In this post, let’s see how to Create Intune Compliance Policy for Windows 365 Cloud PC. We will see a quick overview of creating an Intune compliance policy for Windows 10 or Windows 11 devices. Also, we shall discuss the options of creating a custom Intune compliance policy.
How to Setup Intune Compliance Policy for Windows devices | Microsoft Endpoint Manager | MEM Powered? It’s important to set up Azure AD Conditional Acces policy and Compliance policy to secure Windows 365 Cloud PCs and Azure Virtual Desktop (AVD – single session persistent VMs) similar to physical devices.
Compliance policy configuration is an important design decision while managing Windows 10 or Windows 11 physical or virtual devices with MEM Intune. Intune compliance policies are the first step of the protection before providing access to corporate applications, along with Conditional Access policies.
Intune Compliance Policy for Windows 10 or Windows 11 is to help to protect company data; the organization needs to make sure that the devices used to access company apps and data comply with certain rules. The default compliance policy rules include password/PIN, Patch Level, TPM, Encryption, Secure boot checks, etc.
The user can access the company data securely only from Windows 365 Cloud PC (or any other device for that matter) If the devices are compliant with the rules specified in the policy.
- Managing Windows Bitlocker Compliance Policy Using Intune | MS Graph | Grace Period
- Bitlocker Unlocked With Joy – Behind The Scenes Windows 10 – Part 1
- Easiest Method to Enable MFA for Admins using Azure AD Conditional Access
NOTE! – Microsoft recently released an option to create a Custom Compliance policy for Windows devices with PowerShell script and JSON option. But this is only available for Azure AD Joined devices while writing this post.
Create Intune Compliance Policy
You can start creating compliance policies from two places in the MEM admin center portal. The Devices Node and from Endpoint Security node. This post will show how to create Intune compliance policies from the Endpoint Security node.
- Open endpoint.microsoft.com with appropriate Intune permission to create compliance policies.
- Navigate via Endpoint Security – Compliance Policies.
- Click on + Create Policy button to start the Intune compliance policy creation process.
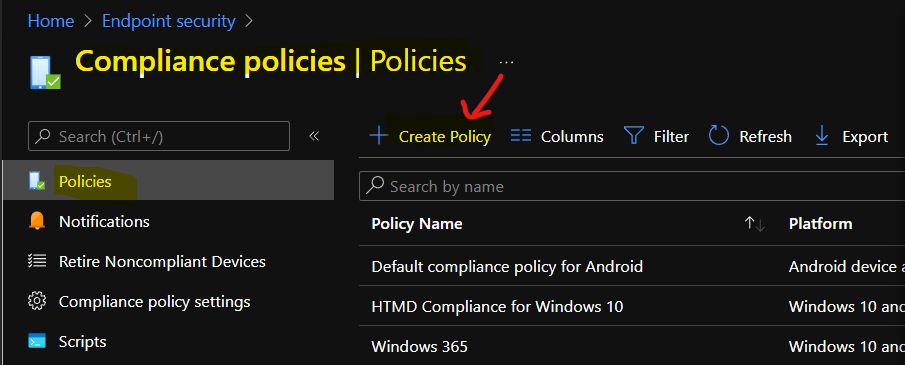
Make sure to select Windows 10 or Later as the platform. The profile type should be Windows 10/11 compliance policy. You will need to click on the Next button to continue.
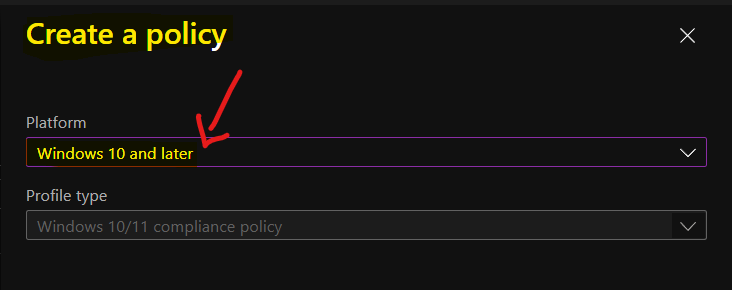
Enter the name and description of the compliance policy on this page. I have used the name Windows 365 Cloud PC Compliance Policy.
NOTE! – This compliance policy will make sure that all the Windows 365 Cloud PC devices are compliant before they can access the corporate resources like email, SharePoint, Teams, etc.
