Let’s discuss Enable Windows Hello for Business and Remove Password Login on Windows 11 v22H2n. If you enable Windows Hello for Business, you can remove the Password Credential Provider on the Windows Lock. This facility is now available on Windows 11 version 22H2.
This feature means that Windows 11 users now get the Windows passwordless experience. We are all familiar with passwordless authentication, right? This facility is available on most Microsoft products.
Passwordless authentication is a security policy that promotes a user experience without passwords on Microsoft Entra-joined devices. By enabling this policy, certain Windows authentication scenarios don’t allow users to use a password.
Passwordless authentication helps organizations and gradually prepares users to move away from passwords. In this blog, I would like to discuss Windows 11 22H2 Passwordless authentication.
Table of Contents

Does Windows Passwordless Affect the Sign-in?
Initial Sign-in experience and local accounts does not affected by Windows Passwordless experience. It affect on the following sign-ins for Microsoft Entra accounts. It still allows a user to sign in with a password when selecting the ‘Other user’ option on the lock screen.
Is Windows Passwordless experience Preventing users from using Passwords?
for the last user who signed in with Windows Hello or a FIDO2 security key the password credential provider is hidden. Windows Passwordless experience is designed to guiding and educating users, not to use passwords.
Enable Windows Hello for Business and Remove Password Login on Windows 11 v22H2
As mentioned above, passwordless authentication is available on Windows 11 version 22H2. Different editions of Windows 11 22H2 have this facility. With Windows passwordless experience, users who sign in with Windows Hello or a FIDO2 security key have the following abilities.
| Abilities |
|---|
| Can’t use the password credential provider on the Windows lock screen |
| Aren’t prompted to use a password during in-session authentications (for example, UAC elevation, password manager in the browser, etc.) |
| Don’t have the option Accounts > Change password in the Settings app |
- Ensuring Data Protection through Windows Recall with New Security Architecture TPM Windows Hello
