Hello Everyone! In this post, let’s see how to set up a Microsoft Enterprise SSO plug-in for macOS Devices using Intune. We will give a quick overview of SSO, the Microsoft SSO plugin, and how to set up the Microsoft SSO plug-in for Apple macOS devices.
In our last blog post How to Deploy Microsoft Edge in MacOS using Intune, we discussed an overview of the Microsoft Edge browser, the prerequisites to deploy the Microsoft Edge browser, and the configuration settings while deploying Microsoft’s built-in app Edge in quick, easy steps using Microsoft Intune.
The Microsoft Enterprise SSO plug-in for Azure AD accounts is officially available for Apple devices ( iOS, iPadOS, and macOS). It supports all the applications earlier supported by Apple’s built-in enterprise SSO feature.
The plug-in supports SSO even for old apps not yet upgraded with the latest identity libraries or protocols. Microsoft has worked closely with Apple to develop the plug-in for enhancing the enterprise user experience and providing the best protection available.
Currently, the Enterprise SSO plug-in is a built-in feature in the Intune Company Portal app on macOS devices and the Microsoft Authenticator app on iOS and iPadOS devices.
- Should you upgrade to Mac OS Ventura v13 managed using Intune
- New System Settings in macOS Ventura v13 and Intune Software Update Configs
What is an SSO
Single sign-on (SSO) is an identification method that allows users to smoothly sign in to multiple apps or websites with a single credential over the browser. This feature streamlines the authentication process for users.
So whenever a user is prompted for a login, it skips the step by automatically signing in to applications or websites, which enhances the end-user experience by minimizing the usage of multiple varieties of usernames and passwords across various accounts and services.
SSO works by sharing and verifying users’ login credentials between service and Identity providers. A service provider is a vendor who provides products, solutions, and services to users and organizations. In contrast, An Identity provider is a system that creates, manages, and maintains user identities and provides authentication services to verify users.
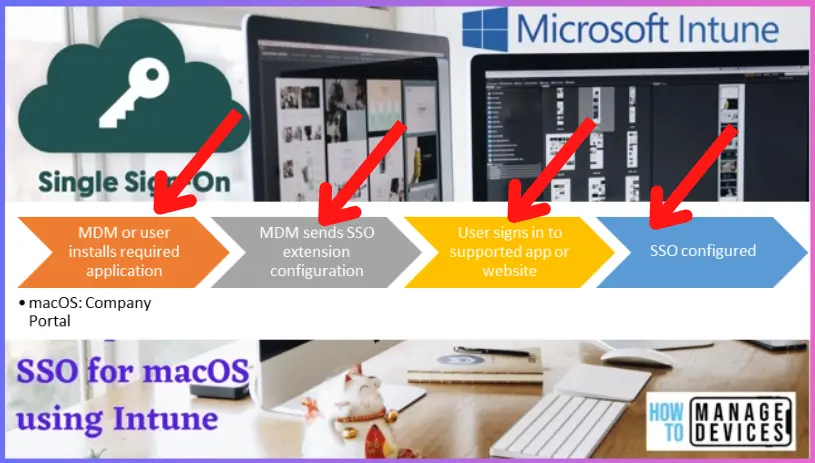
An important thing to consider is SSO services do not store user information or identities. Instead, it matches the user’s login credentials with the data stored in an identity management service or database. A sample Single sign-on can be described in the below steps :
- The user opens up a website or an app (service provider).
- It sends an authentication token to the identity provider, such as the SSO system.
- The identity provider acknowledges and sends a response back to the service provider.
- The user will be prompted to log in.
- Once the user’s credentials are validated, they can access the website or app.
Microsoft Enterprise SSO helps to Increase Security?
Organizations widely use SSOs as they are more secure, however, there are multiple benefits to using an SSO.
- Stronger passwords: As users have to use only a single password, it makes it easier for users to create and remember a stronger password. This also reduces organizations’ risk of cyber attacks because websites have to store less user credential information
- Better password policy enforcement: With one place for password entry, SSO makes it convenient for IT Admins to enforce password security rules easily.
