In this blog post, I will discuss how to Configure the User Confirmed EPM Elevation Settings Policy with Microsoft Intune. Configuring the User Confirmed Elevation (UCE) settings policy in Intune allows organizations to securely manage how standard users elevate their privileges on Windows devices.
This feature, part of Endpoint Privilege Management (EPM), enables users to temporarily elevate permissions for specific tasks while ensuring that IT maintains control through configurable policies. The UCE policy is ideal for reducing the security risks associated with granting local admin rights while still empowering users to perform necessary administrative actions.
Monitoring is critical to maintaining security. Use Intune’s built-in reporting tools to review elevation events, user justifications, and any anomalies in usage. This not only enhances security but also ensures compliance with organizational policies. With proper configuration, the UCE policy balances operational flexibility and robust security, minimizing risks associated with privilege elevation.
Once configured, assign the policy to the appropriate device or user groups in your organization. Target groups can include specific security or Entra ID groups, ensuring that only designated users have access to elevation capabilities. After deploying the policy, test it on a few devices to verify functionality and ensure users receive the prompts and permissions as expected.

Table of Contents
Essential Points to Note for User Confirmed EPM Elevation Settings Policy
Here are the essential points to note when configuring and deploying the User Confirmed Elevation Settings Policy in Intune.
| Details |
|---|
| Windows 365 (CloudPC) is supported using a supported operating system version |
| Workplace-join devices are not supported by Endpoint Privilege Management |
| Azure Virtual Desktop is not supported by Endpoint Privilege Management |
| Elevation settings policy will show as not applicable for devices that don’t run a supported operating system version |
| Endpoint Privilege Management is only compatible with 64-bit Operating System Architectures. Windows on ARM is not currently supported. |
| Endpoint Privilege Management has some new networking requirements, see Network Endpoints for Intune. |
- How to Configure Support Approved EPM Elevation using Intune | Highly secured option
- How to Configure Support Approved EPM Elevation as Administrator using Intune Policy for Normal Users
- Best Method to Create EPM Elevation Rules Policy from Elevation Request Using Intune Policy
Create a User Confirmed EPM Elevation Settings Policy
To create a User Confirmed Endpoint Privilege Management Elevation Policy from scratch, follow the below steps. First, Sign In to the Microsoft Intune Admin Center using your administrator credentials.
- Navigate to Endpoint Security > Endpoint Privilege Management > Choose Policies.
- Click on +Create policy.
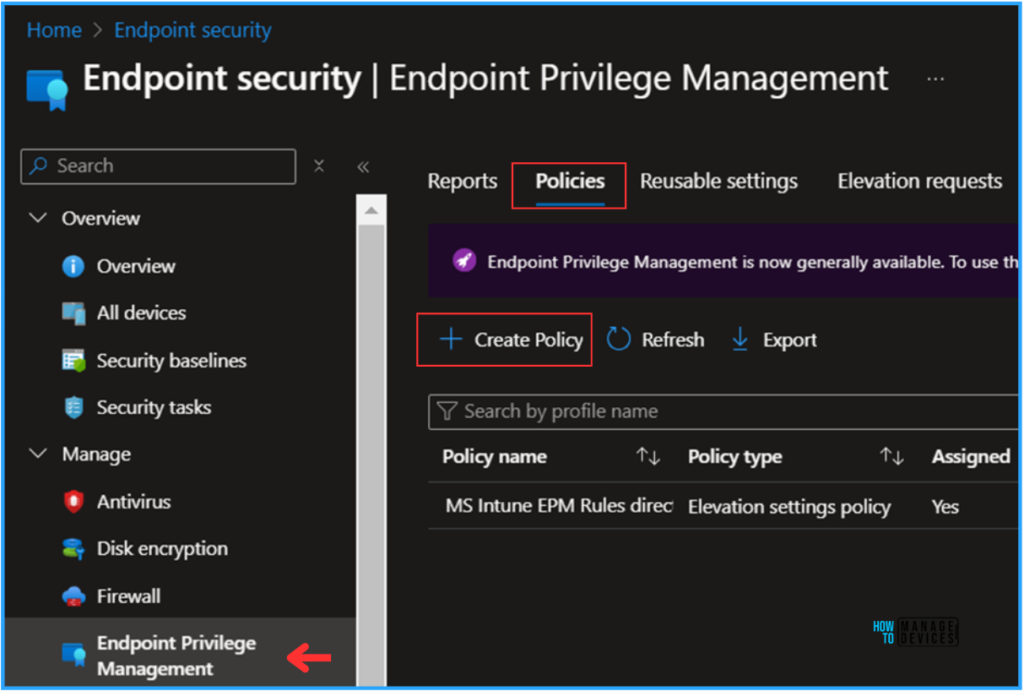
Under the Create a profile window, choose Platform as Windows and the Profile as Elevation settings policy. One more Profile is available in EPM; the Elevation rules policy configures specific predefined rules to support our Elevation settings policy. Here, I am only talking about the User Confirmed Elevation settings policy.
