Let’s learn to configure automatic lock screen for inactive device Using Intune. You can protect your device from an unauthorized use by lock a computer when idle for some time. The device lock feature allows you to screen lock out option after a period of inactivity.
When you lock the computer, you will be taken to the lock screen by default to unlock and sign in when ready to continue where you left off. However the other users can still sign in to their accounts from the sign-in screen.
If the Machine inactivity limit security policy setting is configured, the device locks not only when inactive time exceeds the inactivity limit, but also when the screensaver activates or when the display turns off because of power settings.
The device lock feature provides protection for lost or stolen devices and provides a means for legitimate users who accidentally enter the device lock state to recover their device and continue using it.
Interactive logon messages may also helpful to reinforce corporate policy by notifying employees of the appropriate policy during the logon process. You can configure this setting in a manner consistent with the security and operational requirements of your organization.
- Enable Interactive Logon CTRL ALT DEL Using Intune
- Collect Intune Logs from MEM Portal Diagnostic Data
- Intune Logs Event IDs IME Logs Details For Windows Client Side Troubleshooting
Set Automatic Lock Screen for Inactive Device Using Intune
Let’s follow the step below to manage device lock inactivity using Intune –
- Sign in to the Endpoint Manager Intune portal https://endpoint.microsoft.com/
- Select Devices > Windows > Configuration profiles > Create profile.
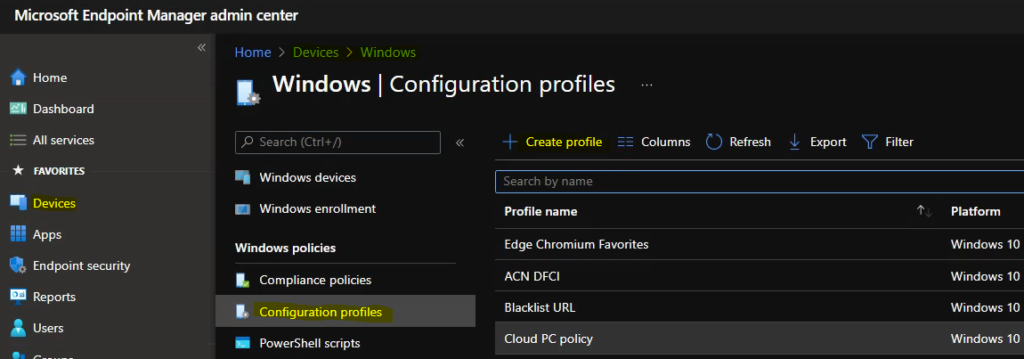
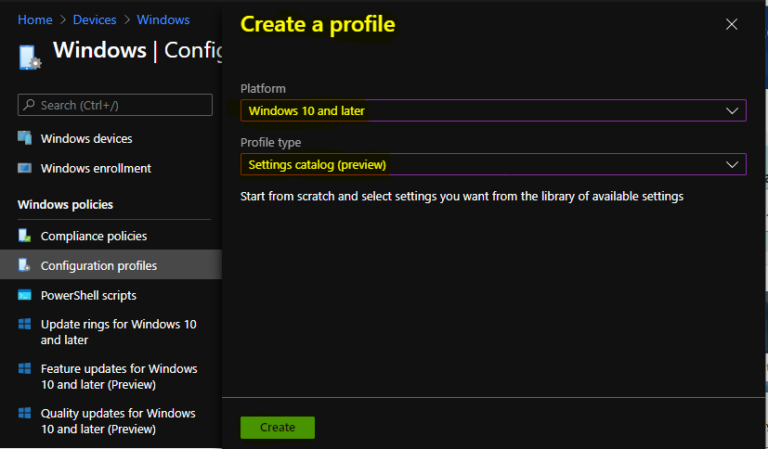
In Create Profile, Select Platform, Windows 10, and later and Profile, Select Profile Type as Settings catalog. Click on Create button.
