Let’s check how to disable stay signed in to all your apps Prompt using Intune Settings catalog (Windows CSP) Vs. registry fix via Win32 App deployment. This is a tricky option when I accidentally click the OK button instead of the No, sign in to this app only option from a personal device.
There are a couple of scenarios that will be a bit tricky for AVD and Windows 365 Cloud PC testing using the RD client subscription option. The first scenario is when I use a personal device to access AVD or Windows 365 for testing. The second scenario is when I use the production device and test the staging environment AVD or Windows 365 Cloud PCs using RD client.
In both scenarios, if you click the OK button accidentally from the Stay Signed in to all your apps popup screen, your device will end up adding an additional account to the Access Work or School section of the settings app in Windows 11 or Windows 10.
- How to Create Shortcut For Access Work Or School Accounts
- Windows 11 Intune Enrollment Process using Company Portal Application
In this post, you will see two methods deploy the same fix. Learn how to Disable Workplace Join using Windows CSP or Registry Fix. I couldn’t make Windows CSP using the settings catalog work! Well, the CSP is to Disallow Workplace Join using Window CSP. Let me know what your experience is after reading the post and testing!
The registry fix explained in this post is to block Workplace join. I don’t know what the difference is between Disallow and Block! This is another question you can answer in the comments.
Manual Method to Avoid Registering Devices to Wrong Azure AD
Whenever you get the following screen and message, such as Stay Signed in to all your apps, you will need to ignore the OK button, as explained below.
With these popup screen settings, Windows will remember your account and automatically sign you in to your apps and websites on this device. This will reduce the number of times you are asked to log in.
Allow my Organization to manage my device.
Selecting this option means your administrator can install apps, control settings, and reset your device remotely. Your Organization may require you to enable this option to access data and apps on this device.
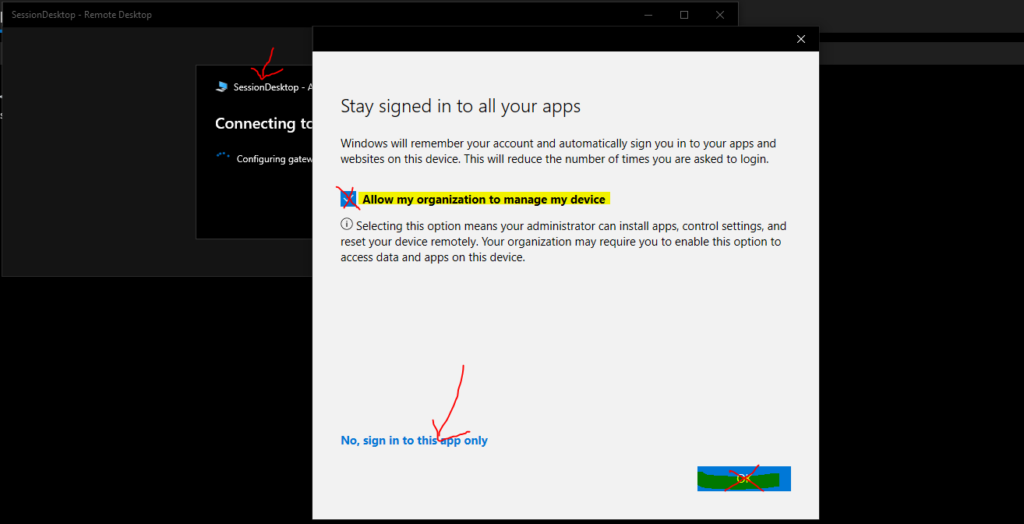
Remove the checkmark near the option called – Allow my Organization to manage my device.
Once the checkmark is removed from Allow my Organization to manage my device option, click on the link No, sign in to this app only.
NOTE! – Do not click on the OK button.
Disable Stay Signed in to all your apps Prompt using Windows CSP
Let’s try to disable Stay Signed in to all your apps Prompt using Intune settings catalog. However, I don’t think this is a very good approach, and this will work for the users who have admin access, etc. I have not tested this solution with non-admin users.
- Login to Endpoint Manager Intune portal https://endpoint.microsoft.com/#home
- Navigate to Devices -> Windows -> Configuration profiles.
