You can disable or enable TLS 1.0 and 1.1 for Internet Explorer and EdgeHTML – the rendering engine for the WebView control. Microsoft announced the disablement of TLS 1.0 and 1.1 back in 2018.
In Oct 2018, Microsoft announced the disablement of Transport Layer Security (TLS) 1.0 and 1.1 by default in Microsoft browsers. The disablement by default is delayed, but it’s happening on the 13th of Sept 2022.
After Sept 2022 patch Tuesday, TLS 1.0 and 1.1 will be disabled by default on all the supported Microsoft browsers such as Internet Explorer and MS EdgeHTML. For MS Edge browser version 84 or later, this is already disabled by default.
Microsoft is not deprecating the TLS 1.0 and 1.1 but disabling them for all the officially supported MS browsers. Microsoft is giving the opportunity to organizations to enable or disable the TLS for their managed devices. You can use Group Policy settings or Intune Cloud Policies to disable or enable TLS 1.0 and TLS 1.1.
- Enable Internet Explorer Mode in Microsoft Edge
- Configure Edge Chromium Favorites Using Intune | Endpoint Manager
- IE11 To Microsoft Edge Migration Adoption Kit | Free Download PowerPoint Email Templates
Do you Still need to keep TLS 1.0 and 1.1 enabled?
Do you Still need to keep TLS 1.0 and 1.1 enabled? Yes, this would be one of the first questions you should ask yourself. How many of your websites support only TLS 1.0 and 1.1?
I think there would be some legacy web applications in your organization (business critical – of course) that still need TLS 1.0 or TLS 1.1 along with Internet Explorer (IE) or MS Edge IE Mode to work. These are the applications going to cause some issues after 13th Sept 2022.
As per Aug 2022 SSL Labs report, 99.8% of the scanned websites support SSL 1.2 or above. This means most public websites are good to go with TLS 1.2 or above. However, internal enterprise web apps might have a different story to tell!
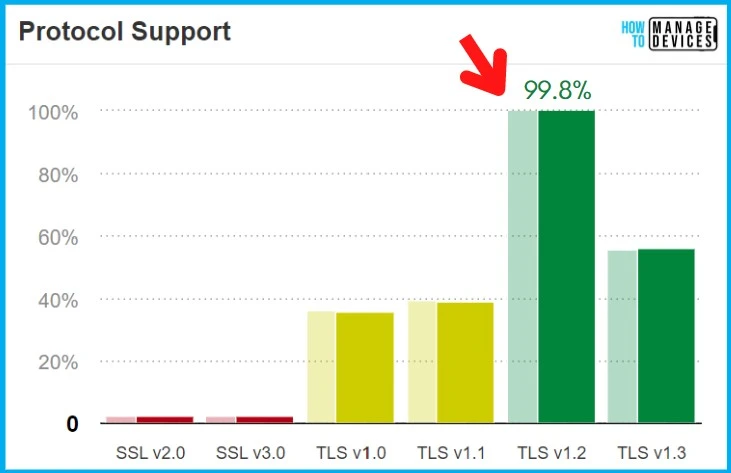
What is Transport Layer Security (TLS) Protocol?
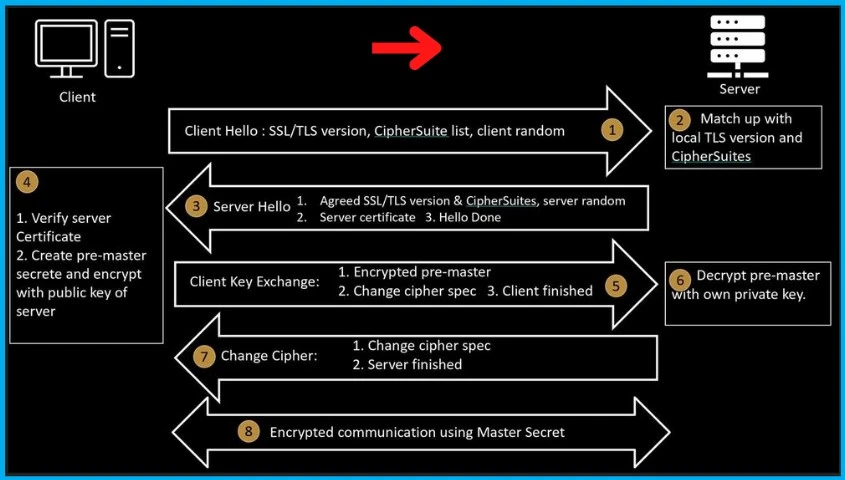
TLS is the protocol that helps protect communication between the browser (Client) and the target server. When the browser attempts to set up a protected communication with the target server, the browser and server negotiate which protocol and version to use.
The browser and server attempt to match each other’s list of supported protocols and versions and select the most preferred match. NOTE! – SSL 2.0 is off by default and is no longer supported starting with Windows 10 Version 1607. SSL 2.0 is an outdated security protocol.
