In this blog post am going to discuss about how to Configure EPM Reusable Settings using Microsoft Intune. Endpoint Privilege Management (EPM) in Microsoft Intune provides a secure way to manage administrative privileges on Windows devices.
By using Reusable Settings, IT administrators can define common elevation rules once and apply them across multiple policies, simplifying privilege management and ensuring consistency. This approach reduces the risk of privilege misuse while streamlining policy deployment.
Configuring Reusable Settings involves specifying how certain applications or processes are elevated on user devices. Administrators can create rules based on file paths, publisher certificates, or file hashes to control which applications receive elevated permissions. Additionally, they can define the elevation behavior, such as auto-approval, requiring user consent, or outright blocking, to align with organizational security policies.
Once created, these reusable configurations can be easily linked to different EPM policies, enabling consistent and scalable privilege management across the enterprise. This not only simplifies administrative tasks but also strengthens endpoint security by standardizing how and when elevated access is granted.

Table of Contents
Different Ways to Add a EPM Reusable Settings
There are several ways to add Endpoint Privilege Management (EPM) Reusable Settings in Microsoft Intune, offering flexibility for managing privilege elevation across devices.
| Ways | Description |
|---|---|
| File Path Rule | This method allows administrators to create elevation rules based on the application’s file location. By specifying the exact file path or using wildcards, IT teams can control which applications are granted elevated permissions. This is ideal for managing internal tools stored in standard directories. Example : C:\Program Files\CompanyApp\App.exe |
| Publisher Rule | Using the digital signature of an application, administrators can configure rules based on trusted software publishers. This ensures that only applications signed by approved vendors (e.g., Microsoft, Adobe) are eligible for elevation, adding an extra layer of security. Example : Allow elevation for apps signed by Microsoft Corporation |
| File Hash Rule | This method involves defining elevation rules using the unique cryptographic hash of a file. It ensures that only a specific version of an application can be elevated, preventing unauthorized or tampered files from gaining privileged access. Example : SHA-256 hash for a verified installer |
- How to Configure Support Approved EPM Elevation using Intune | Highly secured option
- Best Guide to Configure User Confirmed EPM Elevation Settings Policy with Intune
- How to use the Update option in Intune Enterprise App Catalog apps by Vaishnav
- How to Create Secure Boot Compliance Policy with Intune
Create an EPM Reusable Settings
Follow the below mentioned steps to create/configure EPM Reusable Settings using Microsoft Intune. First, Sign In to the Microsoft Intune Admin Center with administrator credentials.
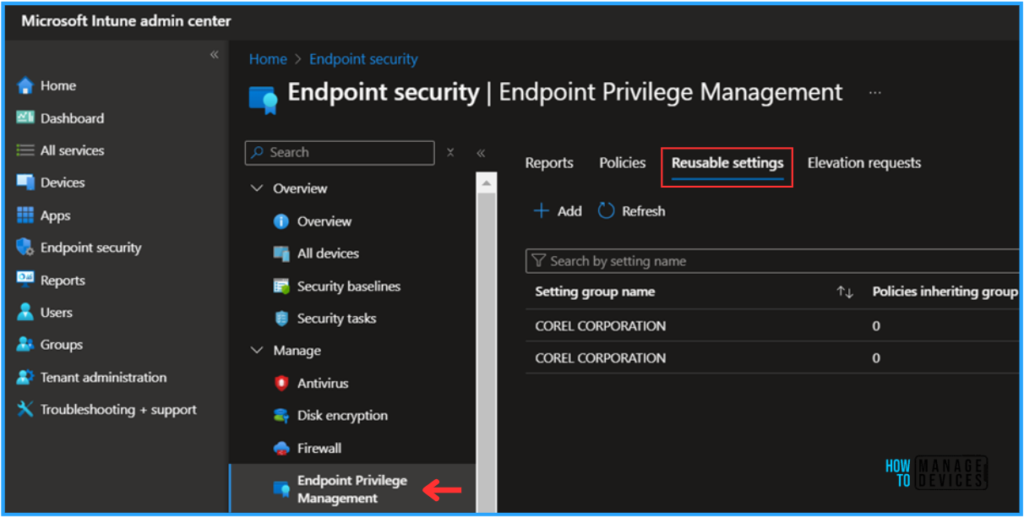
- Navigate to Endpoint security > Endpoint Privilege Management > Reusable settings
- Click on +Add
Export VLC Media Player Certificate Using PowerShell Command
In this, am using vlc-3.0.21-win64.exe binary as an example. Before we start to create a reusable settings, let us export the VLC Media Player’s binary certificate using PowerShell Command. Follow the below steps.