- Click on +Create Profile.
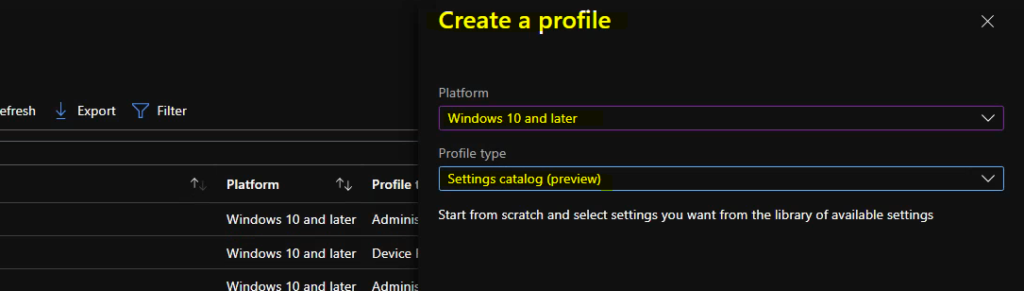
In Create Profile blade, You can select Platform: Select Windows 10 and later and Profile: Select Settings catalog (preview).
Click on Create button. For Example – You have to select the platform Windows 10 and later. You can enter the details of the policy and settings in the next screens.
Once you click on Create button from the above page, you will need to enter the Name and Description of the setting catalog policy.
Enter the name of the policy Name – Disable Stay Signed in to all your apps and click on the next button to continue.
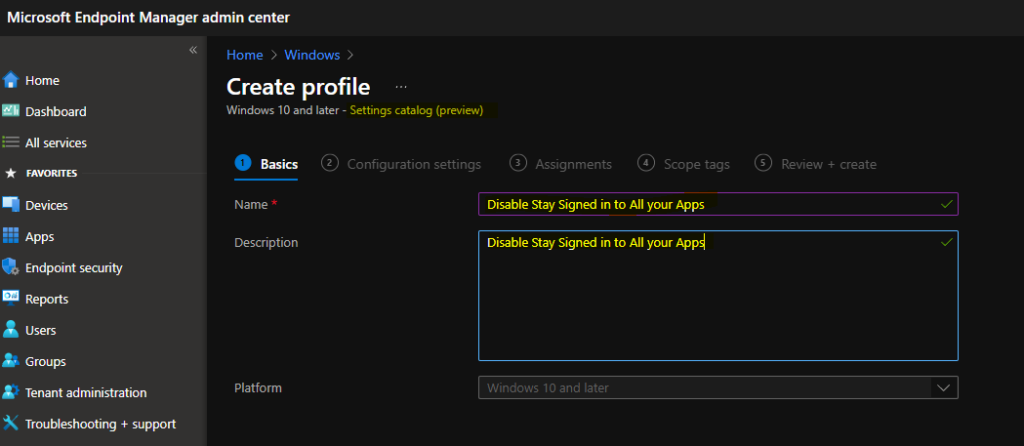
You will need to click on the +Add Settings hyperlink from the next page of the policy configuration wizard. This hyperlink will help with a new blade called the Settings Picker with a search box.
Settings catalog – With the settings catalog, you can choose which settings you want to configure. Click on Add settings to browse or search the catalog for the settings you want to configure.
