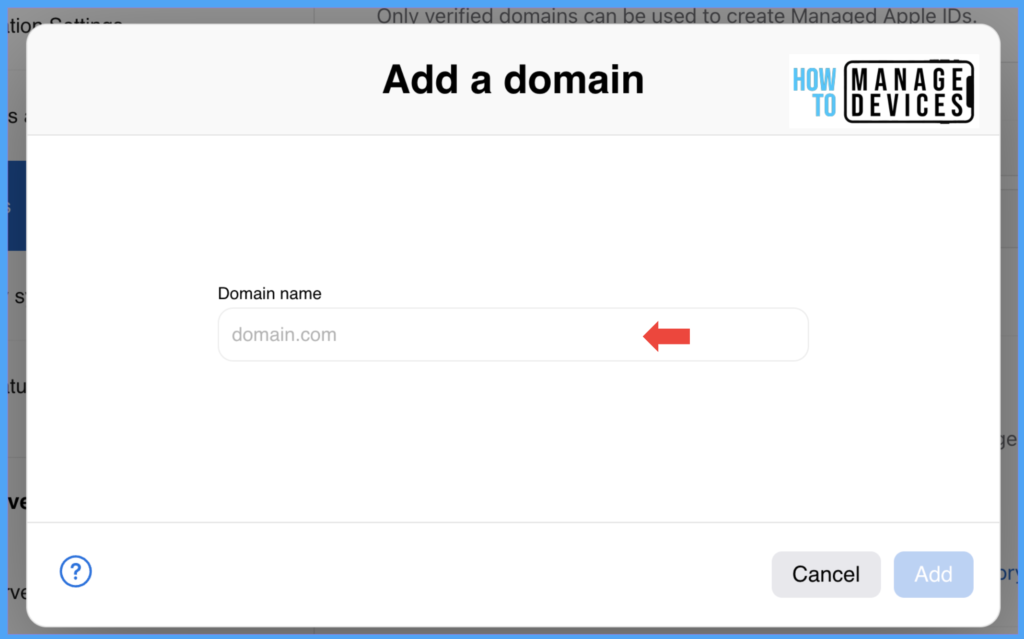
Now we need to verify the Domain. Only verified domains can sync/be federated with an ABM account. A text record is generated and valid for 14 days. We need to create a custom Txt record on your DNS hosting provider. After creating the txt record, click on check now, this will verify the Domain.
Federation with Microsoft Azure
Now we have successfully verified our Domain, we can federate with Azure Active Directory. ABM allows you to federate with Google Cloud service and Microsoft Azure for federation. In our case, we will federate Microsoft Azure. Please follow the below steps to federate your Microsoft Azure.
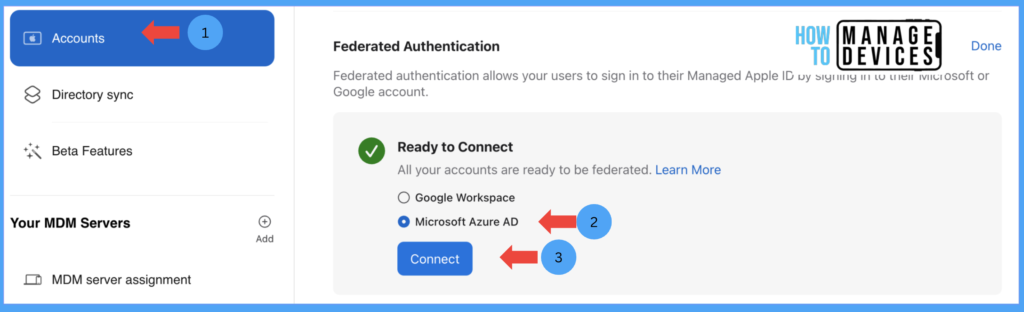
- Log in to the Apple Business Manager account with an Administrator account.
