In this article I will explain how to Enable Device Password History Policy using Microsoft Intune. The Device Password History Policy in Microsoft Intune is a security setting that prevents users from reusing their old passwords on managed devices.
By enabling this policy, IT administrators can specify how many previous passwords are remembered by the system. This ensures users must create a new and unique password when updating their credentials, reducing the risk of compromised passwords being reused.
Using Microsoft Intune, this policy is part of the broader Device Restrictions configuration. Admins can define the password history count (e.g., last 5 or 10 passwords) for Windows, iOS/iPadOS, Android, or macOS devices. This setting enhances compliance with organizational security standards and helps meet regulatory requirements for password management.
Once configured and deployed via Intune, the password history policy is enforced on all assigned devices. Users attempting to reuse an old password during a password change will be blocked, thereby encouraging better password hygiene. Combined with other password policies, this helps maintain a stronger security posture across the organization.

Table of Contents
What is Device Password History Policy
Here’s a concise table explaining key points about the Device Password History Policy Configuration in Microsoft Intune.
| Point | Details |
|---|---|
| Policy Name | Device Password History Policy |
| Purpose | Prevents users from reusing previous passwords |
| Managed Through | Microsoft Intune (Device Configuration Profile > Device Restrictions) |
| Applicable Platforms | Windows, Android, iOS/iPadOS, macOS (platform support may vary) |
| Configuration Option | Set number of previous passwords to remember (e.g., 5, 10) |
| Security Benefit | Enhances password hygiene and prevents easy-to-guess credential reuse |
| Compliance Use | Supports compliance with standards like NIST, ISO 27001, HIPAA |
| Deployment Scope | Assigned to device groups or user groups via Intune |
| User Impact | Users must create new passwords that haven’t been used recently |
| Common Use Case | Enforcing enterprise password policies for enhanced security posture |
- How to Configure Minimum Password Age Security Policy using Intune
- Enable Edge Password Safety Alerts for Users Policy in Microsoft Intune
- Best Method to Enable Virtualization Based Security Using Microsoft Intune
Create a Configuration to Enable Device Password History Policy in Intune
To enable the Device Password History Policy using Microsoft Intune, follow these steps. First, sign in to the Microsoft Intune Admin Center with your administrator credentials.
- Navigate to Devices > Windows > Manage devices > Configuration
- Click on +Create > +New Policy
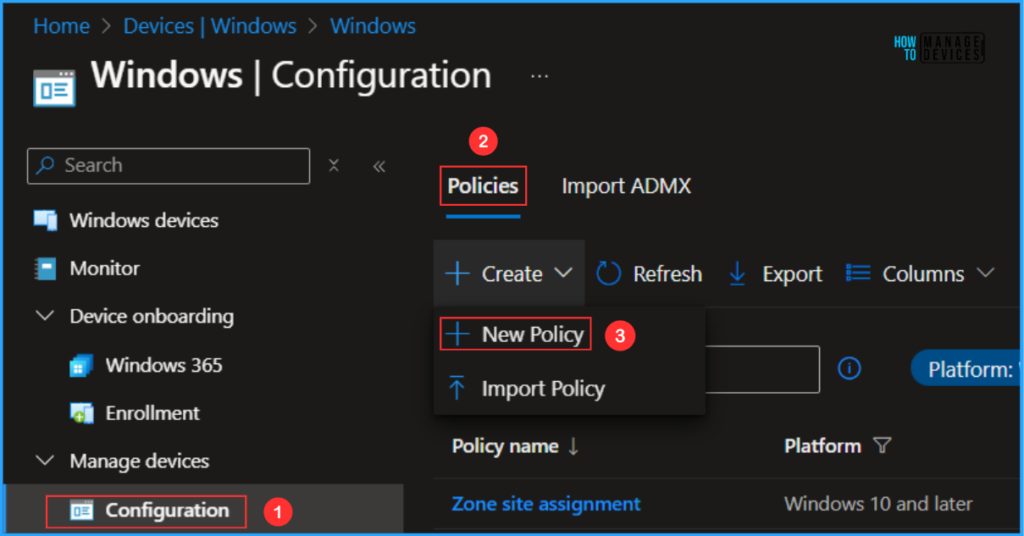
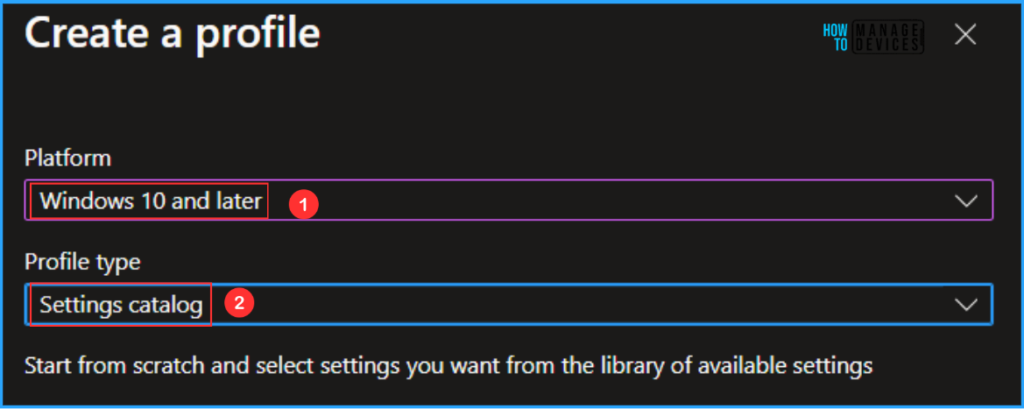
Next, we will create a new configuration profile from scratch. First, we need to provide the options mentioned below.
