Microsoft Cloud LAPS Password management solution to securely randomize and back up the password of the local administrator account to Azure AD. The latest information on Intune and Azure AD policy configurations for Windows LAPS is explained in the following post. More details Windows LAPS Configurations From Azure AD and Intune.
IT pros have widely used the Local Administrator Password Solution (LAPS) for nearly a decade to secure Windows devices, aid in device recovery, and support helpdesk scenarios, and now Microsoft modernizing and improving this technology. The LAPS Client installation using Microsoft Intune. You can refer to the step-by-step guide ->Install LAPS Using Intune Application Deployment Guide.
LAPS is currently available to Windows 10, Windows 11, and Windows Server 2019 or 2022. The LAPS scenario in Azure AD, now part of Microsoft Entra, will shift from private to public preview later this quarter Q1, 2023. Cloud LAPS is not a premium feature.
In the session for Managing local admin account passwords in AD and Azure AD part of the Microsoft Technical Takeoff: Windows + Intune, the Technical team provided a deep dive into the next plan for making it native to Windows.
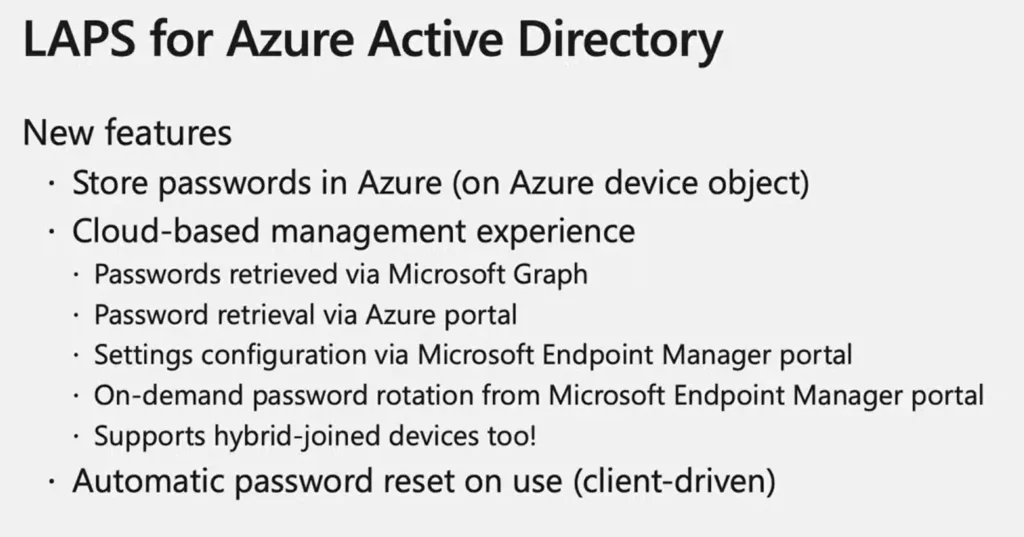
Microsoft LAPS for AzureAD will have the ability to store passwords of AzureAD joined devices on the AAD device object, Cloud-based management experience, passwords retrieved via Graph, Azure portal, or rotated through Intune settings configuration, and more.
- Microsoft Intune Service Release 2210 October Update New Features
- Intune Support for Endpoint Privilege Management
Cloud LAPS Password Management Solution
Let’s check the new version of Cloud LAPS. Microsoft is going to be natively moving it into the operating system, so there will no longer be a need to install a separate MSI package. Moving into the operating system has a lot of advantages it normalizes the patching capability from the Windows update channel.
Modernizing the policy management experience for LAPS, you will have the ability to manage and configure the various LAPS settings from the cloud Microsoft Intune portal.
Considering that a lot of customers have deployed install bases of the current existing product and Microsoft wants to make it very easy to run the new solution side by side until you can get migrated over.
Supported Platforms
Windows LAPS is supported on desktop Windows, Windows Server, and Windows Server Core. Windows LAPS is a native Windows feature on all supported SKUs. No extra steps are required to install the feature.