- Click on your Account and click on Preferences
Click on Accounts, and click on federated accounts, Click on Edit, and We can federate ABM accounts with 2 services, Microsoft Azure or Google WorkSpace. As we are using Microsft Azure, select Microsoft Azure and click Connect, This will open a window asking to sign into Microsoft Azure.
Sign in to Azure with admin credentials, and the user must have any of the Azure administrative roles Application Administrator, Cloud Application Administrator, or Global Administrator.

After successful authentication, the Admin requests admin consent to add the Apple Business Manager application. Read the permissions, and click on Accept
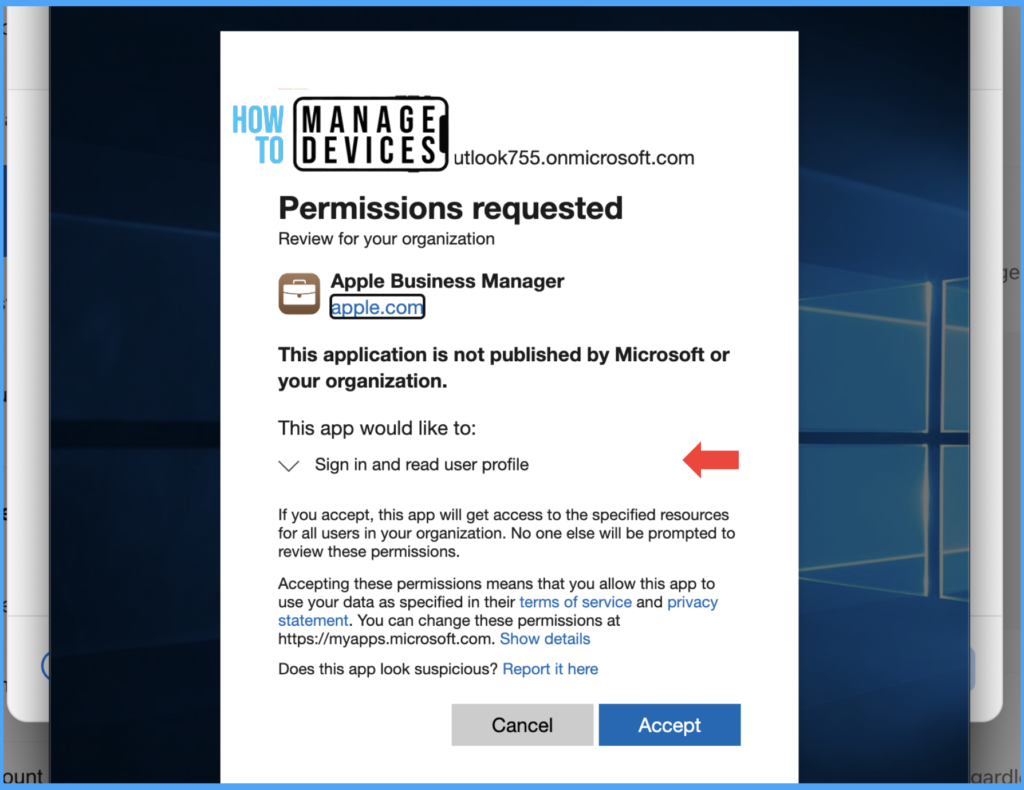
Now click on Done. We successfully federated the Azure Acitvie directory with the ABM account. This is a one-time activity. We can Federate the ABM account only with either Microsoft Azure or Google Cloud services at a given time.
