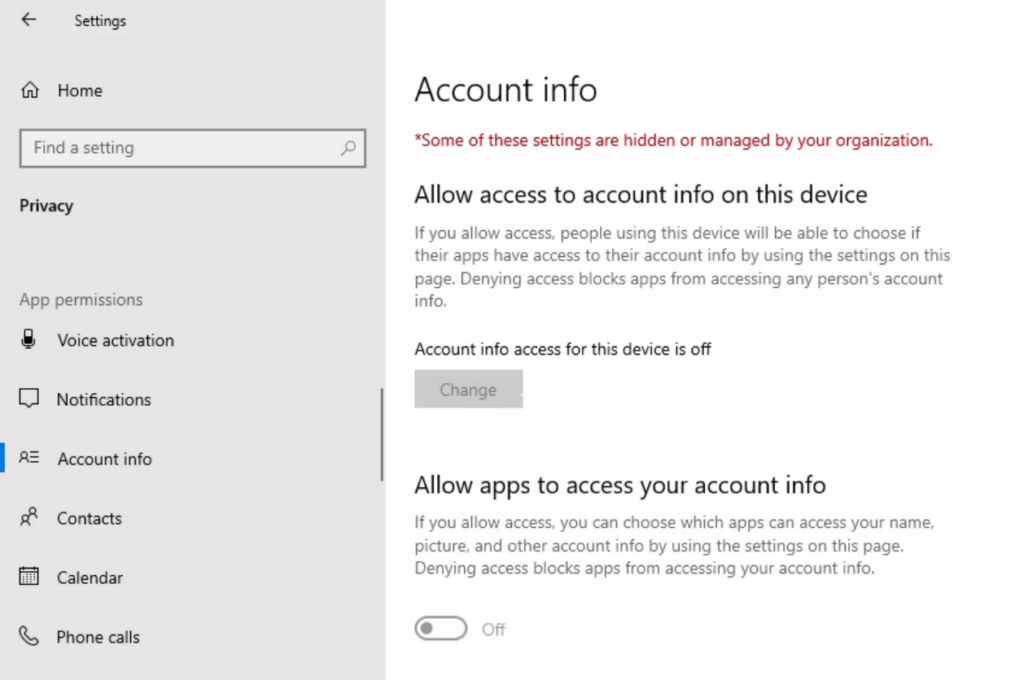
Let’s see how to Manage Apps Access Permission for Account Info using Intune, aka, Endpoint Manager. By default, universal Windows Platform (UWP) apps can access certain file system locations account info. Microsoft is giving you more control to decide which UWP apps can access your account info.
Windows provides a wealth of data access to make apps useful and valuable to you. These capabilities, which are security constructs that gate access to personal data, include Calendar, Contacts, Call history, and more.
Each capability has its privacy settings page so that you can control it and what apps and services can use that capability.
If you allow access, users on your PC will be able to turn on or off if their apps have access to their account info. If you turn it on to let apps access your account info, you can choose to allow or deny access for individual apps.
Microsoft recommends setting catalog profiles to create and manage security policies for all Intune managed Windows devices. The Intune Settings Catalog is the best place to go for all the policy settings in Intune (MEM). In the settings catalog profile, you will also get an option Duplicate to create a copy of an existing setting catalog profile.
- Collect Intune Logs from MEM Portal Diagnostic Data
- Intune Logs Event IDs IME Logs Details For Windows Client Side Troubleshooting
- How to Control Running Background Windows Apps Using Intune
Manage Apps Access Permission for Account Info Using Intune
Let’s follow the step below to manage apps access permission for account info using Intune –
- Sign in to the Endpoint Manager Intune portal https://endpoint.microsoft.com/
- Select Devices > Windows > Configuration profiles > Create profile.
