ConfigMgr SCCM Setup Co-Management CMG Azure Cloud Services. The Cloud Management Gateway (CMG) provides a simple way to manage SCCM clients online.
As the SCCM CMG continues to evolve, it is important to stay updated with the latest version to take advantage of the continuously enhanced features.
The CMG is a PaaS (Platform As A Service) solution in Azure. So, unlike with an Azure IaaS (Infrastructure As A Service) solution, we don’t need to maintain the servers in the Azure platform.
Before implementing Co-Management CMG, we must set up and configure Azure Cloud Services within SCCM. Co-Management CMG is not a prerequisite for all the SCCM Co-Management scenarios.
Table of Contents
Video Step-by-Step Guide to Setup Cloud Management Gateway
Utilize the Azure Services Wizard to streamline the configuration of your Azure cloud services with SCCM. I’ve covered this in the video tutorial.
Co-Management Related Posts
- All Co-Management Video tutorials
- Overview Windows 10 Co-Management with Intune and SCCM
- Custom Report to Identify Machines Connected via SCCM CMG
- How to Setup Co-Management – Introduction – Prerequisites Part 1
- How to Setup Co-Management – Firewall Ports Proxy Requirements Part 2
- Setup Co-Management – AAD Connect UPN Suffix Part 3
- SCCM CMG Cloud Management Gateway Implementation Guide
SCCM Cloud Management Gateway – CMG Requirements
Co-Management CMG is not a prerequisite for all SCCM Co-Management scenarios. However, it is required for the scenario where you want to install an SCCM client from the internet. SCCM Cloud Management Gateway (CMG) and CDP are needed in the abovementioned situation.
- Azure subscription with Azure Admin access to host the CMG
- Azure Cloud Services Configured within SCCM (Azure AD User Discovery – for some authentication scenarios)
- Azure Web and Client applications (Part of Azure Cloud Services)
- Azure Resource Manager (ARM) SCCM 1802 or later to avoid Azure Management certificates
- Client Authentication Certificate – Root Cert and Intermediate/Issuing certificates (PKI or Public Certificates)
- Server Authentication Certificate (Web Server Template & Custom web server certificate with CMG/CDP CNAME)
- The service connection point must be in online mode
Before implementing the Co-Management CMG setup, I recommend reading the CMG Prerequisite and Certificate requirements.
Setup Azure Services – Cloud Management
I would recommend going through and configuring Azure services cloud management before proceeding with CMG configuration.
Use the Azure Services Wizard to simplify setting up your Azure cloud services with SCCM. I have also explained this in the video tutorial.
Azure Services configuration wizard provides a standard configuration experience using Azure Active Directory (Azure AD) web app registrations.
This wizard creates Web and Client (native) applications to manage subscription and configuration details and authenticate communications with Azure AD.
Cloud Management: This service enables the SCCM site and clients to authenticate Azure AD. This authentication allows for other scenarios, such as:
Install and assign SCCM Windows 10 clients using Azure AD for authentication
Configure Azure AD User Discovery
Support specific Cloud Management Gateway scenarios
Configure Azure Services
This wizard helps you deploy and configure Azure services through SCCM. I explained it in the Video Tutorial.
Navigate via \Administration\Overview\Cloud Services\Azure Services – Click on the Configure Azure Services button from the ribbon menu.
1. Select an Azure service and specify the name, description
- Name:- ACN Azure Cloud Services
- Description:- Any full, meaningful description
2. Select Cloud Management and click on the NEXT button to proceed further
Note – Deploying the Azure service for Cloud Management enables SCCM clients to authenticate with the site using Azure AD. You can also allow the discovery of Azure AD resources for this tenant.
