Let’s check Cloud PC RBAC Roles for Windows 365 Enterprise and Business. RBAC helps Cloud PC Admins to control who can perform various tasks related to Windows 365 Cloud PCs for both Enterprise and Business editions.
Role-based access control (RBAC) helps Cloud PC Admins to control who can perform various Intune tasks within your enterprise. There are Eight (8) Intune RBAC and two (2) built-in Cloud PC roles. You can create custom Cloud PC or Intune roles if none of the provided roles supports your scenario.
Support for custom Windows 365 role-based access control (RBAC) roles are now general availabile. Windows 365 supports the Windows 365 Administrator role available for role assignment through the Microsoft Admin Center and Azure AD.
With this role, you can manage Windows 365 Cloud PCs for both Enterprise and Business editions. By assigning roles to your Cloud PC Admins, you can limit what they see and change. Each role has a set of permissions that determine what users with that role can access and change within your organization.
The Windows 365 Administrator role can grant more scoped permissions than other Azure AD roles like Global Administrator. You can assign built-in roles to groups without further configuration. You can’t delete or edit the name, description, type, or permissions of a built-in role.
| Role | Type |
|---|---|
| Cloud PC Administrator | Built-in Role |
| Cloud PC Reader | Built-in Role |
- Provide Admin Access To Windows 365 Cloud PC Using User Settings Policy
- Windows 365 Cloud PC Hybrid Azure AD Join Vs Azure AD Join
Windows 365 Administrator Role
Users with Windows 365 Administrator role have global permissions on Windows 365 resources, when the service is present. Additionally, this role contains the ability to manage users and devices in order to associate policy, as well as create and manage groups.
Assign the Windows 365 Administrator role to users who need to do the following tasks:
- Manage Windows 365 Cloud PCs in Microsoft Endpoint Manager
- Enroll and manage devices in Azure AD, including assigning users and policies
- Create and manage security groups, but not role-assignable groups
- View basic properties in the Microsoft 365 admin center
- Read usage reports in the Microsoft 365 admin center
- Create and manage support tickets in Azure and the Microsoft 365 admin center
| Actions | Description |
|---|---|
| microsoft.directory/deletedItems.devices/delete | Permanently delete devices, which can no longer be restored |
| microsoft.directory/deletedItems.devices/restore | Restore soft deleted devices to original state |
| microsoft.directory/devices/create | Create devices (enroll in Azure AD) |
| microsoft.directory/devices/delete | Delete devices from Azure AD |
| microsoft.directory/devices/disable | Disable devices in Azure AD |
| microsoft.directory/devices/enable | Enable devices in Azure AD |