Registry Entries for Internet Explorer TLS Support
Let’s check the registry entries for Internet Explorer (aka IE and IE Mode for MS Edge). You can refer to the Microsoft Edge browser group policy post to enable TLS 1.0 and 1.1 – Microsoft Edge ADMX Group Policy Settings.
| Registry Path | Value | Value Name | |
|---|---|---|---|
| Use TLS 1.0, TLS 1.1, and TLS 1.2 | HKLM or HKCU Software\Policies\Microsoft\Windows\CurrentVersion\Internet Settings | 2688 | SecureProtocols |
| Use TLS 1.0 and TLS 1.1 | HKLM or HKCU Software\Policies\Microsoft\Windows\CurrentVersion\Internet Settings | 640 | SecureProtocols |
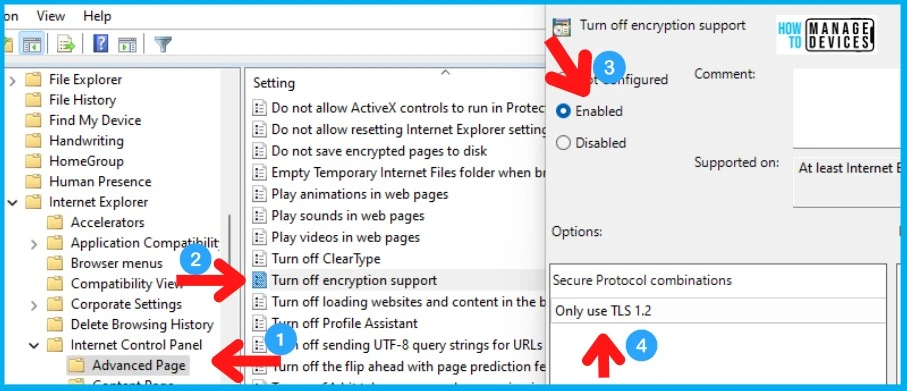
Disable TLS 1.0 and 1.1 using Group Policy
Microsoft will automatically disable TLS 1.0 and 1.1 for all Microsoft browsers after 13th Sept 2022. However, suppose your organization wants to ensure that all the managed Windows devices can use only the latest versions of TLS 1.2 or above. In that case, you can use the following group policy.
The following group policy helps to disable Transport Layer Security (TLS) 1.0 and 1.1.
- Launch Group Policy Management Console.
- Navigate Computers Configuration – Policies – Administrative Templates – Windows Components – Internet Explore – Internet Control Panel – Advanced Page.
- Open the policy setting called “Turn off encryption support.”
- Click on Enable.
- And from the drop-down options, select -> Only Use TLS 1.2
NOTE! – If you enable this policy setting, the browser negotiates or does not negotiate an encryption tunnel by using the encryption methods you select from the drop-down list. But not sure whether what will happen to sites running with TLS 1.3. Let me know in the comments.
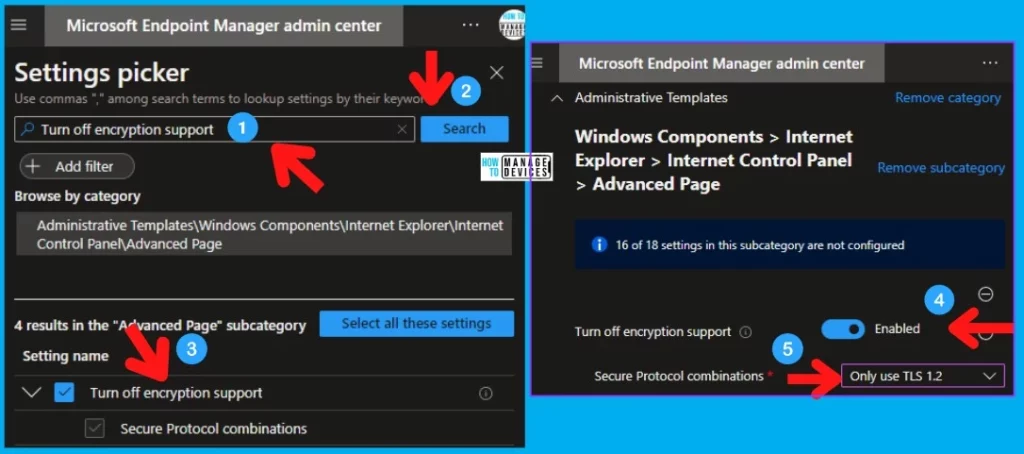
Intune Policy to Disable TLS 1.0 and 1.1
There is also an option to use Intune Policy to Disable TLS 1.0 and 1.1. There is an option in Intune to create a Settings Catalog Policy to disable TLS 1.0 and 1.1.