3. Select AzurePublicCloud as Azure Environment from the App properties page
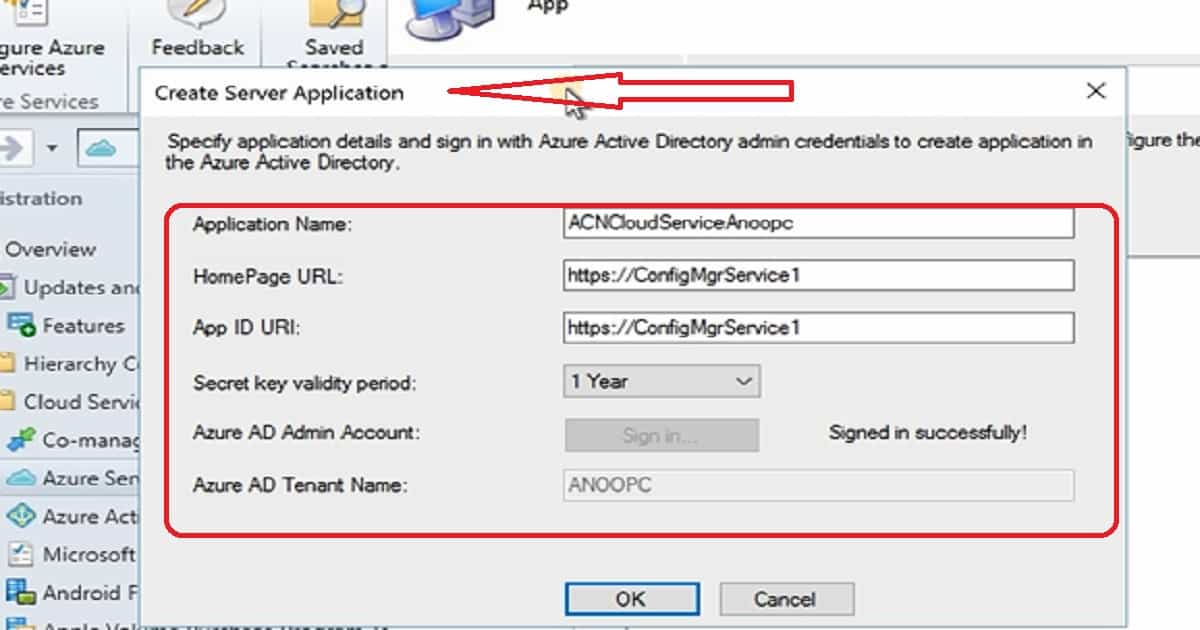
4. Create a new WEB APP in Azure for Authentication (Server App for SCCM). Add an application that represents a web application, a web API, or both.
Server App—To configure Azure services, Select a list of available server apps. You can also import or create a server app. In this scenario, I opted to create a new Server Application.
Specify application details and sign in with AAD admin credentials to create an application in the Azure Active Directory
- Application Name: ACNCloudServiceAnoopC
- Homepage URL: https://ConfigMgrService1
- App ID URI: https://ConfigMgrService1
- Secret Key Validity Period: 1 Year
- Azure AD Admin Account: Sign in – Signed in successfully!
- Azure AD Tenant Name: ANOOPC
5. Create a NATIVE Client App. A native client is an application that can be installed on a user’s device or computer. To Create a Client Application, Specify application details and sign in with AAD admin credentials to create an application in the Azure Active Directory.
- Application Name: ACN CloudService AnoopC
- Reply URL: https://ConfigMgrClient1
- Azure AD Admin Account: Sign in – Signed in successfully!
- Tenant Friendly Name: ANOOPC
- App Friendly Name: ACN CloudService AnoopC
- Service Type: Blank
6. Enable Azure AD Discovery on the Configure Discovery Settings page. Click the Settings button to check and configure the advanced options of AAD Discovery.
Azure AD User Discovery – Configure the settings to discover resources in the Azure AD. When resources are discovered, SCCM creates records in the SCCM DB for them and their associated information.
We must enable Azure AD discovery to allow the AAD authentication scenario in SCCM. If you want SCCM to authenticate the AAD user, you must first have the user discovered.
As I showed in the video tutorial, you must provide/grand appropriate permissions for the WEB (Server) application on Azure.
Setup Co-Management CMG (Cloud Management Gateway)
Before starting a Co-management CMG setup, ensure all the prerequisites and certs are available. I have also explained this in the video tutorial.
- Navigate via SCCM CB console – \Administration\Overview\Cloud Services\Cloud Management Gateway
- Click on Create Cloud Management Gateway icon in the ribbon menu
- Select Azure Environment as AzurePublicCloud on Specify details of this cloud service page
NOTE – Specify the Azure environment and the deployment method for the cloud service. Provide Azure subscription ID, the management certificate, or Azure AD administrator credentials to proceed.
4. Choose how you want to deploy your cloud Service – Azure Resource Manager (ARM) deployment
Note:- Please use an administrator account to access your Azure subscription. SCCM will obtain the subscription information and contribute the permission required to deploy the service.