- Single point for enforcing password re-entry: IT Admins can enforce re-entering login credentials after a certain amount of time to make sure the same user is still active on the signed-in device.
- Increased Productivity: In case of password forgetting, IT Admins have to spend less time helping users recover or reset their passwords, increasing business productivity.
- Less Shadow IT Risks: Shadow IT occurs when users avoid the organization’s security policies to use apps, devices, services, or software not sanctioned or authorized for official use. SSO helps organizations avoid this by monitoring which applications employees are using.
Features of Microsoft Enterprise SSO
The Microsoft Enterprise SSO plug-in for Apple devices offers the below features,
- It provides SSO for Azure AD accounts across all apps which support the Apple Enterprise SSO feature.
- It can be enabled by any mobile device management (MDM) solution and is supported in both device and user enrollment.
- It extends SSO to apps that don’t yet use the Microsoft Authentication Library (MSAL)
- It extends SSO to applications that use Authentication methods such as OAuth 2, OpenID Connect, and SAML.
- It is integrated with the Microsoft Authentication Library (MSAL), which provides a smooth end-user experience when the Microsoft Enterprise SSO plug-in is enabled.
Pre-requisite to enable Microsoft Enterprise SSO
To enable the Microsoft Enterprise SSO plug-in for Apple Mac devices, ensure the below steps :
- Intune manages the device.
- macOS should run on Catalina v10.15 or higher.
- Intune Company portal App should be installed on the device to enable the Microsoft Enterprise SSO plug-in.
How to Enable Microsoft Enterprise SSO Plug-in on macOS Devices
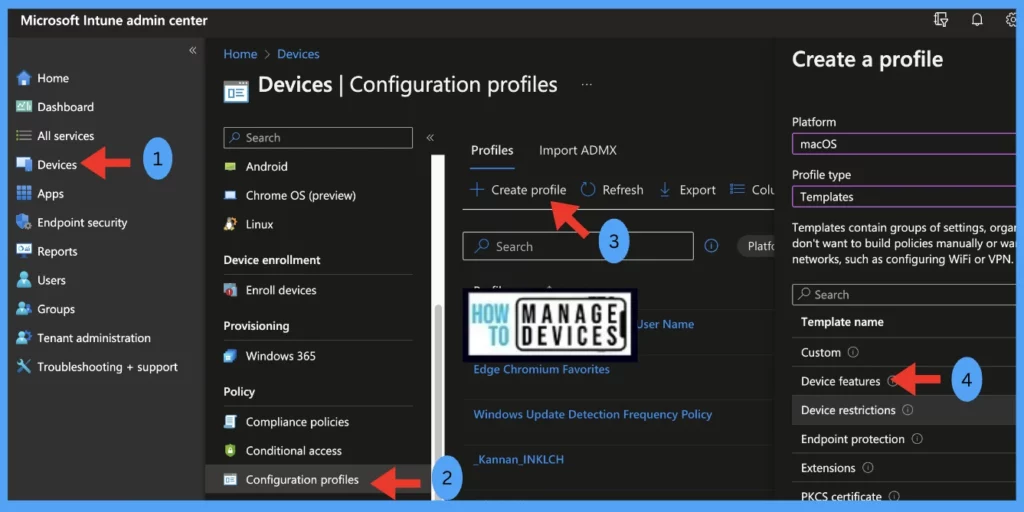
To create a configuration profile, we must ensure the required access to the Intune Portal. Follow the steps mentioned below to create a configuration profile in Intune portal for macOS devices:
- Sign in to the Microsoft Intune admin center https://intune.microsoft.com/.
- On the left sidebar, select Devices > under Policy, select Configuration profiles.
- The list of existing configuration profiles will be reflected on the right side. To create a new profile, click on Create Profile.