Support for the Windows LAPS Azure Active Directory scenario is currently extended to Windows 10, Windows 11, and Windows Server, and the Azure Active Directory LAPS scenario is in private preview.
New LAPS capabilities are coming directly to your devices starting with April 11, 2023 security update for the following Windows editions:
- Windows 11 Pro, EDU, and Enterprise
- Windows 10 Pro, EDU, and Enterprise
- Windows Server 2022 and Windows Server Core 2022
- Windows Server 2019
LAPS for Azure AD
Let’s go through what Microsoft is adding in the LAPS feature for the Azure active directory (Azure AD) the device will now have the capability to store passwords in Azure these are going to be stored on the Azure device object.
Microsoft modernizes the cloud-based management experience, In Azure, you will be retrieving them over Microsoft graph there will be an Associated RBAC policy that is associated with that coming up.
Later this year but there will be a first-class password retrieval scenario management experience via the Azure portal you’ll be able to manage all of the LAPS policy settings via the Microsoft Intune portal.
If you’re managing a device’s LAPS settings from the cloud, you will have the ability to do an on-demand password rotation for the Hybrid Joined devices as well from the Intune portal.
This scenario will work you can configure those hybrid devices to back up their passwords to Azure which will work just fine with the client-side features, it’s a security Improvement designed to limit password exposure after use.
- Azure AD LAPs Group Policy Settings For Windows 11 | Intune Policy For LAPs
- Enable Intune LAPS | Local Administrator Password Solution | Proactive Remediation Feature
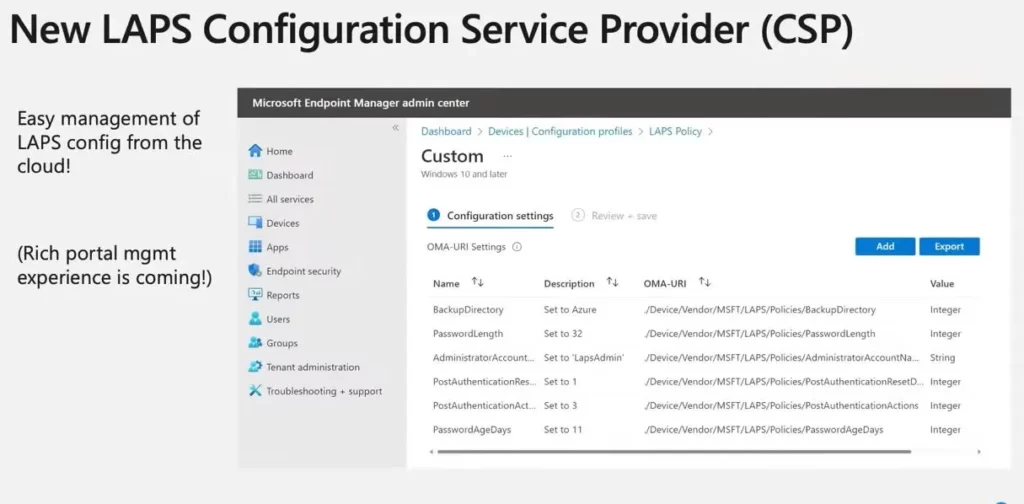
LAPS CSP Policies for Azure AD
The Windows LAPS CSP and Windows LAPS Group Policy object both manage the same settings, but only a subset of these settings apply to Windows LAPS in Azure mode.
The following settings are applicable when backing passwords up to Azure Active Directory:
- BackupDirectory
- PasswordLength
- AdministratorAccountName
- PasswordAgeDays
- PasswordComplexity
- PostAuthenticationResetDelay
- PostAuthenticationActions
List – Cloud LAPS Windows CSP
Jose Luis Mesones Albitres shared an excellent list of Windows CSPs for Cloud LAPS in the following Table. You can refer to the latest updates in the spreadsheet that he provided in the comments section of this post.