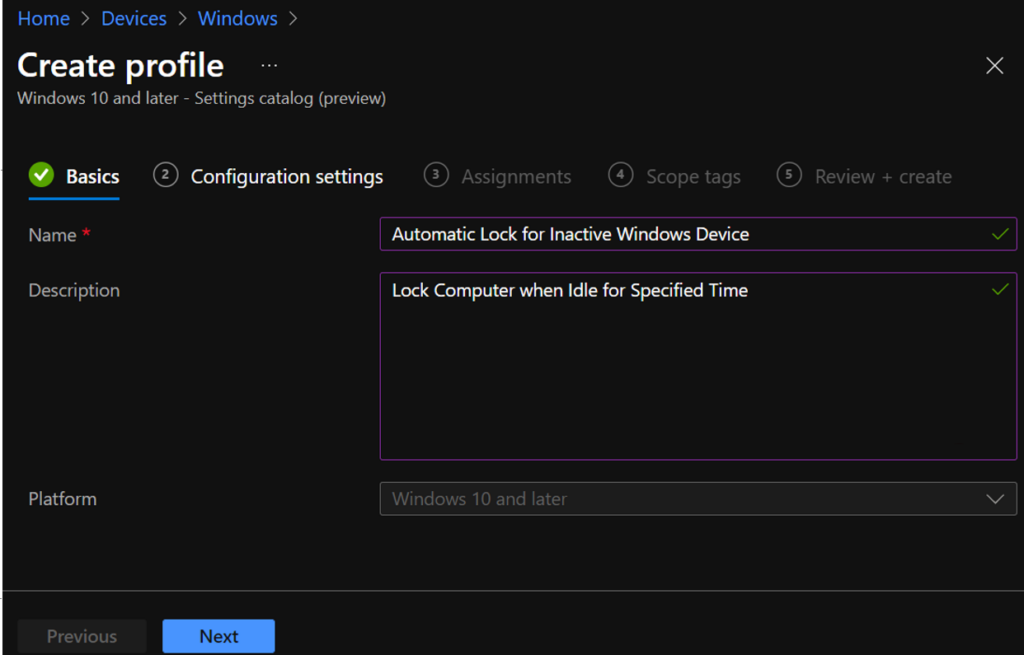
On the Basics tab, enter a descriptive name, such as Automatic Lock Screen for Inactive Device or Automic Lock for Inactive Windows Device. Optionally, enter a Description for the policy, then select Next.
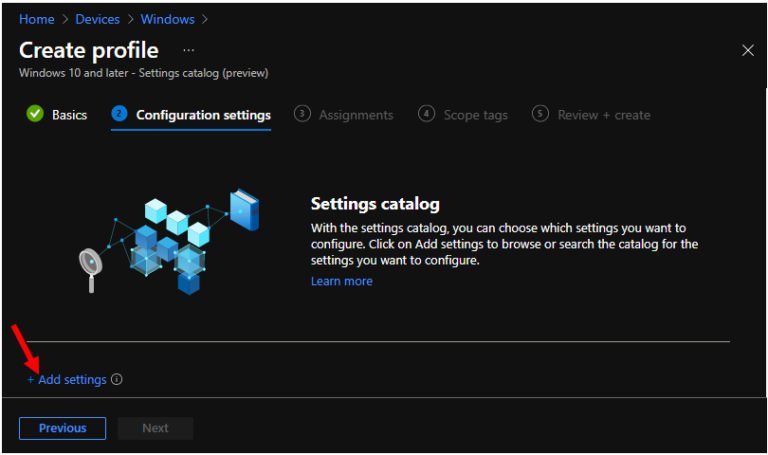
In Configuration settings, click Add settings to browse or search the catalog for the settings you want to configure.
On the Settings Picker windows, Select Device Lock to see all the settings in this category. Select the below settings, Max Inactivity Time Device Lock.
After adding your settings, click the cross mark at the right-hand corner to close the settings picker.
Note – In policy, use the search box to find specific settings. You can search by category or a keyword, such as Max Inactivity Time Device Lock/Inactivity Time It will display all the related settings available.
