This post helps in learning how to set Ambient Authentication for InPrivate and Guest Profiles Policy Using Intune. We will explore how to apply this policy using Intune’s Configuration Profiles. The main goal is to acquire understanding and hands-on experience in effectively configuring and setting Ambient Authentication for InPrivate and Guest Profiles Policy Using Intune.
Ambient authentication is a feature in Microsoft Edge that allows websites to use HTTP authentication with default credentials when explicit credentials are not provided through NTLM (Windows Integrated Authentication), Kerberos, or Negotiate (SPNEGO) challenge/response schemes. It automatically uses your Windows credentials to authenticate you on websites, making the login process seamless and transparent.
Ambient Authentication is a form of HTTP authentication using default credentials when explicit credentials are not provided via NTLM/Kerberos/Negotiate challenge/response schemes. If you set the policy to “RegularOnly” (value 0), ambient authentication will only be allowed for Regular sessions. InPrivate and Guest sessions will not be allowed to authenticate ambiently.
If you set the policy to “InPrivateAndRegular” (value 1), ambient authentication will be allowed for InPrivate and Regular sessions. Guest sessions will not be allowed to authenticate ambiently. If you set the policy to “GuestAndRegular” (value 2), ambient authentication will be allowed for Guest and Regular sessions. InPrivate sessions will not be allowed to authenticate ambiently.
If you set the policy to “All” (value 3), ambient authentication will be allowed for all sessions, including Regular, InPrivate, and Guest. Please note that ambient authentication is always permitted on Regular profiles. In Microsoft Edge versions 81 and later, if the policy is not set, ambient authentication will be enabled in Regular sessions only.
- Setting Up MS Edge Homepage using Intune
- Force Sync of Browser Data without Consent Policy using Intune
Ambient Authentication for InPrivate and Guest Profiles Policy Using Intune
To set Ambient Authentication for InPrivate and Guest Profiles Policy Using Intune, follow the steps stated below:
- Sign in to the Intune Admin Center portal https://intune.microsoft.com/.
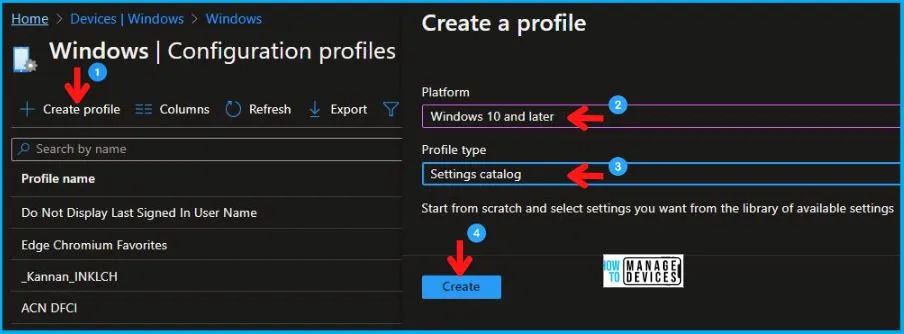
- Select Devices > Windows > Configuration profiles > Create a profile.
In Create Profile, Select Windows 10 and later in Platform, and Select Profile Type as Settings catalog. Click on Create button.
| Platform | Profile Type |
|---|---|
| Windows 10 and later | Settings Catalog |
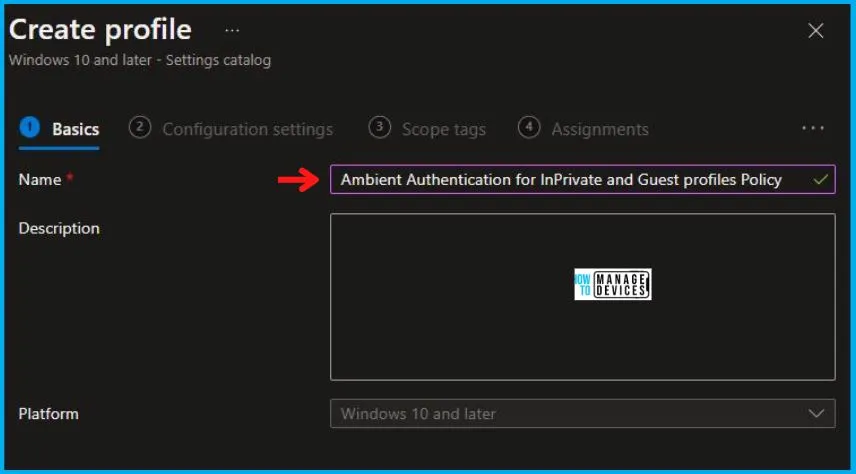
On the Basics tab pane, provide a name for the policy as “Ambient Authentication for InPrivate and Guest Profiles Policy.” Optionally, you can enter a description for the policy and then proceed by selecting “Next.
