Let’s talk about the Post-auth Terminate Processes Feature. Windows LAPS, or Local Administrator Password Solution, got a helpful upgrade. Now, there is a new feature called “post-authentication-action,” and it is all about making your LAPS-enabled devices more secure.
In the Windows Local Administrator Password Solution (LAPS), a new feature called “post-authentication actions policy” has been improved. This feature comes into play after you have logged into your computer. It is like an extra layer of security steps that happen automatically.
This feature now includes a new part called “post-auth Terminate Processes.” This means that after you successfully log in, the system can take additional actions, like stopping specific processes or tasks.
It is a way to ensure things stay secure even after gaining access to your computer. This improvement is designed to enhance the overall security of your system by taking specific actions automatically after you have logged in.

- Windows LAPs Automatic Account Management
- Windows LAPS Integration with Local Device MaximumPasswordAge Policy
- Windows LAPs Smart-Card-only Policy Integration
- Enable Windows LAPS Managed Account in WinRE or Safemode
- Setup New Windows LAPs using Intune Policies Local Admin Password Management Policy
Post-auth Terminate Processes Feature
The “Post-auth Terminate Process” feature is currently available in Windows insider builds. Now, let’s talk about “post-authentication action.” This is a security measure.
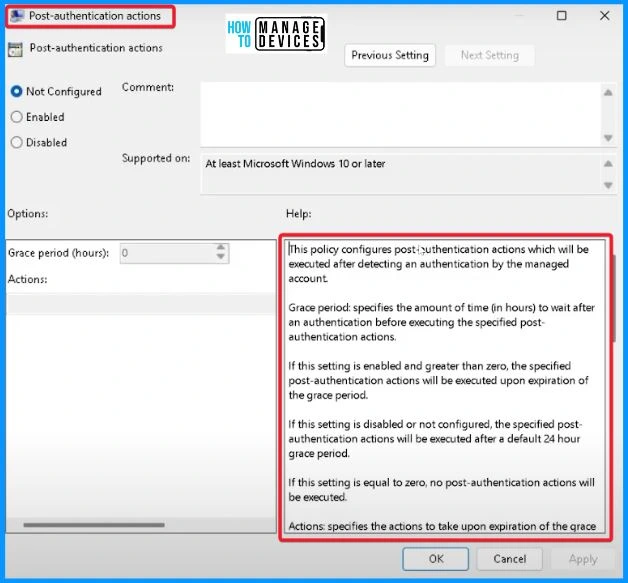
This policy configures post-authentication actions, which will be executed after detecting an authentication by the managed account. Grace period: specifies the time (in hours) to wait after an authentication before performing the specified post-authentication actions.
| Post-Authentication Actions | Details |
|---|---|
| If this setting is enabled and greater than zero | The specified post-authentication actions will be executed upon expiration of the grace period. |
| If this setting is disabled or not configured | The specified post-authentication actions will be executed after a default 24-hour grace period. |
| If this setting is equal to zero | No post-authentication actions will be executed. |
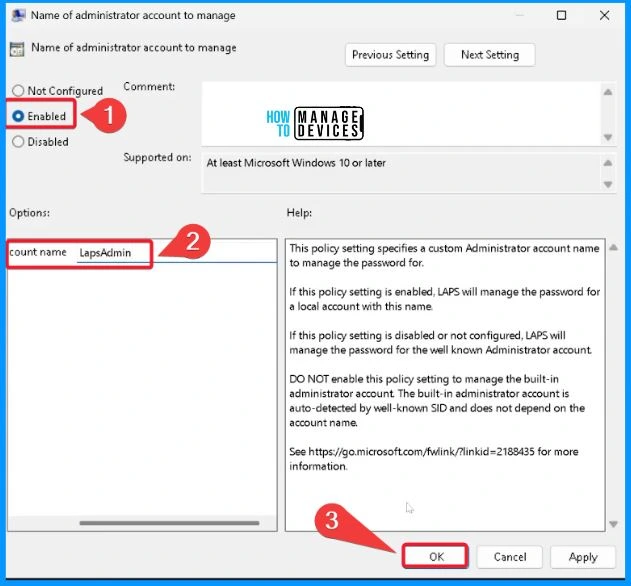
Name of Administrator Account to Manage
This policy setting specifies a custom Administrator account name to manage the password. If this policy setting is enabled, LAPS will manage the password for a local account with this name. If this policy setting is disabled or not configured, LAPS will manage the password for the well-known Administrator account.