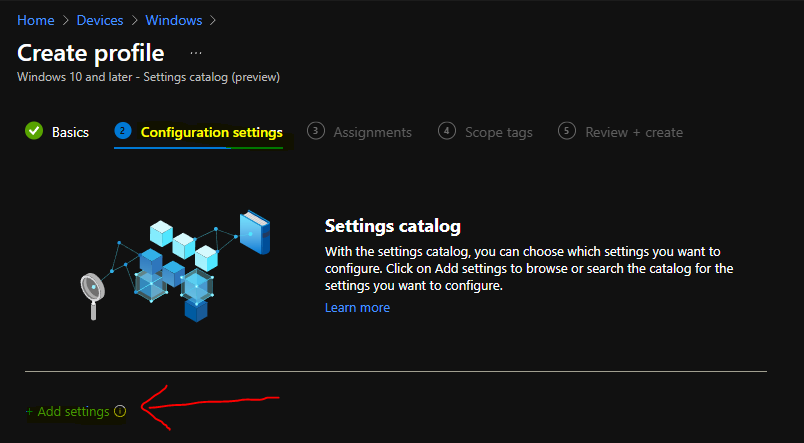
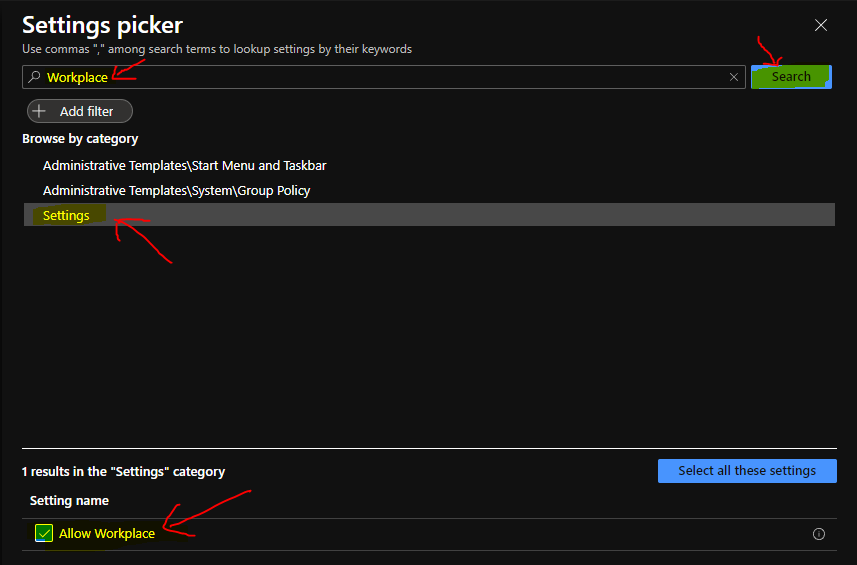
You also have many other options like filtering the policies based on OS edition etc. You can use the search box to find the relevant policies to Workplace Profiles.
I have clicked on the Settings category and selected one policy called Allow Workplace to disable Stay Signed in to all your apps Prompt using Intune popup screen.
Windows MDM CSP details for this setting – Allows users to change workplace settings, and this is a device-based policy. The following list shows the supported values:
- 0 – Not allowed.
- 1 (default) – Allowed.
Now, you will need to block Allow Workplace to test whether this will help remove or disable the problematic popup screen whether you try to subscript to Windows 365 or Azure Virtual Desktop.
- Allow Workplace – BLOCK
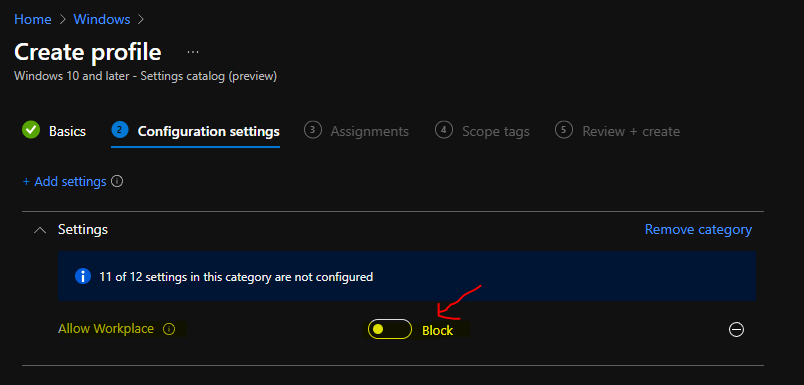
This section will help you to assign the “Disable Allow Workplace” Policy to the AAD User Group. You can refer to the following guide to Create Intune Settings Catalog Policy and deploy it only to a set of Intune Managed Windows 11 or Windows 10 devices using Intune Filters.
I used all users’ deployment as an example for this particular policy deployment. I want to disable Allow Workplace for all the users. You can click on the Next button and add the Scope Tags on the next page.
You will need to click on the next and create buttons to complete the policy creation process.