- Select the correct categories for Profile creation,
- Platform – macOS
- Profile type – Templates, and Select Device Features
- Click on Create.
Once you click on Create button from the above page, Provide the Name and Description and click on Next.
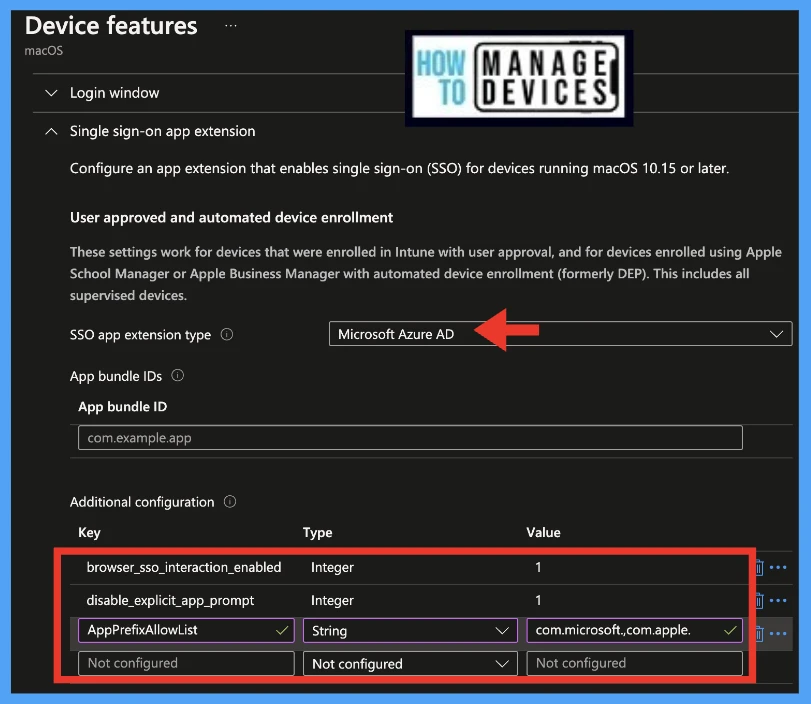
Under the Configuration settings tab, select Single sign-on app extension, and configure the following properties:
- SSO app extension type: Select Microsoft Azure AD
- App bundle ID: Enter a list of bundle IDs for apps that don’t support Microsoft Authentication Library (MSAL) and are allowed to use the SSO feature.
- Additional configuration: To customize the end-user experience, IT Admins may add the following properties. These properties are the default values used by the Microsoft SSO Extension, but they can be customized as per the organization’s needs.
| Key | Type | Description |
|---|---|---|
| AppPrefixAllowList | String | Recommended value: <string value>Enter a list of prefixes for apps that don’t support Microsoft Authentication Library (MSAL) and are allowed to use SSO. E.g., com.microsoft.,com.apple. |
| browser_sso_interaction_enabled | Integer | Recommended value: 1When set to 1, users can sign in from Safari browser, and from apps that don’t support Microsoft Authentication Library (MSAL). Enabling this setting allows users to bootstrap the extension from Safari or other apps. |
| disable_explicit_app_prompt | Integer | Recommended value: 1Some apps might incorrectly enforce end-user prompts at the protocol layer. If you see this problem, users are prompted to sign in, even though the Microsoft Enterprise SSO plug-in works for other apps. When set to 1 (one), It reduces prompts for end-users. |
Scope tags are filtering options provided in Intune to ease the admin jobs. In the scope tag section, you will get an option to configure scope tags for the policy. Click on Next.