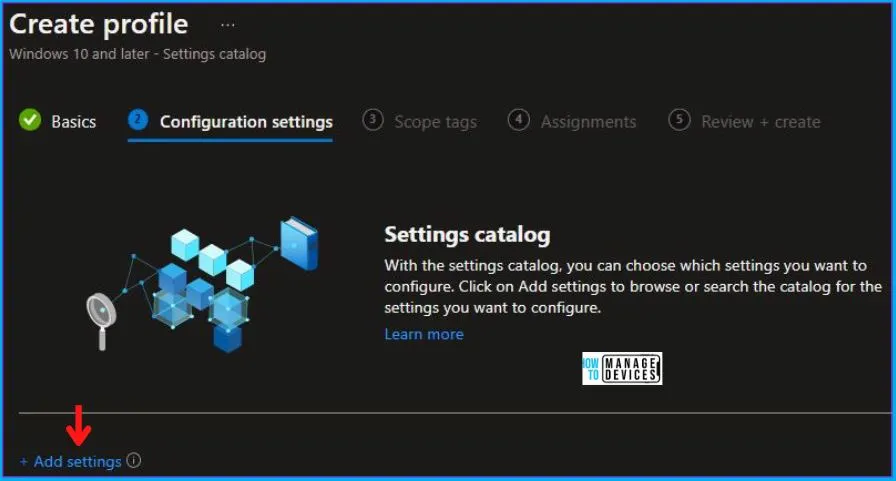
Now in Configuration Settings, click Add Settings to browse or search the catalog for the settings you want to configure.
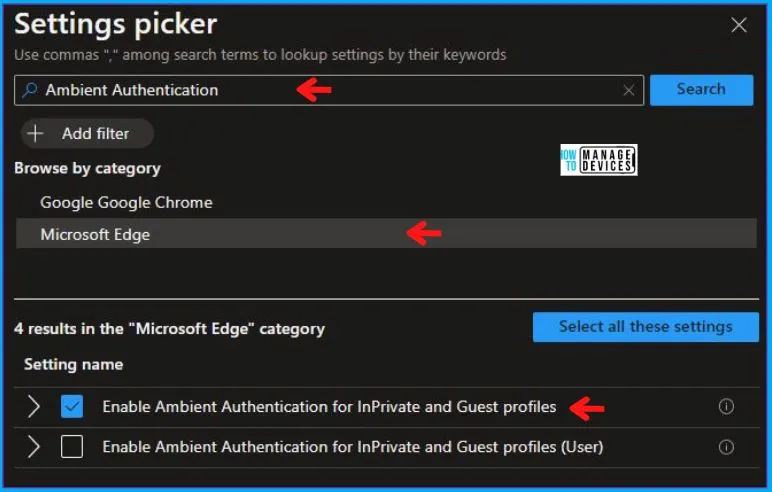
In the Settings Picker windows, search by the keyword Ambient Authentication, you’ll get the category Microsoft Edge, and select this.
When you select the option as stated above, you will see one option, which is Enable Ambient Authentication for InPrivate and Guest profiles. After selecting your setting, click the cross mark at the right-hand corner, as shown below.
