Let’s learn how to Block Internet Macros for Office Applications using Intune Settings Catalog or Group Policy. Microsoft made changes in the default behavior of Internet Macros for Office Applications. In February 2022, Microsoft announced that they block internet macros by default for office applications.
They reverted the changes on the 8th of July 2022, and the default behavior was changed back to allow internet macros. There would be some scenarios where organizations want to block the internet macros for Microsoft 365 apps.
You can use Intune Settings Catalog or Group Policy to block the internet macro download for Microsoft office applications on Windows 11 or Windows 10 devices. This will block macros from running in Office files from the Internet.
Update 22nd July 2022 -> Microsoft is again planning to roll out the Macro settings disable change as the default option starting from 27th July 2022.
- Collect Intune Logs from MEM Portal Diagnostic Data
- Intune Logs Event IDs IME Logs Details for Windows Client Side Troubleshooting
- Intune Audit Logs Track Who Created Updated Device Compliance Policy
Block Internet Macros for Office Applications
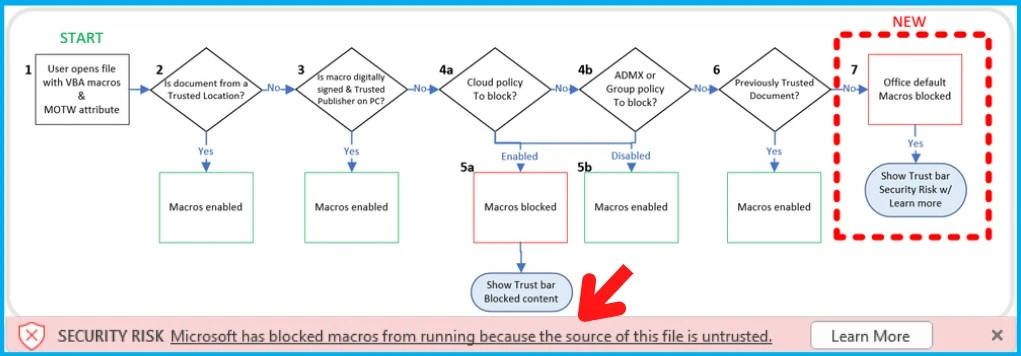
Let’s check end-user experience and workflow when Block Internet Macros for Office Applications policy is implemented. The Office app Trust bar shows the following error when blocking internet macros via Cloud policy or via default settings implemented for all the users.
When a user tries to run the macro on a Windows device, it will give the following error message because the macro source is untrusted. The new box (#7) shown in the diagram below is not the default behavior anymore.
⚠️SECURITY RISK Microsoft has blocked macros from running because the source of this file is untrusted.
- This post will cover scenario 5a – Micros blocked using policy.
Microsoft confirmed in the Techcommunity article that “We’re resuming the rollout of this change in the Current Channel. Based on our review of customer feedback, we’ve made updates to both our end user and our IT admin documentation to make clearer what options you have for different scenarios.”
Confirm the Macro Policy is Set or not
You can use the following method to confirm whether the Office 365 macro policies set on Windows devices or not. The policy was set to Disabled or Not Configured, then the app would check the settings under:
- File > Options >
- Trust Center > Trust Center Settings…
- Macro Settings.
The default is set to “Disable all macros with notification,” which allows users to enable content in the Trust Bar.
Create Intune Cloud Policy to Block Macros from Internet
Let’s create an Intune Cloud Policy to Block Macros from the Internet. You can use Intune cloud policy or Group Policy ADMX template to block the macros running from non-trusted locations such as the internet.
The following steps help you turn on macro blocking for office applications.