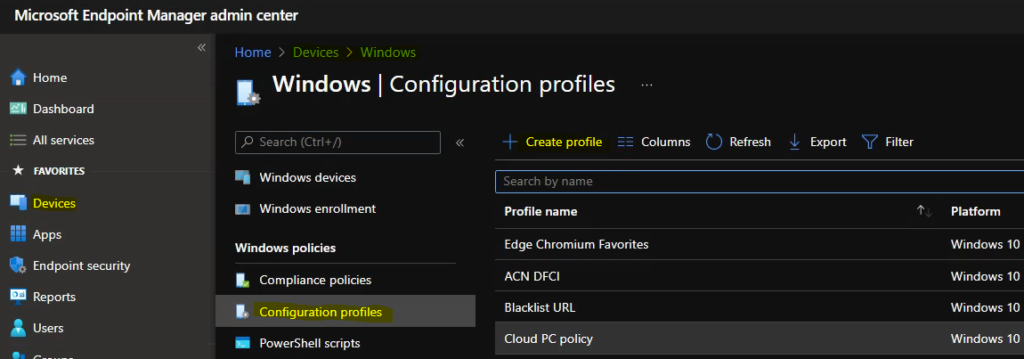
In Create Profile, Select Platform, Windows 10, and later and Profile, Select Profile Type as Settings catalog. Click on Create button.
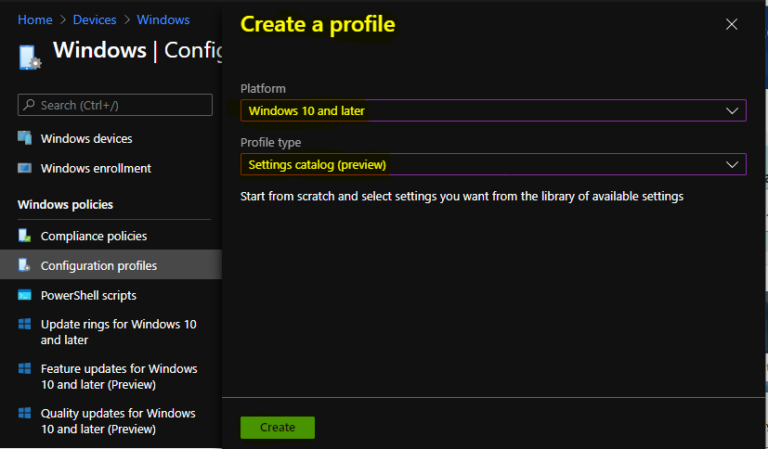
On the Basics tab, enter a descriptive name, such as Manage Apps Permission for Access Account Info. Optionally, enter a Description for the policy, then select Next.
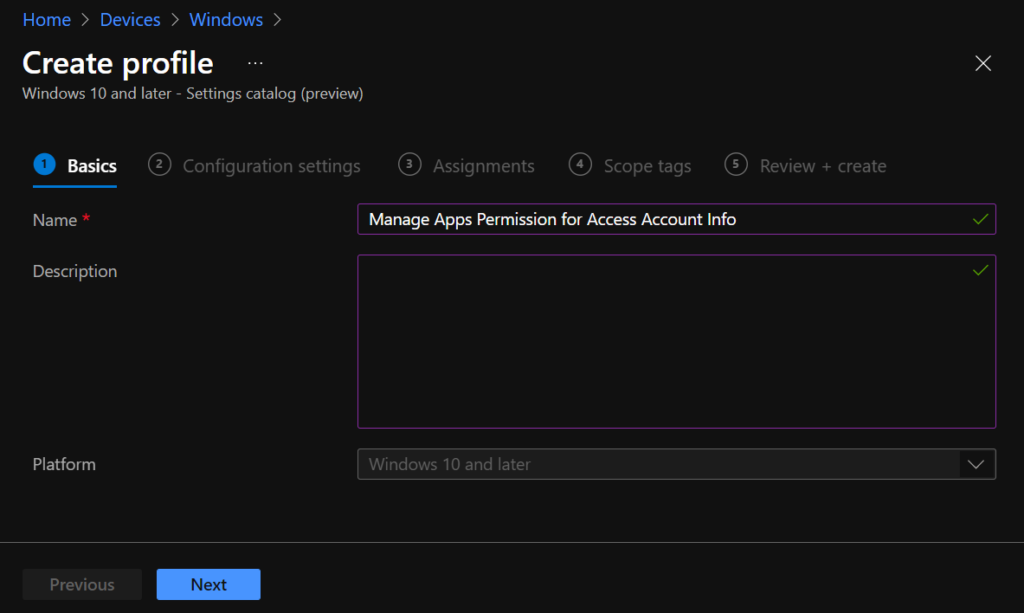
In Configuration settings, click Add settings to browse or search the catalog for the settings you want to configure.