| microsoft.directory/devices/basic/update | Update basic properties on devices |
| microsoft.directory/devices/extensionAttributeSet1/update | Update the extensionAttribute1 to extensionAttribute5 properties on devices |
| microsoft.directory/devices/extensionAttributeSet2/update | Update the extensionAttribute6 to extensionAttribute10 properties on devices |
| microsoft.directory/devices/extensionAttributeSet3/update | Update the extensionAttribute11 to extensionAttribute15 properties on devices |
| microsoft.directory/devices/registeredOwners/update | Update registered owners of devices |
| microsoft.directory/devices/registeredUsers/update | Update registered users of devices |
| microsoft.directory/groups.security/create | Create Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/delete | Delete Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/basic/update | Update basic properties on Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/classification/update | Update the classification property on Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/dynamicMembershipRule/update | Update the dynamic membership rule on Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/members/update | Update members of Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/owners/update | Update owners of Security groups, excluding role-assignable groups |
| microsoft.directory/groups.security/visibility/update | Update the visibility property on Security groups, excluding role-assignable groups |
| microsoft.directory/deviceManagementPolicies/standard/read | Read standard properties on device management application policies |
| microsoft.directory/deviceRegistrationPolicy/standard/read | Read standard properties on device registration policies |
| microsoft.azure.supportTickets/allEntities/allTasks | Create and manage Azure support tickets |
| microsoft.cloudPC/allEntities/allProperties/allTasks | Manage all aspects of Windows 365 |
| microsoft.office365.supportTickets/allEntities/allTasks | Create and manage Microsoft 365 service requests |
| microsoft.office365.usageReports/allEntities/allProperties/read | Read Office 365 usage reports |
| microsoft.office365.webPortal/allEntities/standard/read | Read basic properties on all resources in the Microsoft 365 admin center |
Windows 365 Cloud PC built-in Roles
Let’s check the built-in Cloud PC RABC roles available in the Intune admin center portal. Two built-in roles are available for Cloud PC:
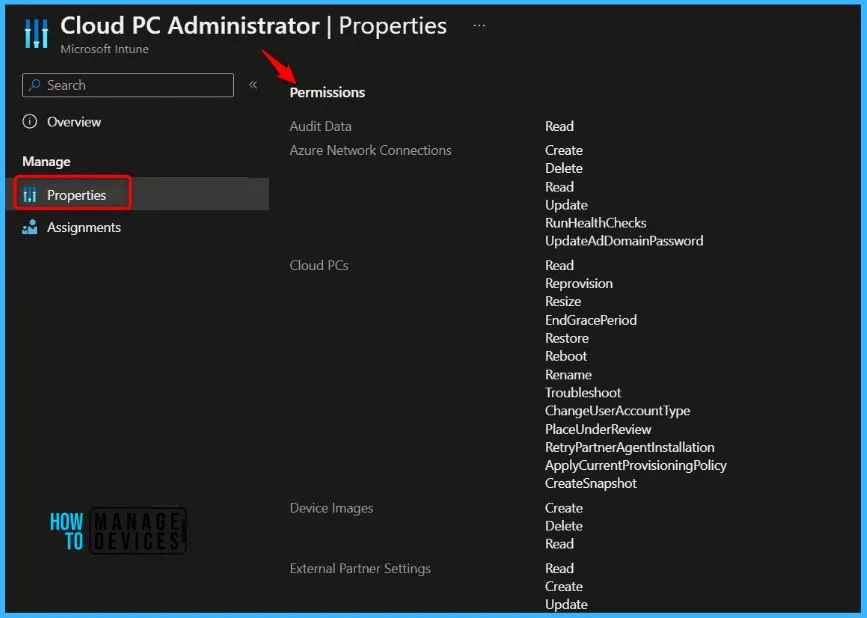
Cloud PC Administrator: Manages all aspects of Cloud PCs, like: Assign administrators to Endpoint Manager Roles. Create and configure custom Endpoint Manager Roles
- OS image management
- Azure network connection configuration
- Provisioning
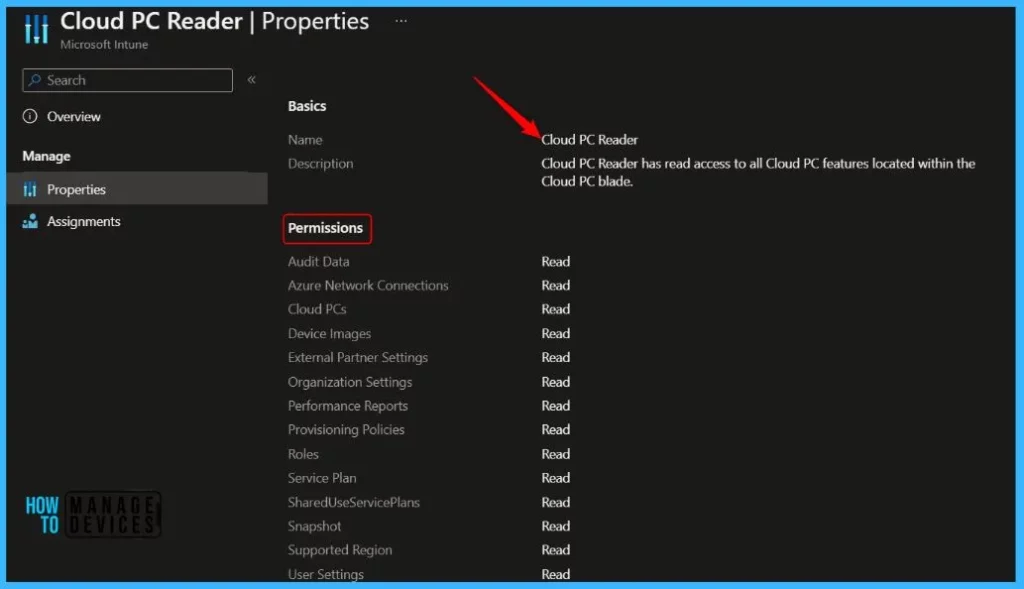
Cloud PC Reader: Views Cloud PC data available in the Windows 365 node in Microsoft Endpoint Manager, but can’t make changes.