- Sign in to the Endpoint Manager Intune portal
- Select Devices > Windows > Configuration profiles > Create profile
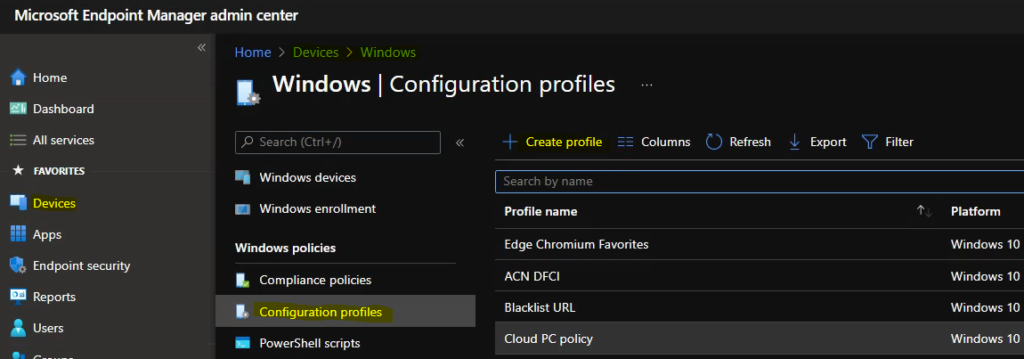
In Create Profile, Select Platform, Windows 10, and later and Profile, Select Profile Type as Settings catalog.
- Click on Create button.
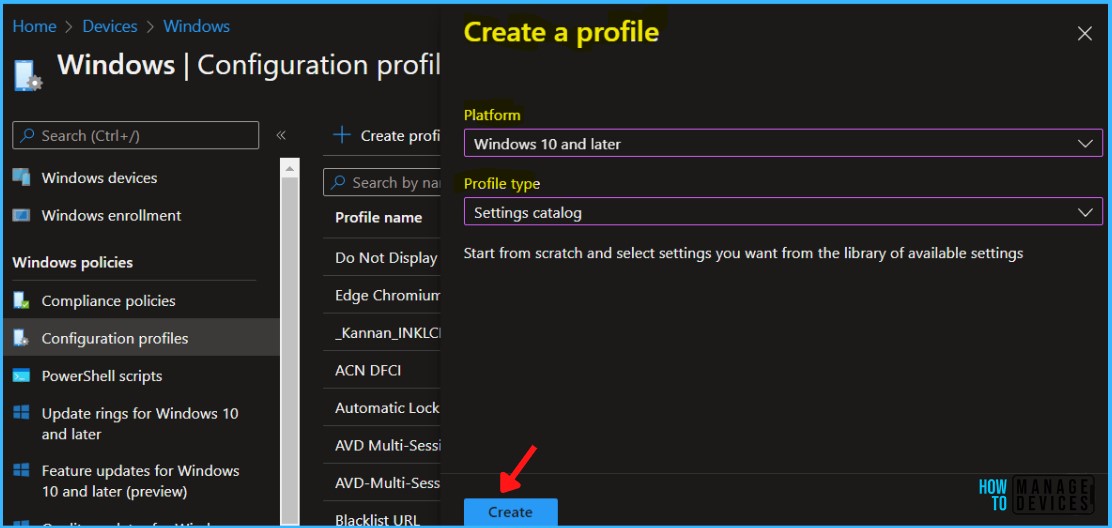
On the Basics tab, enter a descriptive Name, such as Block Internet Macros for Office Applications.
- Optionally, enter a Description for the policy – Block macros from running in Office files from the Internet.
- Select Next to continue.
In Configuration settings, click Add settings to browse or search the catalog for the settings you want to configure. In this case, to block internet macros from running on office apps.
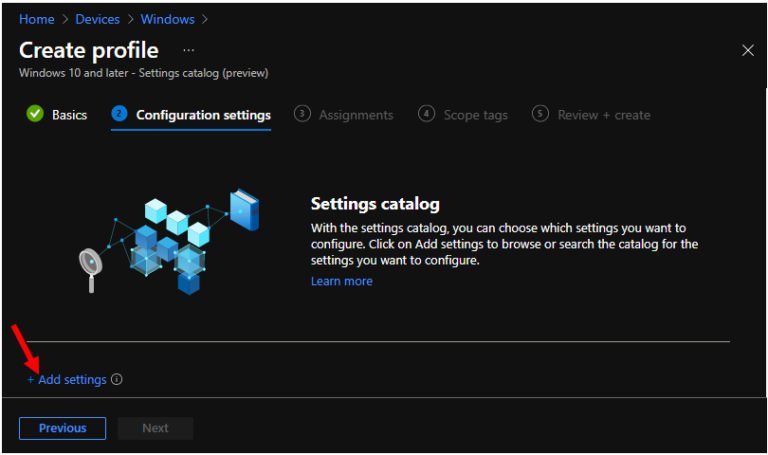
On the Settings Picker windows, use the search box and type macros from running in Office files from the Internet, and click Search.