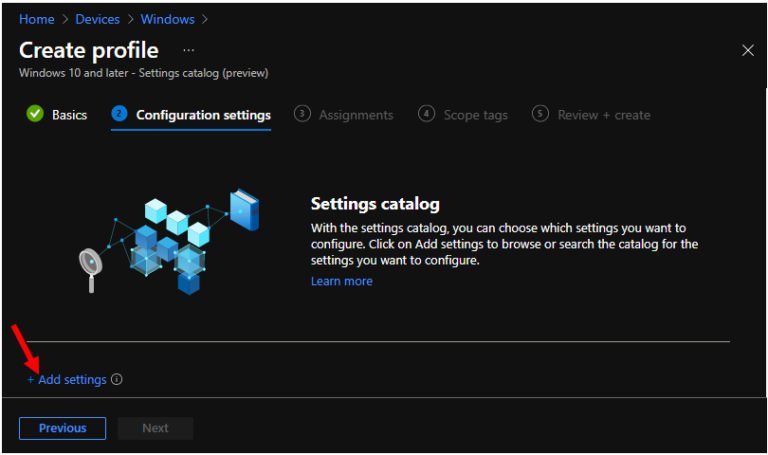
On the Settings Picker windows, Select Privacy to see all the settings in this category. For Example – I selected the below four settings. After adding your settings, click the cross mark at the right-hand corner to close the settings picker.
- LetAppsAccessAccountInfo – Specifies whether Windows apps can access account information.
- LetAppsAccessAccountInfo_ForceAllowTheseApps – List of semi-colon delimited Package Family Names of Windows apps. Listed Windows apps are allowed access to account information. This setting overrides the default LetAppsAccessAccountInfo policy setting for the specified Windows apps.
- LetAppsAccessAccountInfo_ForceDenyTheseApps – List of semi-colon delimited Package Family Names of Windows apps. Listed Windows apps are denied access to account information. This setting overrides the default LetAppsAccessAccountInfo policy setting for the specified Windows apps.
- LetAppsAccessAccountInfo_UserInControlOfTheseApps – List of semi-colon delimited Package Family Names of Windows apps. The user is able to control the account information privacy setting for the listed Windows apps. This setting overrides the default LetAppsAccessAccountInfo policy setting for the specified Windows apps.
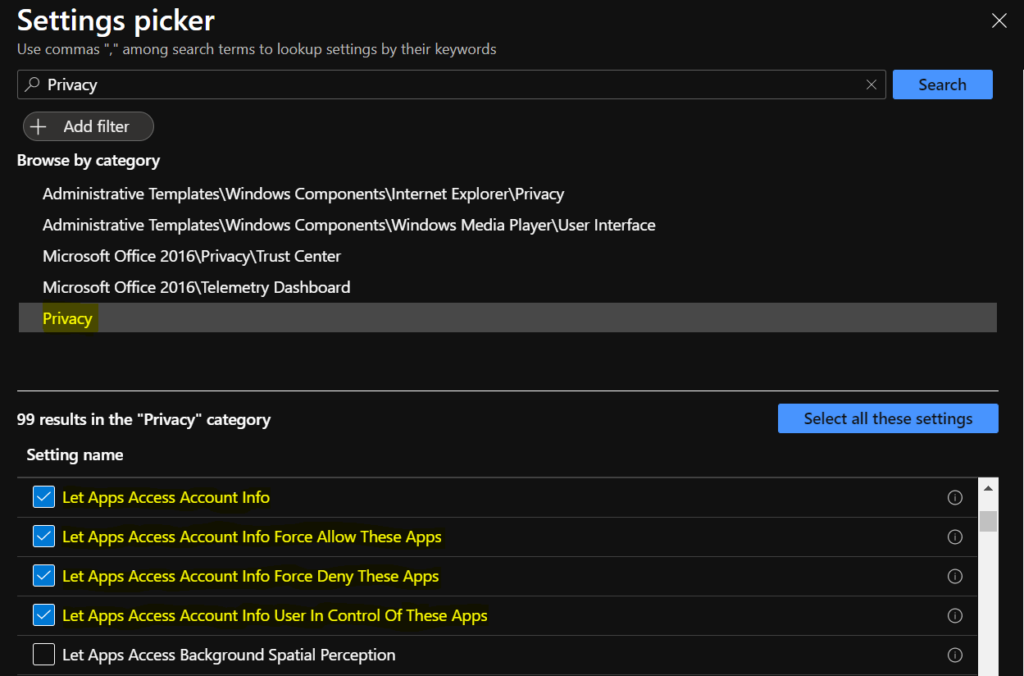