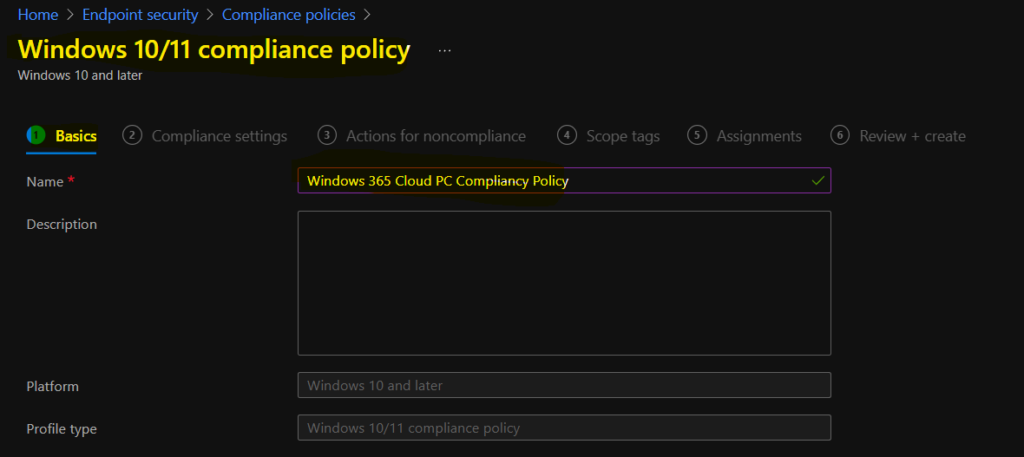
Intune Compliance Policy – Device Health Checks
Now, let’s decide the policies required for your organization as per the security standards from the Device Health check category. I tested Require Secure Boot to be enabled on the device, and it didn’t work for the Windows 365 Cloud PC, which is Windows 11 upgrade capable as per Endpoint Analytics.
The following options are available under the Device Health category of MEM Intune compliance policies.
- Device Health
- Windows Health Attestation Service evaluation rules Require BitLocker
- Require
- Not configured
- Require Secure Boot to be enabled on the device
- Require
- Not configured
- Require code integrity
- Windows Health Attestation Service evaluation rules Require BitLocker
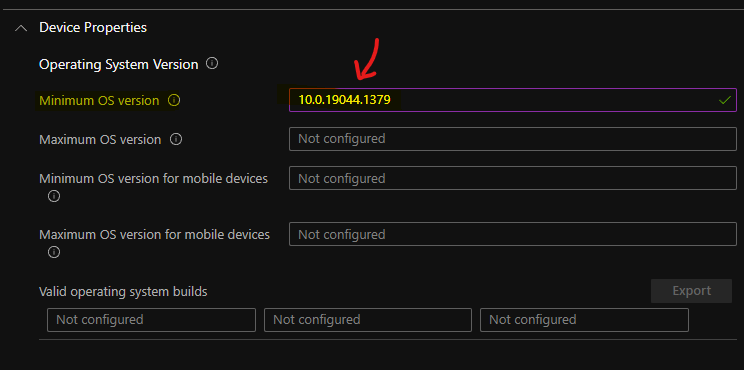
Operating System Version Intune Compliance Policy Rules
Let’s check Operating System Version Intune Compliance Policy Rules. The following are the compliance policy rules that you can set for Cloud PCs to make sure the monthly patches are installed and users restarted their devices, etc.
You will need to use Windows 10 or Windows 11 version or build number or revision number to achieve the patch compliance of Cloud PCs. You can see the details of the operating system version numbers defined as major.minor.build.revision from the below posts.
- Windows 11 Version Numbers Build Numbers Major Minor Build Rev
- Windows 10 Version Numbers Build Numbers Major Minor Build Rev
The following are Intune compliance rules available for Operating System versions that can help you control patch level compliance of Windows 365 Cloud PCs.
- Operating System Version
- Minimum OS version
- Maximum OS version
- Minimum OS version for mobile devices
- Maximum OS version for mobile devices
- The valid operating system builds
- Configuration Manager Compliance
- Require device compliance from Configuration Manager
I have entered 10.0.19043.1379 as the minimum OS version, and this means if the November CU update is not installed on 21H1 devices, those devices will be reported as non-compliant devices.
