Microsoft has announced a workaround for Office and Windows HTML Remote Code Execution Zero-Day Vulnerability along with other 5 Zero-days. The impact is for the customers who use Microsoft Defender for Office are protected from attachments that attempt to exploit this vulnerability.
Microsoft is investigating reports of a series of remote code execution vulnerabilities impacting Windows and Office products. Microsoft is aware of targeted attacks that attempt to exploit these vulnerabilities by using specially-crafted Microsoft Office documents.
An attacker could create a specially crafted Microsoft Office document that enables them to perform remote code execution in the context of the victim. However, an attacker would have to convince the victim to open the malicious file. This CVE vulnerability is related to Storm-0978 attacks, revealing financial and espionage motives topic.
We will see the mitigation options in the following sections of this post. Previously also had a zero-day vulnerability for the office – Zero Day Security Vulnerability for Outlook. Microsoft also released Windows 10 and Windows 11 Cumulative Update patches for the month of July 2023.

CIS Benchmark to Mitigate Actively Exploited RCE Vuln with CIS Benchmarks
As per the CIS benchmark communication, if you have the following CIS benchmark policies in place then you don’t have to worry about Office and Windows HTML Remote Code Execution Zero Day Vulnerability CVE-2023-36884.
CIS Benchmark research shows that doing so mitigates CVE-2023-36884. Microsoft’s recommendations in the security advisory above align with what’s already present in our CIS Benchmarks and CIS Hardened Images.
Take the CIS Microsoft Windows 10 Benchmark as an example. The following security recommendations mitigate the vulnerabilities:
- 18.10.43.6.1.1 (L1) Ensure ‘Configure Attack Surface Reduction rules‘ is set to ‘Enabled’
- 18.10.43.6.1.2 (L1) Ensure ‘Configure Attack Surface Reduction rules: Set the state for each ASR rule’ is configured
A Quick Video Summary – Zero Day Office Vulnerability CVE-2023-36884 without a FIX until now
Zero Day Office Vulnerability CVE-2023-36884 summary video is available now. An attacker could create a specially crafted Microsoft Office document that enables them to perform remote code execution in the context of the victim. All you want to know about this Vulnerability. Impacted Office Versions with CVE-2023-36884 Vulnerability.
Impacted Office Versions with CVE-2023-36884 Vulnerability
Let’s check what are the impacted Office App versions with CVE-2023-36884 Vulnerability. Office and Windows HTML Remote Code Execution Zero-Day Vulnerability impact the following versions of Microsoft 365 Apps. If I’m running Office365 Semi-Annual Channel Extended, are we affected by this vulnerability?
- Office365 Semi-Annual Channel Extended (specifically versions 2208 and 2202) is affected.
- Microsoft 365 Apps Semi-Annual Channel Extended (specifically versions 2208 and 2202) are affected.
However, Microsoft 365 Semi-Annual Channel version 2302 (and all later versions) is protected from this vulnerability.
Windows 11 July 2023 Patches
More Details on Windows 11 July LCU patch Windows 11 KB5028182 KB5028185 July Patches.
- 2023-07 Cumulative Update for Windows 11 (KB5028182)
- 2023-07 Cumulative Update for Windows 11 Version 22H2 (KB5028185)
Windows 10 July 2023 Patches
Microsoft has already released a fix/mitigation for Office and Windows HTML Remote Code Execution Zero-Day Vulnerability CVE-2023-36884. More details Windows 10 KB5028166 July Patch Tuesday 2023.
1 – 2023-07 Cumulative Update for Windows 10 Version 1507 for x64-based Systems (KB5028186) Windows 10 LTSB.
2 – 2023-07 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB5028169) Windows 10 LTSB, Windows 10.
2023-07 Cumulative Update for Windows 10 Version 1809 for x64-based Systems (KB5028168) Windows 10 LTSB Security Updates.