Custom Cloud PC Roles
You can create custom roles for Windows 365 in Microsoft Intune admin center. To create a provisioning policy, an admin needs the following permissions:
- Provisioning Policy Read/Create
- Azure network connection Read
- Supported region Read
- Image Read permissions
Create Custom Windows 365 Role
You can create a custom Windows 365 role that includes any permissions required for a specific job function. After creating a custom role, you can assign it to any users that need those permissions. Here’s how you can create Cloud PC RBAC Roles:
To create, edit, or assign roles, your account must have Global Administrator or Intune Service Administrator permissions in Azure AD.
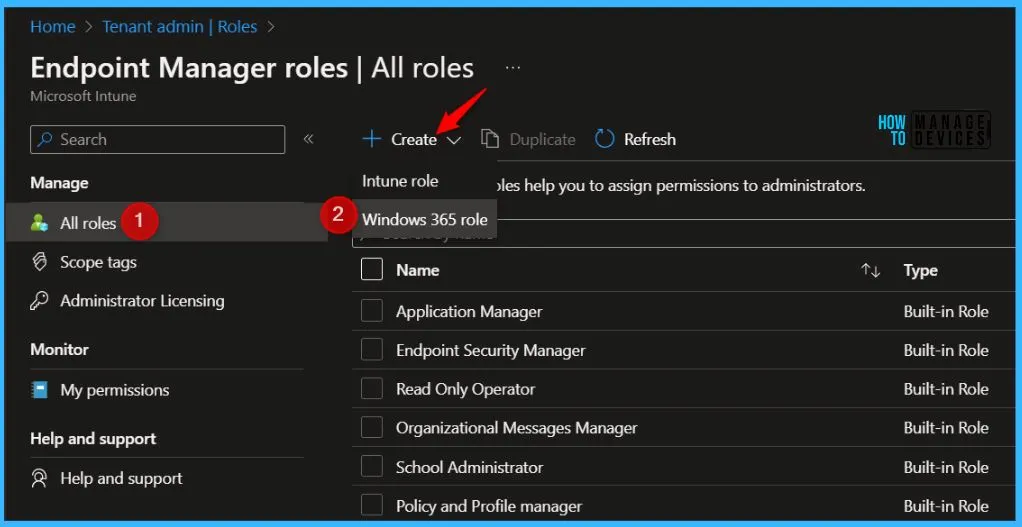
- Login to the Microsoft Intune Admin Center https://endpoint.microsoft.com/
- Navigate to Tenant administration > Roles > All roles.