- Platform: Windows 10 and later
- Profile type: Settings catalog
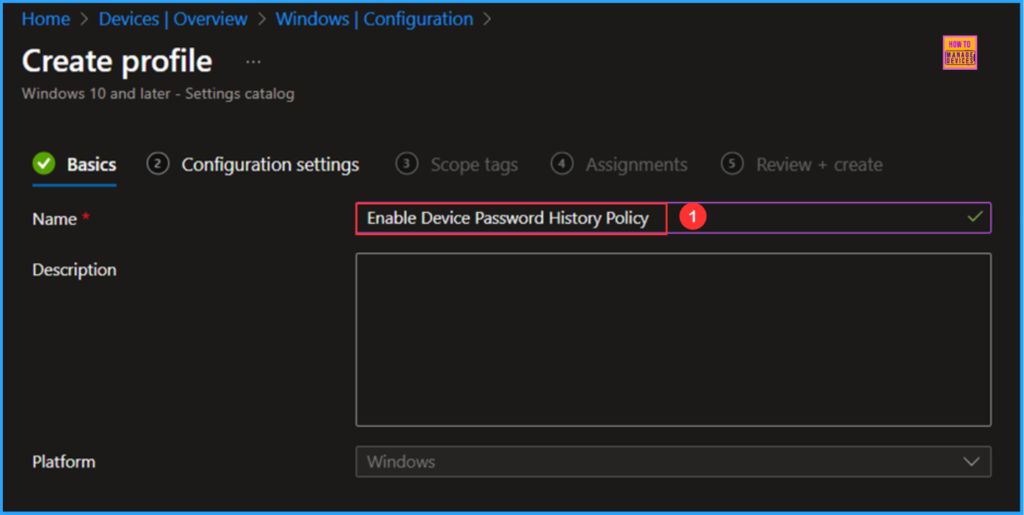
On the Basics details page, we can name the configuration policy “Enable Device Password History Policy,” if necessary, provide a brief description of its usage, and then click Next.
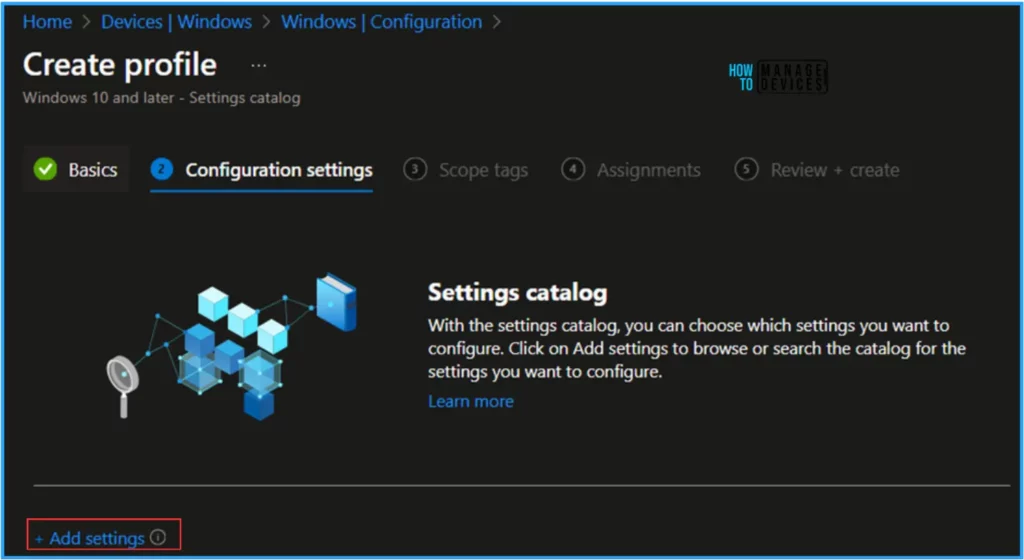
We can now add the necessary settings to the Configuration Settings pane. To do this, click on +Add settings in the bottom left corner of the page.