Intune Event ID 813
The Intune event ID 813 indicates a string policy is applied on the Windows 11 or Windows 10 devices. You can also see the exact value of the policy being applied on those devices.
You can check the Event log path to confirm this – Applications and Services Logs – Microsoft – Windows – Devicemanagement-Enterprise-Diagnostics-Provider – Admin.
MDM PolicyManager: Set policy int, Policy: (AllowWorkplace), Area: (Settings), EnrollmentID requesting merge: (D1E11663-BF69-4DD8-974A-BAD47E6EF433), Current User: (Device), Int: (0x0), Enrollment Type: (0x6), Scope: (0x0).
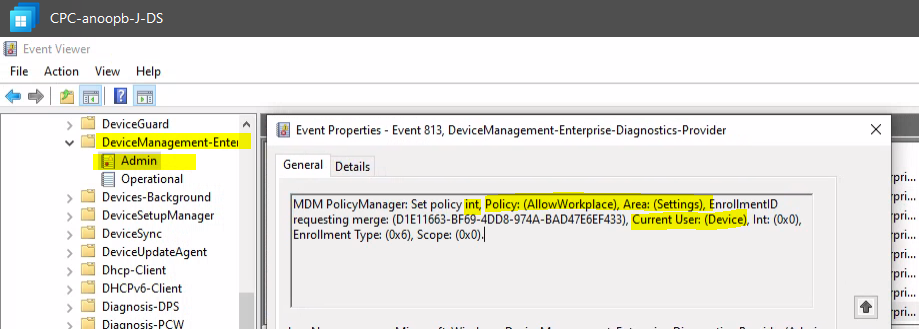
Disallow Workplace Join using Window CSP
I could see that the correct registry value worked got applied as expected on the Cloud PC. This Windows CSP is to Disallow Workplace Join using Window CSP.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\current\device\Settings
AllowWorkplace = 0 means the Workplace join scenario is disabled for the user.
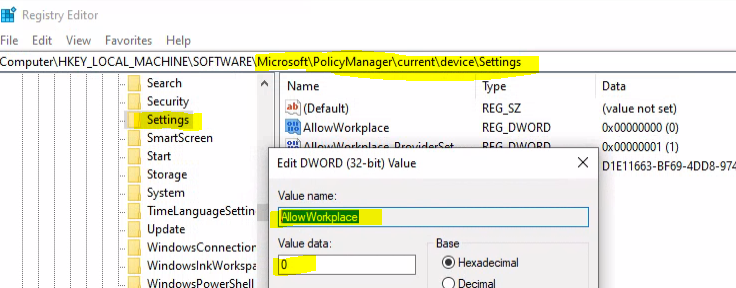
Now, you can see that the + Connect button is disabled from the Access work or school tab. So the policy got applied correctly as expected.
As per my testing, disabling Access Work or School didn’t make any difference to Stay Signed in to all your apps Prompt. I don’t think this is the correct policy for disabling the Stay signed in to all your apps popup.
Registry Fix using Intune Win32 App to Disable Stay Signed in to all your apps Prompt
Now, let’s check whether the Registry Fix using Intune Win32 App to Disable Stay Signed in to all your apps Prompt will work as expected or not. This registry fix will block workplace join.
The registry fix is the supported way as per Microsoft docs. This registry fix helps to block users from adding more work accounts (Azure AD registered) on my corporate Windows 10/11 devices.
Prepare to Create IntuneWin file for Registry Fix to block workplace join
You need to create two files to deploy registry fix using Intune, as I explained in Deploy Registry Fix Using Intune Win32 App. Once those files are created, you will need to go through the steps mentioned in the above blog post to create the “.IntuneWin” package.
- The first file is the registry file itself. You will need to paste the following registry information to a notepad and save it as DisableWorkplaceJoin.reg file.
The following is the registry value that you will need to deploy.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WorkplaceJoin]
@=""
"BlockAADWorkplaceJoin"=dword:00000001Now, it’s time to create a batch file to execute this registry fix on the Windows 10 Azure AD joined devices or Hybrid Azure AD joined devices. It’s just a simple batch file to execute the DisableWorkplaceJoin.reg file.
- You can paste the following batch file and save it as DisableWorkplaceJoin.cmd.