- TPM 2.0 Transition to Windows 11 For Better Security
- Top 83 Windows 11 Desktop Admin Interview Question
System Requirements
There are some system requirements needed for accessing Windows passwordless experience. The following list shows the system requirements.
- Windows 11, version 22H2 with KB5030310 or later
- Microsoft Entra joined
- Windows Hello for Business credentials enrolled for the user or a FIDO2 security key
- MDM-managed: Microsoft Intune or other MDM solution
Licensing Requirements for Windows Editions
Windows editions that support Windows passwordless experience include Windows Pro, Windows Enterprise, Windows Pro, Education/SE, and Windows Education. The following licenses grant Windows passwordless experience license entitlements.
- Windows Pro/Pro Education/SE
- Windows Enterprise E3
- Windows Enterprise E5
- Windows Education A3
- Windows Education A5
Enable Windows Passwordless Experience using Intune
Using Microsoft Intune, you can configure a policy for passwordless authentication. Settings Catalog can be used for this. The steps below will guide you.
- Sign in to Microsoft Intune admin center
- Go to Devices > Configuration > +Create
- Click on the New Policy from +Create
- Select Windows 10 and later as the Platform
- Settings Catalog as Profile type
- Click on the Create button
- On the Basic tab, enter the
- Name – Enable passwordless authentication Experience
- Description – This policy is created to Enable passwordless authentication Experience
- On the Configuration Settings, click on the +Add settings
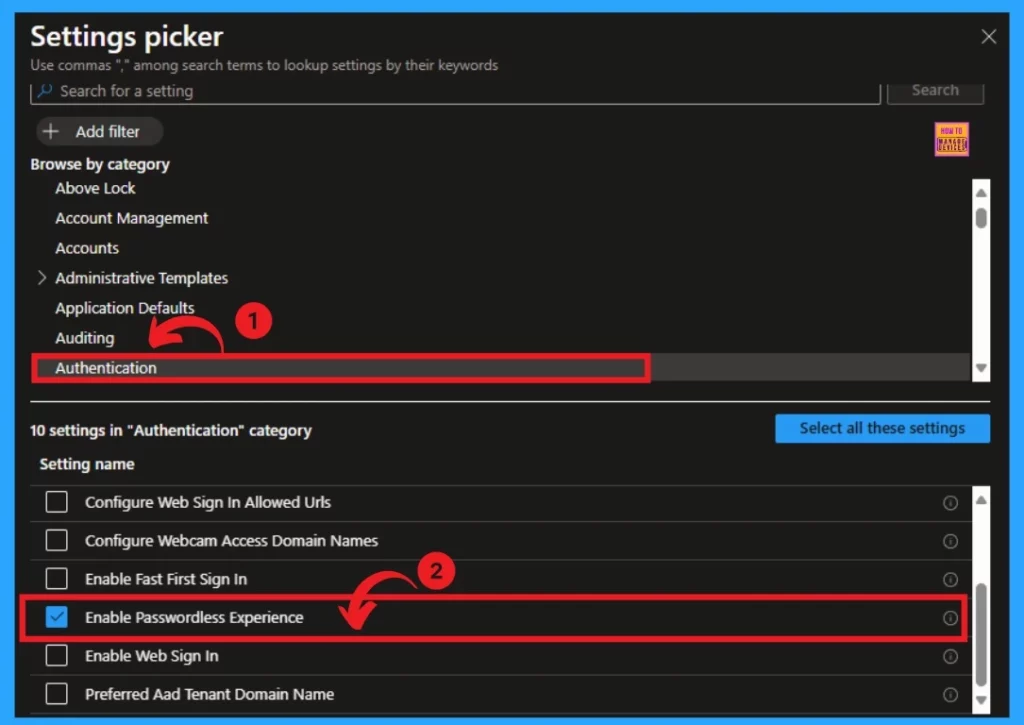
- on the Settings Picker, Select the Authentication Category
- Click on the checkbox near the Enable Passwordless Experience
Read More – The Best Method to Enable Windows Passwordless Experience using Intune
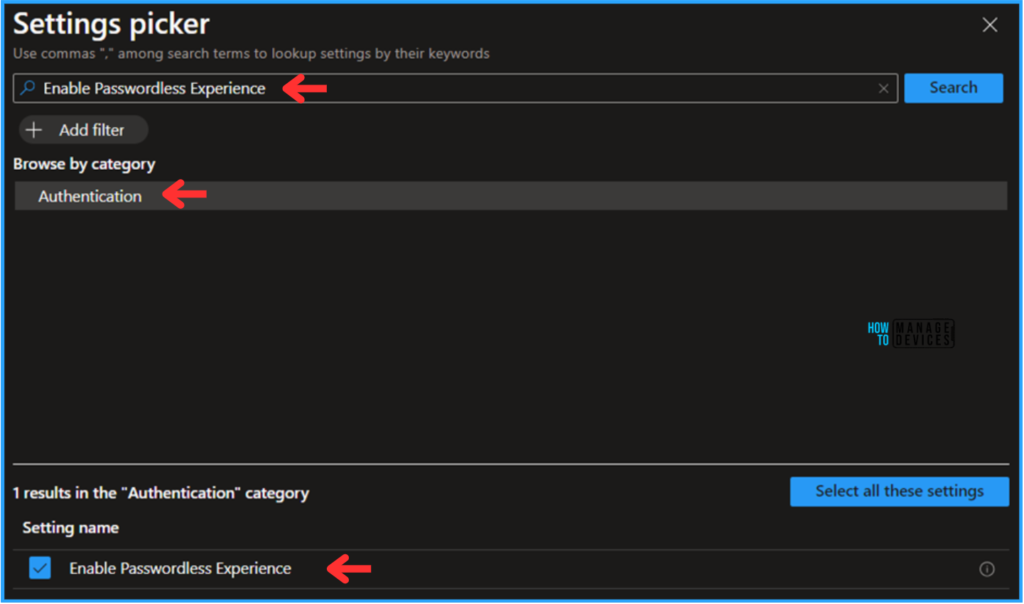
On the next page, choose Enabled from the Enable Passwordless Experience drop-down menu. This will activate the passwordless experience on Windows. Finally, click Next to proceed.
User Experiences
Here, I show the lock screen experience and in-session authentication. I will then share the users’ experience when the passwordless experience is turned off or on.