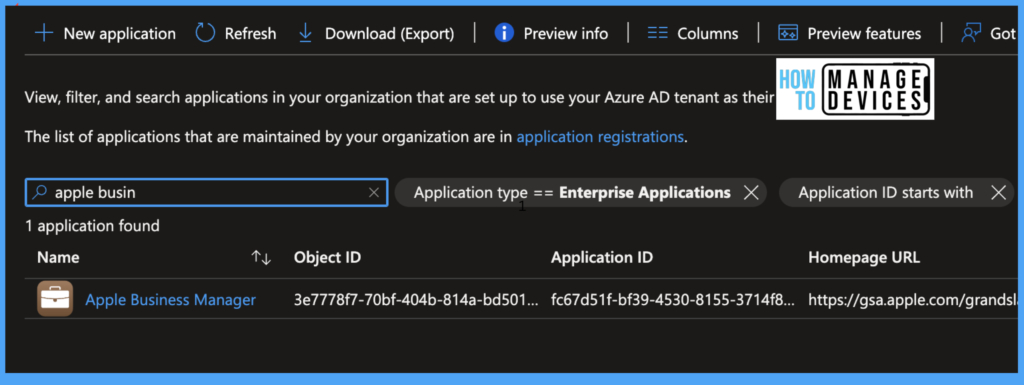
An enterprise application with the name Apple Business Manager is created in Azure. To verify that, log into Azure, click on Azure Active directory, click on Enterprise Applications, and search for Apple Business Manager, you will find an application as the below screenshot.
To create Managed Apple Ids with the organization’s email address, we can use System for Cross-domain Identity Management (SCIM) process. SCIM is an open standard for automating the exchange of user identity information between identity domains and IT systems. All accounts synced to ABM are read-only. Changes made in ABM will not reflect in Azure AD.
Enable Directory Sync
To enable directory sync, we need an Azure admin account with any Azure roles of Application Administrator, Cloud Application Administrator, Application Owner, or Global Administrator. Let’s see how we can enable the directory sync between ABM and Azure Ad.
- Login to ABM account with Administrator account
- Click on your Account and click on Preferences
- Click on Directory Sync
- Click on Enable
- Now, you will get a prompt to Merge automatically or Merge Manually the existing Accounts.