- Block macros from running in Office files from the Internet (User)
Use commas “,” among search terms to lookup settings by their keywords “macros from running in Office files from the Internet.”. The Browse by category – 1 results in the “Trust Center” subcategory – Setting name.
This policy setting allows you to block macros from running in Office files from the Internet. If you enable this policy setting, macros are blocked from running, even if “Enable all macros” is selected in the Macro Settings section of the Trust Center.
The disable macro policy is available for 5 office applications such as Access, Excel, PowerPoint, Visio, and Word.
You can use the settings called “Block macros from running in Office files from the Internet (User)” to change the default behavior of the Office application towards enabling the Macros received from the internet.
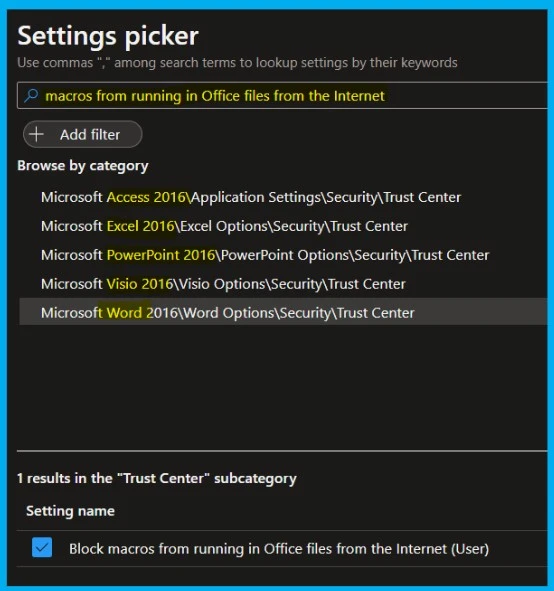
- Microsoft Access 2016 – Application Settings > Security > Trust Center – 11 of 12 settings in this subcategory are not configured.
- Microsoft Excel 2016 – Excel Options > Security > Trust Center – 15 of 16 settings in this subcategory are not configured.
- Microsoft PowerPoint 2016 – PowerPoint Options > Security > Trust Center – 13 of 14 settings in this subcategory are not configured.
- Microsoft Visio 2016 – Visio Options > Security > Trust Center – 114 of 115 settings in this subcategory are not configured.
- Microsoft Word 2016 – Word Options > Security > Trust Center – 18 of 19 settings in this subcategory are not configured.
Also, instead of having the choice to “Enable Content,” users will receive a notification that macros are blocked from running. Macros will be allowed to run if the Office file is saved to a trusted location or was previously trusted by the user.
If you disable or don’t configure this policy setting, the settings configured in the Macro Settings section of the Trust Center determine whether macros run in Office files that come from the Internet.
- Use the slider (move to the right) to enable the block policy for running the macros from office files, as shown in the below screenshot.
- Follow the same steps for all 5 applications.
- Click on Next.
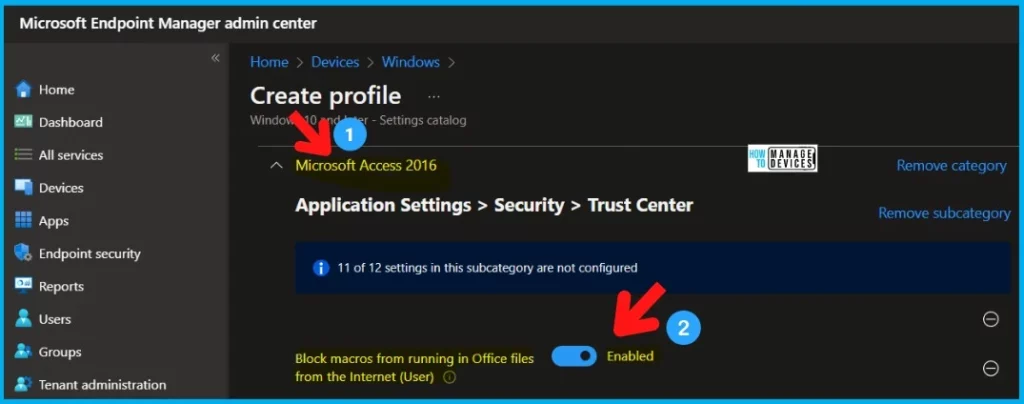
Under Assignments, In Included groups, click Add groups and then choose Select groups to include one or more groups.