DO NOT enable this policy setting to manage the built-in administrator account. The built-in administrator account is auto-detected by a well-known SID and does not depend on the account name.
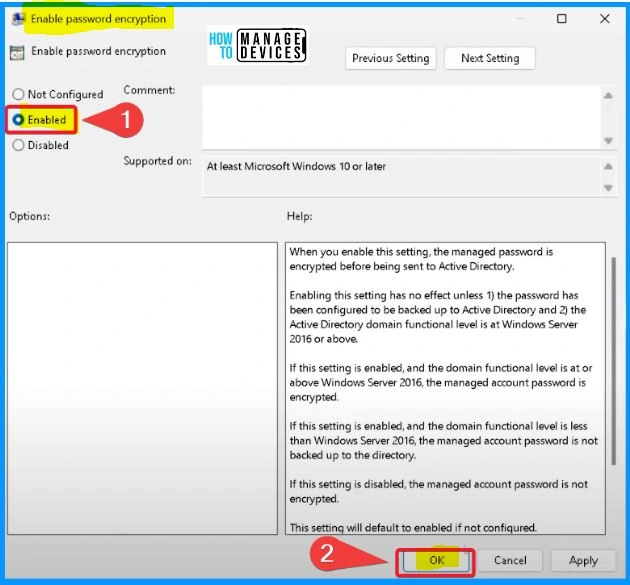
Enable Password Encryption
When you enable this setting, the managed password is encrypted before being sent to Active Directory. Enabling this setting has no effect unless 1) the password has been configured to be backed up to Active Directory and 2) the Active Directory domain functional level is at Windows Server 2016 or above.
- The managed account password is encrypted if this setting is enabled and the domain functional level is at or above Windows Server 2016.
- If this setting is enabled, and the domain functional level is less than Windows Server 2016, the managed account password is not backed up to the directory.
- If this setting is disabled, the managed account password is not encrypted.
- This setting will default to enabled if not configured.
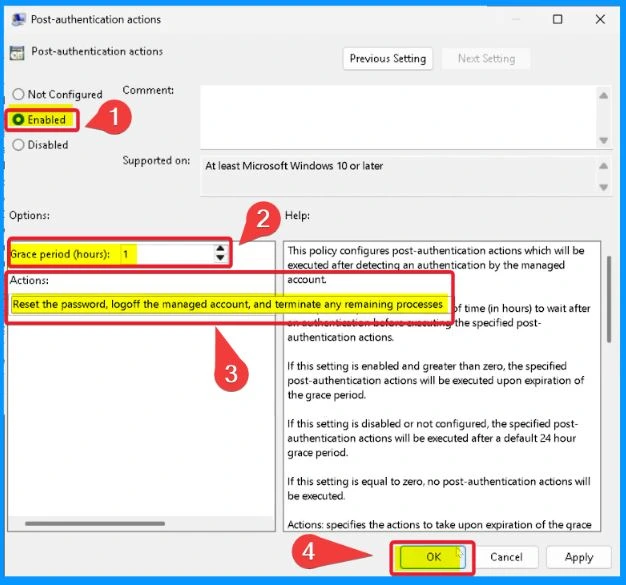
Post-Authentication Actions
This policy configures post-authentication actions, which will be executed after detecting an authentication by the managed account. If this setting is enabled and greater than zero, the specified post-authentication actions will be performed upon the expiration of the grace period.
- If this setting is disabled or not configured, the specified post-authentication actions will be executed after a default 24-hour grace period.
- If this setting equals zero, no post-authentication actions will be executed.
- Select the Grace Period as I hours
- Select the Action “Reset the password, logoff the managed account, and terminate any remaining processes”.
