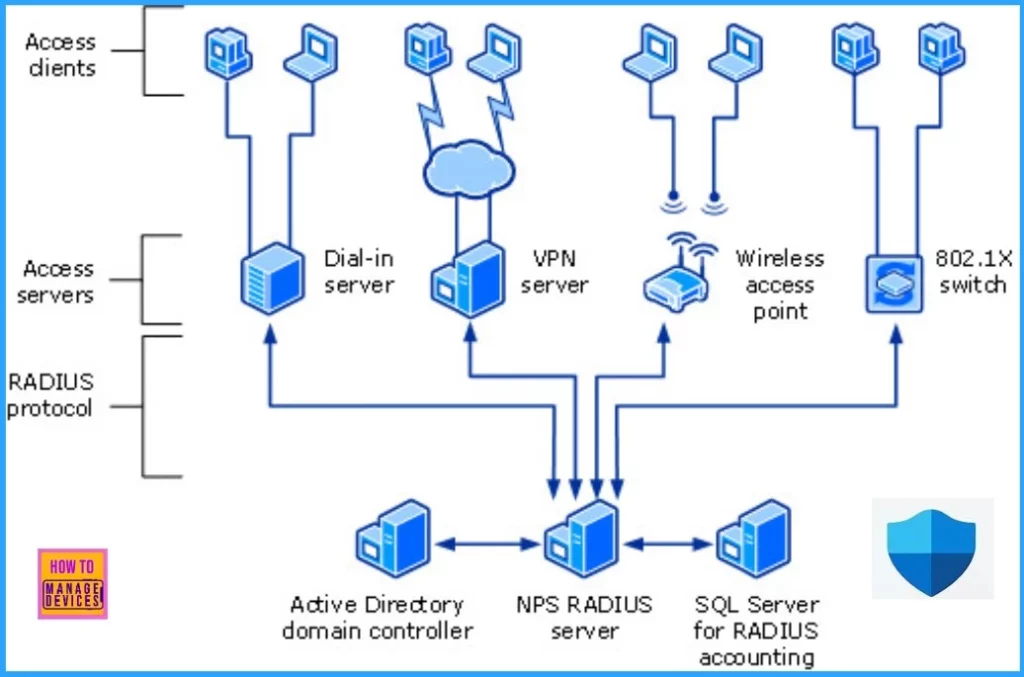
It is essential to know about a security risk, CVE-2024-3596, in the Remote Authentication Dial-In User Service RADIUS protocol related to MD5 hashing. MD5 is a cryptographic hash function algorithm that converts input data of any length into a fixed 128-bit (16-byte) hash value.
MD5 is a hashing method used to secure data. However, different pieces of data can produce the same hash value, known as a collision. This issue is especially concerning for RADIUS traffic sent over the Internet using UDP or User Datagram Protocol.
UDP is one of the core protocols of the Internet Protocol (IP) suite. It does not check if data is altered, so if an attacker exploits the MD5 collision problem, they can change the data packets. This can lead to unauthorized access or other security issues.
To take advantage of this security risk, an attacker must be on the same network as the RADIUS server and have access to it. However, if the RADIUS traffic is sent through a VPN (Virtual Private Network), the VPN secures the data and prevents tampering, so this risk does not apply.
Table of Contents
What is the Security Risk Related to the RADIUS Protocol?
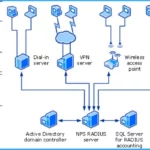
The security risk involves MD5 collision issues that affect RADIUS traffic sent over the internet using the User Datagram Protocol (UDP).
Does this Security Risk Affect all RADIUS Environments?
No, This risk requires physical access to the RADIUS network and the Network Policy Server (NPS).
New RADIUS Standard and Potential NPS Connection Failures with July 2024 Windows Updates
Starting July 9, 2024, Windows updates support a new security feature called the Message-Authenticator attribute in RADIUS Access-Request packets. This is required by new RADIUS standards. While this update improves security, it might cause connection issues with the Network Policy Server (NPS) if your firewall or RADIUS system doesn’t support this feature.
- The update doesn’t cause these issues directly; they happen only if your current setup is incompatible.
- July 2024 Windows 11 KB5040442 KB5040431 Patches and 4 Zero-Day Vulnerabilities
- New Granular Permissions for Endpoint Security Workloads in Intune
- Free Microsoft Copilot for Security Training in Audit Mode | 5 Modules
Workaround or Actions to Secure Your RADIUS Environment
KB5040268 provides detailed guidance on managing the vulnerability associated with CVE-2024-3596. It involves an attack on Access-Request packets in the RADIUS protocol. This vulnerability, related to MD5 collisions, poses a risk where data packets can be altered during transit.