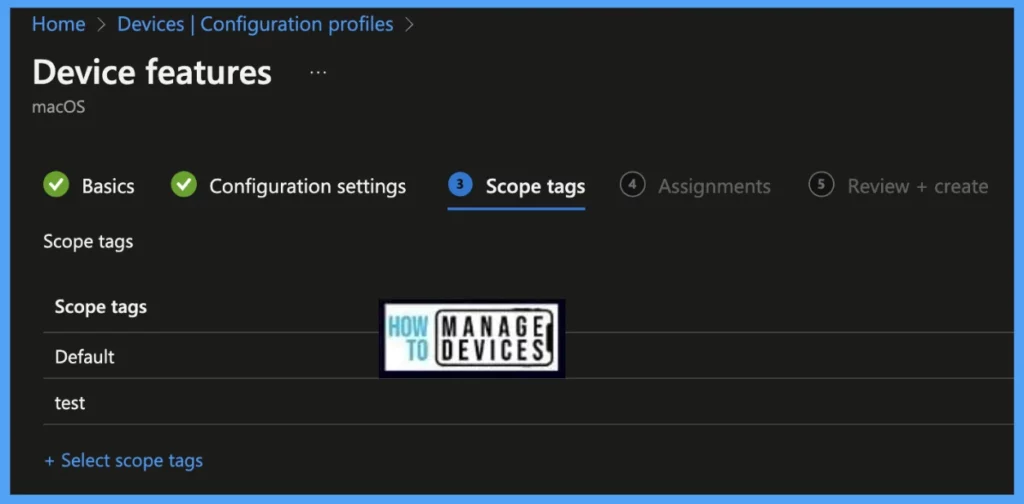
The assignment Group determines who has access to the profile by assigning groups of users to include and exclude. Select Assignments group (Included groups and Excluded groups) and click Next.
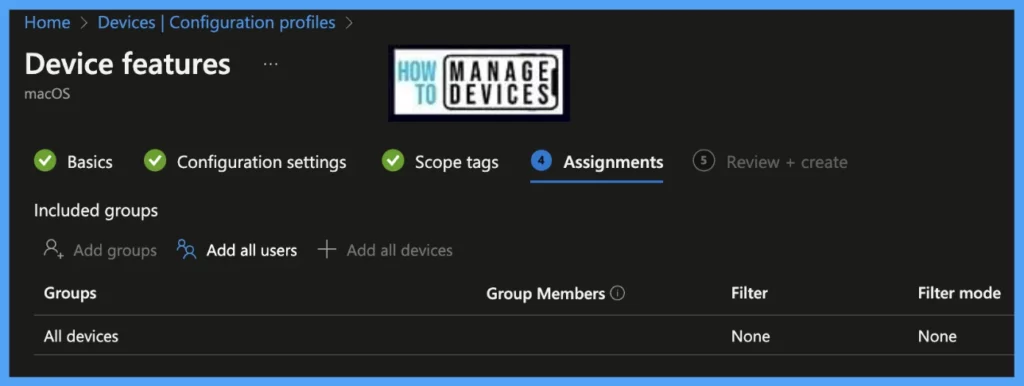
On the Review+create page, please review if any settings need to be changed, or else go ahead and click on Create button.
Once the Configuration Profile is created, it will take a few minutes to get pushed to all of the devices. also, to view the deployment status on the list of devices, we can check by the below ways.
The report reflects the successful deployment of Microsoft Enterprise SSO plug-in settings on macOS devices. To see all the device statuses, Navigate to Devices > Configuration Profiles > Select the Profile, and you can find the list of devices under categories such as below.