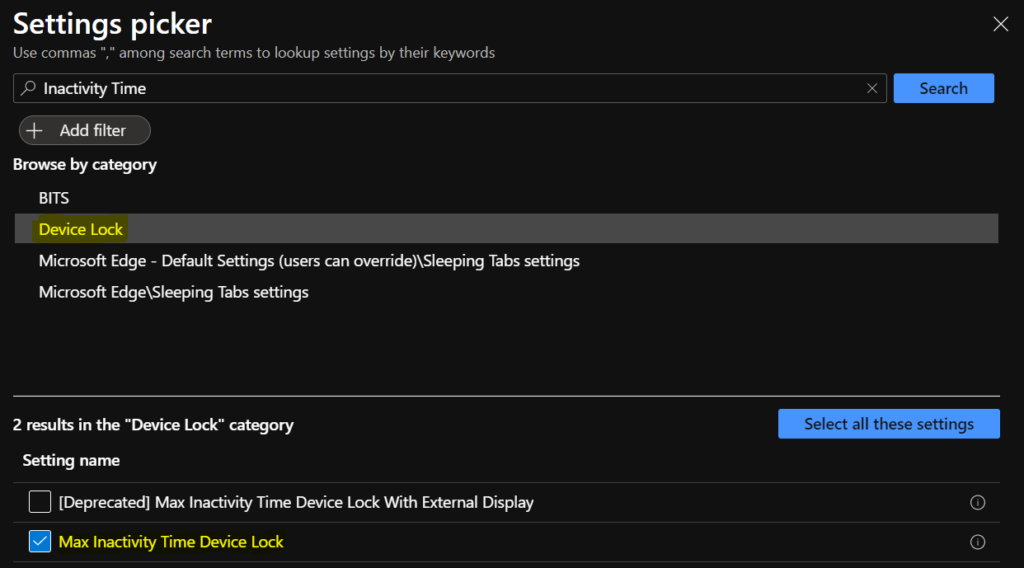
The setting is shown and configured with a default value Disabled. Set Device Password Enabled to Enabled and configure Max Inactivity Time Device Lock with value . And Click Next.
Specifies the maximum amount of time (in minutes) allowed after the device is idle that will cause the device to become PIN or password locked. Users can select any existing timeout value less than the specified maximum time in the Settings app.
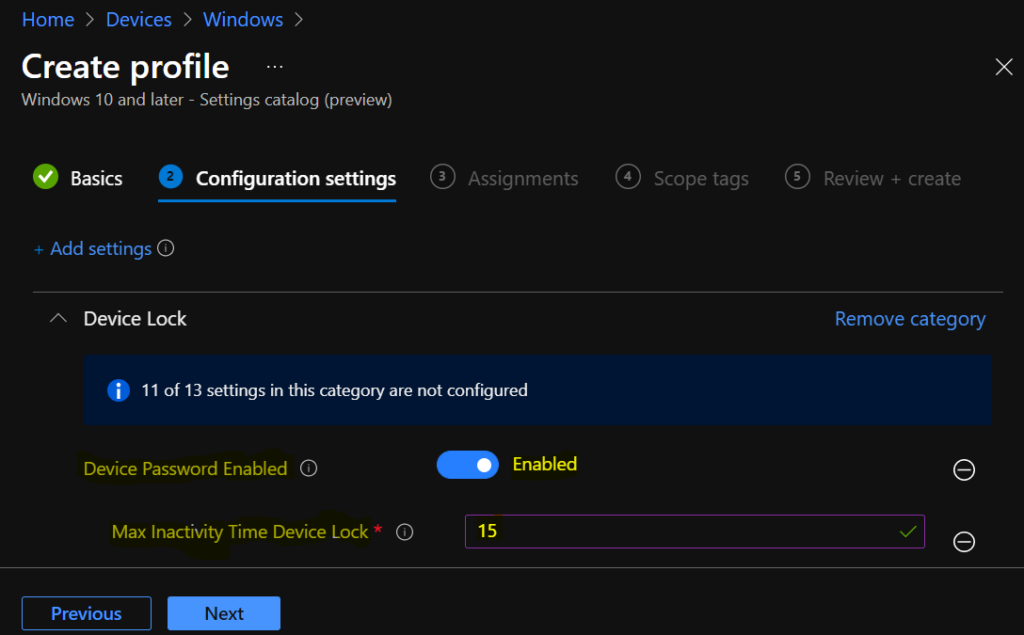
Under Assignments, In Included groups, click Add groups and then choose Select groups to include one or more groups. Click Next to continue.
In Scope tags, you can assign a tag to filter the profile to specific IT groups. Add scope tags (if required) and click Next.
In Review + create, review your settings. When you select Create, your changes are saved, and the profile is assigned.
A notification will appear automatically in the top right-hand corner with a message. Here you can see that Policy “Automatic Lock for Inactive Windows Device” created successfully. The policy is also shown in the Configuration profiles list.
Your groups will receive your profile settings when the devices check-in with the Intune service. Once the policy applies to the devices, you may required to log out and back in before the policy takes effect.
Reporting – Configure Automatic Lock for Inactive Windows Device
You can check Intune settings catalog profile report from Intune Portal, which provides an overall view of device configuration policies deployment status.
To monitor the policy assignment, from the list of Configuration Profiles, select the policy, and here you can check the device and user check-in status. If you click View Report, additional details are displayed.