Lock Screen Experience
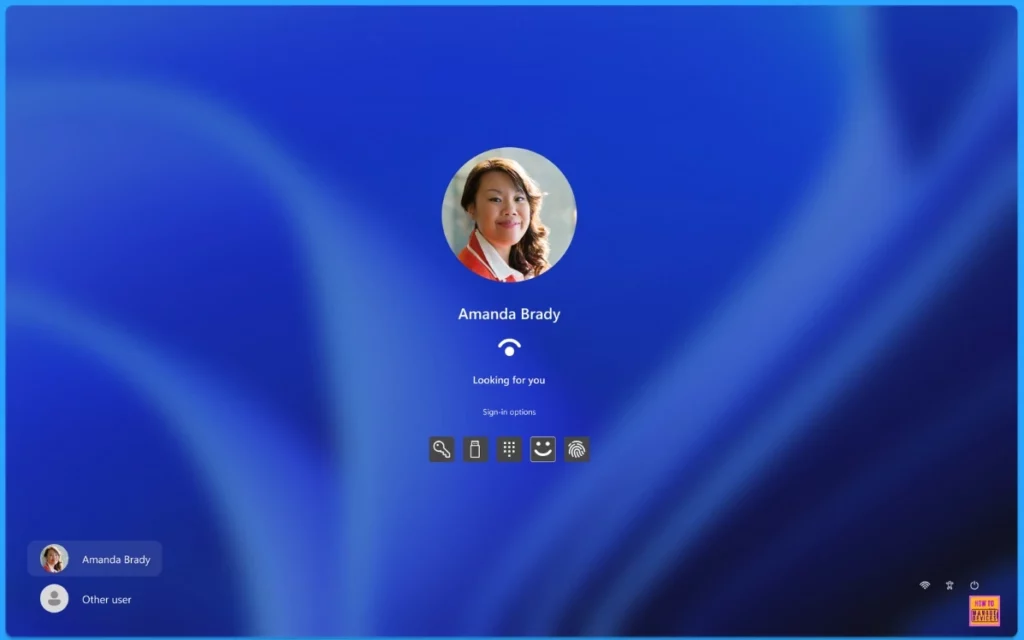
Some changes will appear after enabling or disabling passwordless Authentication. When the Passwordless experience is turned off, users can sign in using a password, as indicated by the presence of the password credential provider in the Windows lock screen.
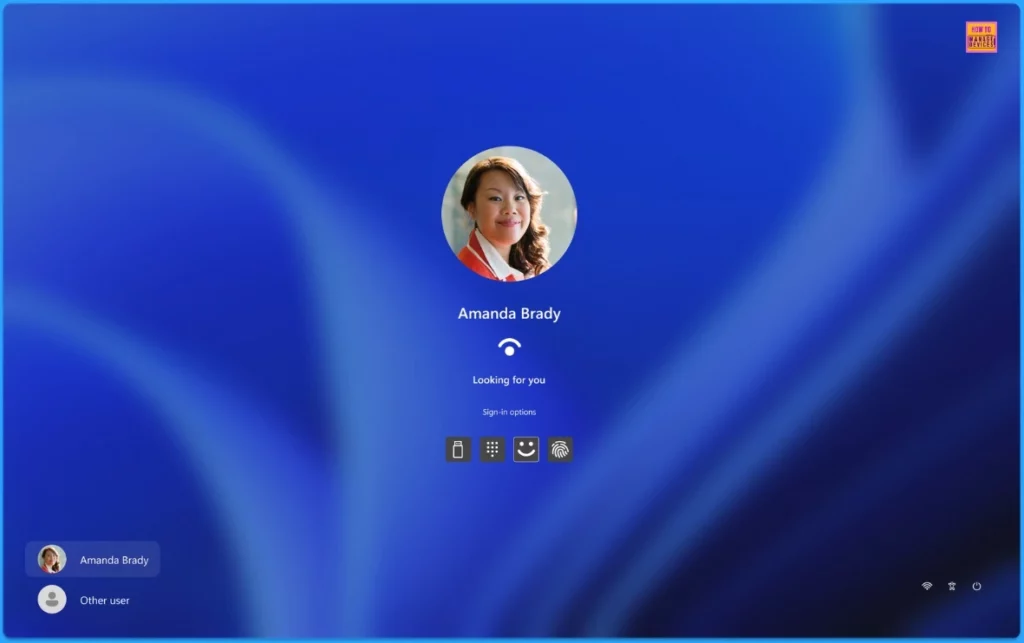
The passwordless experience is turned on. The password credential provider is missing for the last user who signed in with strong credentials. A user can either sign in using a strong credential or opt to use the Other user option to sign in with a password.
Read More – How to Create and Use Passkeys in Windows
In-Session Authentication Experiences
After enabling the Windows passwordless experience, users can’t use the password credential provider for in-session authentication scenarios. The following are some scenarios.