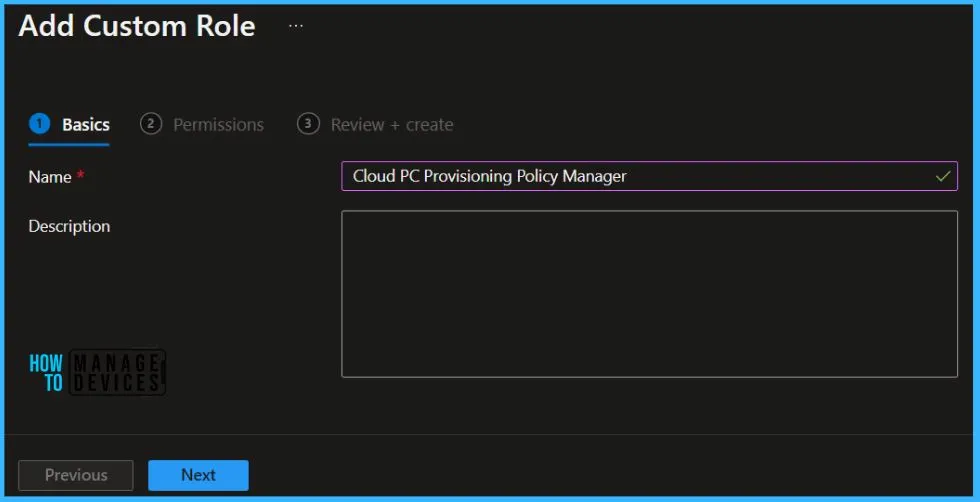
On the Basics page, enter a name for the Cloud PC role (For Example, Cloud PC Provisioning Policy Manager) and description for the new role, then choose Next.
On the Permissions page, choose the permissions you want to use with this role.
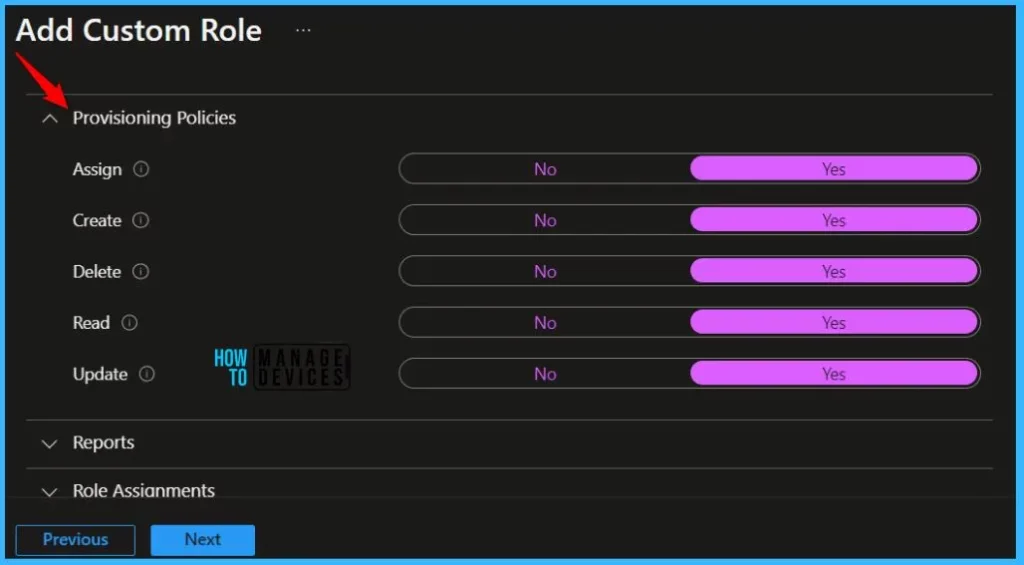
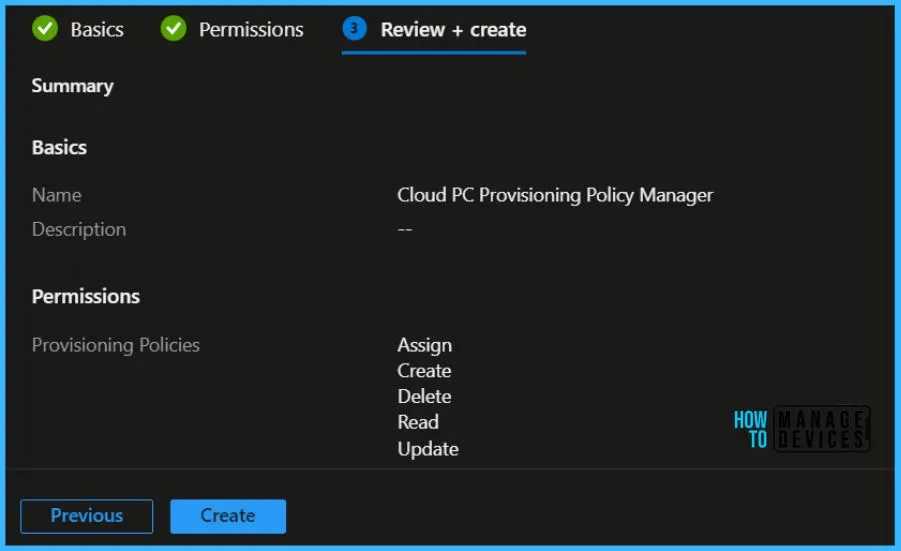
On Review + create, review assigned roles. Click on Create.
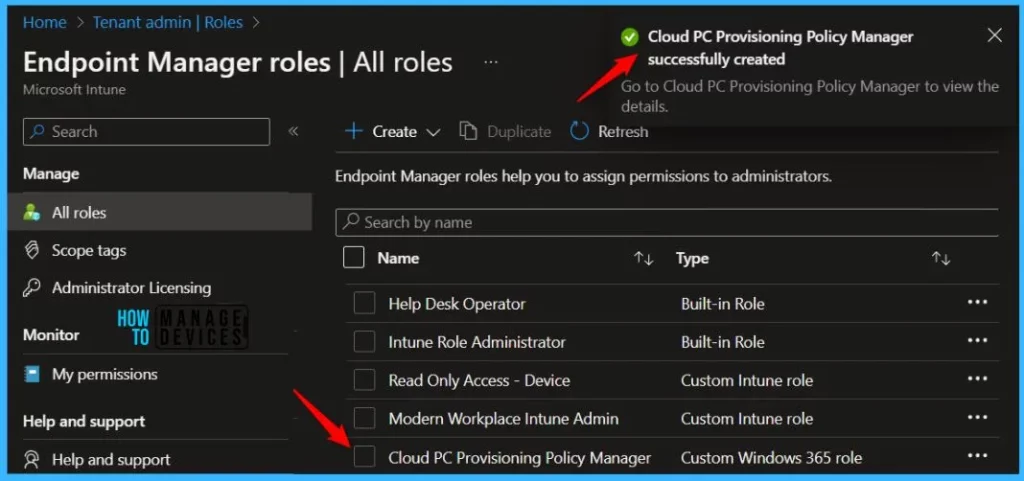
A notification will appear automatically in the top right-hand corner with a message. Here you can see, Cloud PC Provisioning Policy Manager successfully created. Click the Refresh button at the top to quickly see the roles. You will be able to see the Custom Windows 365 role created.
Once the Cloud PC RBAC roles has created, you can assign to the groups based on your requirements. You can easily copy an existing role that will be helpful for Cloud PC admin to create a custom Windows 365 role that includes any permissions required for a specific job function.
Here you will see the details about the option that allows you to duplicate RBAC roles, Duplicate Intune RBAC Roles | Cloud PC Roles.
Author
About Author – Jitesh, Microsoft MVP, has over five years of working experience in the IT Industry. He writes and shares his experiences related to Microsoft device management technologies and IT Infrastructure management. His primary focus is Windows 10/11 Deployment solution with Configuration Manager, Microsoft Deployment Toolkit (MDT), and Microsoft Intune.
