In this article am going to explain. How to create Secure Boot Compliance Policy with Microsoft Intune. Secure Boot is a critical security feature that ensures devices boot only with trusted software, protecting them from rootkits and bootkits.
With Microsoft Intune, you can enforce Secure Boot through compliance policies, enhancing the security of your organization’s managed devices. These policies validate that Secure Boot is enabled on devices, helping to safeguard against unauthorized firmware or software during the boot process.
Once you configured the any compliace policy define actions for non-compliance, such as sending alerts or blocking access via Conditional Access policies. This ensures that only compliant devices can access corporate resources.
For successful deployment, ensure that targeted devices support UEFI and have Secure Boot enabled in BIOS/UEFI settings. Test the policy on a pilot group before rolling it out widely to avoid disruptions. Combining this compliance policy with other Intune security configurations, like BitLocker enforcement, creates a robust defense against modern security threats.

Table of Contents
Advantages of Secure Boot Compliance Policy
Implementing a Secure Boot compliance policy in Intune offers several advantages for enhancing an organization’s security posture. By enabling Secure Boot as a compliance standard, organizations significantly enhance endpoint resilience and protect sensitive data from sophisticated attacks.
| Advantage | Description |
|---|---|
| Protection Against Malware | Secure Boot ensures that only trusted software and firmware are loaded during the boot process. This protects devices from advanced threats like rootkits and bootkits that compromise the operating system even before it starts. |
| Improved Compliance and Security Standards | Enforcing Secure Boot aligns devices with industry best practices and regulatory compliance requirements, such as NIST and ISO 27001. It demonstrates a proactive approach to device security management. |