MD C:\Windows\Temp\DisableWorkplaceJoin
Copy "%~dp0*.reg" C:\Windows\Temp\DisableWorkplaceJoin /Y
PUSHD C:\Windows\Temp\DisableWorkplaceJoin
regedit.exe /s DisableWorkplaceJoin.reg
@echo 1.0>C:\Windows\Temp\DisableWorkplaceJoin\Ver1.0.txt
Del C:\Windows\Temp\ActiveXFix\*.reg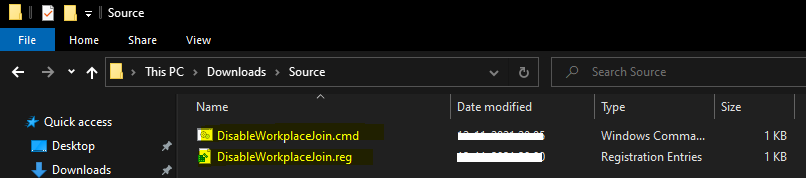
Now, you can create an IntuneWin file using the guide Deploy Registry Fix Using Intune Win32 App. Download the IntuneWinAppUtil.exe to covert the files created above into the IntuneWin package.
C:\Users\Anoop\Downloads>IntuneWinAppUtil.exe
Please specify the source folder: C:\Users\Anoop\Downloads\Source
Please specify the setup file: DisableWorkplaceJoin.cmd
Please specify the output folder: C:\Users\Anoop\Downloads\Package
Do you want to specify the catalog folder (Y/N)?n
Now, you have the package called DisableWorkplaceJoin.intunewin. The package is ready to deploy registry fix using Intune application deployment method.
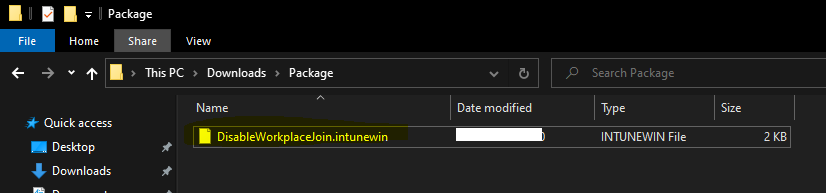
Create Intune Win32 app to Block Workplace Join
You can now head to the MEM admin center portal to create Intune Win32 application to deploy the registry fix. It would help if you kept the DisableWorkplaceJoin.cmd file information handy while creating the application.
- Login to endpoint.microsoft.com portal.
- Navigate to All Apps > Windows -> Click on +Add button to create Win32 app.
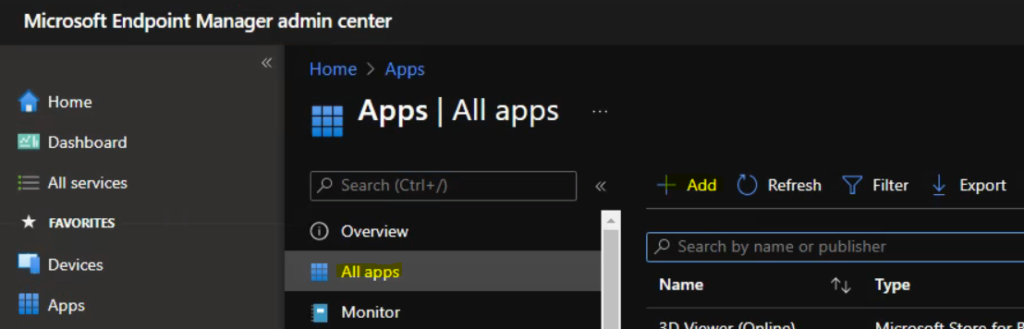
You now need to select the app type that you want to deploy. Select the Intune app type called Windows app (Win32) and then click on the Select button to start the app creation process.
You can now upload the file you created in the above section IntuneWin package “DisableWorkplaceJoin.intunewin” from the select app package file hyperlink.
You can click on the OK button to continue.