System Security Related Compliance Policy Rules for Windows Devices
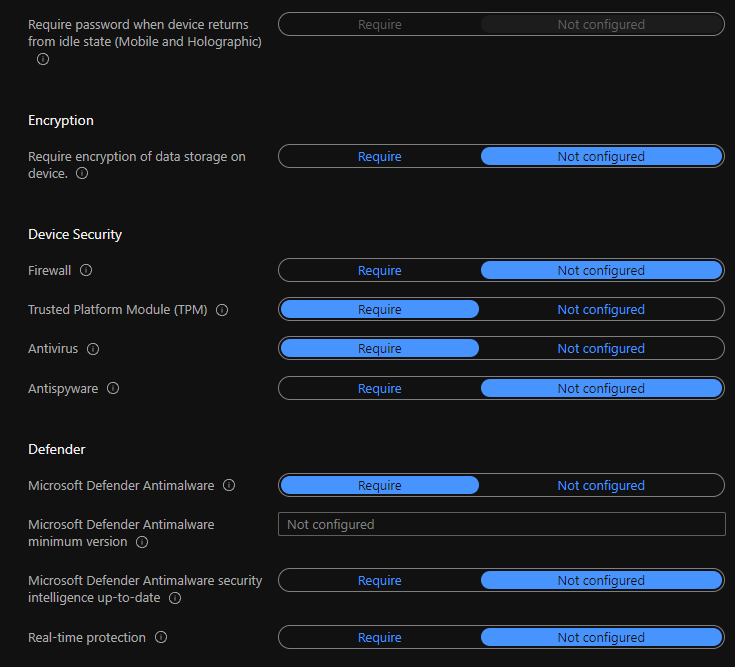
Let’s check the System Security Related Compliance Policy Rules for Windows Devices. You can specify the compliance policies for password settings, the complexity of the password, Encryption policies for data storage on devices, etc.
NOTE! – These password policies are important when you move Windows 365 Cloud PC to Azure AD join scenario soon. I’m assuming that the password policies are managed through GPOs in Hybrid Azure AD join scenarios for most of you.
Other system security policy compliance rules such as Firewall, TPM, Antivirus, and Antispyware are also available as out of box options. The defender policies are the other one. All these system security policy rules will help you ensure the device is fully secured from all the threads.
Also, if the Windows device does not meet any of the required rules defined in the compliance policy, then that device won’t access company resources until they fix those issues.
For example, if the device is missing antivirus software, then the compliance policy and the Azure AD conditional access policy will block the device from accessing company resources.
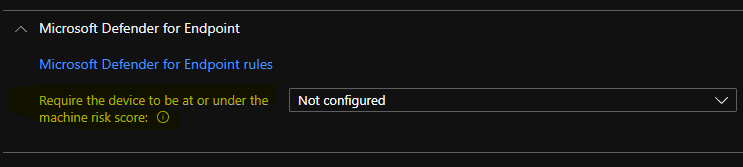
Device Risk Score Compliance Policy Rule
One option is to check the Device Risk Score using IntuneCompliance Policy Rule and provide access to corporate resources.
Select the maximum allowed machine risk score for devices evaluated by Microsoft Defender for Endpoint if the Devices that exceed this score get marked as noncompliant.
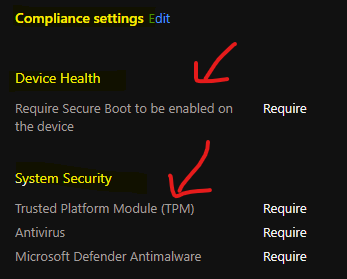
Sample Intune Compliance Rules Set for Windows 365 Cloud PC Testing
I have tested Windows 365 Cloud PCs with a set of sample Intune Compliance policy rules as listed down in the below list. You will need to change the set of rules as per your organization’s requirements and security standards.
NOTE! – This is not the recommended rules from my side but just a sample to let you know how this works.
Device Health
Require Secure Boot to be enabled on the device – Require
System Security
Trusted Platform Module (TPM) – Require
Antivirus – Require
Microsoft Defender Antimalware – Require
How to Enforcement Intune compliance policy Rules Quickly
This section of the compliance policy settings for Windows devices and Cloud PC + Azure Virtual Desktop persistent single session devices. The default value I put in is 1 day, but you can change it to 4 hours or 5 days as per your requirement.
The following blog will help you make it more flexible using MS Graph and PS script. We already have a blog post from Mark Thomas to guide you through quickly enforcing the Intune compliance policy rules on Windows Devices, including Cloud PCs and AVDs.