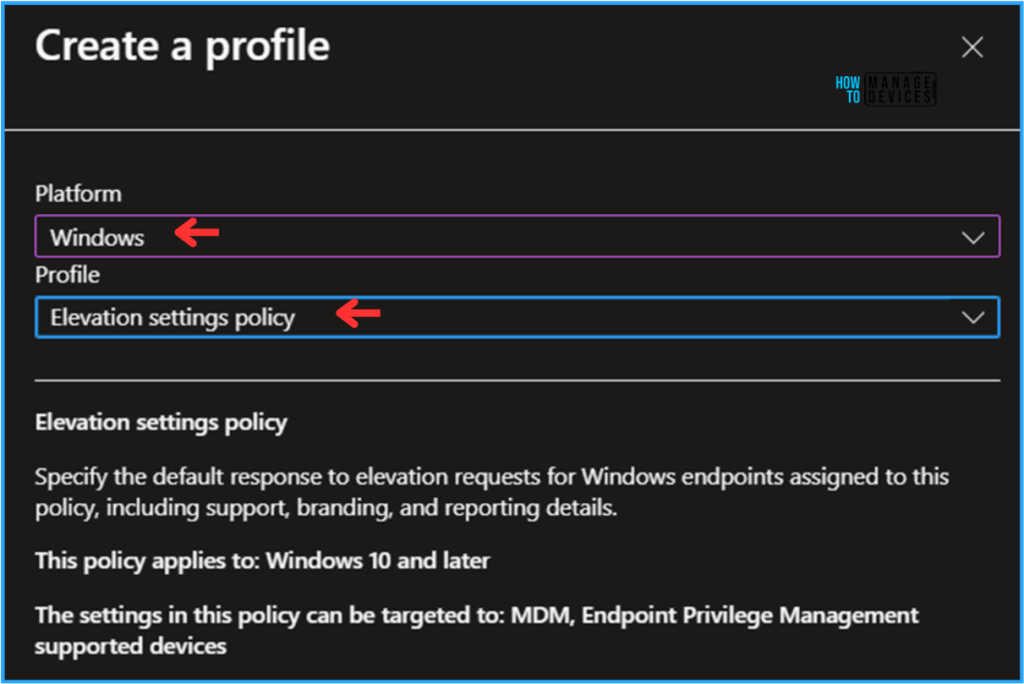
On the Basics details page, I am giving our policy name, HTMD – User Confirmed EPM Elevation Settings Policy. If needed, provide a brief policy description and click Next.
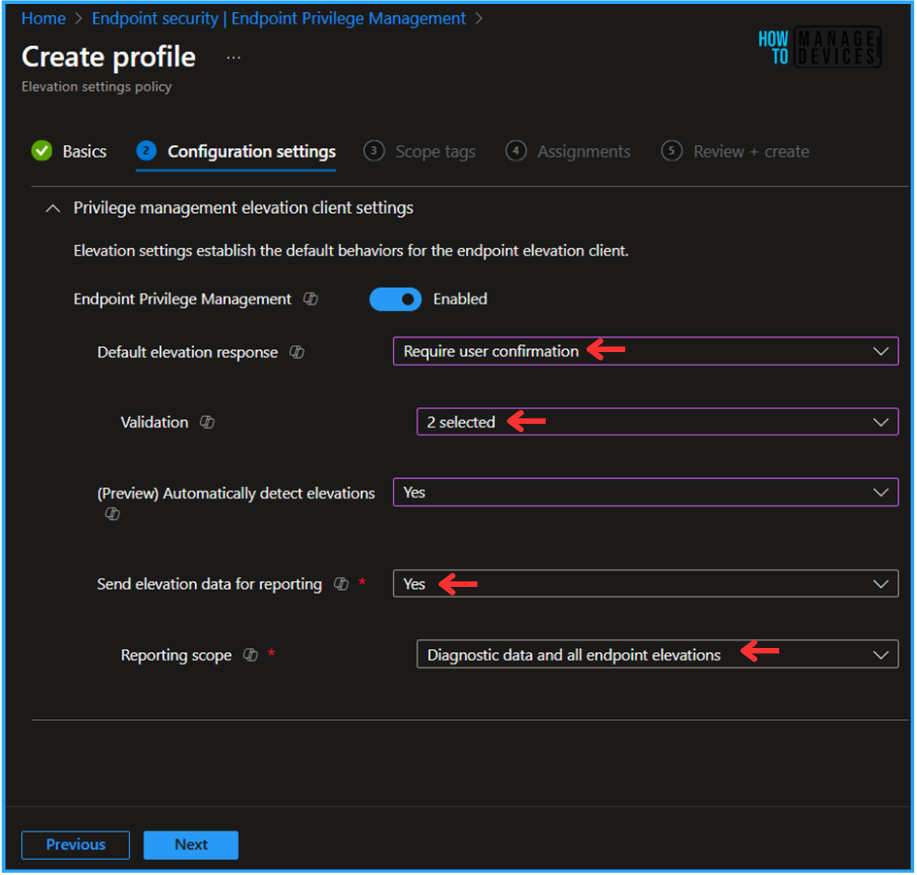
The settings on the Configuration settings page can be configured based on the concept of the User Confirmed EPM. A few options are mandatory. Check the options below and choose them accordingly.
- Endpoint Privilege Management – Enabled (By Default)
- Default elevation response – Require user confirmation
- Validation – Check both Business justification and Windows authentication options