| Reduced Risk of Unauthorized Access | By requiring Secure Boot, you minimize the risk of unauthorized firmware or operating system modifications, ensuring that only validated configurations are used. |
| Enhanced Management via Intune | With Intune, you can monitor Secure Boot status across all managed devices, automate enforcement, and take corrective actions for non-compliance. This simplifies security management and strengthens endpoint protection. |
| Support for Conditional Access | Combining Secure Boot compliance with Conditional Access policies ensures that only secure and trusted devices can access corporate resources, reducing the attack surface for cyber threats. |
- Best Guide to Configure User Confirmed EPM Elevation Settings Policy with Intune
- How to Configure Support Approved EPM Elevation using Intune | Highly secured option
- How to Manage Intune Compliance Policy Settings
- Managing Windows Bitlocker Compliance Policy Using Intune | MS Graph | Grace Period
Create a Secure Boot Compliance Policy
Follow these steps to create a Compliance Policy that check the Secure Boot status of the devices using Microsoft Intune. First, sign in to the Microsoft Intune Admin Center with administrator credentials.
- Navigate to Devices > Windows > Manage Devices > Compliance
- Click on +Create policy
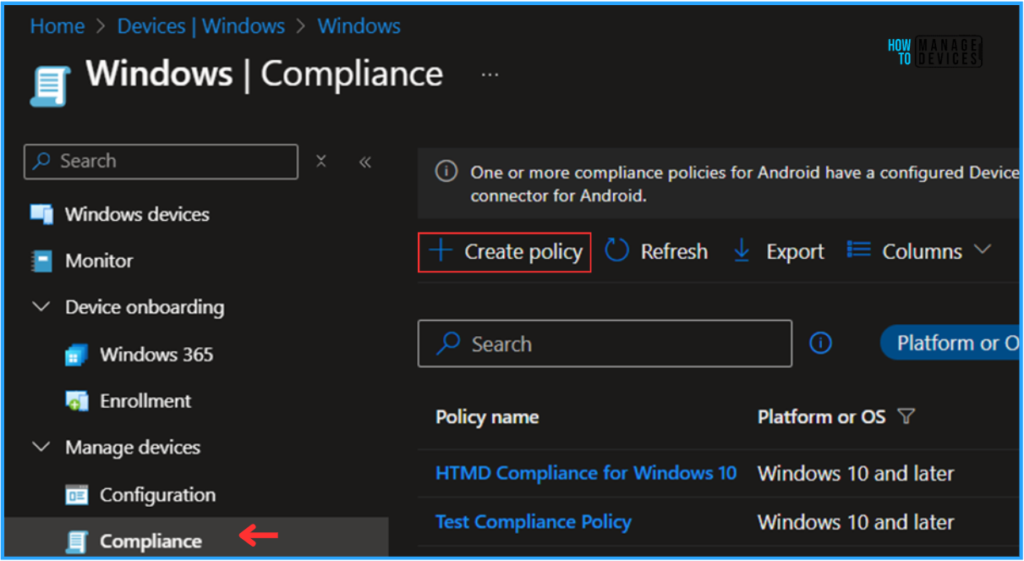
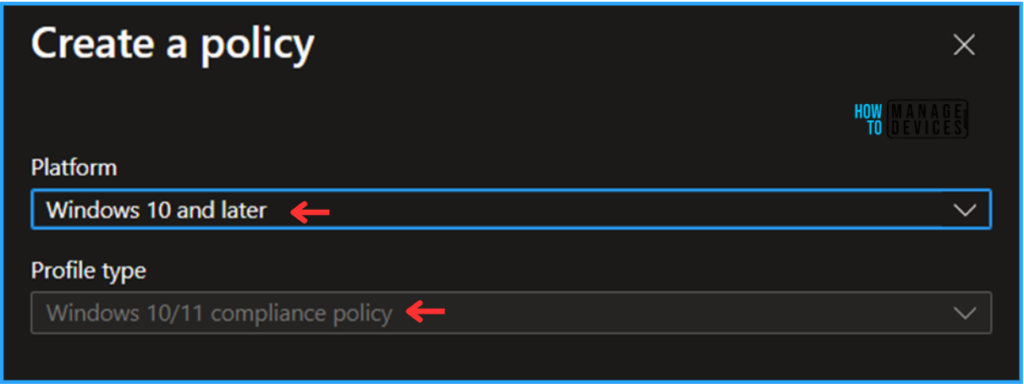
In the next step, we can create a new Compliance Policy from scratch. First, we need to provide the options mentioned below.
- Platform: Windows 10 and later
- Profile type: Windows 10/11 complaince policy will be by default selected
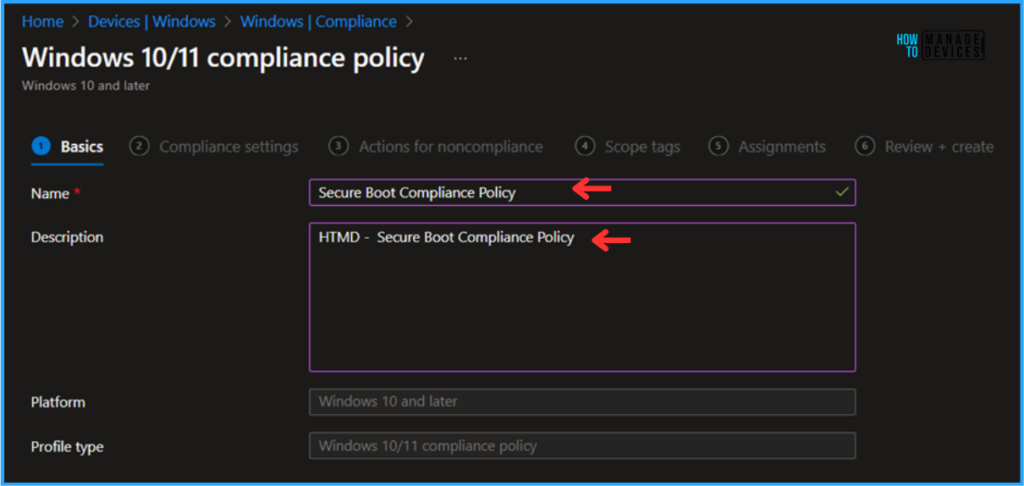
On the Basics details page, we can name the compliance policy “ Secure Boot Compliance Policy” if needed, briefly describe the policy, here am giving description as “HTMD – Secure Boot Compliance Policy”, and click Next.
