Greetings everyone! In this post, we will go through how to Enable Tamper Protection for macOS using Intune. We will discuss the purpose of tamper protection and the necessary requirements to enable it on multiple devices. Additionally, we will walk you through enabling it in our test environment so you can follow the steps to enable it across your own organizational devices.
Our last blog post discussed Configure Extensible Single Sign-On for macOS Devices. We have provided an overview of SSO and the Microsoft Enterprise SSO plugin and explained the steps to configure the Extensible Single Sign-On SSO Authentication for Apple macOS devices in Intune.
Tamper protection is a useful feature that safeguards security settings set by organizations’ IT Admins on managed client devices, including virus and threat protection. As an IT Security Admin, we should enable tamper protection so the security settings can not be edited by any user for safety concerns.
By default, IT Admins can enable or disable Tamper protection tenant wide by using the Microsoft 365 Defender portal. Or else, if Tamper protection is deployed and managed through Intune, then it can be managed in Intune Admin Portal Under Endpoint Security > Antivirus.

- How to deploy Microsoft Defender for macOS using Intune
- Learn How to Configure macOS Antivirus Policy Using Intune
Tamper Protection and its Advantages
Microsoft Defender for Endpoint offers a feature called Tamper Protection which is used to safeguard important security settings, such as virus and threat protection, from being altered or disabled on the managed client devices in an organization.
Cyber attackers often try to turn off security features on devices during an attack, due to which attackers can easily access user data, install malware, and exploit user identity, data, and devices.
Tamper protection is designed to prevent these malicious activities from happening, making it an essential component of Microsoft Defender for Endpoint’s anti-tampering capabilities that include standard protection attack surface reduction rules.
Once IT Admins enable tamper protection in managed client devices, it can prevent in disable or altered in settings such as :
- Virus and threat protection remains enabled.
- Real-time protection remains turned on.
- Behavior monitoring remains turned on.
- Antivirus protection, including IOfficeAntivirus (IOAV), remains enabled.
- Cloud protection remains enabled.
- Security intelligence updates occur.
- Automatic actions are taken on detected threats.
- Archived files are scanned.
Users can still check their configuration settings even with tamper protection activated. Additionally, non-Microsoft antivirus apps are not affected by tamper protection. If any organization uses Defender for Endpoint, tamper protection settings cannot be changed by users. However, only the security team can manage them from the backend.
Types of Tamper Protection Modes
As an IT Admins, we have been provided with 3 types of modes while setting up Tamper production for managed client devices, let us discuss them in detail.
| Mode | Description |
|---|---|
| Audit | In this mode, Tampering operations will be logged but not blocked. It is the default mode after installation. |
| Block | In this mode, Tamper Protection will be activated. However, Tampering options will be blocked. |
| Disabled | In this mode, Tamper protection will be turned off. |
Let us discuss in detail when Tamper protection is set to Audit / Block mode and what should be expected from the app or configuration. When we set Tamper Protection to Audit mode, as stated above, it records or logs all the tampering operations for auditing purposes.
- Uninstall the Defender for the Endpoint agent
- Creating/modifying Endpoint files and new files under the defender Endpoint location
- Deleting or renaming defenders for endpoint files
However, when we set it to Block mode, it blocks all the tampering operations while the tamper protection feature is activated on the macOS.
- Block to uninstall the Defender for the Endpoint agent
- Block creating/modifying Endpoint files and new files under the defender Endpoint location
- Block Deleting or renaming defenders for endpoint files
- The Defender agent cannot be forced to quit by the user
Pre-Requisites
Before IT Admins enable tamper protection on managed macOS devices, they should also look into the minimum requirements which should be checked.
- macOS versions supported Big Sur or later
- Install Defender for Endpoint app v101.70.19 or later
- System Integration Protection (SIP) should be enabled
- Defender for Endpoint should have Full Disk Access authorization
- Configure Microsoft Defender for Endpoint using Intune MDM Platform
Note! macOS has System Integrity Protection (SIP) to prevent unauthorized code execution. Only App Store apps and notarized apps can be launched by default.
To configure and deploy Microsoft Defender App on macOS devices, check out my previous post on How to deploy Microsoft Defender for macOS using Intune.