Configure Password Backup Directory
Use this setting to configure which directory the local admin account password is backed up. The allowable settings are: 0=Disabled (password will not be backed up), 1=Backup the password to Azure Active Directory, and 2=Backup the password to Active Directory.
- If not specified, this setting will default to 0 (Disabled).
- If this setting is configured to 1, and the managed device is not joined to Azure Active Directory, the local administrator password will not be executed.
- If this setting is configured to 2, and the managed device is not joined to Active Directory, the local administrator password will not be executed.
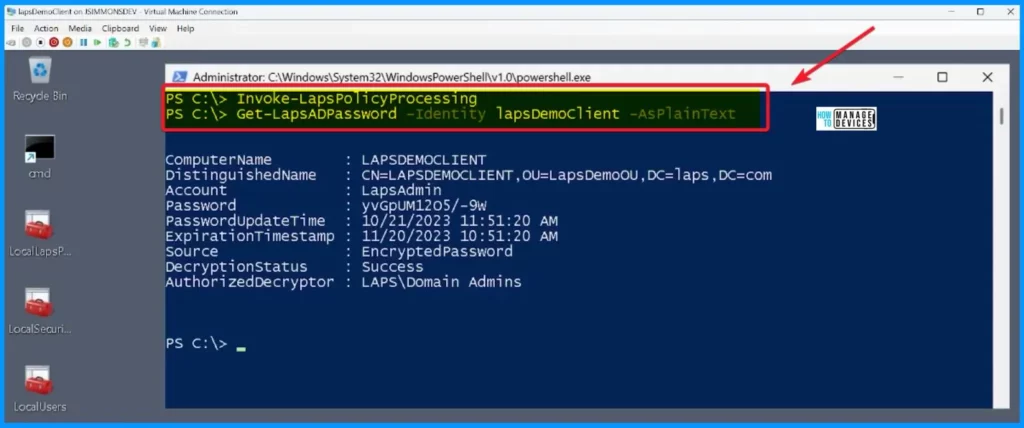
Once you set up the LAPS (Local Administrator Password Solution) policy, it is time to check if everything is working smoothly. You stored a new password using LAPS. Next step: you’re going to get that password back. It is like ensuring the system does what it’s supposed to – securely storing and retrieving passwords.
PS C: > Invoke-LapsPolicyProcessing
PS C: > Get-LapsADPassword -Identity lapsDemoclient -AsPlainText
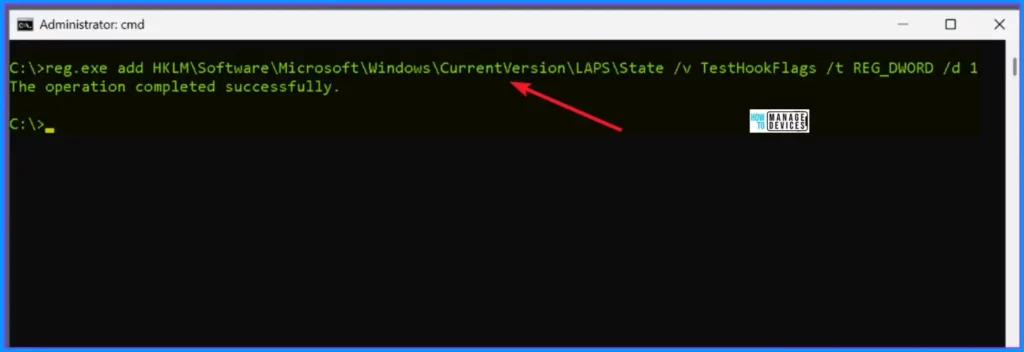
After setting this below flag, something interesting happens with the grace period. Normally, this grace period is specified in hours, but with the test hook flag in action, it changes things. The system starts interpreting the grace period in minutes instead of hours.