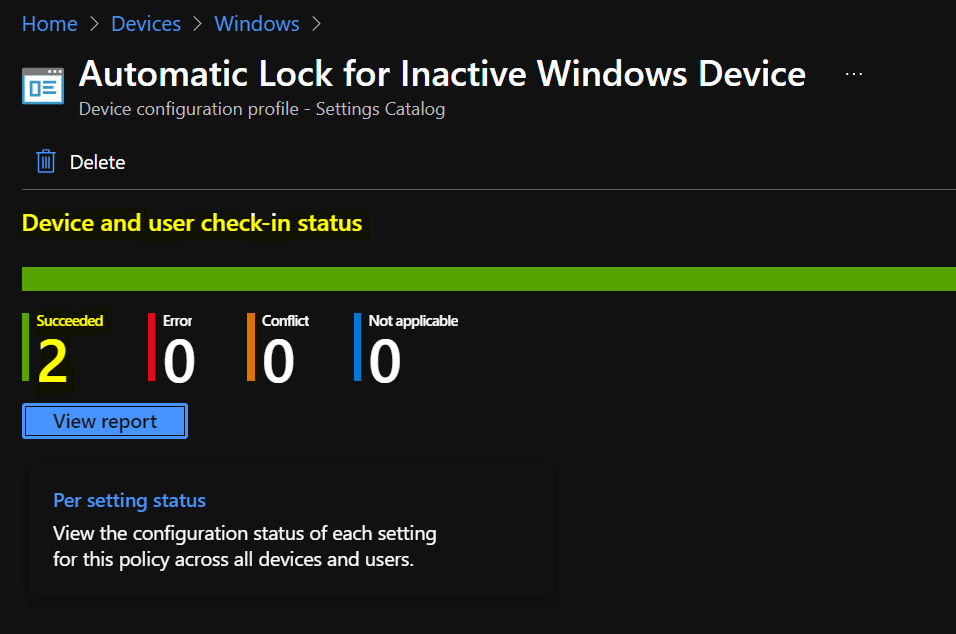
Intune MDM Event Log
The Intune event ID indicates a string policy is applied on the Windows 10 or 11 devices. You can also see the exact value of the policy being applied on those devices.
In the target device, You can check the Event log path to confirm – Applications and Services Logs – Microsoft – Windows – Devicemanagement-Enterprise-Diagnostics-Provider – Admin.
you can look at the Event ID 813 generated for the configured policies for managing apps, Here are the highlights from the Event logs.
MDM PolicyManager: Set policy int, Policy: (MaxInactivityTimeDeviceLock), Area: (DeviceLock), EnrollmentID requesting merge: (78BF73E9-4EBB-4575-9EF5-21B30DB3FD4E), Current User: (Device), Int: (0xF), Enrollment Type: (0x6), Scope: (0x0).
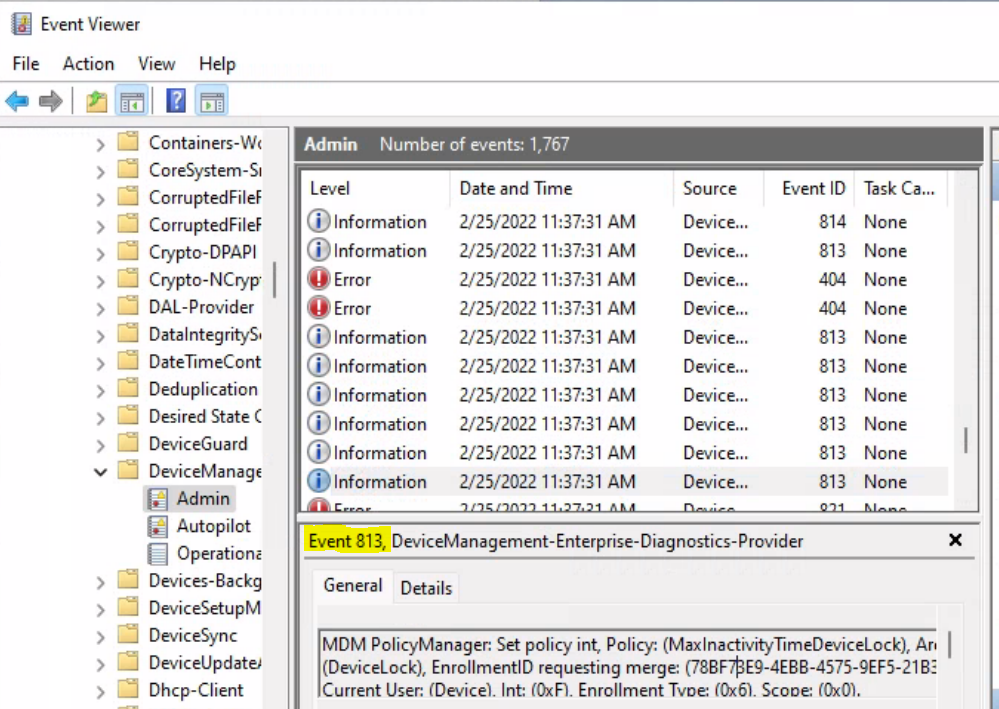
Validate Registry
Here you can validate whether the registry values are changed or not. You can see the registry entries related to the Device Lock Inactivity Time in the following registry path –
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\current\device\DeviceLock MaxInactivityTImeDeviceLock (Data should be visible as the value you defined in the policy)

Hello,
I’ve been trying this by settings 60 minutes, the value is correctly reflected in the registry, but the client keeps locking after 15 minutes. No conflicts about the same profile. What else could override this setting?