You can specify either a default setting for all apps or a per-app setting by specifying a Package Family Name. Let’s collect the information from your system, To get the Package Family Name for an app by using the Get-AppPackage Windows PowerShell cmdlet.
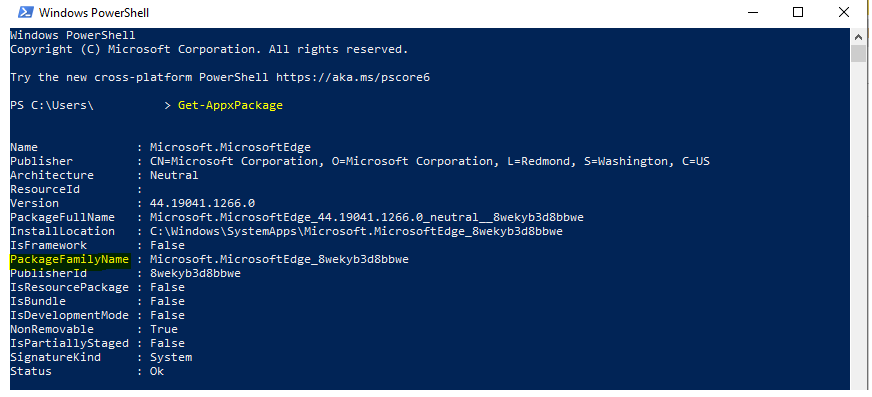
Here you can see the package family name for apps added to allow or deny lists based on the requirements. Similarly, you can add more by clicking +Add. And click Next to continue.
The following available options for Let Apps Access Account Info –
- If you choose the “User is in control” option, employees in your organization can decide whether Windows apps can run in the background by using Settings > Privacy on the device.
- “Force Allow” option, Windows apps are allowed to run in the background and employees in your organization cannot change it.
- “Force Deny” option, Windows apps are not allowed to run in the background and employees in your organization cannot change it.
Under Assignments, In Included groups, click Add groups and then choose Select groups to include one or more groups. Click Next to continue.
In Scope tags, you can assign a tag to filter the profile to specific IT groups. Add scope tags (if required) and click Next.
In Review + create, review your settings. When you select Create, your changes are saved, and the profile is assigned.