| Name | Description | OMA-URI | Value Type |
|---|---|---|---|
| LAPS BackupDirectory | Allows the administrator to configure which directory the local administrator account password is backed up to. Data type is integer. 0 – Disabled (password won’t be backed up) 1 – Back up the password to Azure AD only 2 – Back up the password to Active Directory only | ./Device/Vendor/MSFT/LAPS/Policies/BackupDirectory | Integer |
| LAPS PasswordAgeDays | Use this policy to configure the maximum password age of the managed local administrator account. If not specified, this setting will default to 30 days This setting has a minimum allowed value of 1 day when backing the password to on-premises Active Directory, and 7 days when backing the password Azure AD. This setting has a maximum allowed value of 365 days. Data type is integer. | ./Device/Vendor/MSFT/LAPS/Policies/PasswordAgeDays | Integer |
| LAPS PasswordComplexity | Use this setting to configure password complexity of the managed local administrator account. Data type is integer. 1- Large letters 2 – Large letters + small letters 3 – Large letters + small letters + numbers 4 – Large letters + small letters + numbers + special characters | ./Device/Vendor/MSFT/LAPS/Policies/PasswordComplexity | Integer |
| LAPS PasswordLength | Use this setting to configure the length of the password of the managed local administrator account. If not specified, this setting will default to 14 characters. This setting has a minimum allowed value of 8 characters. This setting has a maximum allowed value of 64 characters. Data type is integer. | ./Device/Vendor/MSFT/LAPS/Policies/PasswordLength | Integer |
| LAPS AdministratorAccountName | Use this setting to configure the name of the managed local administrator account. If not specified, the default built-in local administrator account will be located by well-known SID (even if renamed). If specified, the specified account’s password will be managed. Notes: If a custom account name is specified in this setting, the specified account must be created via other means. Specifying a name in this setting will not cause the account to be created. Data type is string. | ./Device/Vendor/MSFT/LAPS/Policies/AdministratorAccountName | String |
| LAPS PostAuthenticationResetDelay | Use this setting to specify the amount of time (in hours) to wait after an authentication before executing the specified post-authentication actions (see the PostAuthenticationActions setting below). If not specified, this setting will default to 24 hours. This setting has a minimum allowed value of 0 hours (this disables all post-authentication actions). This setting has a maximum allowed value of 24 hours. Data type is integer. | ./Device/Vendor/MSFT/LAPS/Policies/PostAuthenticationResetDelay | Integer |
| LAPS PostAuthenticationActions | Use this setting to specify the actions to take upon expiration of the configured grace period (see the PostAuthenticationResetDelay setting above). Data type is integer. 1 – Reset password The managed account password will be reset 3 – Reset password and log off The managed account password will be reset and any interactive logon sessions using the managed account will be terminated 5 – Reset password and reboot The managed account password will be reset and the managed device will be immediately rebooted. | ./Device/Vendor/MSFT/LAPS/Policies/PostAuthenticationActions | Integer |

What do you think about Win10 support?
What about W10 ?
I put together this OMA-URI list to make it easier to copy and paste when it becomes available to us peasants.
https://1drv.ms/x/s!AtBxBgo0HqI5gfUialOX-Yo_oq5laA
Win10!
Any updates on a GA release date for Cloud LAPS? I’ve seen this but am hoping for a Microsoft-native rather than community-developed solution. This will be a crucial element for us.
msendpointmgr.com/cloudlaps/
Thanks for all the time you put into helping us, Anoop.
Thanks for sharing! This is the configuration part. How to use this? In other words, how do I retrieve the password for a device after configuration is done?
By using the PowerShell commands mentioned in https://www.anoopcnair.com/new-built-in-laps-client-for-windows-11-and-10/ ?
Does LAPS apply to local admins like.\Administrators account only or it can apply to azure AD device or global admins account like xyz@abc.com accounts as well?
I saw most of the settings are also available via the setting catalog. Only “BackupDirectory” is not available yet.
I followed your steps and everything was set successfully. But a few entries later I saw the following: LAPS failed to find the currently configured local administrator account (0x80070002).
Does this has to do with the disabled builtin administrator account or is this because it’s still in private preview? In “Azure AD > Device > Local Administrator password recovery (preview)” I also end up with a internal error.