Some quick thoughts – Group Policy if Hybrid Joined device? Power Policies?
For Info, It seems like the setting under “Endpoint protection” , “Local device security options” and “Minutes of lock screen inactivity until screen saver activates” can override the setting displayed in your article.
FYI if you assign this to a device group you may see an extra reboot during Autopilot (between Device and User ESP) which requires the user to sign in again.
Was tearing my hair out until I found this – moving to user assignment, or using a different policy (screensaver) should resolve this.
Do machnes have to be windows ent and not pro to allow configuration policys? I’ve a machine that it works with which is windows 10 ent but dosen’t work for any of our win 10 pro machines.
This feature is available for Pro and Ent. Not for HOME versio https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-localpoliciessecurityoptions#localpoliciessecurityoptions-interactivelogon-machineinactivitylimit
I have followed this plan to the letter but the screen does not lock on the test endpoint. Any suggestions to find what the blocker is…. freshly formatted Windows Surface Laptop 4 with Windows 11 Pro. I see the settings I created on the endpoint but the screen is not locking as I expected.
It seems Max Inactivity Time Device Lock With External Display has been Deprecated. What would be the new setting?
Wondering the same. Is there a new setting for this?
Hi
I did all the steps i can see the regkey setu but still i get lock after 5min any idea?
Same here, still no proper way to lock the screen after x minutes of idle time. Embarassing, Microsoft! 🙁
This does not work. Gives black screen while enrolling and reboots only to ask for credentials twice.
Microsoft has a way of overcomplicating everything. GPO using local Windows server / AD worked great and was intuitive. InTune is a f’ing nightmare to configure.
Thanks for this post Anoop, very helpful. Grateful for you sharing as always!
To note that Lock Screen Settings conflict with Screensaver settings. Run RSOP to see if any GPO settings on the device are conflicting.
We’re having an issue during testing on a Windows 10 22H2 Enterprise device with E5 license where the Lock Screen isn’t working as expected. For us, it’s currently locking the screen after 10 minutes when I set it to 1 minute for testing. This 10 minutes seems to be forced by a Screen saver timeout GPO setting. I found an old article that mentioned a similar setting in Group Policy which said the ‘screensaver had to be active’ for this to work but that might not be applicable.
Settings that might have some affect on this setting I would guess are:
Screensaver timeout
Screensaver settings
Power Settings
“Endpoint protection” , “Local device security options” and “Minutes of lock screen inactivity until screen saver activates
Solution
I found that a GPO was applying a screensaver settings that was configured for 10 minutes. This won the conflict. Once I removed this GPO setting the Lock Screen would trigger at the MaxInactivityTimeDeviceLock I set of 1 minute. If you open SETTINGS > PERSONALIZATION > LOCK SCREEN . SCREEN SAVER SETTINGS > Then check what the WAIT time is set to. For me, this was at 10 minutes, once I removed the GPO setting this was set to 1 minute
Quick question, is it a separate password or does it lock the screen and ask the user to enter their azure ad password?
Where is this?
“Endpoint protection” , “Local device security options” and “Minutes of lock screen inactivity until screen saver activates
from SCCM, 365defender? or?
In the Microsoft Intune admin center from the Home Screen, browse to and select:
Endpoint security>Security Baselines>Security Baseline for Windows 10 and later>”Your Profile Name”>Properties>Configuration settings – Expand Settings, then expand Local Policies Security Options.
This is where the “Minutes of lock screen inactivity until screen saver activates” is located. Chhose edit if you need to change this or any of the other settings and then click save.