- Click Next to continue.
On the Scope tags page, you can assign a security tag to filter the profile to specific IT groups. Add scope tags (if required).
- Click Next to go to the next page.
- In Review + create, review your settings.
- When you select Create, your changes are saved, and the profile is assigned.
Group Policy Settings to Block Internet Macros for Office Applications
Let’s check Group Policy Settings to Block Internet Macros for Office Applications. Office 365 or 2019 ADMX templates are not available as part of Windows 10, Windows 11, and Server 2022 default ADMX templates. You have to download the Office ADMX template and install it on the Domain Controller.
Read More -> How to Download and Install ADMX templates – Download Microsoft Edge ADMX Group Policy Templates
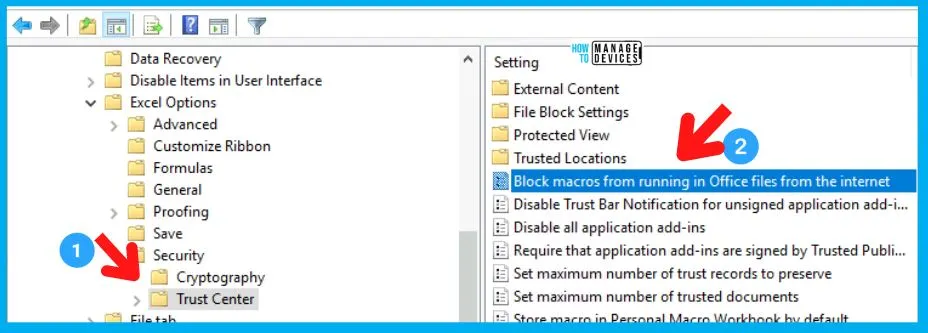
Once the ADMX template for Office is installed and configured, you would be able to see new ADMX folders for Office applications. The following table shows where each policy can be found:
- Group Policy Management Console under User Configuration\Policies\Administrative Templates:
| Application | Policy location |
|---|---|
| Access | Microsoft Access 2016\Application Settings\Security\Trust Center |
| Excel | Microsoft Excel 2016\Excel Options\Security\Trust Center |
| PowerPoint | Microsoft PowerPoint 2016\PowerPoint Options\Security\Trust Center |
| Visio | Microsoft Visio 2016\Visio Options\Security\Trust Center |
| Word | Microsoft Word 2016\Word Options\Security\Trust Center |
This policy setting allows you to block macros from running in Office files that come from the internet.
If you enable this policy setting, macros are blocked from running, even if "Enable all macros" is selected in the Macro Settings section of the Trust Center. Users will receive a notification that macros are blocked from running.
The exceptions when macros will be allowed to run are:
- The Office file is saved to a Trusted Location.
- The Office file was previously trusted by the user.
- Macros are digitally signed and the matching Trusted Publisher certificate is installed on the device.
If you disable this policy setting, the settings configured in the Macro Settings section of the Trust Center determine whether macros run in Office files that come from the internet.