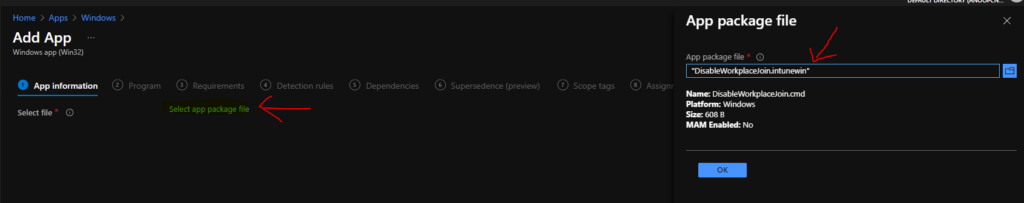
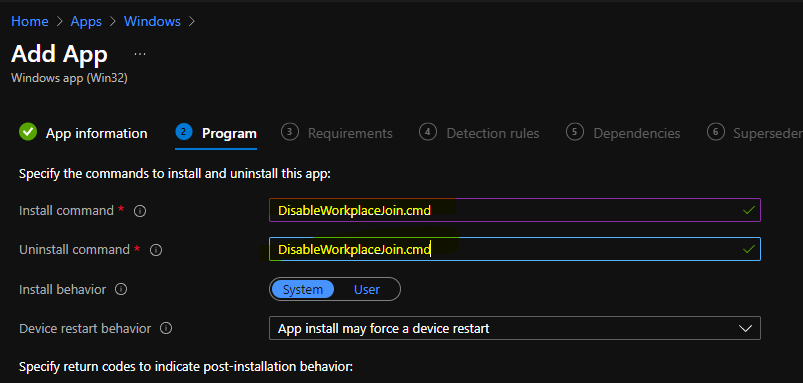
You can now enter the name of the application and other details from the Application information page. Proceed to the Program page to enter the install command and uninstall command details.
- Install Command = DisableWorkplaceJoin.cmd
- Uninstall Command = DisableWorkplaceJoin.cmd
- Click on the NEXT button to continue.
NOTE! – The uninstall command is just a fake command just for my lab testing. But the recommendation is to go with the proper uninstall command. This is just an example of deploying a registry fix using Intune. Only for testing purposes.
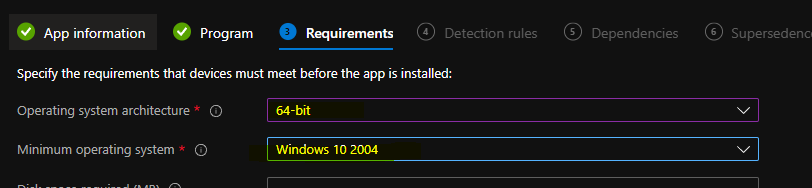
You can now select the requirement page OS architecture and minimum OS from this page and click on the next button to continue. This package is going to help to disable Stay Signed in to all your apps Prompt.
- Operating System Architecture = 64-bit
- Minimum Operating System – Windows 10 2004
- Click on the Next button
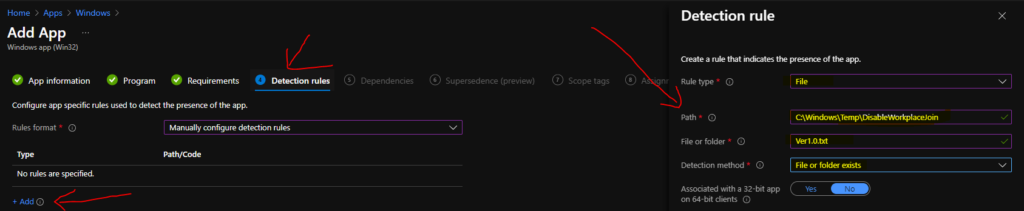
You can also go over the Detection Rules page and select Configure app-specific rules used to detect the app’s presence. Select the option Manually configure detection rules to continue building detection logic for this application deployment.
Click on the +Add button to add the following detection rule.
- Rule Type -> File
- Path -> C:\Windows\Temp\DisableWorkplaceJoin
- File or folder – Ver1.0.txt
- Detection Method -> File or Folder exists
- Associated with a 32-bit app on 64-bit clients -> NO
- Click OK and NEXT to continue.