- (Preview) Automatically detect elevations – Yes
- Send elevation data for reporting – Yes
- Reporting scope – Diagnostic data and all endpoint elevations
On the next page, leave the scope tags default; if you have any other custom scope tag available, you can select one based on your requirements.
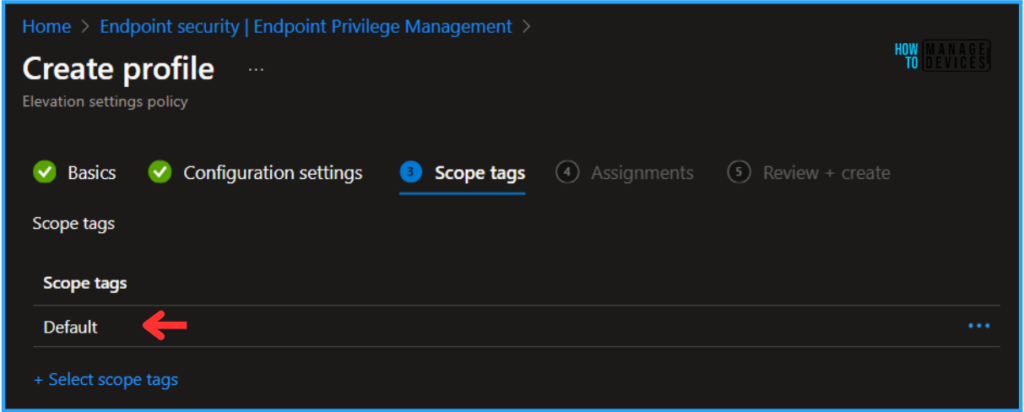
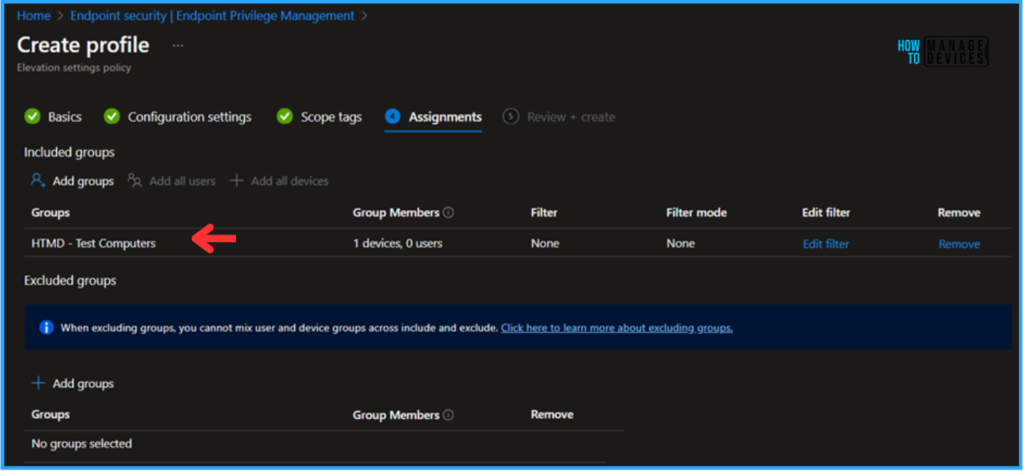
Click Next and assign our Elevation settings policy to a Device Group or a User Group. Both support it. In this example, I am deploying it to a device group, HTMD – Test Computers. To do so, click Add Groups under the Included Groups section and select the required device group.