- Subscription Admin Account: Sign In
- Subscription ID: Automatically gets populated once you log in with the Azure admin account
- Azure AD App Name: ACNCloudServiceAnoopC (WEB/Server Application which we created (above) will automatically get populated)
- Azure AD Tenant: ANOOPC (Automatically gets populated once you log in with Azure admin account)
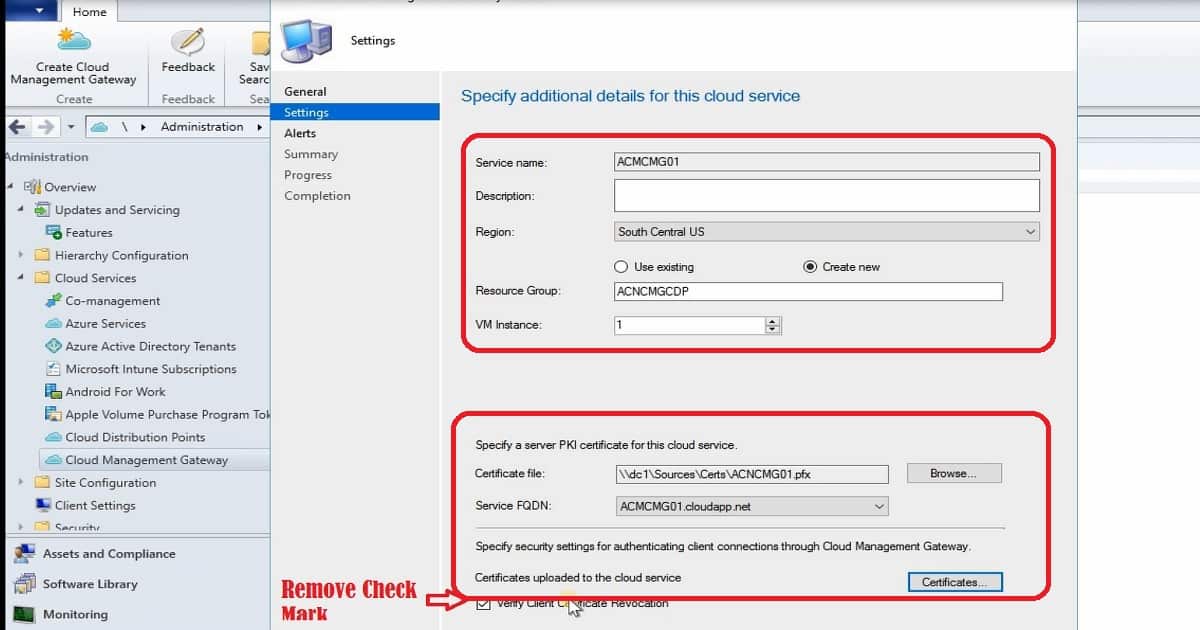
5. Specify Additional Details for the cloud Service (CMG) page
Service Name: ACMCMG01 Automatically gets populated based on the CName mentioned in the certificate. You won’t be able to change it. As explained in the previous blog, you need to create a new WEB certificate to change the service name.
Description: Useful information to identify the CMG instance if you have more than one CMGRegion: South Central US
Resource Group: ACNCMGCDP. Click on the Create New radio button above and give it a meaningful name.
VM Instance: 1 (depending on your requirement)
Select the CMG PFX file created for CMG in the previous post about creating certs. We need to specify a server PKI certificate for this cloud service.
Certificate File: Select the PFX file created for CMG in the previous post. Enter the password for the PFX certificate. Once you have uploaded the PFX cert successfully, the Service Name and Service FQDN will automatically populate.
Service FQDN: ACMCMG01.Cloudapp.net These details will be populated automatically, as mentioned above.
Specify security settings for authenticating client connections through CMG (Cloud Management Gateway).
Certificates uploaded to the cloud services: Click on the Certificates button to upload Root CA and Intermediate/Issuing CA certs. I have only root CA in the chain of certs. Click on Add to upload certificates to the cloud service.
Remove the “Verify Client Certificate Revocation” check box when you have not published CRL on the internet. I recommend publishing CRL to the internet to have a more secure PKI. However, I don’t use this for my lab environment.
Sample Configuration Details of SCCM Cloud Management Gateway (CMG) Wizard
General • Subscription ID: dda75f69a-5a3b-4ecd-b385-db1223e9549873 • Azure AD application: ACNCloudServiceAnoopc Settings • Service Name: ACMCMG01 • Description: • Primary Site: Primary CB 2 (PR3) • Region: South Central US • Resource group: ACNCMGCDP • Service Certificate:\\dc1\Sources\Certs\ACNCMG01.pfx • CName:ACMCMG01.cloudapp.net • Number of Instances: 1 • Root Certificate: 681B323ghdAC90E2523489898HUD7C0E4015E812; • Verify client certificate revocation enabled:True Alerts • Outbound Data Transfer Threshold:Enabled • Outbound Data Transfer Threshold:10000 GB • Outbound data transfer Warning alert level: 50% • Outbound data transfer Critical alert level: 90%
Setup Co-Management – Cloud Management Gateway Connector
The CMG connection point is the SCCM site system’s role for communicating with the CMG and on-prem components like MP/SUP. I have also explained this in the video tutorial.