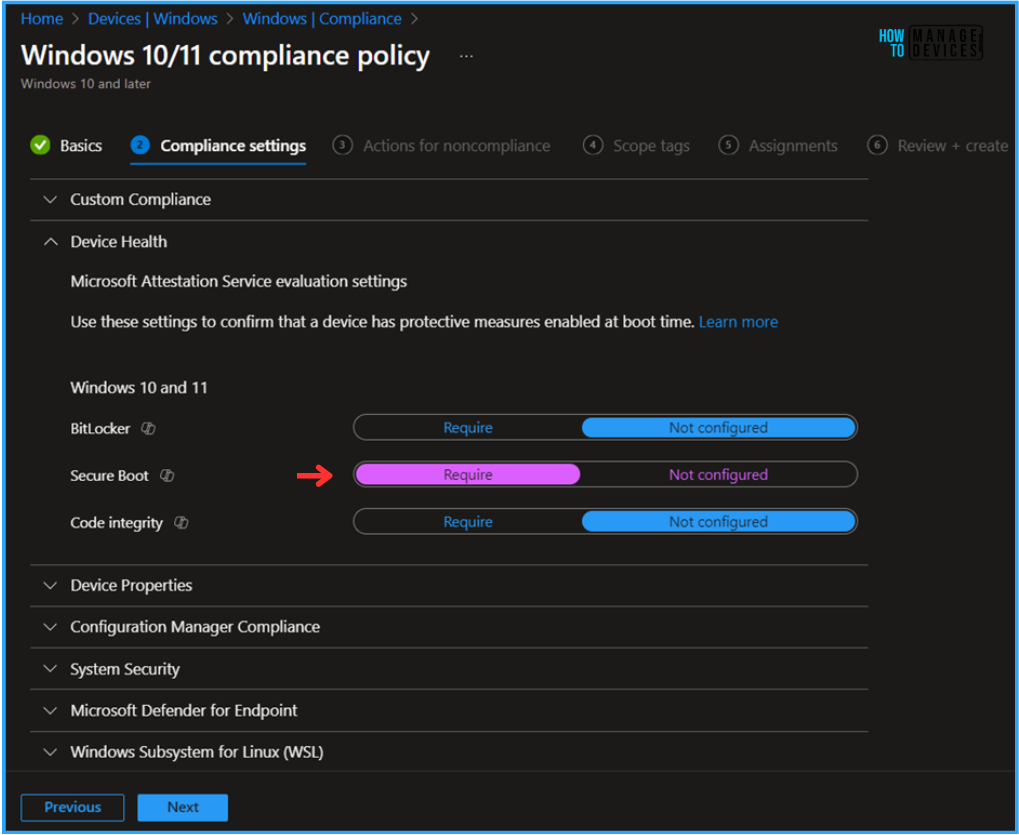
We can now add the required settings to the Compliance settings page. Under the Device Health option toggle the Secure Boot option as Require. Leave the other settings as it is and click on Next.
In the Action of noncompliance pane, Action choose as Mark device noncompliant and Schedule (days after noncompliance) set as immediately. You can manage this settings as per your requirement. Here I am only configured a basic noncompliance action.
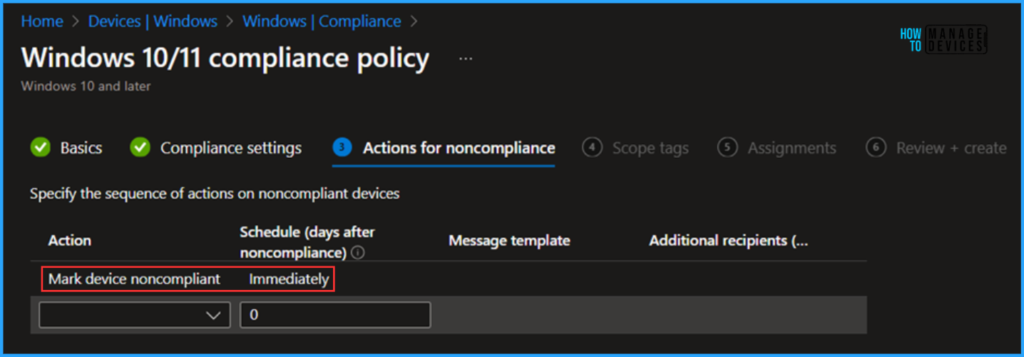
On the next page, Leave the Scope tags as Default. If your tenant has custom scope tags, you can select them based on your policy requirements.