Search for “Device Password History” as a keyword. This will help us find the correct policy based on your current needs. Next, look for the “Device Lock” category and click on it. Check the settings labeled “Device Password History” and then close the Settings picker window.
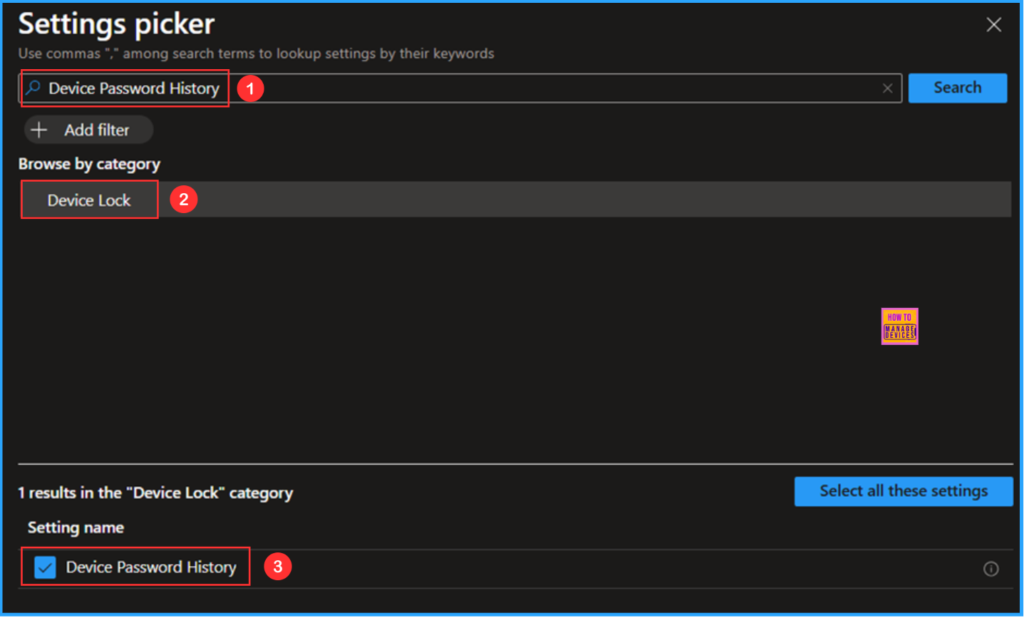
On the current Configuration Settings page, enable the Device Password and set the Device Password History to 5, this Specifies how many passwords can be stored in the history that can’t be used.then click Next.