- Sign in to the Microsoft Endpoint Manager admin center.
- Select Devices > Configuration profiles > Create profile.
- Select platform -> Windows 10 and Later.
- Click on Create button (and follow the guide to create Intune Settings Catalog Policy).
There are thousands of settings available in the settings catalog. To make it easier to search specific settings, use the built-in features shown in the diagram below.
- I searched with the keyword “Turn off encryption support.”
- Select the relevant values (same as Group Policy above) – Only Use TLS 1.2 from the drop down.
NOTE! – The choice of Only using TLS 1.2 is tricky; it’s not a perfect one (I think) because I’m not sure what will happen to sites running with TLS 1.3. Let me know in the comments.
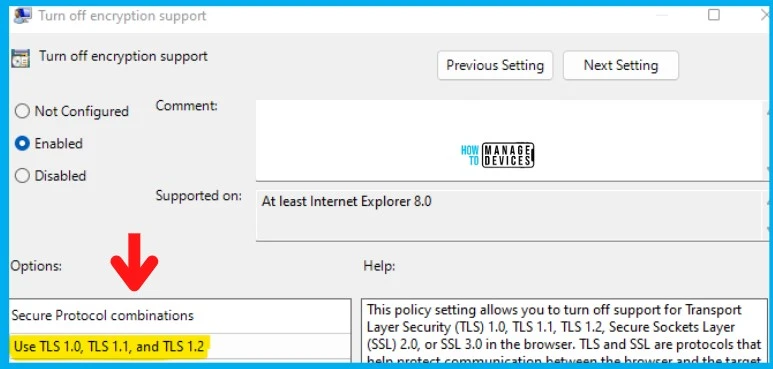
Enable TLS 1.0 and 1.1 using Group Policy
The TLS 1.0 and 1.1 will be disabled by default on all the supported MS browsers, such as IU and MS EdgeHTML, after the 13th Sept 2022 patch Tuesday. If you need to enable TLS 1.0 and 1.1, you must use a group or Intune policy to enable it back after Sept 2022.
Some organizations still wanted to use TLS 1.0 and TLS 1.1 for some of the internal business-critical web applications. You must follow the steps.
- Launch Group Policy Management Console.
- Navigate Computers Configuration – Policies – Administrative Templates – Windows Components – Internet Explore – Internet Control Panel – Advanced Page.
- Open the policy setting called “Turn off encryption support.”
- Click on Enable.
- And from the drop-down options select -> “Use TLS 1.0, TLS 1.1, and TLS 1.2.”
NOTE! – If you disable or do not configure this policy setting, the user can select which encryption method the browser supports. Hence I have decided to use TLS 1.0, TLS 1.1, and TLS 1.2 options.
Intune Policy to Enable TLS 1.0 and 1.1
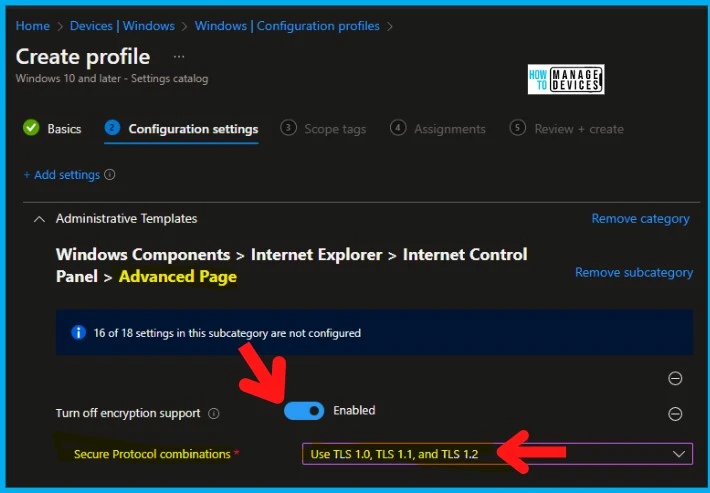
You can enable TLS 1.0 and 1.1 protocols using Intune Settings Catalog ADMX policies. This similar method is used to disable TLS 1.0 and 1.1 in the above section. The Intune method is useful when you have Azure AD Joined Windows devices.
- Follow the guide to creating Intune Settings Catalog Policy.
There are thousands of settings available in the settings catalog. To make it easier to search specific settings, use the built-in features shown in the diagram below.
- I searched with the keyword “Turn off encryption support.”
- Select relevant values (same as Group Policy above) from the drop-down options – Use TLS 1.0, TLS 1.1, and TLS 1.2.
NOTE! – I thought the option – Use TLS 1.0, TLS 1.1, and TLS 1.2 is the best option I could figure out from the Turn off encryption support group policy Settings. What do you think?
Author
Anoop C Nair is Microsoft MVP! He is a Device Management Admin with more than 20 years of experience (calculation done in 2021) in IT. He is Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc.