Users may have created Apple accounts using your organizational accounts. In this case, we need to choose any of the options. When we choose Merge existing accounts automatically, users will get an email notification to convert.
Note: If users have apple ids which are created using the organization email address, they will get an email notification saying their organization email address will be changed to managed apple id and change it to the personal email address as this apple id all the data will be transferred to their new personal apple id. Users will have 14 days to convert.
After selecting the required option, a secret token and URL are generated. We need to add these details in Apple Business App created in Azure. Click on Copy to copy the secret token.
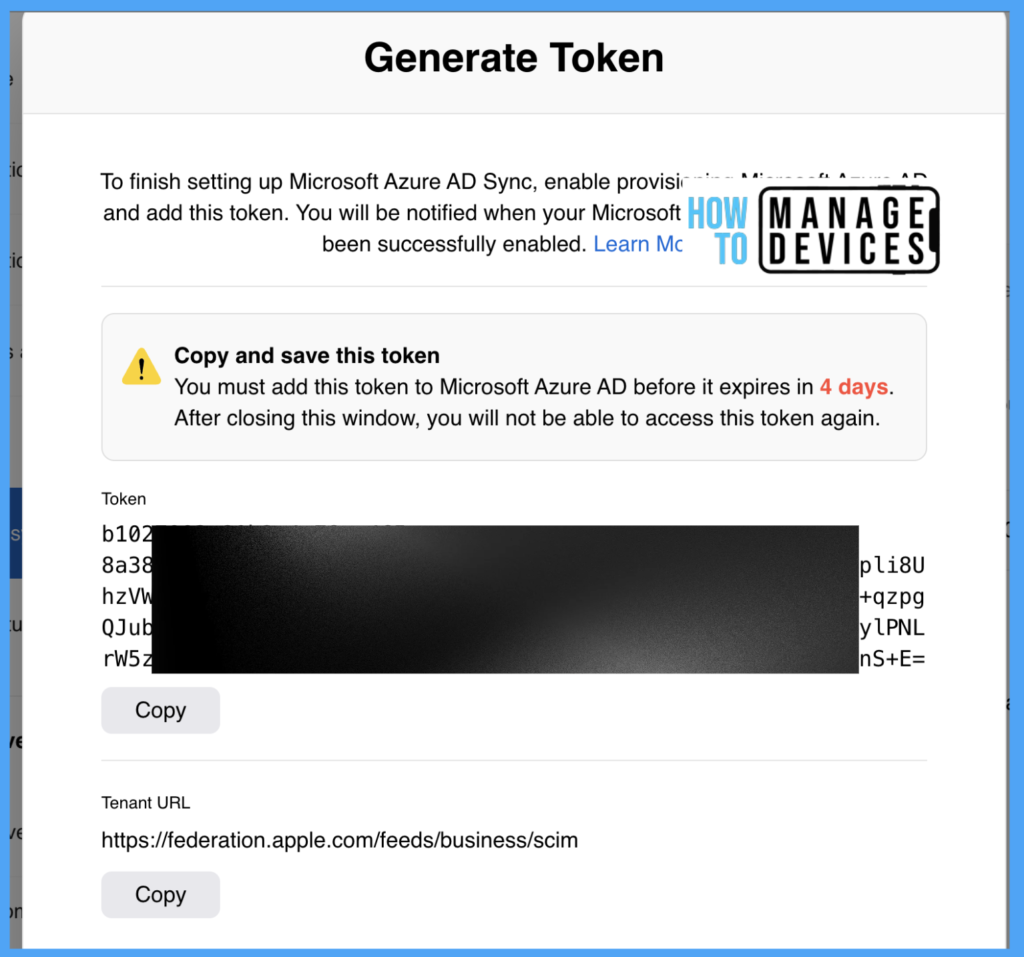
Log in to the Azure portal with the required Azure role to add the details. Click on Enterprise Applications, and search for the Apple Business Manager application. Now Click on Provisioning.
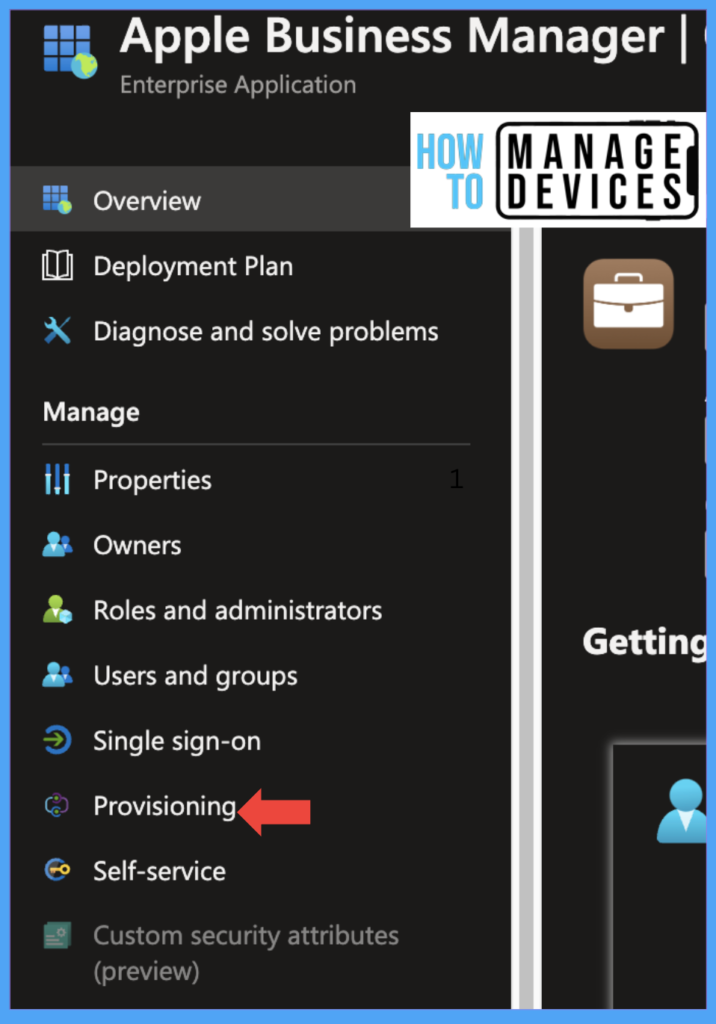
In the Provisioning Overview, click on Start Provisioning, Now click on Provisioning under Admin Credentials, add the Secret Token copied, and add the Tenant URL copied from Directory Sync. We can leave the rest of the settings blank or add an email address to get a notification when a failure occurs. Now change Provisioning Status to On and click on Save.