C: >reg.exe add HKLM\Software\Microsoft\Windows\CurrentVersion\LAPS\State /v TestHookFlags /t REG_DWORD /d 1
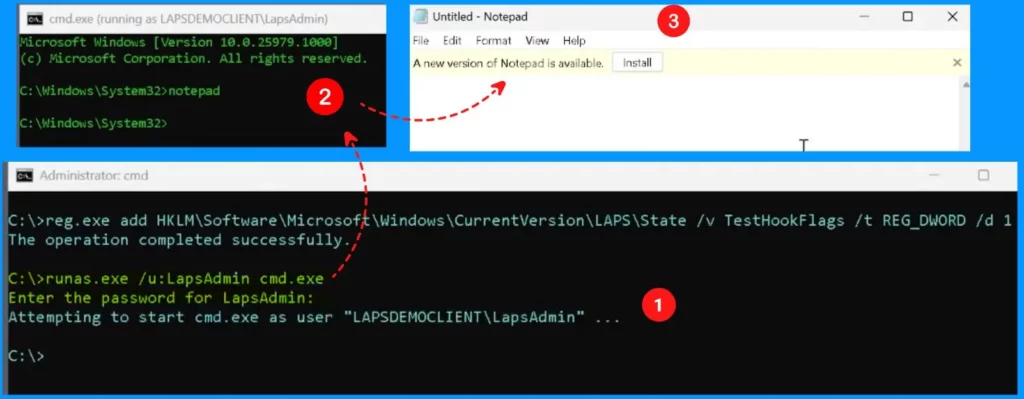
Now you use a command, like “runas.exe /u:LapsAdmin cmd.exe”, and then you enter the password for the LAPS admin. This action launches a timer, and the exciting part is that the one-minute timer starts as soon as you perform the first action. You got a fresh password and are now using it to launch processes, like opening Notepad. The catch is that the one-minute timer started when you did the first action.
C: >runas.exe /u: LapsAdmin cmd.exe
Event Viewer Local
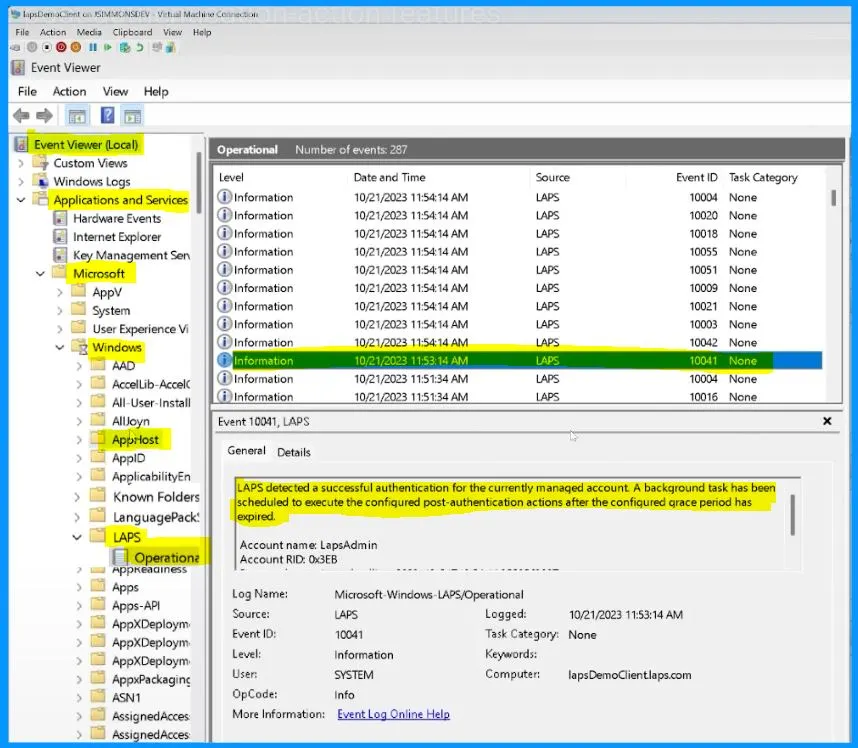
Let’s check out the Event Viewer to understand what’s going on with Event ID 10041. This event is like a notification that tells us something important happened.