- Succeeded
- Error
- Conflict
- Not Applicable

To see the report on the Intune console, you click on the view report button, you can see the list of devices along with their details below :
- Device name
- Logged in User
- Check-in Status
- Last check-in time
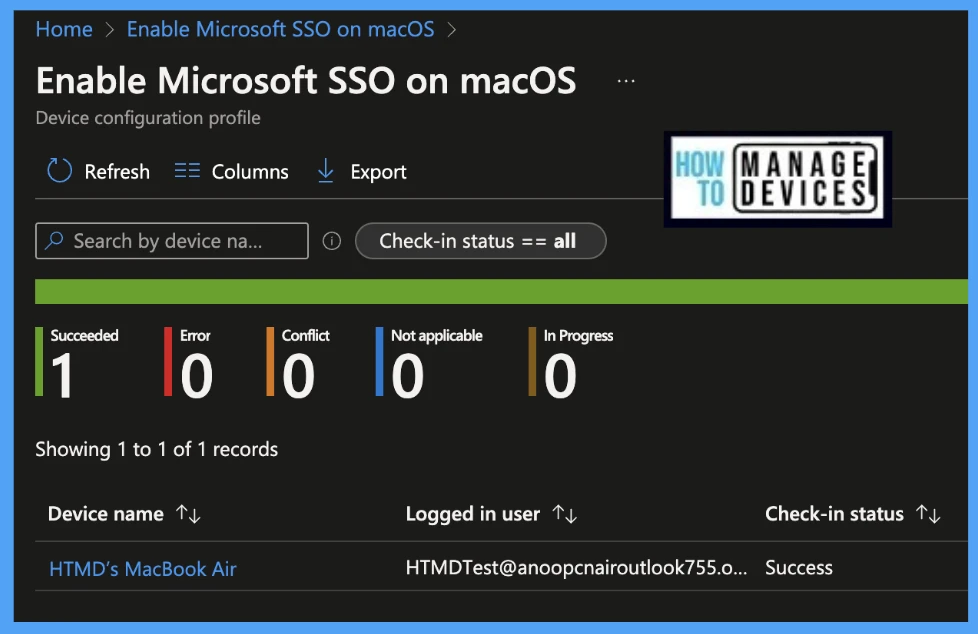
Also, we can view the two different types of reports, you can quickly check the update as devices/users check-in status reports.
Device assignment status, This report will show the list of targeted devices under the configuration profile, including devices in pending policy assignment status. To get the status, click on Generate Report button.
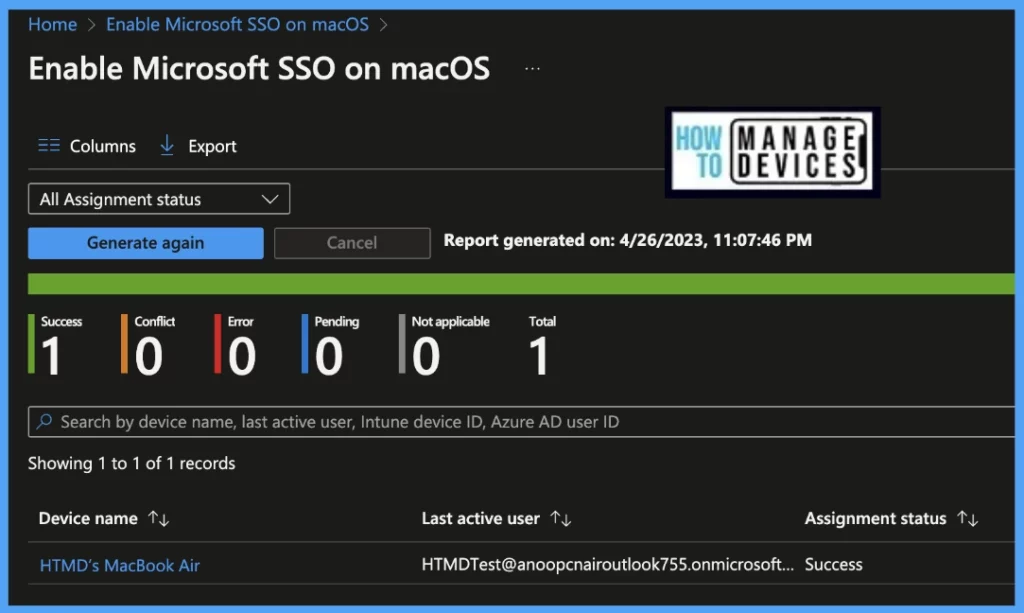
Per settings status, This report will show the configuration status of this policy across all devices and users.