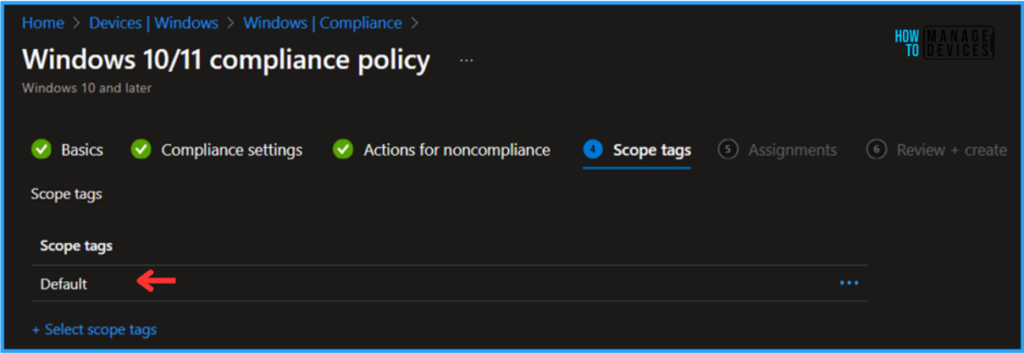
Click on Next. Here, I am assigning the Secure Boot Compliance Policy to HTMD – Test Computers. To do that, click Add groups and select a required device group under the Included Groups option. I am not using any Filter in this example, and the Excluded Groups option was also left blank.
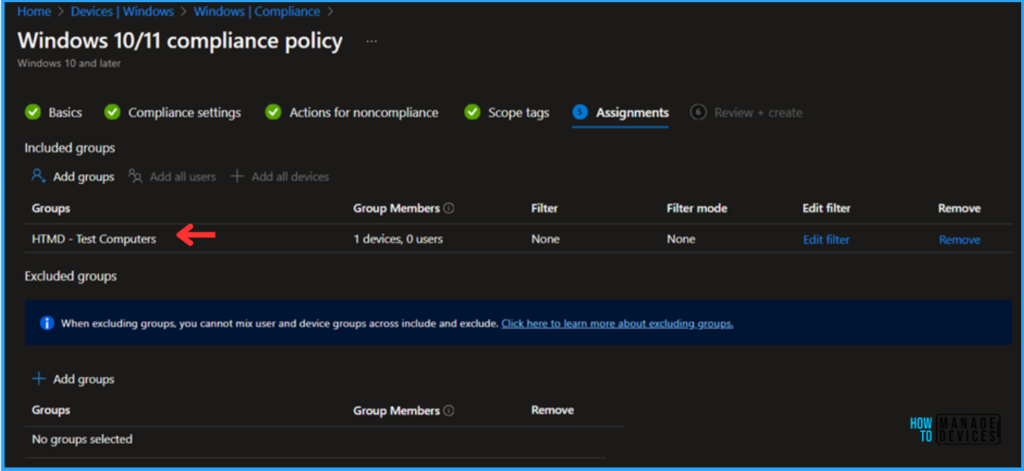
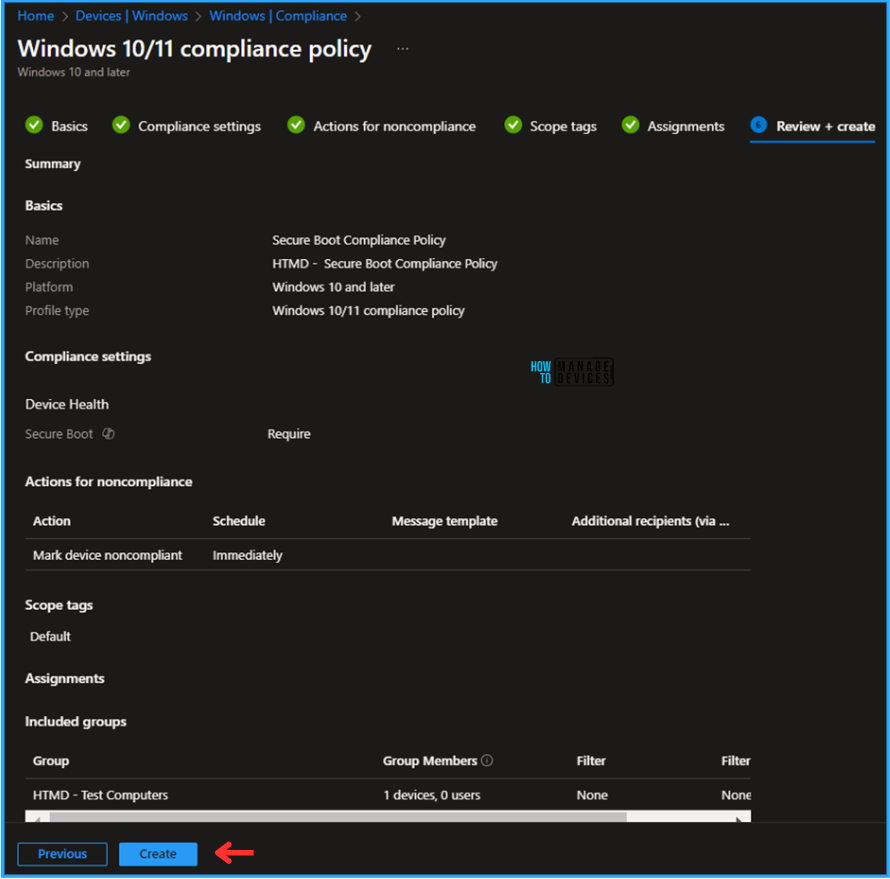
On the Review + Create page, carefully review all the settings you’ve defined for the “Secure Boot Compliance Policy”. Once you’ve confirmed everything is correct, select “Create” to deploy the policy.
- Configure macOS Compliance Policy in Intune for Devices