If you don’t configure this policy setting, macros will be blocked from running. Users will receive a notification telling them of the security risks of macros from the internet along with a link to learn more.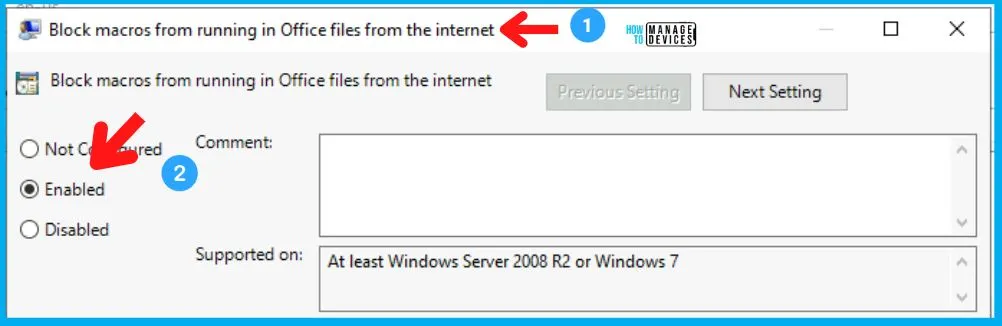
Disable Macro – Troubleshoot Intune Policy Deployment
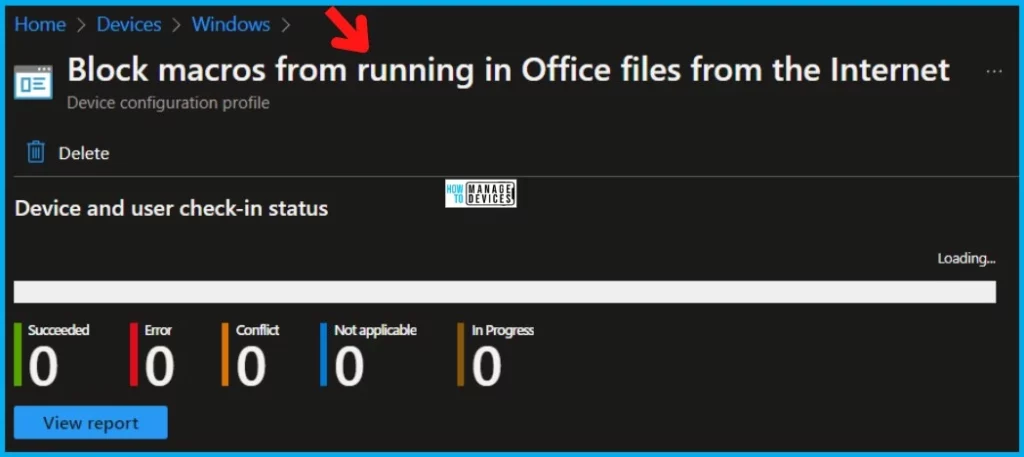
Let’s see how to Disable Macro – Troubleshoot Intune Policy Deployment. The first thing is to look at the Intune reports to understand the trend and whether the deployment is going well.
You can check Intune settings catalog profile report from Intune Portal, which provides an overall view of device configuration policies and deployment status. The next step is to look into the event logs and confirm whether the policy is applied or not.
Event Log path for Intune logs – > Applications and Services -> Microsoft->Windows->DeviceManagement-Enterprise-Diagnostics-Provider->Admin
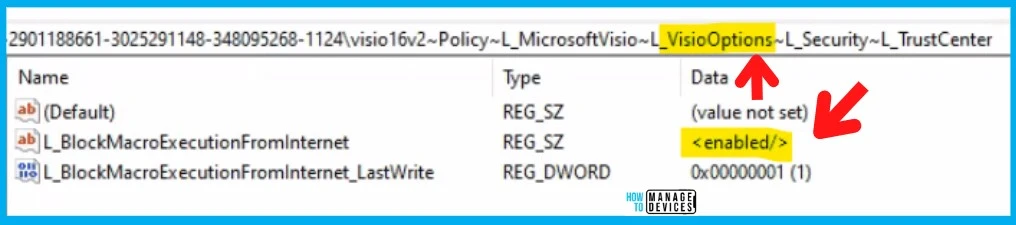
You can check for the event log ID 814 (policy is successfully applied) and confirm whether the policy string to block macro is in the event log L_BlockMacroExecutionFromInternet. This is a user-based policy; hence you would be able to see the Current User and user’s SID details.