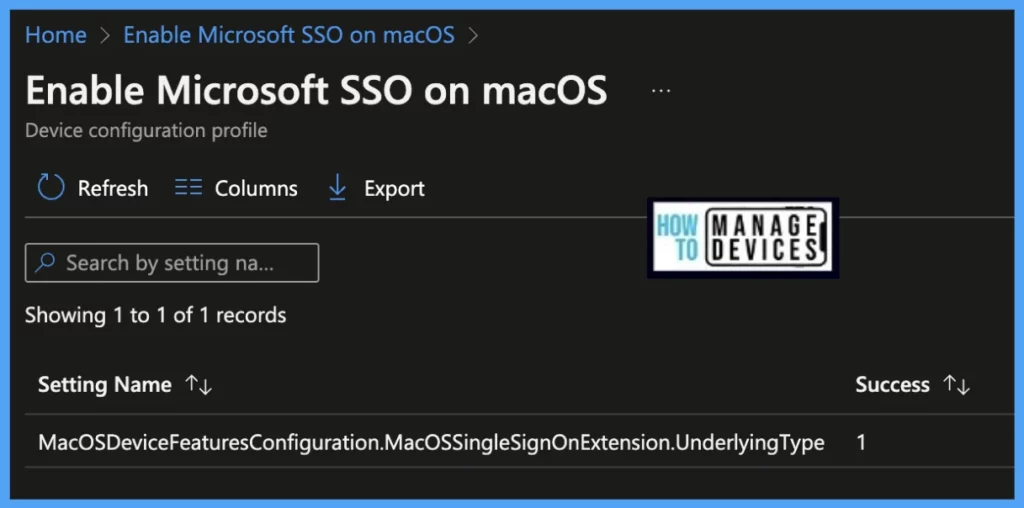
Here’s how you can export Intune setting catalog Profile report from Intune portal. You have two options to navigate to the compliance policies node either you can navigate to the Devices node or Endpoint Security, Intune Settings Catalog Profile Report.
- Enroll macOS in Intune with Step by Step Guide
- Configure macOS Compliance Policy in Intune for Devices
Results – Check if the Microsoft SSO is Enabled on macOS
Once the Profile gets pushed to the list of client macOS devices as part of the assignment group, it may take a few minutes to reflect on the end user’s device. To manually get the policy pushed on the macOS device, launch the company portal app and run check status.
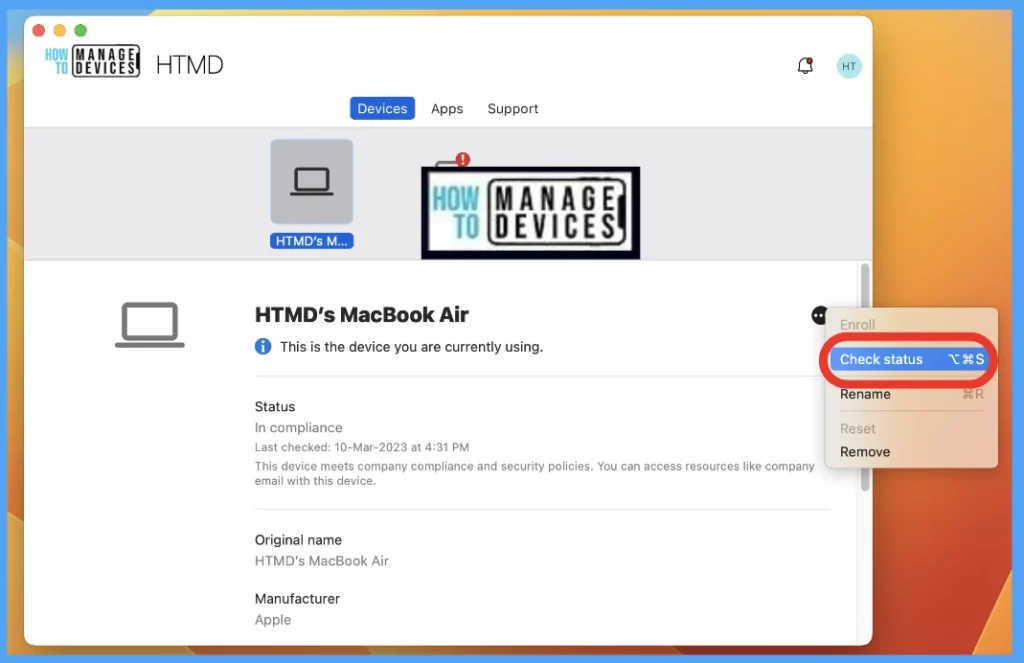
To check the profile status on the client device, we can follow the below steps.