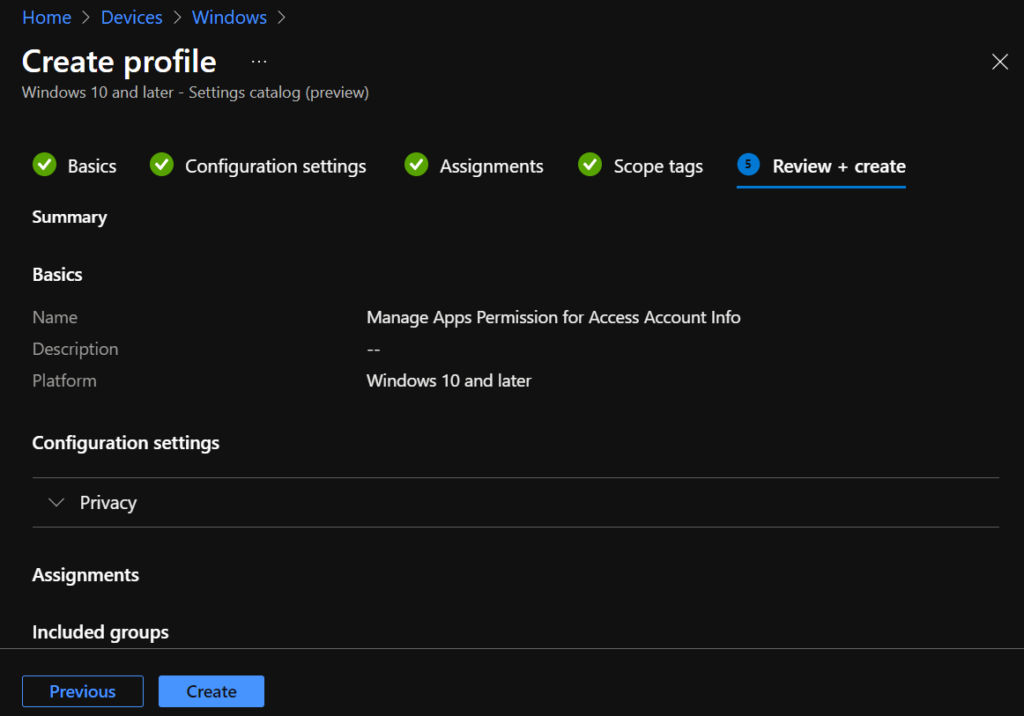
A notification will appear automatically in the top right-hand corner with a message. Here you can see that Policy “Manage Apps Permission for Access Account Info“ created successfully. The policy is also shown in the Configuration profiles list.
Reporting – Manage Apps Permission for Access Account Info
You can check Intune settings catalog profile report from Intune Portal, which provides an overall view of device configuration policies deployment status.
After deploying the policy, the assigned groups will receive the profile settings once the devices check-in with the Intune service.
To monitor the policy assignment, from the list of Configuration Profiles, select the policy, and here you can check the device and user check-in status.
If you click View Report, additional details are displayed.