- Download and Save the vlc-3.0.21-win64.exe file
- Open PowerShell/PowerShell ISE with Administrator Privilege
PowerShell Command : Get-AuthenticodeSignature “C:\Users\HTMDTestAccount\Downloads\vlc-3.0.21-win64.exe” | Select-Object -ExpandProperty SignerCertificate | Export-Certificate -Type CERT -FilePath “C:\temp\VLC-3.0.21.cer”
The above command line will help you to export the require VLC Media Player’s certificate in C:\Temp Folder of your device. Certificate Name is VLC-3.0.21.cer.
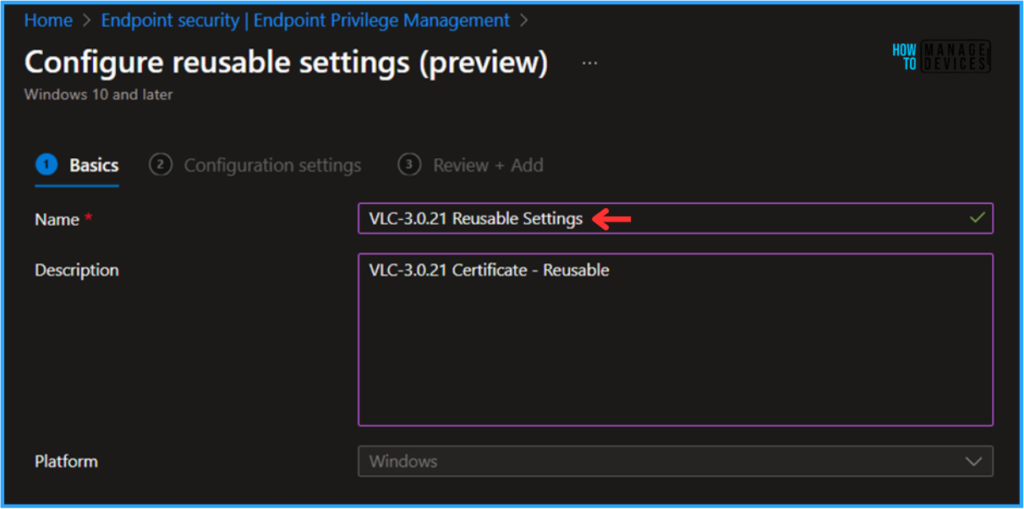
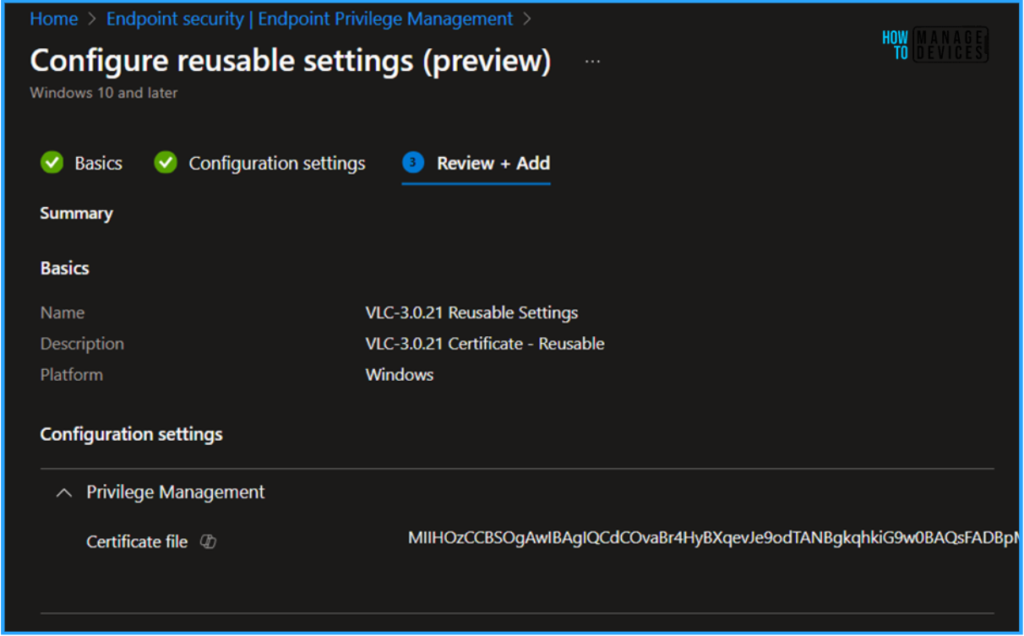
On the Basics page, we can name the reusable settings as “ VLC-3.0.21 Reusable Settings” briefly describe the settings, here am giving description as “VLC-3.0.21 Certificate – Reusable”, and click Next.