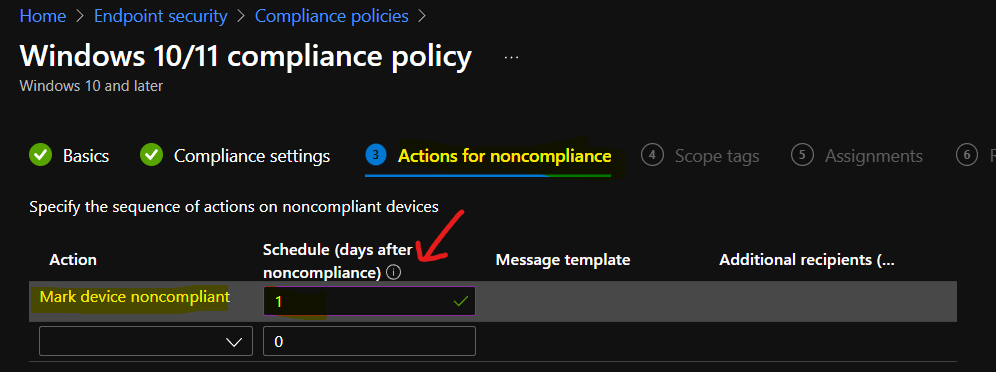
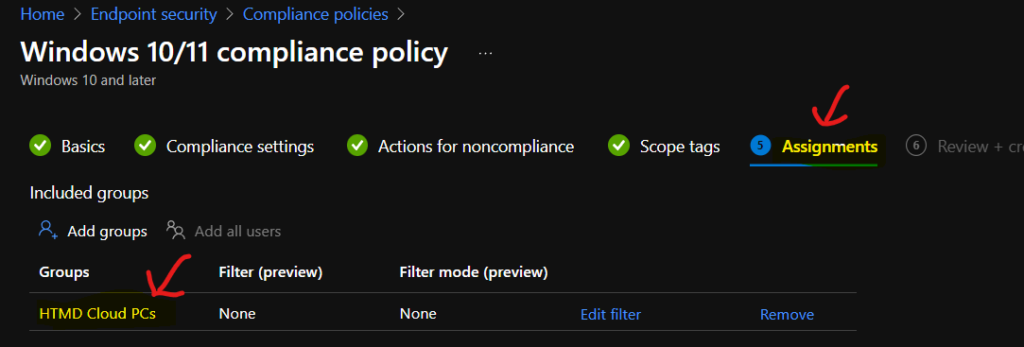
Compliance Policy to Cloud PC Device Group
The deployment of compliance policy should go to an Azure AD dynamic Device group where all the Cloud PCs or AVD devices are present. I don’t think this compliance policy should be deployed to the user group.
You can select the appropriate scope tags to support proper Intune RBAC scenarios. You can now click on CREATE button to complete the Intune Compliance policy rules for Windows 365 Cloud PCs.
Conclusion
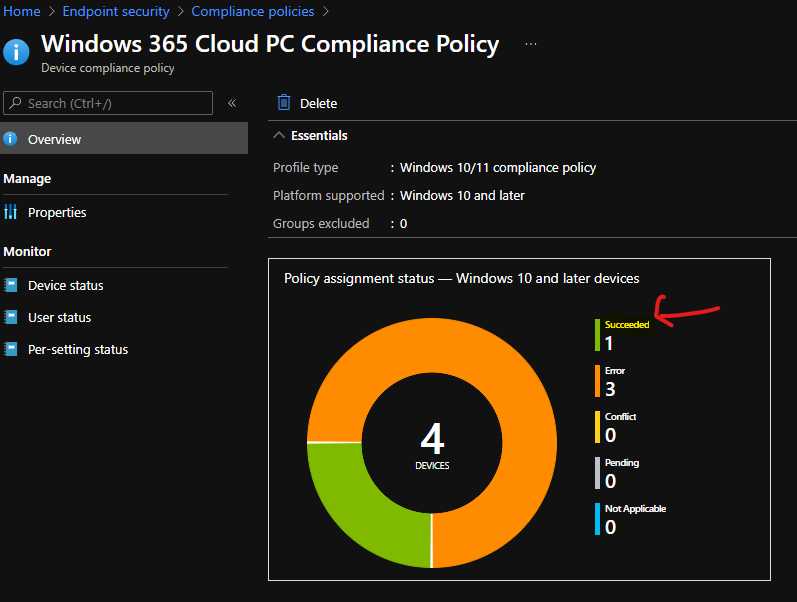
Well, it’s a bit tricky to conclude anything without much more testing. The design decisions related to Windows 365 Cloud PC or AVD Intune compliance policies should differ from physical devices. Some of the security features can be overkill for Cloud PCs and AVD session hosts.