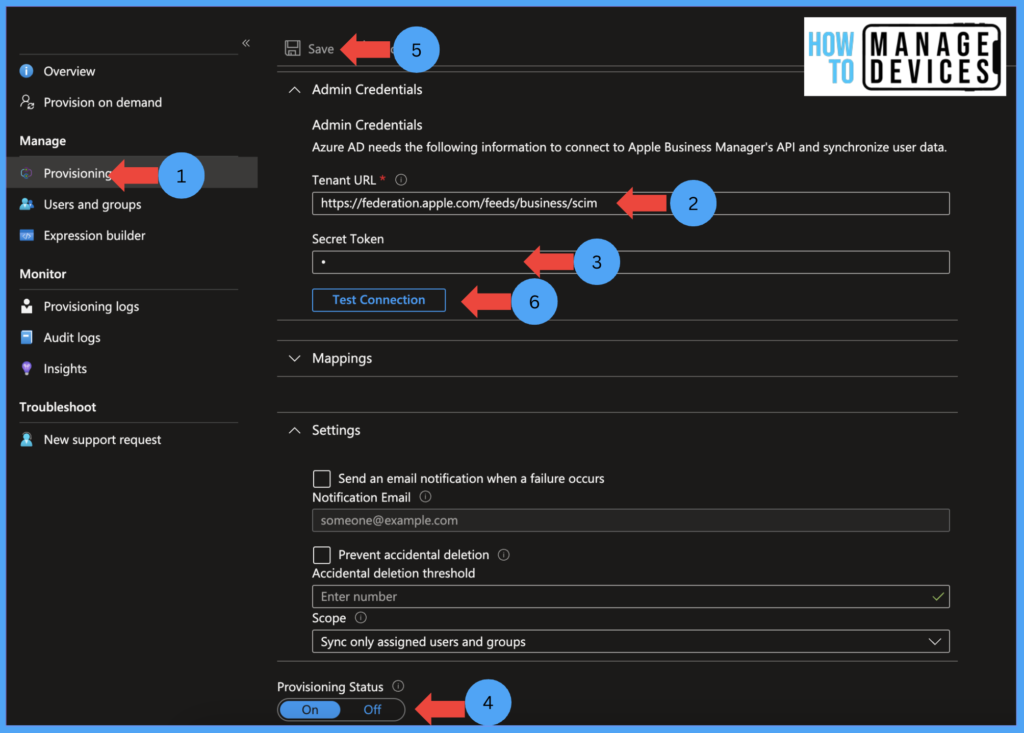
Now click on Test Connection under Admin Credentials section to test the connection between ABM and Azure. We can sync all Azure accounts or specific users or groups to ABM. To add specific users or groups, click on Users and Groups and click on Add users or groups and add groups.