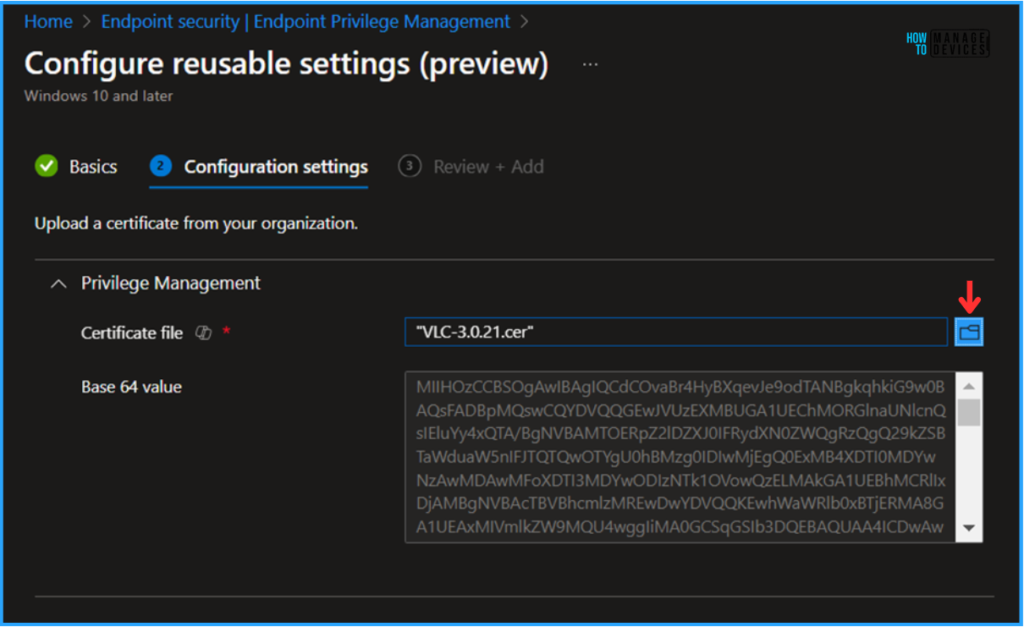
We can now browse and upload the certificate that we need to use it for VLC Player’s reusable settings. We can also see the uploaded certificate’s Base64 value also. once it is successfully uploaded and click then on Next.
On the Review + Save page, review all the settings you’ve defined for the VLC Media Player’s “EPM Reusable Settings”. Once you’ve confirmed everything is correct, select “Add” it to Intune Portal for future use.
How to Add EPM Reusable Settings with an Exisiting Elevation Request
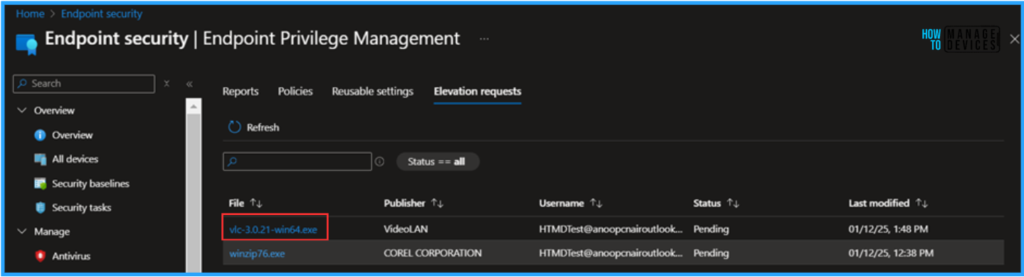
If you already have an active elevation request in the Intune Portal based on that application it’s very easy to add that to Reusable settings. Here I already have an vlc-3.0.21-win64.exe elevation request requested by as user. So Navigate and Create it as per the below mentioned steps.