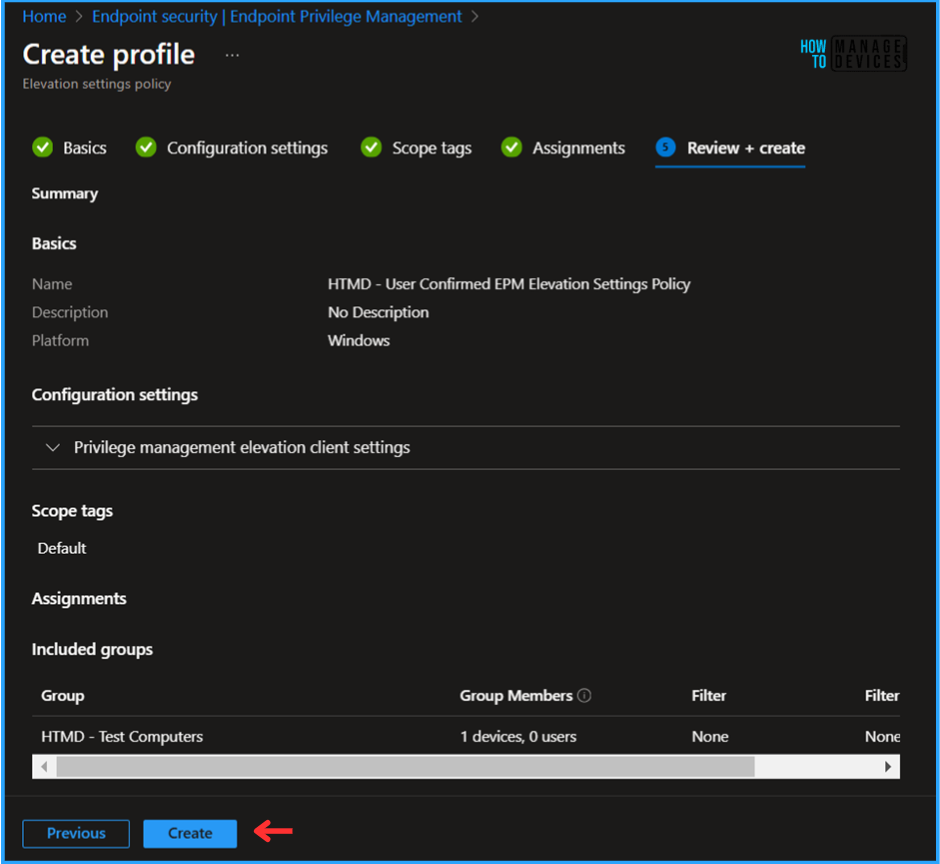
On the Review + Create pane, carefully review all the settings you’ve defined for the User Confirmed EPM Elevation Settings Policy Elevation. Select Create to implement the changes once you’ve confirmed everything is correct.