Add new Site System Role – Select a server to use as a site system. When you have only one site system – Click NEXT.
System Role Selection – Specify roles for this server – Select Cloud Management Gateway Connection Point
Specify the Cloud Management Gateway Connection Point settings. When you have more than one CMG in your SCCM environment, you can select a relevant one from the drop-down option. For me, it’s only one CMG.
Cloud Management Gateway Name: ACMCMG01.CLOUDAPP.NET
Region: South Central US
Install client authentication certificate manually for CMG connection point to communicate with client-facing site roles in HTTPS mode.
Azure Portal experience Co-Management CMG
Login to Azure Portal and click on Subscriptions – Resource Groups – ACMCMG01
There will be 2 (two) services associated with Resource Group, which we create from the SCCM console. The video tutorial provides more details.
1. ACMCMG01 PaaS server for CMG service
2. acmcmg01 storage account for CMG
Click on PaaS server ACMCMG01 to check the details. You can also log in to the server and check (there is no need to log in and check in normal scenarios).
SCCM Cloud Management Gateway CMG Log Files
The following table lists the log files that contain information related to the cloud management gateway.
| Log name | Description | Computer with log file |
|---|---|---|
| CloudMgr.log | Records details about deploying the cloud management gateway service, ongoing service status, and associated user data. You can configure the logging level by editing the Logging level value in the registry key HKLM\SOFTWARE\ Microsoft\SMS\COMPONENTS\ SMS_CLOUD_ SERVICES_MANAGER. | The installdir folder is on the primary site server or CAS. |
| CMGSetup.log1 | Records details the second phase of the cloud management gateway deployment (local deployment in Azure). You can configure the logging level using the setting Trace level (Information (Default), Verbose, Error) on the Azure portal\Cloud services configuration tab. | The %approot%\logs on your Azure server or the SMS/Logs folder on the site system server |
| CMGHttpHandler.log1 | Records details about connecting the cloud management gateway service and the cloud management gateway connection point. | The %approot%\logs on your Azure server or the SMS/Logs folder on the site system server |
| CMGService.log1 | Records details about the cloud management gateway service core component in Azure. You can configure the logging level using the setting Trace level (Information (Default), Verbose, Error) on the Azure portal\Cloud services configuration tab. | The %approot%\logs on your Azure server or the SMS/Logs folder on the site system server |
| SMS_Cloud_ ProxyConnector.log | Records details about setting up connections between the cloud management gateway service and the cloud management gateway connection point. | Site system server |
- Setup Co-Management – CA PKI & Certificates Part 4
- Setup Co-Management Cloud DP Azure Blob Storage Part 5
- Setup Co-Management Azure Cloud Services CMG Part 6 (This Post)
- SCCM Configure Settings for Client PKI certificates Part 7
- How to Setup SCCM Co-Management to Offload Workloads to Intune – Part 8
- How to Deploy SCCM Client from Intune – Co-Management – Part 9
- End User Experience of Windows 10 Co-Management – Part 10
Resources
- https://docs.microsoft.com/en-us/sccm/core/clients/manage/cmg/plan-cloud-management-gateway
- https://docs.microsoft.com/en-us/sccm/core/servers/deploy/configure/azure-services-wizard
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here –HTMD WhatsApp.
Author
Anoop C Nair is Microsoft MVP! He is a Device Management Admin with more than 20 years of experience (calculation done in 2021) in IT. He is a Blogger, Speaker, and Local User Group HTMD Community leader. His primary focus is Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc.

Hi,
Is it possible to join a w10 to only AAD (with automatic Intune enrollment) and install the configmgr client on it via the install string thats displayed during co-mgmt configuration? Of we try this the configmgr client never initialize. On technet rendement is hybrid aad joined so i presume it will not work for pure aad joined/Intune devices, correct?
Hi there,
If we are using a 3rd Party DigiCert certificate for the cloud service, do we still need to upload our internal root cert as in section:
Specify security settings for authenticating client connections through Cloud Management Gateway
Our computers are all connected to on prem AD.
how many tenants we can attach in MECM console
It looks like Microsoft may have clarified the recommendations for the APP ID registration url to show the following recommened formatting:
api://{tenantId}/{string}, for example, api://5e97358c-d99c-4558-af0c-de7774091dda/ConfigMgrService
https://{verifiedCustomerDomain}/{string}, for example, https://contoso.onmicrosoft.com/ConfigMgrService
In testing, I found that the https://Configmgrservice formatting prevents AAD user token retrieval. Device management seemed to work ok, but things like application request approval through the CMG did not until the App ID registration url was changed to recommended format. CcmAADBroker.log will show an error if this is not working properly.