Policy CSP – ./Device/Vendor/MSFT/Policy/Config/DeviceLock/DevicePasswordHistory
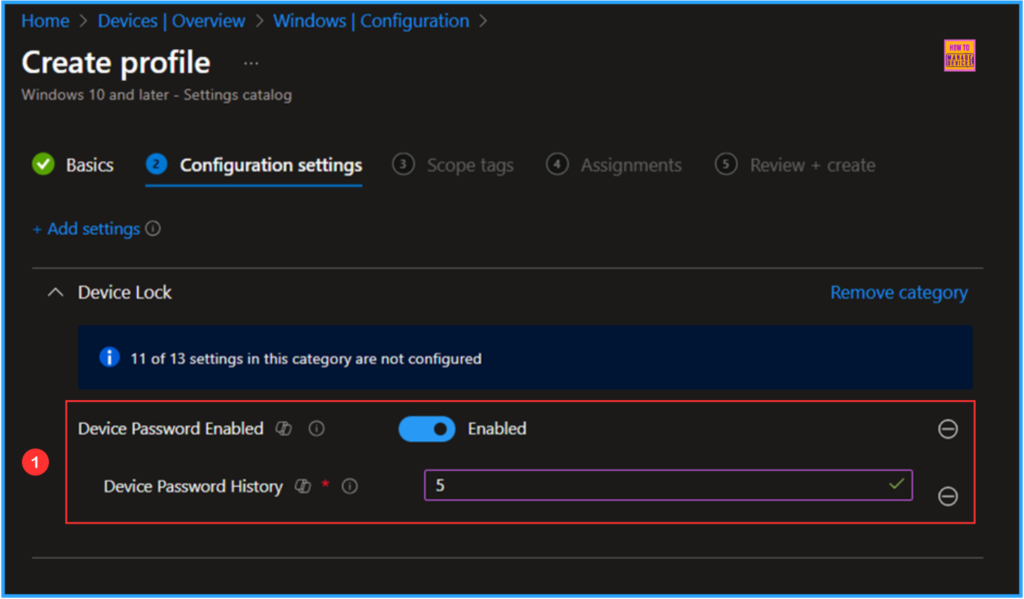
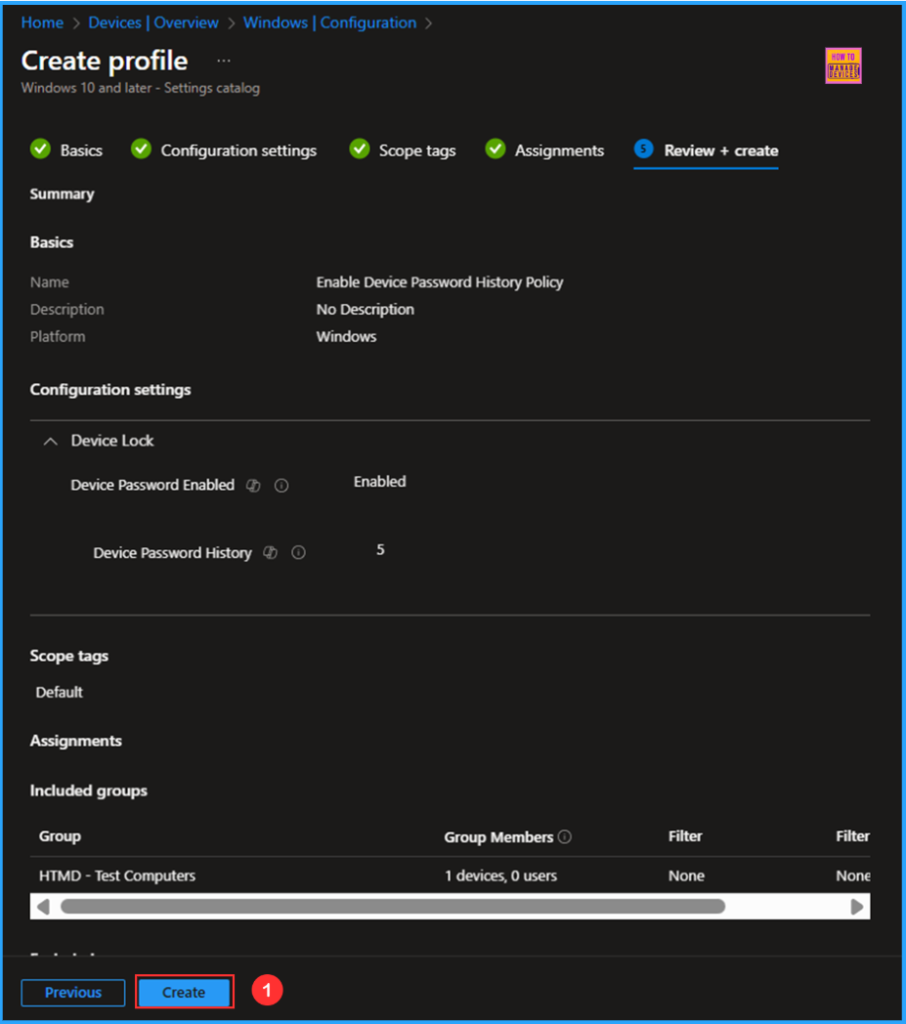
On the next page, keep the Scope tags set to Default. If your tenant has custom scope tags, select them according to your policy needs, then click on Next.