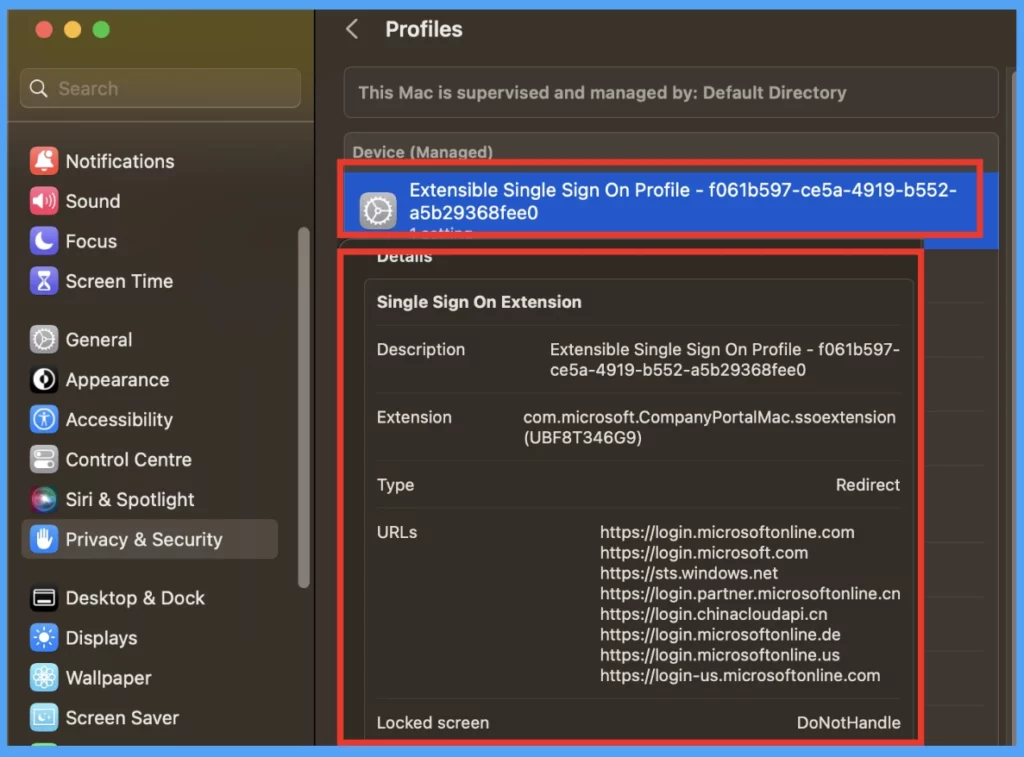
- Click on the Apple icon > Click on System Settings.