Implementing specific configurations and workarounds is essential to secure your RADIUS environment. The table below provides more details.
| Secure Your RADIUS Environment | Workaround or Actions |
|---|---|
| Enable Message-Authenticator for Requests | It is important to ensure that all Access-Request packets include the Message-Authenticator attribute. This feature is turned off by default, so make sure to activate it. |
| Verify Message-Authenticator in Requests | You should confirm that Access-Request packets contain the Message-Authenticator attribute. It is advisable to enforce this requirement for all packets. By default, this setting is off, so you should enable it. |
| Check Message-Authenticator with Proxy-State | If you use the Proxy-State attribute, consider enabling the limitProxyState option. This will drop packets with the Proxy-State attribute if they do not also include the Message-Authenticator attribute. This option is off by default, so it’s recommended to turn it on if you cannot validate every packet. |
| Verify Message-Authenticator in Responses | You must ensure that RADIUS response packets (Access-Accept, Access-Reject, and Access-Challenge) include the Message-Authenticator attribute. Enable the requireMsgAuth option to discard response packets from remote servers that lack this attribute. This setting is off by default, so turn it on to enhance security. |
- Managing Data Limits for Network Connections in Windows 11
- Windows 11 Reset Network Settings | Track Internet Data Usage
- How to Backup Restore Wi-Fi Network Profiles in Windows 11
- 6 Methods to Check Wi-Fi Network Signal Strength in Windows 11
- 11 Best Fixes for Windows 11 WiFi Connection Issues in 2024
- How to Find Network Adapter Connection Speed in Windows 11
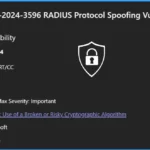
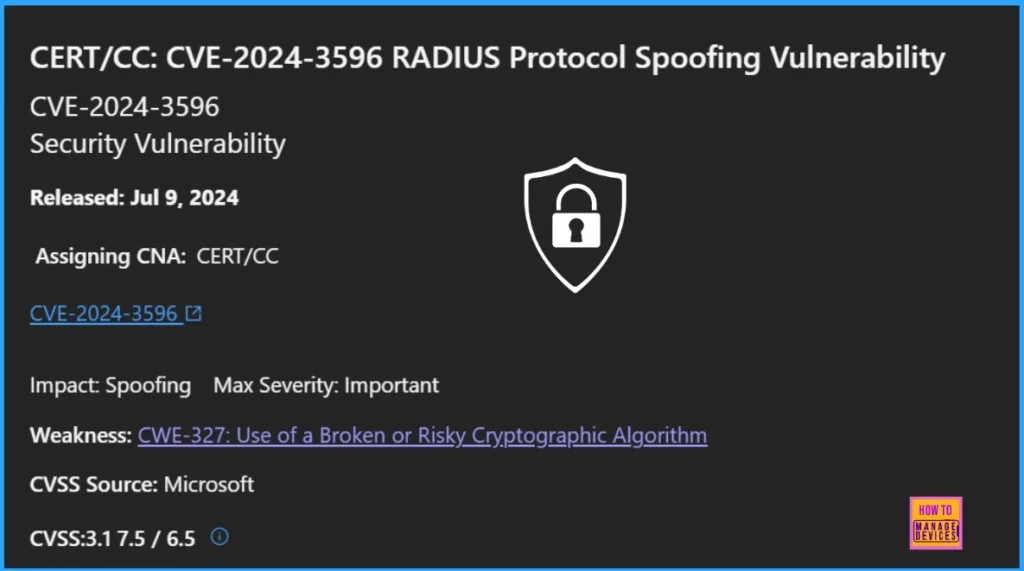
CVE-2024-3596 RADIUS Protocol Spoofing Vulnerability
CVE-2024-3596 is a security vulnerability in the RADIUS protocol identified by CERT/CC. This vulnerability is classified as important due to its potential impact on spoofing. The table below provides more details.
| CVE Details | Data |
|---|---|
| CVE Title | CERT/CC: CVE-2024-3596 RADIUS Protocol Spoofing Vulnerability |
| CVE ID | CVE-2024-3596 |
| Release Date | July 9, 2024 |
| Assigning CNA | CERT/CC |
| Impact | Spoofing |
| Max Severity | Important |
| Weakness | CWE-327: Use of a Broken or Risky Cryptographic Algorithm |
| CVSS Source | Microsoft |
| CVSS Score | 7.5 / 6.5 |
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here. HTMD WhatsApp.
Author
Anoop C Nair has been Microsoft MVP from 2015 onwards for 10 consecutive years! He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is also a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.