- Endpoint security > Endpoint Privilege Management > Elevation requests > Click on vlc-3.0.21-win64.exe
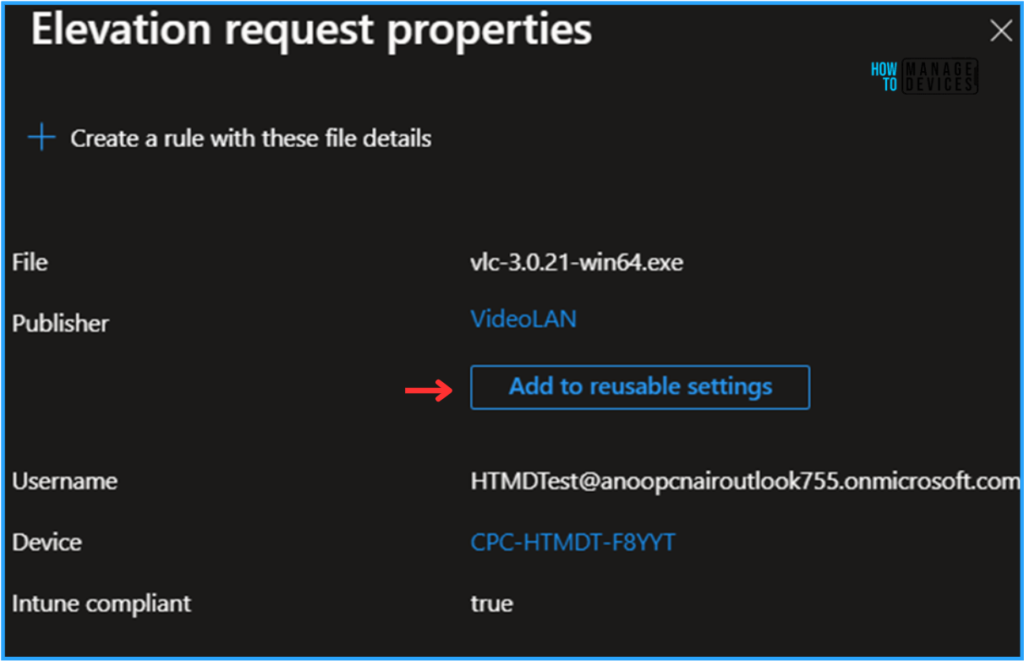
On the Elevation request properties pane, Under Publisher Click on Add to reusable settings it will create the same settings with VideoLAN settings group name.
- How to Configure Support Approved EPM Elevation as Administrator using Intune Policy for Normal Users
- Easily Create New Intune EPM Rules directly from the Elevation Reports
- Best Way to Set Copilot Hardware Key Using Microsoft Intune
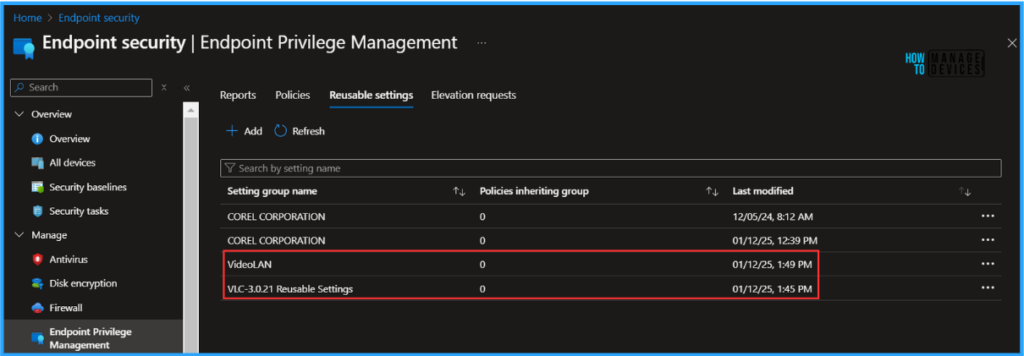
The final step is to confirm the Reusable settings creation for that go to Endpoint security > Endpoint Privilege Management > Reusable Settings. We can see VLC Player Reusable Settings has been created via using both the methods.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Vaishnav K has over 11 years of experience in SCCM, Device Management, and Automation Solutions. He writes and imparts knowledge about Microsoft Intune, Azure, PowerShell scripting, and automation. Check out his profile on LinkedIn.