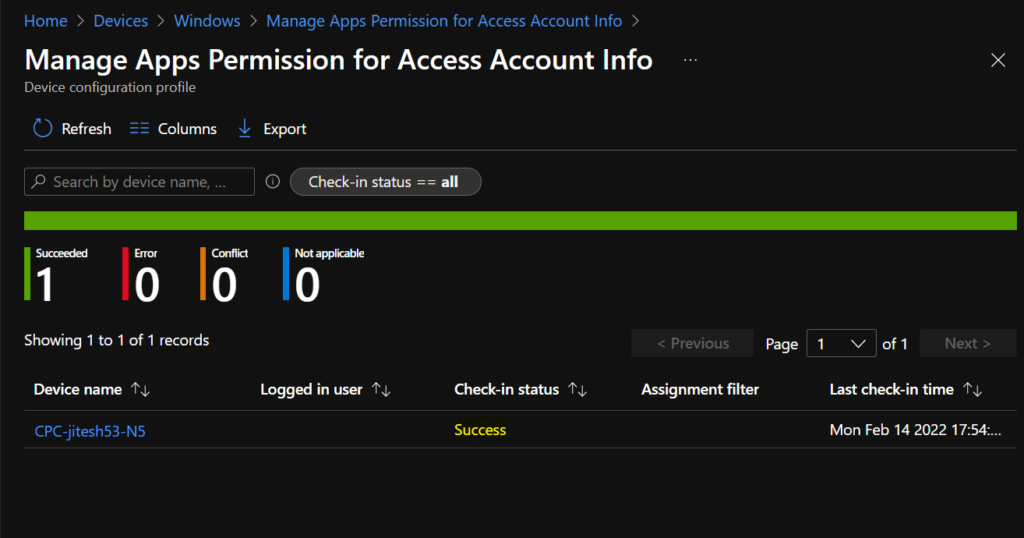
Intune MDM Event Log
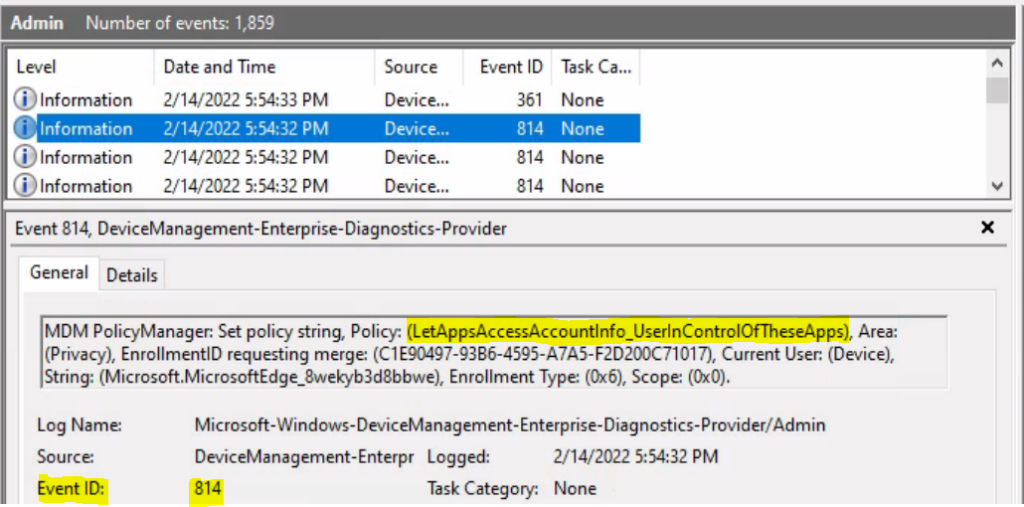
The Intune event ID indicates a string policy is applied on the Windows 10 or 11 devices. You can also see the exact value of the policy being applied on those devices.
In the target device, You can check the Event log path to confirm – Applications and Services Logs – Microsoft – Windows – Devicemanagement-Enterprise-Diagnostics-Provider – Admin.
MDM PolicyManager: Set policy int, Policy: (LetAppsAccessAccountInfo), Area: (Privacy), EnrollmentID requesting merge: (C1E90497-93B6-4595-A7A5-F2D200C71017), Current User: (Device), Int: (0x2), Enrollment Type: (0x6), Scope: (0x0).
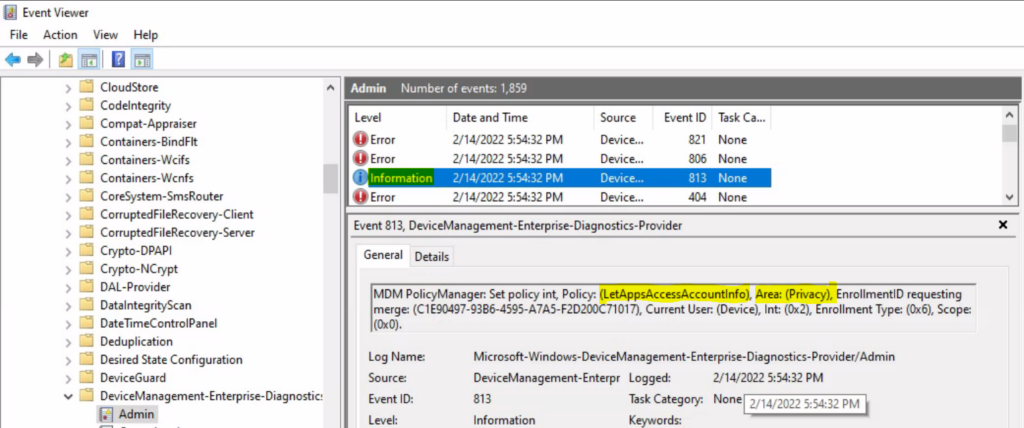
Similarly, you can look at the Event ID 814 generated for the configured policies for managing apps, Here are the highlights from the Event logs.