Event ID 10041 is related to LAPS (Local Administrator Password Solution) specifically. LAPS noticed that you used the “runas.exe” command on a managed account, indicating that some action was taken with that account.
- Event Viewer (Local) > Application and Services > Microsoft > Windows > LAPS > Operational
- LAPS detected a successful authentication for the currently managed account. After the configured grace period has expired, a background task has been scheduled to execute the configured post-authentication actions.
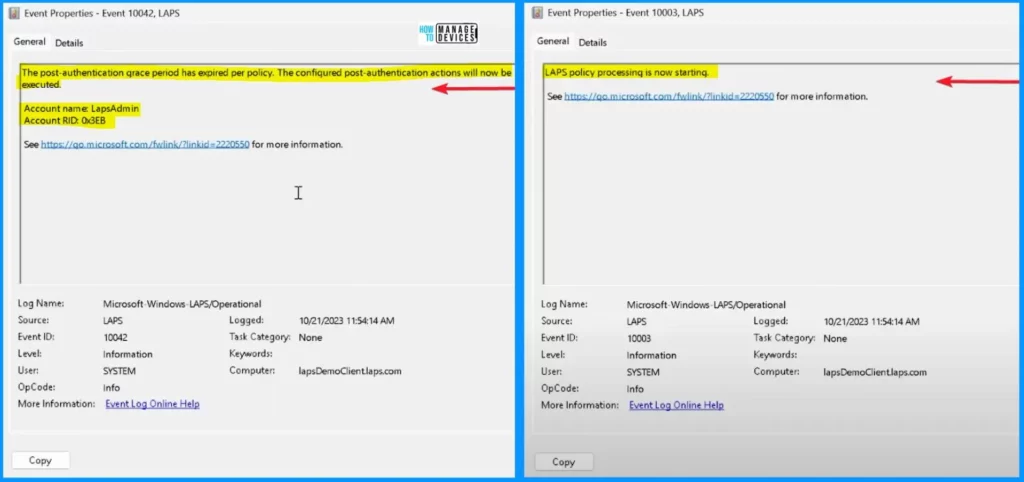
The post-authentication grace period has expired per policy. The configured post-authentication actions will now be executed. The Account name is LapsAdmin, and the Account RID is 0x3EB. The second screenshot shows that the LAPS policy process is now starting.
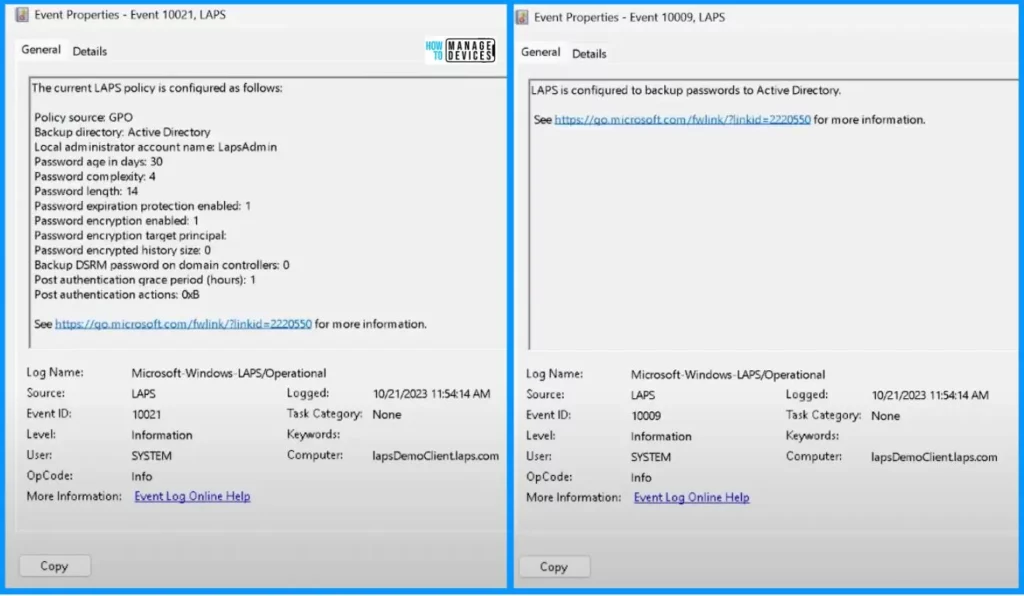
The first screenshot confirms the current LAPS policy in the following way. The second screenshot shows that LAPS must back up passwords to the Active Directory.