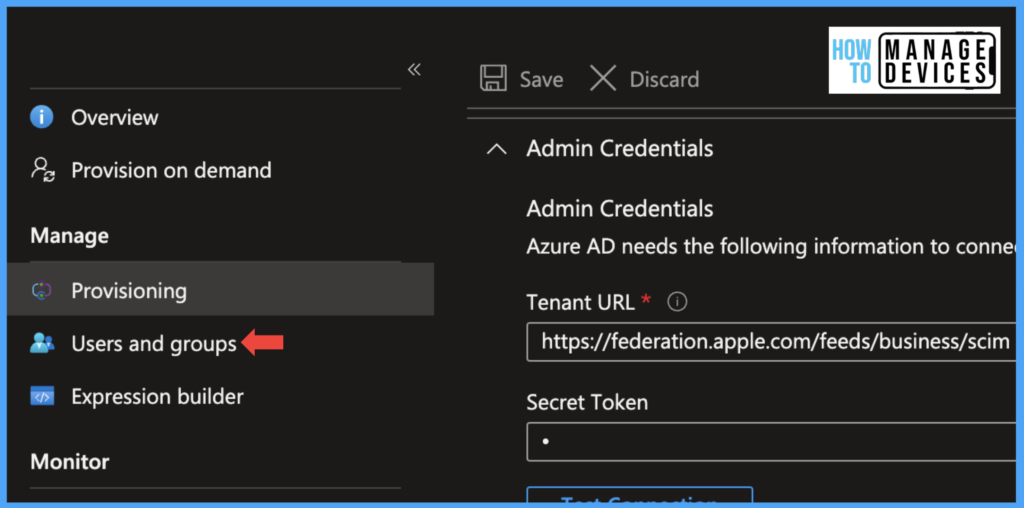
The initial sync will take longer, up to 40 mins, compared to the next sync cycles. Now check if you can view the sync successfully. If you are facing issues like those in the screenshot below, this is due to the Domain is not federated.

Now click on Accounts, Edit under Domain, select your Domain, and click Federate.
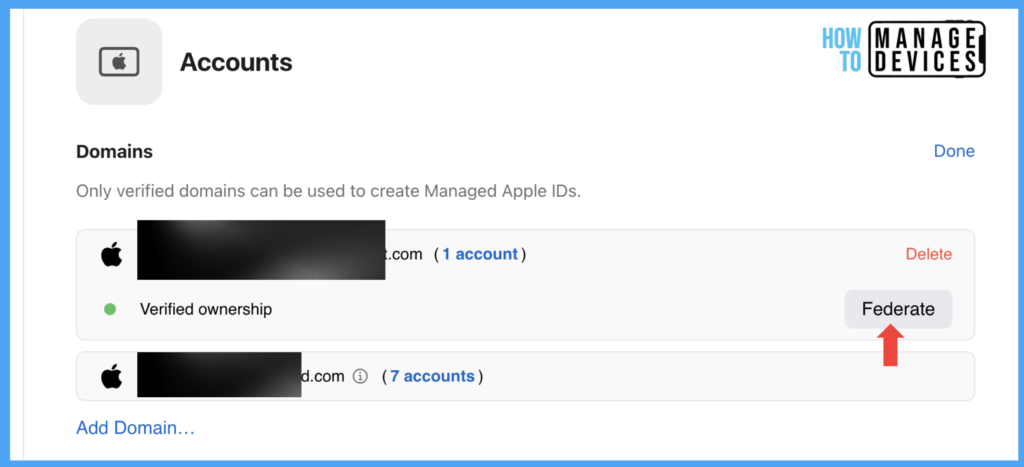
Sign in to Azure with the same credentials in order to federate. After successful login, your Domain will be Federated, and Ad accounts will be synced.
All the AD accounts synced will have a staff role assigned to them by default. These roles can be changed to provide access to the ABM account. All the managed apple ids created will have an iCloud storage of 5GB and features of personal apple ids. But these managed apple ids are controlled by your organization’s IT admins.
Conclusion
By this, we come to the end of part 1 of the series and will discuss what configurations need to make in Intune to enable Account-Driven Apple User Enrolment and Enrolling an iOS device in part 2. Till then, have happy learning.
Author
About Author – Narendra Kumar Malepati (Naren) has 11+ years of experience in IT, working on different MDM tools. Over the last seven years, Naren has been working on various features of Intune, including migration from different MDMs to Intune. Naren mainly focuses on Android, iOS, and MacOS.

Hello Narendra Malepati,
First of all thx for all the worthful articles. I would like to know when part 2 of this article is being published ?
Kind regards