- Best Way to Auto Update Mozilla Firefox Browser Using Intune Configuration Policy
- Easy Way to Install a Language Pack using Intune PowerShell Script
Monitor the Secure Boot Compliance Policy Deployment in Intune
This complianace policy has been deployed to the HTMD – Test Computers device group, a Microsoft Entra ID group. Once the device is synced, the policy will take effect immediately. To monitor the policy deployment status from the Intune Portal, follow the steps below.
- Navigate to Devices > Windows > Compliance > Search for the “Secure Boot Compliance Policy”.
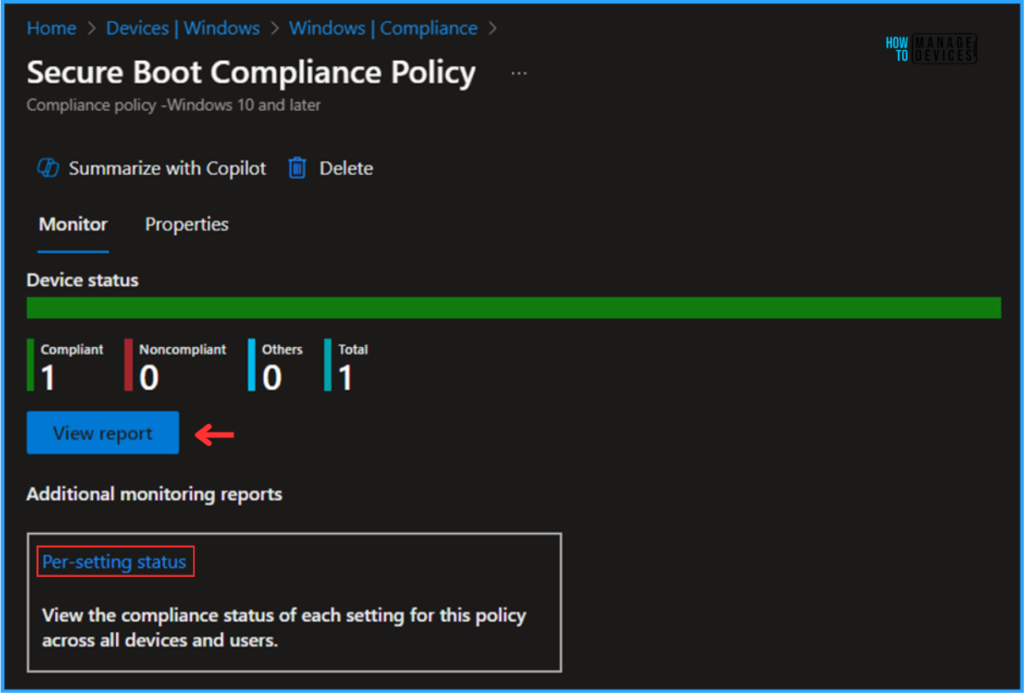
- Under the Monitor you can see the Device status of the particlular policy’s deployment.