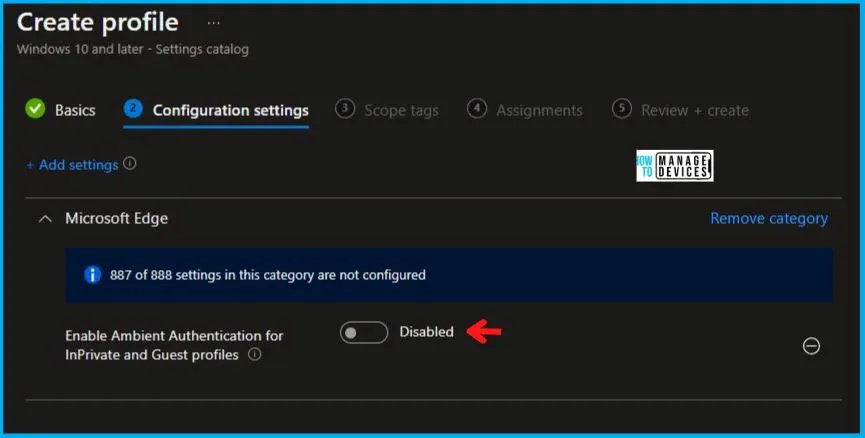
Now, in the Administrative Templates, set Enable Ambient Authentication for InPrivate and Guest profiles to Disabled, as shown below in the image.
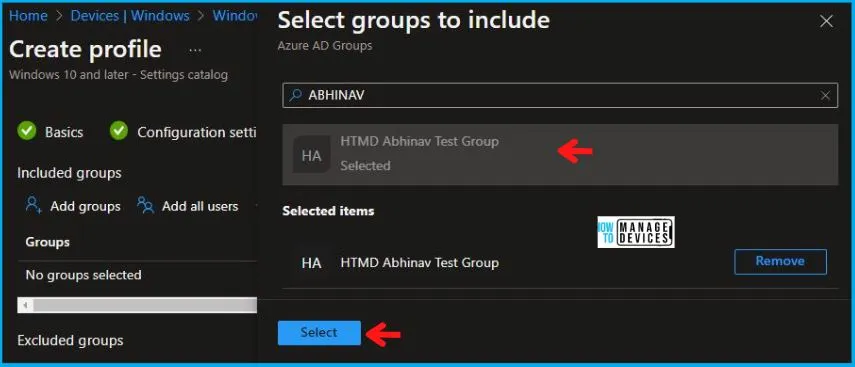
Using Scope tags, you can assign a tag to filter the profile to specific IT groups. One can add scope tags (if required) and click Next to continue. Now in Assignments, in Included Groups, you need to click on Add Groups, choose Select Groups to include one or more groups, and click Next to continue.
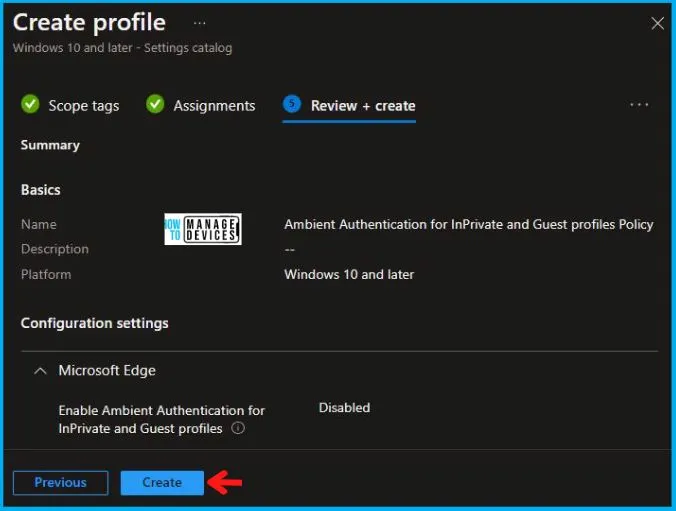
In the Review + Create tab, you need to review your settings. After clicking on Create, your changes are saved, and the profile is assigned.
Upon successfully creating the “Ambient Authentication for InPrivate and Guest Profiles Policy,” notification will appear in the top right-hand corner, confirming the action. You can also verify the policy’s existence by navigating to the Configuration Profiles list, where it will be prominently displayed.
Your groups will receive your profile settings when the devices check in with the Intune service. The Policy applies to the device.
Intune Report for Ambient Authentication for InPrivate and Guest Profiles Policy
From Intune Portal, you can view the Intune settings catalog profile report, which provides an overview of device configuration policies and deployment status.