The secure boot and TPM types of compliance rules need more testing to understand whether it is something you want to include in the Cloud PC or AVD compliance rules or not. I have tested these two rules with 4 Cloud PCs, and the results are not very stable, I would say.
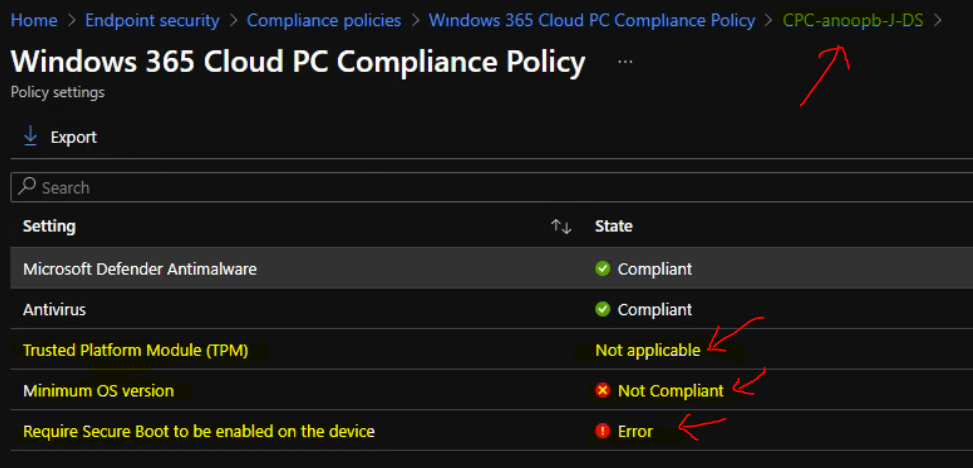
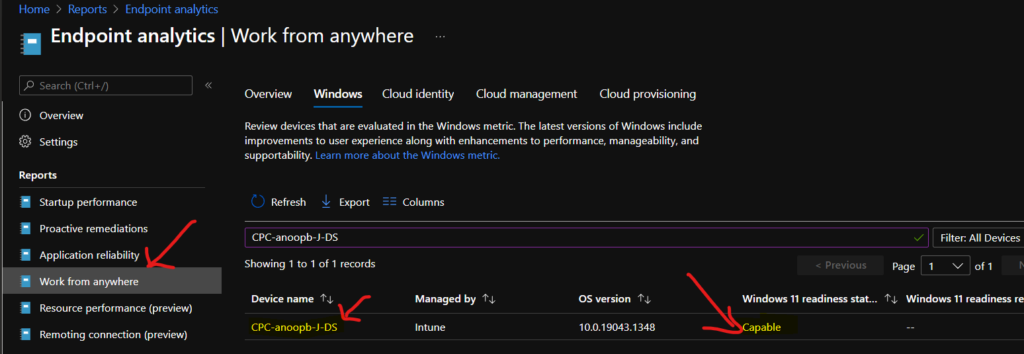
I got an error when testing CPC-anoopb-J-DS VM, which is Windows 11 upgrade capable (as per Endpoint Analytics reports), but I can check the compliance rule called Require Secure Boot to be enabled on the device. This is mainly because of virtual machine level or hypervisor layer limitations.
Error 0x87d10194 – Error Details SyncML(404): The requested target was not found.
Also, you can see the report below where the TPM check is also not applicable for a Windows 11 capable VM. I might need to dive deep into this to understand more about these errors and the limitations of compliance rules for virtual desktop scenarios.
TPM Check – Not applicable
There is another status that concerns me is the Minimum OS version. This gives a not compliant error. This is also accurate since I have provided the minimum OS version as 10.0.19043.1379, but the actual OS version of Cloud PC is 10.0.19043.1348.
Minimum OS Version – Not Compliant
TIP: Cloud PC Monitoring Health Performance Using Endpoint Analytics Intune. The above Cloud PC can Windows 11 upgrade with TPM chipset and all. However, the Compliance rule thinks that it can’t check the TPM of this Cloud PC.

Is there anyway to automate or script the minimum os build portion? That way you don’t have to go in there every month and change the value. Seems like there’s potential to forget resulting in devices being non compliant.