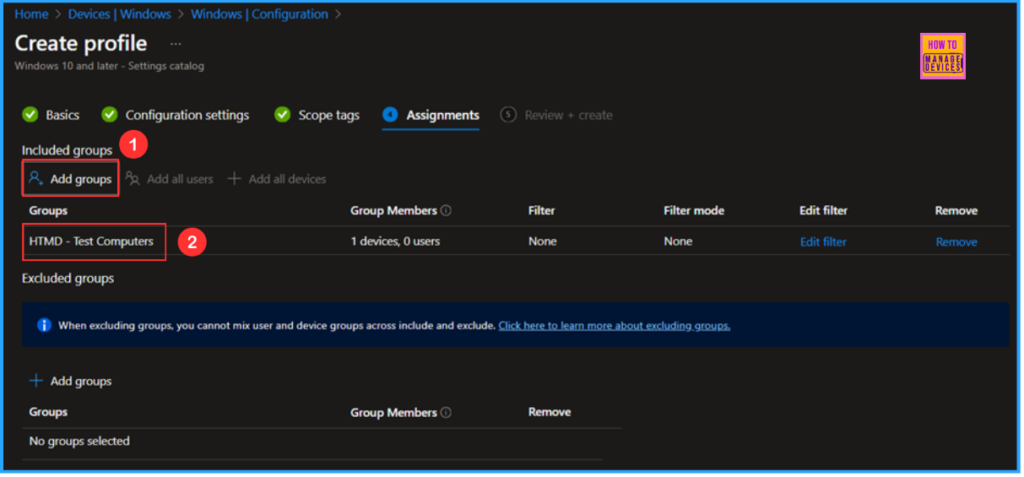
I am assigning the configuration policy to the “HTMD – Test Computers” device group. To do this, click on “Add Groups” and select the desired device group under the “Included Groups” option. In this example, I am not using any filters, and the “Excluded Groups” option has been left blank.
On the Review + create page, thoroughly review all settings defined for the Enable Device Password History Policy. Once you’ve confirmed everything is correct, select “Create” to deploy the policy.
- Easy Way to Disable Device Password Sync with Intune
- Easier Way to Enable Local Security Authority Protection Mode with Intune
- Best Method to Add a Local User to Local Administrator Group with Intune Local User Membership Policy
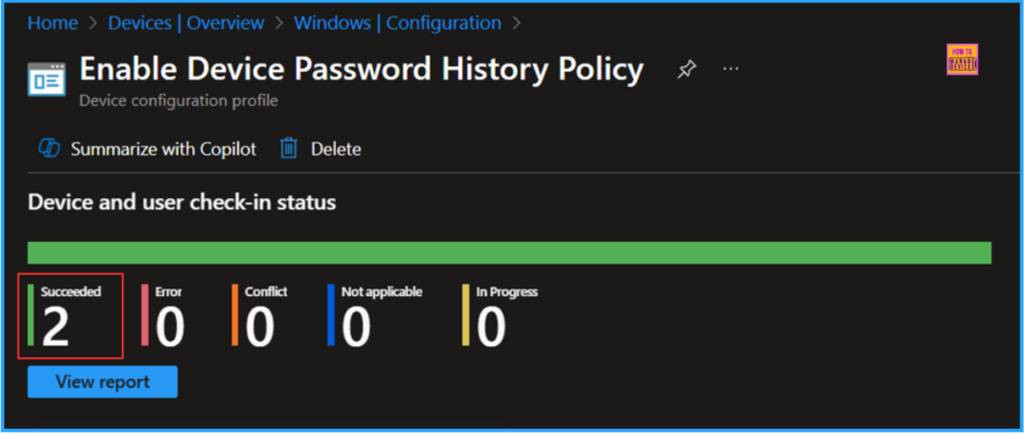
Monitor the Enable Device Password History Policy Deployment
The configuration policy has been successfully deployed to the HTMD – Test Computers, Microsoft Entra ID Device group. Once the device is synced, the policy will take effect immediately. To monitor the policy deployment from the Intune Portal, follow the steps below.
- Navigate to Devices > Windows > Configuration > Search for the “Enable Device Password History Policy” configuration.
- Under the Device and user check-in status, you can see the policy’s deployment status.
End User Experience
We can now verify whether the “Enable Device Password History Policy” policy is functioning correctly. Start by logging into the device affected by the policy. Next, we can check the status of the policy using the Intune Event Logs. To do this, open the Event Viewer on the device.
- Navigate to Applications and Services Logs > Microsoft > Windows > Devicemanagement-Enterprise-Diagnostics-Provider – Admin
Filter the latest logs with Event ID 814 to to easily locate the successful log. The screenshot below shows that the policy was successfully applied to the system, and our policy has worked as expected!

Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
Vaishnav K has over 11 years of experience in SCCM, Device Management, and Automation Solutions. Writes and imparts knowledge about Microsoft Intune, Azure, PowerShell scripting, and automation. Check out my profile on LinkedIn.