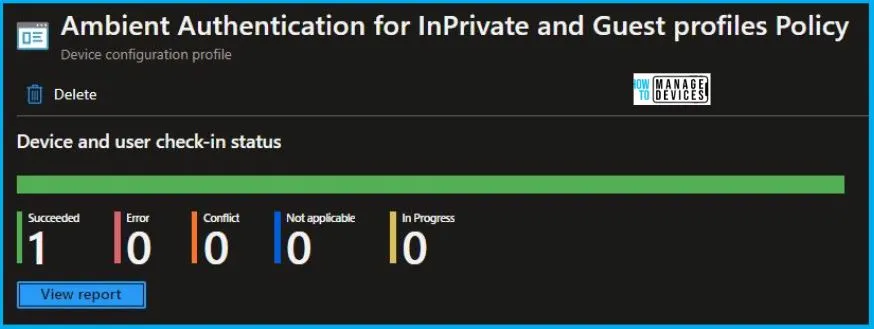
To track the assignment of the policy, you need to select the relevant policy from the Configuration Profiles list. By reviewing the device and user check-in status, you can determine if the policy has been successfully applied. If you require more detailed information, you can click on “View Report” to access additional insights.
Intune MDM Event Log
To verify the successful implementation of String or integer policies on Windows 10 or 11 devices through Intune, you can leverage event IDs 813 and 814. These event IDs provide valuable insights into the application status of the policy as well as the specific value assigned to the policy on those devices. In the case of this particular policy, the value is a String and is linked to the event ID 814.
By analyzing these event IDs, you can gain a clear understanding of the policy’s application status and the corresponding value associated with it on the devices in question.
To confirm this, you can check the Event log path – Applications and Services Logs – Microsoft – Windows – Devicemanagement-Enterprise-Diagnostics-Provider – Admin.
MDM PolicyManager: Set policy string, Policy: (AmbientAuthenticationInPrivateModesEnabled), Area: (microsoft_edgev81 diff~Policy~microsoft_edge), EnrollmentID requesting merge: (FFCDEF31-E97E-4DBE-BE54-1410A26176CC), Current User: (Device), String: (<disabled />), Enrollment Type: (0x6), Scope: (0x0).
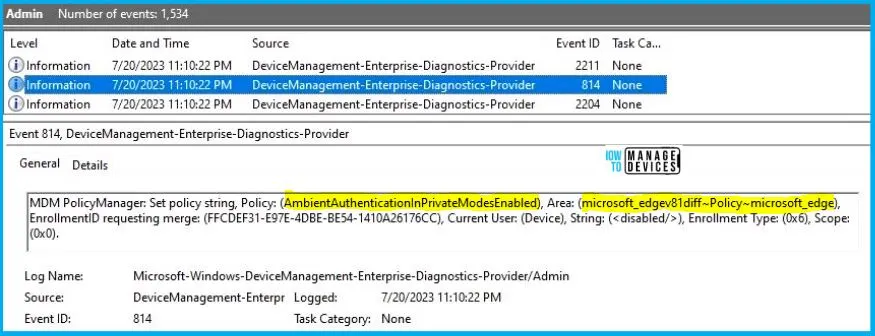
By reviewing the above log entry in the Event Viewer, you will come across essential information, including the Area and Enrollment ID. These details play a significant role in identifying the corresponding registry path. To locate the specific information, please consult the table provided below:
| Area | Policy | String | Scoped | Event ID |
|---|---|---|---|---|
| microsoft_edgev81 diff~Policy~microsoft_edge | AmbientAuthenticationInPrivateModesEnabled | Disabled | Device | 814 |
The details presented in the table above for the Ambient Authentication for InPrivate and Guest Profiles Policy Using Intune can be employed to access the registry settings that hold the group policy configurations on a specific computer. To accomplish this, you can execute “REGEDIT.exe” on the target computer and navigate to the precise registry path where these settings are stored.
- Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\providers\FFCDEF31-E97E-4DBE-BE54-1410A26176CC\default\Device\microsoft_edgev81 diff~Policy~microsoft_edge
When you navigate to the above path in the Registry Editor, you will find the registry key with the name AmbientAuthenticationInPrivateModesEnabled. Refer to the table and image below.
| Registry Name | Data |
|---|---|
| AmbientAuthenticationInPrivateModesEnabled | Disabled |

Author
Abhinav Rana is working as an SCCM Admin. He loves to help the community by sharing his knowledge. He is a B.Tech graduate in Information Technology.

thanks, please try to add screen shot of the results