MDM PolicyManager: Set policy string, Policy: (LetAppsAccessAccountInfo_ForceAllowTheseApps), Area: (Privacy), EnrollmentID requesting merge: (C1E90497-93B6-4595-A7A5-F2D200C71017), Current User: (Device), String: (Microsoft.AccountsControl_10.0.19041.1023_neutral__cw5n1h2txyewy), Enrollment Type: (0x6), Scope: (0x0).
MDM PolicyManager: Set policy string, Policy: (LetAppsAccessAccountInfo_ForceDenyTheseApps), Area: (Privacy), EnrollmentID requesting merge: (C1E90497-93B6-4595-A7A5-F2D200C71017), Current User: (Device), String: (Microsoft.WindowsStore_22112.1401.2.0_x64__8wekyb3d8bbwe), Enrollment Type: (0x6), Scope: (0x0).
MDM PolicyManager: Set policy string, Policy: (LetAppsAccessAccountInfo_UserInControlOfTheseApps), Area: (Privacy), EnrollmentID requesting merge: (C1E90497-93B6-4595-A7A5-F2D200C71017), Current User: (Device), String: (Microsoft.MicrosoftEdge_8wekyb3d8bbwe), Enrollment Type: (0x6), Scope: (0x0).
Validate Registry
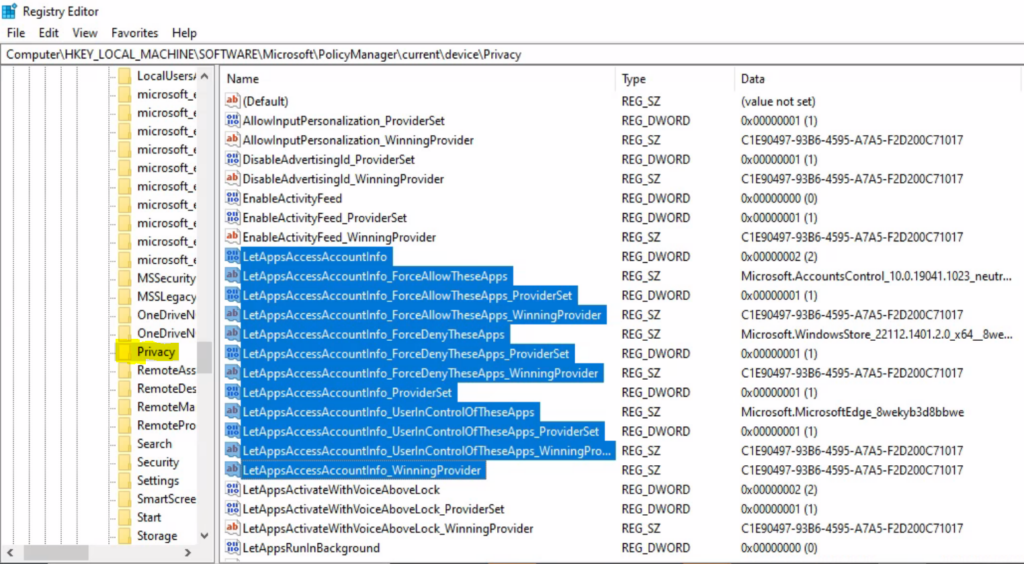
It’s now time to validate whether the registry values are changed or not. You can see the registry entries related to the Activity Feed privacy settings in the following registry path –
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\current\device\Privacy LetAppsAccessAccountInfo DWORD value 2 = Disable
LetAppsAccessAccountInfo_UserInControlOfTheseApps <Package Family Name>
LetAppsAccessAccountInfo_ForceAllowTheseApps <Package Family Name>
LetAppsAccessAccountInfo_ForceDenyTheseApps <Package Family Name>
Validate Windows Settings
Open Settings, and click on the Privacy icon.
Click on Account info on the left side. Under the setting, you can see Account info access for this device is turned Off and Turned Off Let Specific/Apps Access Your Account Info –