- Policy source GPO
- Backup directory: Active Directory
- Local administrator account name: LapsAdmin
- Password age in days: 30
- Password complexity: 4
- Password length: 14
- Password expiration protection enabled: 1
- Password encryption enabled: 1
- Password encryption target principal:
- Password encrypted history size: 0
- Backup DSRM password on domain controllers: 0
- Post-authentication grace period (hours): 1
- Post authentication actions: OxB
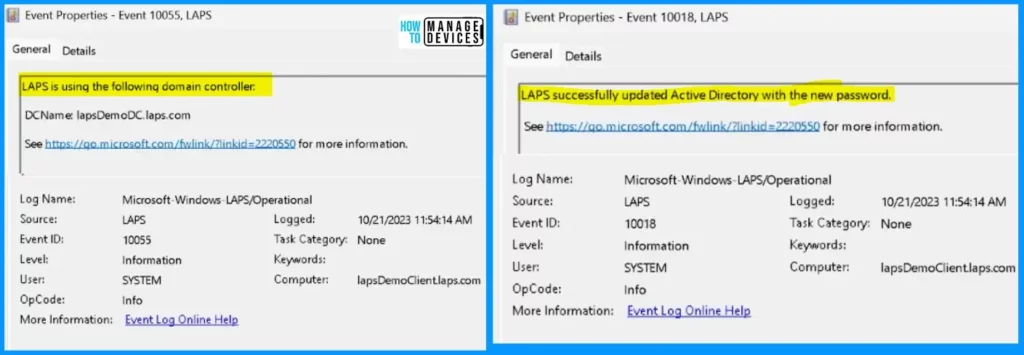
The screenshot shows that the Laps uses the following domain controller, and the second screenshot shows that the LAPS successfully updated the Active Directory with the new Password.
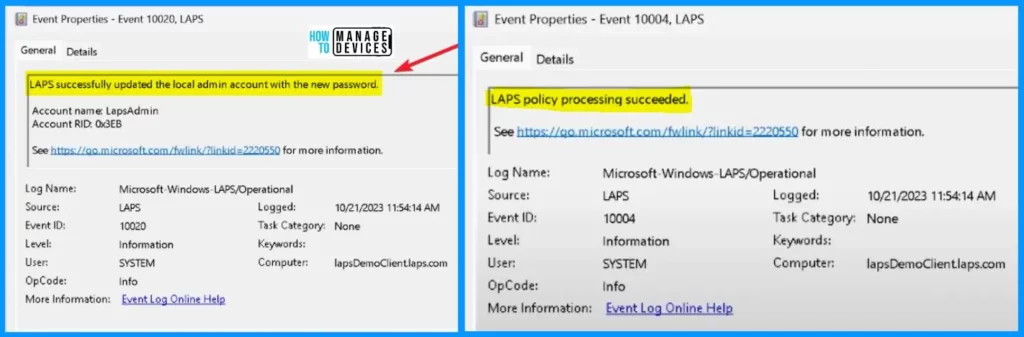
The first screenshot shows that LAPS successfully updated the local admin account with the new password, and the second screenshot shows that the LAPS policy processing succeeded.