MDM PolicyManager: Set policy string, Policy: (L_BlockMacroExecutionFromInternet), Area: (word16v2~Policy~L_MicrosoftOfficeWord~L_WordOptions~L_Security~L_TrustCenter), EnrollmentID requesting merge: (B4E48680-C0A3-44F3-8D0E-0691407CAAA4), Current User: (S-1-5-21-2901188661-3025291148-348095268-1124), String: (<enabled/>), Enrollment Type: (0x6), Scope: (0x1).MDM PolicyManager: Set policy string, Policy: (L_BlockMacroExecutionFromInternet), Area: (visio16v2~Policy~L_MicrosoftVisio~L_VisioOptions~L_Security~L_TrustCenter), EnrollmentID requesting merge: (B4E48680-C0A3-44F3-8D0E-0691407CAAA4), Current User: (S-1-5-21-2901188661-3025291148-348095268-1124), String: (<enabled/>), Enrollment Type: (0x6), Scope: (0x1).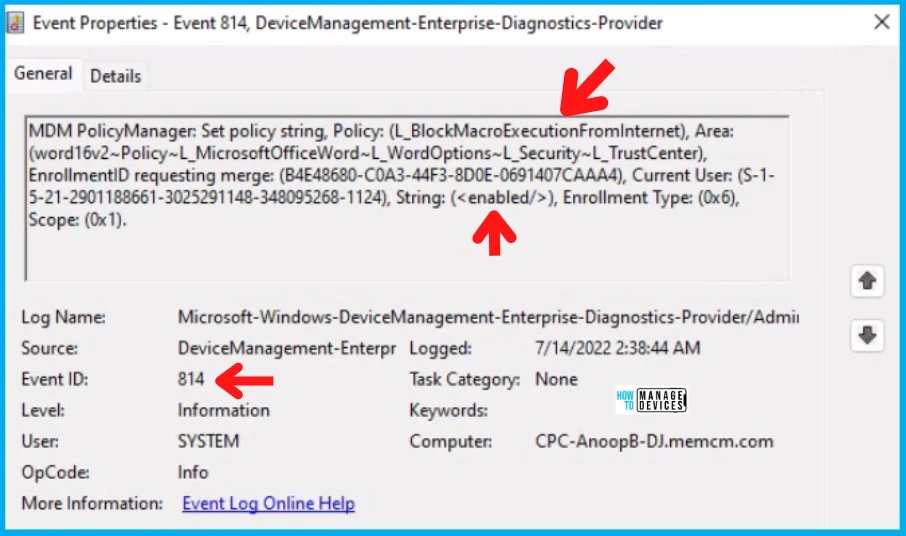
The registry is the next place you can check to confirm whether the registry entries are already created and applied or not.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\providers\B4E48680-C0A3-44F3-8D0E-0691407CAAA4\default\S-1-5-21-2901188661-3025291148-348095268-1124\visio16v2~Policy~L_MicrosoftVisio~L_VisioOptions~L_Security~L_TrustCenter
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\providers\B4E48680-C0A3-44F3-8D0E-0691407CAAA4\default\S-1-5-21-2901188661-3025291148-348095268-1124\visio16v2~Policy~L_MicrosoftVisio~L_VisioOptions~L_Security~L_TrustCenter]
"L_BlockMacroExecutionFromInternet"="<enabled/>"
"L_BlockMacroExecutionFromInternet_LastWrite"=dword:00000001
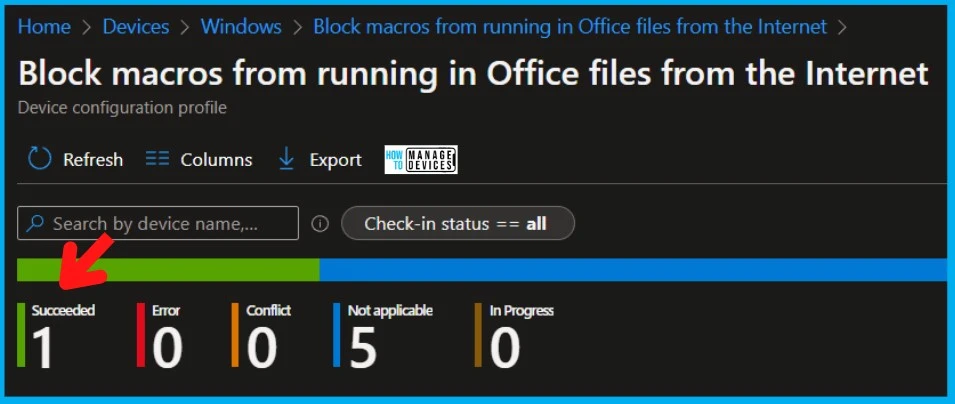
Results
The report reflects the successful deployment of the block internet Macros for Office application policy to Windows 11 devices.
Author
Anoop C Nair is Microsoft MVP! He is a Device Management Admin with more than 20 years of experience (calculation done in 2021) in IT. He is Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc.