2023-07 Cumulative Update for Windows 10 Version 21H2 for x64-based Systems (KB5028166) Windows 10 Windows 10, version 1903 and later.
Zero-Day Vulnerability Table
As per the report from the Microsoft Security Response Center (MSRC), there is 1 zero-day vulnerability CVE-2023-36884 which is publically disclosed and Exploited. This impacts Windows 10, Windows 11, etc. Also, Office versions as documented by Microsoft.
As per Microsoft, the campaign involved the abuse of CVE-2023-36884, which included a remote code execution vulnerability exploited before disclosure to Microsoft via Word documents, using lures related to the Ukrainian World Congress.
- CVE-2023-36884 Base score metrics: 8.3 / Temporal score metrics: 8.1
| Last Updated | CVE Number | CVE Title | Publicly Disclosed | Exploitability Assessment | Exploited |
| Jul 11, 2023 | CVE-2023-35311 | Microsoft Outlook Security Feature Bypass Vulnerability | No | Exploitation Detected | Yes |
| Jul 11, 2023 | ADV230001 | Guidance on Microsoft Signed Drivers Being Used Maliciously | No | Exploitation Detected | Yes |
| Jul 11, 2023 | CVE-2023-36884 | Office and Windows HTML Remote Code Execution Vulnerability | Yes | Exploitation Detected | Yes |
| Jul 11, 2023 | CVE-2023-36874 | Windows Error Reporting Service Elevation of Privilege Vulnerability | No | Exploitation Detected | Yes |
| Jul 11, 2023 | CVE-2023-32049 | Windows SmartScreen Security Feature Bypass Vulnerability | No | Exploitation Detected | Yes |
| Jul 11, 2023 | CVE-2023-32046 | Windows MSHTML Platform Elevation of Privilege Vulnerability | No | Exploitation Detected | Yes |
Mitigation or FIX Office and Windows HTML Remote Code Execution Zero-Day Vulnerability
Customers who use Microsoft Defender for Office are protected from attachments that attempt to exploit this vulnerability. Let’s check for FIX Office and Windows HTML Remote Code Execution Zero-Day Vulnerability.
In current attack chains, the use of the Block all Office applications from creating child processes Attack Surface Reduction Rule will prevent the vulnerability from being exploited.
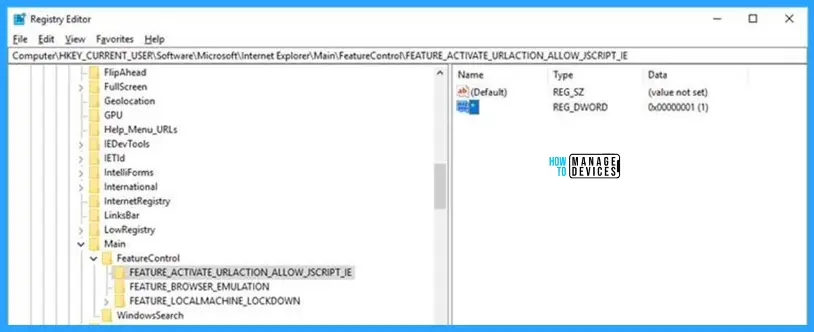
Organizations that cannot take advantage of these protections can set the FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION registry key to avoid exploitation. Please note that while these registry settings would mitigate exploitation of this issue, they could affect regular functionality for certain use cases related to these applications.
Add the following application names to this registry key as values of type REG_DWORD with data 1.:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION
Excel.exe
Graph.exe
MSAccess.exe
MSPub.exe
PowerPoint.exe
Visio.exe
WinProj.exe
WinWord.exe
Wordpad.exe
Alternatively, customers could enable the Feature Control Key for their applications. Please see Restrict JScript at a Process Level for more information.
Author
About Author – Vidya is a computer enthusiast. She is here to share quick tips and tricks with Windows 11 or Windows 10 users. She is also keen to find solutions to day-to-day tech problems and write about them.

Powerpnt.exe not PowerPoint.exe