- Password Manager in a web browser
- Connecting to file shares or intranet sites
- User Account Control (UAC) elevation, except if a local user account is used for elevation
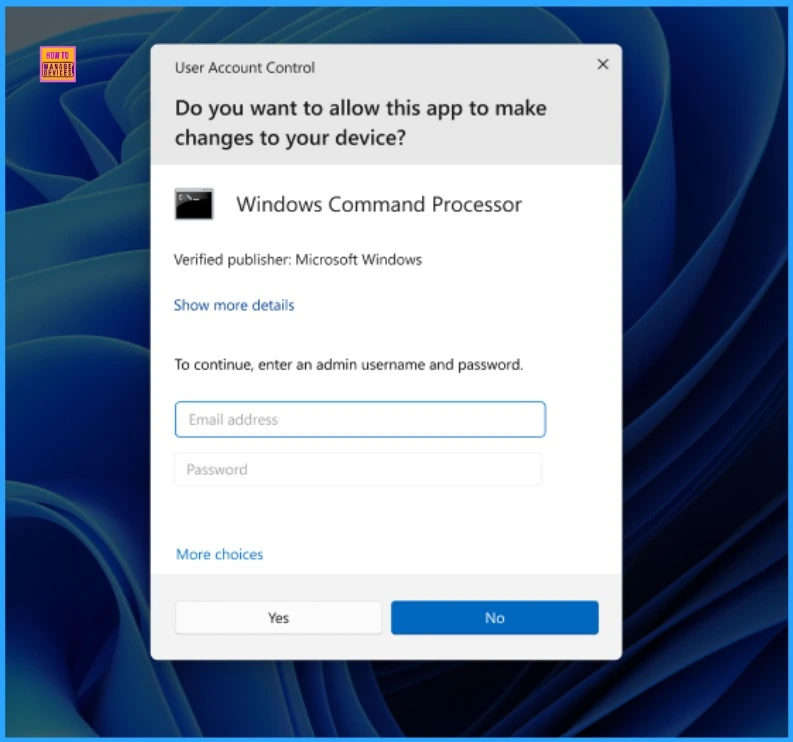
When Passwordless Experience Turned Off
When the Passwordless experience is turned off, UAC elevation allows the user to authenticate using a password. The screenshot below will help you.
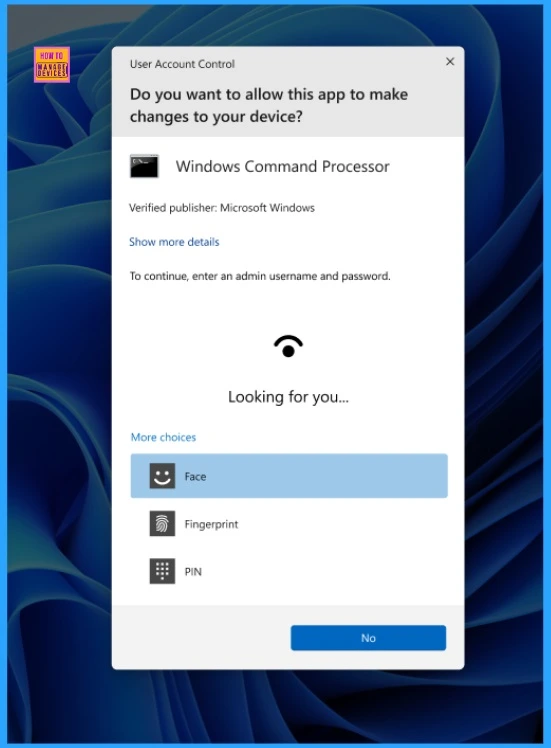
When Passwordless Experience Turned On
When Passwordless Experience is Turned On, UAC elevation doesn’t allow the user to use the password credential provider for the currently logged-on user. If available, the user can authenticate using Windows Hello, a FIDO2 security key, or a local user account.
Recommendations
There are some recommedations you should consider before enabling Windows passwordless experience. The below table shows the recommadations.
| Recommendations |
|---|
| If Windows Hello for Business is enabled, configure the PIN reset feature to allow users to reset their PIN from the lock screen. The PIN reset experience is improved starting in Windows 11, version 22H2 with KB5030310 |
| Don’t configure the security policy Interactive logon: Don’t display last signed-in, as it prevents Windows passwordless experience from working |
| Don’t disable the password credential provider using the Exclude credential providers policy |
| The Exclude credential providers policy disables passwords for all accounts, including local accounts. Windows passwordless experience only applies to Microsoft Entra accounts that sign in with Windows Hello or a FIDO2 security key. It also excludes Other User from the policy, so users have a backup sign in option |
| Exclude credential providers policy prevents the use of passwords for RDP and Run as authentication scenarios |
| To facilitate helpdesk support operations, consider enabling the local administrator account or create a separate one, randomizing its password using the Windows Local Administrator Password Solution (LAPS) |
Known Issue on Passwordless Authentication
A known issue affected on Known Issue on Passwordless Authentication. There’s a known issue affecting the in-session authentication experience when using FIDO2 security keys, where security keys aren’t always an available option. The product group is aware of this behavior and plans to improve this in the future.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Resource
Windows passwordless experience
Author
Anoop C Nair has been Microsoft MVP from 2015 onwards for 10 consecutive years! He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is also a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.

Can this feature be enabled as optional ? Or do we need to work with excluded groups ?