To drill through a detailed report, click on the View Report option. The report will display the targeted devices names, logged-in users, policy compliance status, Device Id, OS, and the last connected date & time.
NOTE! Per-setting status provides View the compliance status of each setting for this policy across all devices and users.
End User Experience – Secure Boot Compliance Policy
It’s time to check as per the Intune report whether the Secure Boot is already enabled on the targted devices or not. To check that, login to one of the policy-targeted devices.
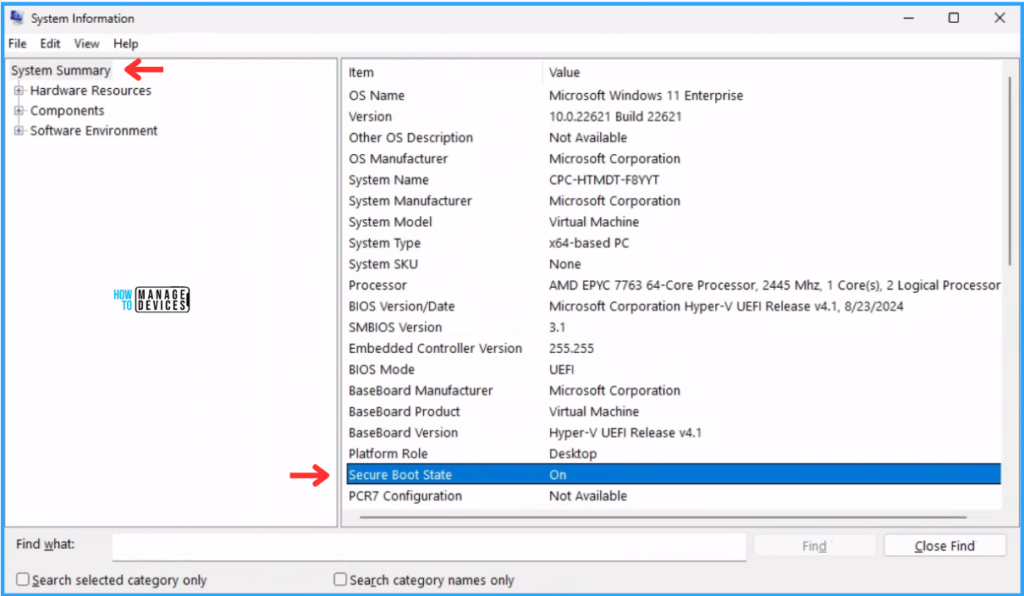
- Open Run and type msinfo32 hit enter
- Under System Summary search for Secure Boot State and the Value should be On
- BIOS Mode will show UEFI
So we can conclue that the newly deployed Compliance Policy checked Secure Boot status of the device correctly!
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Vaishnav K has over 11 years of experience in SCCM, Device Management, and Automation Solutions. He writes and imparts knowledge about Microsoft Intune, Azure, PowerShell scripting, and automation. Check out his profile on LinkedIn.