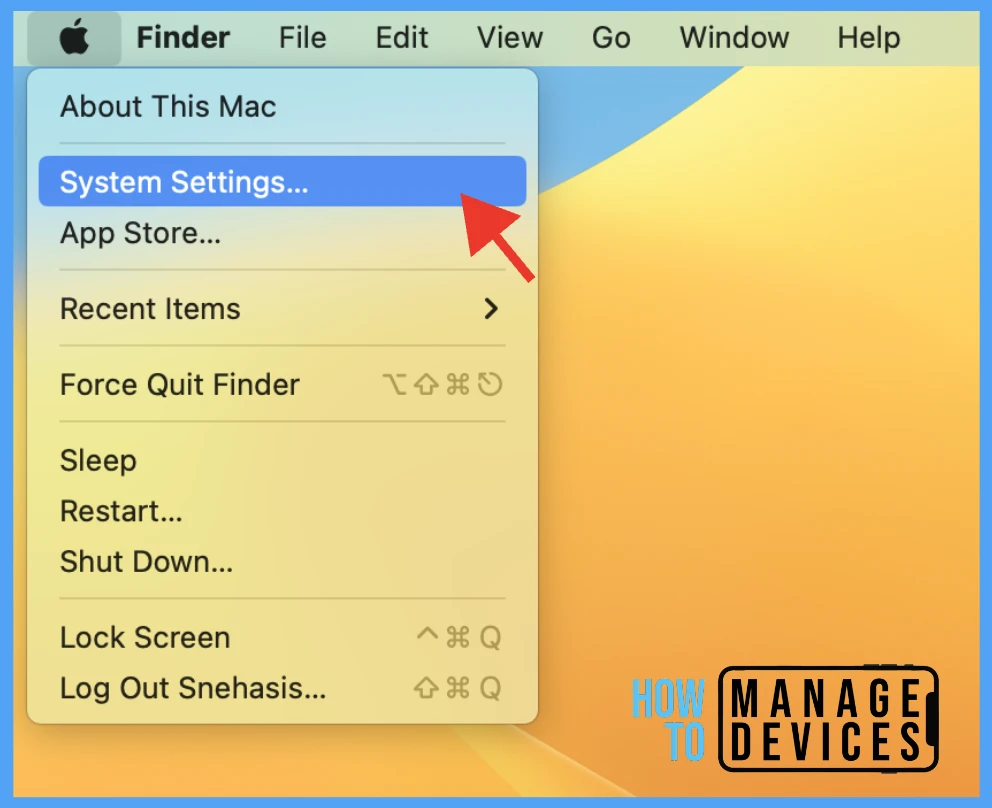
Go to Privacy & Security > Profiles > You can see the deployed profile on the device.
Now let’s have a look at the end-user experience with the configured Microsoft Enterprise SSO plug-in. Here I’ve used a Safari browser on a macOS device, running on macOS Ventura. That experience is shown below where I have tried to launch portal.office.com, and it simply picks the required account.
Conclusion
As we know, organizations implement SSO on Windows devices to enhance the end-user experience, and now thanks to Microsoft’s new feature, the Microsoft Enterprise SSO plug-in is finally available on Apple macOS devices as well. And the best part is the apps/websites that don’t support the MSAL feature yet, can simply be added to the Intune portal by the IT Admins.
Author
Snehasis Pani is currently working as a JAMF Admin. He loves to help the community by sharing his knowledge on Apple Mac Devices Support. He is an M.Tech graduate in System Engineering.

Why did you go for adding the App bundle IDs in AppPrefixAllowList instead of the App Bundle ID setting right above? Does your method have any benefit over the other?
Hi Dennis,
Thanks for asking.
App bundle IDs specify specific apps for SSO, whereas Appprefixallowlist allows all apps with matching prefixes to participate in SSO.
Hope that answers your question.
Does this only work in Safari? I’ve set up the SSO extension using a Jamf Config Profile and though we are seeing success in Safari, no other browsers are able to leverage this feature.
Applications that do not use Apple Networking technologies (like WKWebview and NSURLSession) will not be able to use the shared credential (PRT) from the SSO Extension.
Both Google Chrome and Mozilla Firefox fall into this category. Even if they are configured in the MDM configuration profile, the result will be a regular authentication prompt in the browser.
If edge is configured in this way, can sso also be implemented
Hi, what about if user password reset, have problem that password expired for mac OS users not reflected om their devices, meaning when the password is expired on AD user can still access al office365 resources with old passwords.