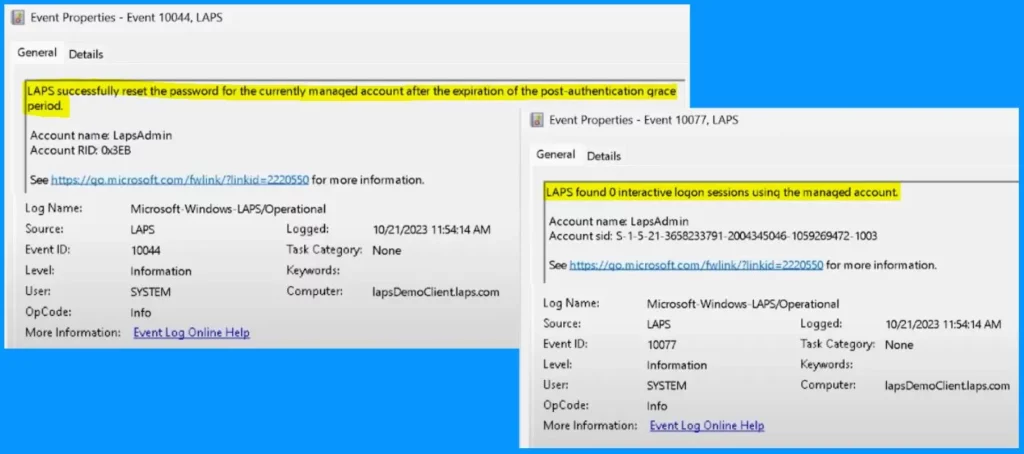
The first screenshot shows that the LAPS successfully reset the password of the currently managed account after the post-authentication grace period expires. The second screenshot shows that the Laps found 0 interactive logon sessions using the managed account.
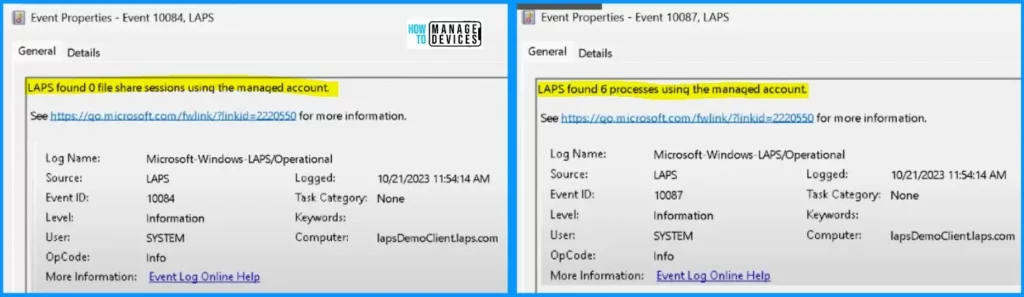
The first screenshot shows that the LAPS found 0 file share sessions using the managed account, and the second screenshot shows that the LAPS found six processes using the managed account.
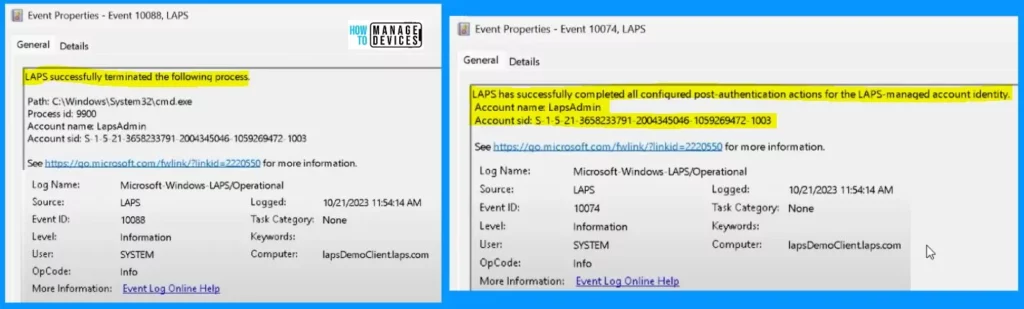
The first screenshot shows the LAPS successfully terminated the following process. The second screenshot shows that the LAPS has completed all configured post-authentication actions for the LAPS-managed account identity.
- The Account name is LapsAdmin.
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here. HTMD WhatsApp.
Author
About the Author – Vidya is a computer enthusiast. She is here to share quick tips and tricks with Windows 11 or Windows 10 users. She loves writing on Windows 11 and related technologies. She is also keen to find solutions and write about day-to-day tech problems.