You can go over the dependencies and supersedence, scope tags pages to continue. Those pages are not mandatory for this Registry to fix Intune win32 application. On the assignment page, you need to assign this application to any Azure AD device group.
You can refer to the following guide to Create Intune Settings Catalog Policy and deploy it only to a set of Intune Managed Windows 11 or Windows 10 devices using Intune Filters.
I used all users’ deployment as an example for this particular policy deployment. I want to disable Workplace Join and stop getting Stay Signed in to all your apps prompt. You can click on the Next button and add the Scope Tags on the next page.
You will need to click on the next and create buttons to complete the policy creation process. Now, you are already deployed the registry fix to Disable Workplace Join.
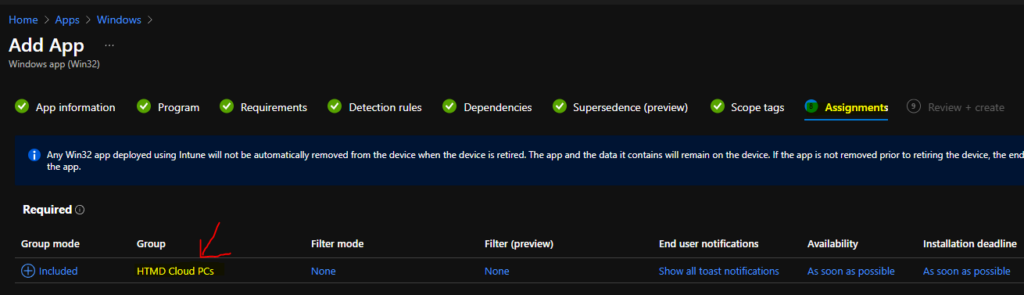
Restart Intune Management Extension Service to deploy the registry fix to disable Workplace Join and stop getting Stay Signed in to all your apps prompt using Win32 app to Cloud PCs.
Verification Block Workplace Join
You can look into Intune Management Extension Deep Dive – Win32 App Deployment Troubleshooting Help Guide to get more details on troubleshooting if the registry fix via Win32 App deployment is not working for you.
The registry check before the application deployment to add the registry value.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WorkplaceJoin
The registry key name BlockAADWorkplaceJoin is not present.
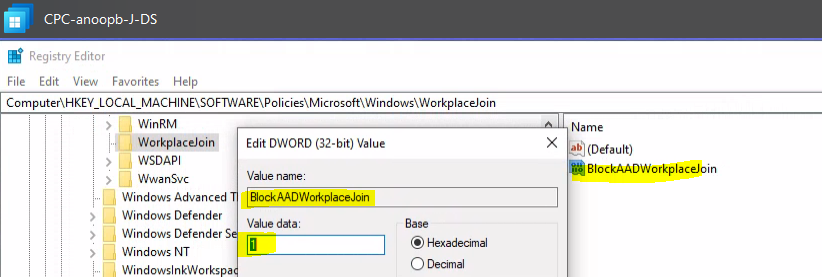
After the successful deployment of the application BlockAADWorkplaceJoin, the Registry key called BlockAADWorkplaceJoin got created.
BlockAADWorkplaceJoin = 1
Conclution Disable Workplace Join using Windows CSP Vs Registry Entry
Didn’t Work as expected – Windows CSP is to Disallow Workplace Join using Window CSP; it didn’t help to disable Stay Signed in to all your apps prompt.
WORKED Fine – The registry fix to Block Workplace Join using Intune helped to disable Stay Signed in to all your apps prompt.
Author
Anoop is Microsoft MVP! He is a Solution Architect in enterprise client management with more than 20 years of experience (calculation done in 2021) in IT. He is Blogger, Speaker, and Local User Group HTMD Community leader. His main focus is on Device Management technologies like SCCM 2012, Current Branch, and Intune. He writes about ConfigMgr, Windows 11, Windows 10, Azure AD, Microsoft Intune, Windows 365, AVD, etc……………

How do you do this for guest users accessing Teams (for example) from their unmanaged personal devices?
I have a similar concern. I would like to have unmanaged devices blocked from getting this prompt as we have seen a number of accidental enrollments which turned into us fully managing personal devices, which is not in our management strategy.
Can this prompt be blocked for unmanaged or unknown devices?