- Quick Fix to your Windows OS Issues with Detection and Remediation Scripts with Intune
- Easy Way to Install a Language Pack using Intune PowerShell Script
- Best Method to Allow Telemetry or Diagnostic Data with Intune
Monitor the User Confirmed EPM Elevation Policy Deployment
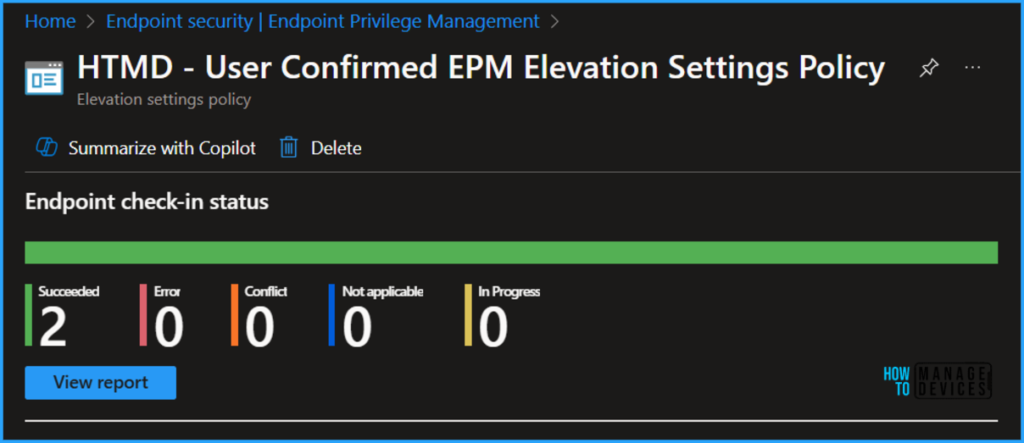
Our newly created EPM policy has been deployed to the Microsoft Entra ID group (HTMD – Test Computers). The policy will take effect as soon as possible once the device is synced.
To monitor the policy deployment status from the Intune Portal, follow the steps below.
- Navigate to Endpoint Security> Under Manage > Endpoint Privilege Management > Policies.
Search for the HTMD – User Confirmed EPM Elevation Settings Policy. Click on that to see our policy’s Endpoint check-in status. Selecting View Report allows you to drill through the deployment, device name, logged user, check-in status, etc.
End User Experience – User Confirmed EPM Elevation Settings Policy
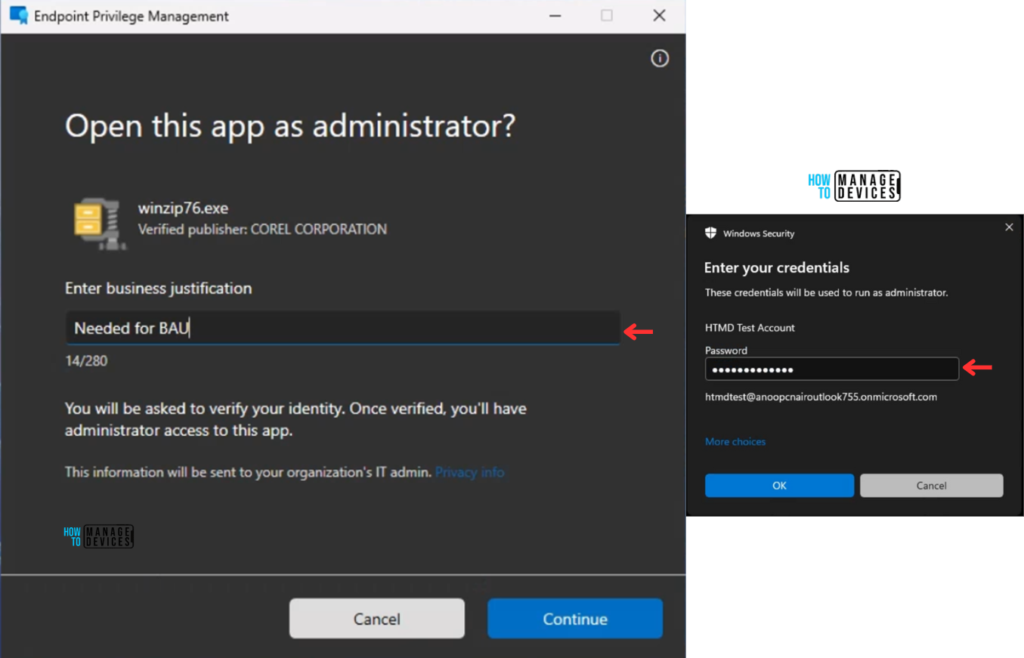
Now, we have to check whether the User Confirmed EPM Elevation Settings Policy is working fine or not. Log in to one of the policy-targeted devices. Just verify the Microsoft EPM Agent Service is running. In this example, I just downloaded and kept winzip76.exe and tried to install it for a standard user (Without admin rights). Follow the below steps.
Right-click on the binary and select Run with elevated access. In the first step, you will get the Enter business justification. Once you enter that and click Continue, you must authenticate with your credentials. Then, you will get the Elevated admin access for that particular app.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Vaishnav K has over 11 years of experience in SCCM, Device Management, and Automation Solutions. He writes and imparts knowledge about Microsoft Intune, Azure, PowerShell scripting, and automation. Check out his profile on LinkedIn.