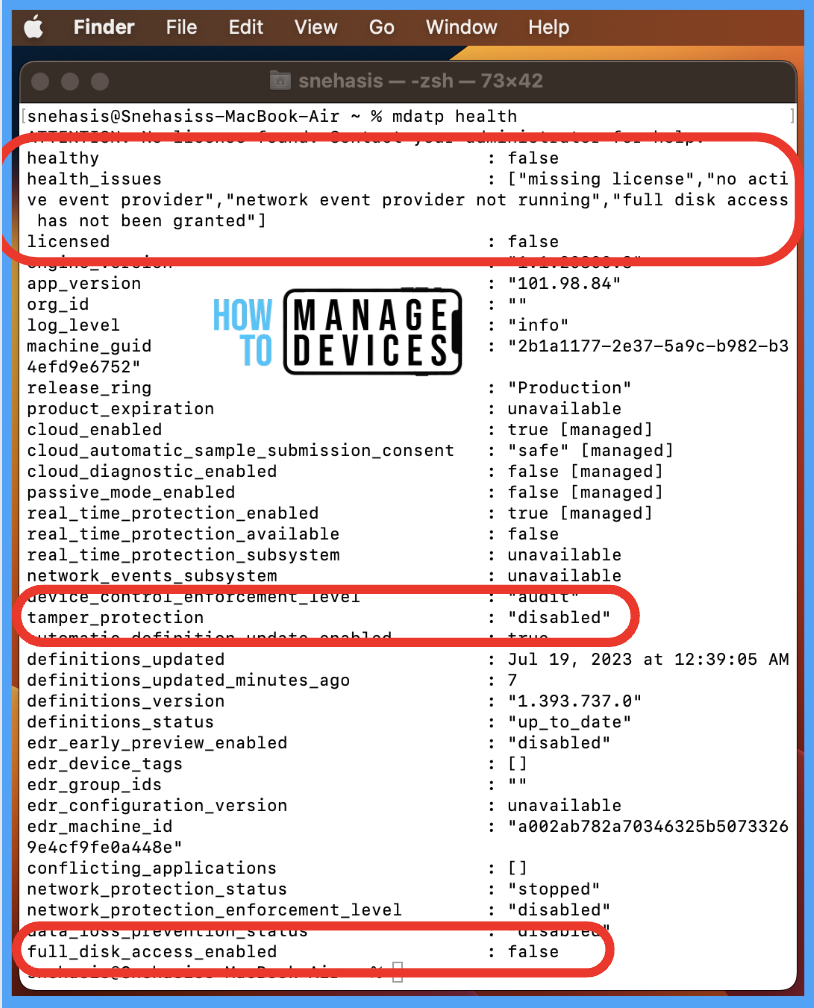
For the current user, the license is showing as false, health_issues is showing as a missing license, and Tamper_protection is disabled as User doesn’t have a Microsoft Defender license. If the machine is licensed, then by default, Tamper_protection will show as Audit, if not licensed, it will show as Disabled.
Licensing Requirements to Use Microsoft Defender on Mac, Please ensure to have any of the below lists of licenses before pushing Microsoft Defender for Endpoint on Mac devices.
- Microsoft 365 E5
- Microsoft 365 E5 Security
- Microsoft 365 A5
- Windows 10 Enterprise E5
- Microsoft 365 Business Premium
- Windows 11 Enterprise E5
- Microsoft Defender for Endpoint
Also, on the device manually, We can configure Tamper protection by running the command: mdatp config tamper-protection enforcement-level –value { disabled|audit|block }
Configure Tamper Protection on macOS
As we have checked the system requirements and ensured all the requirements are checked, and the license is assigned to the device, the status is shown below.
- healthy: true
- health_issues : [ ]
- licensed: true
- tamper_protection: “audit”
Enable Tamper Protection for macOS
Let’s see how can we deploy the Tamper protection by creating a configuration profile, we must ensure to have the required access to the Intune Portal. Follow the steps mentioned below to create a Tamper Protection Configuration profile in Intune portal for macOS devices.
- Sign in to the Microsoft Intune admin center https://intune.microsoft.com/.
- Select Devices > macOS > Configuration Profiles and click on Create Profile.
- Select Profile type as Settings Catalog and click on Create.
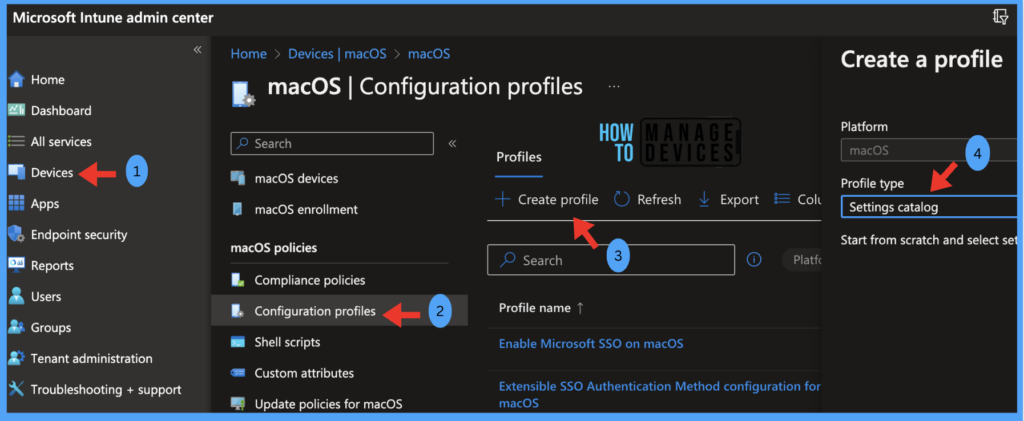
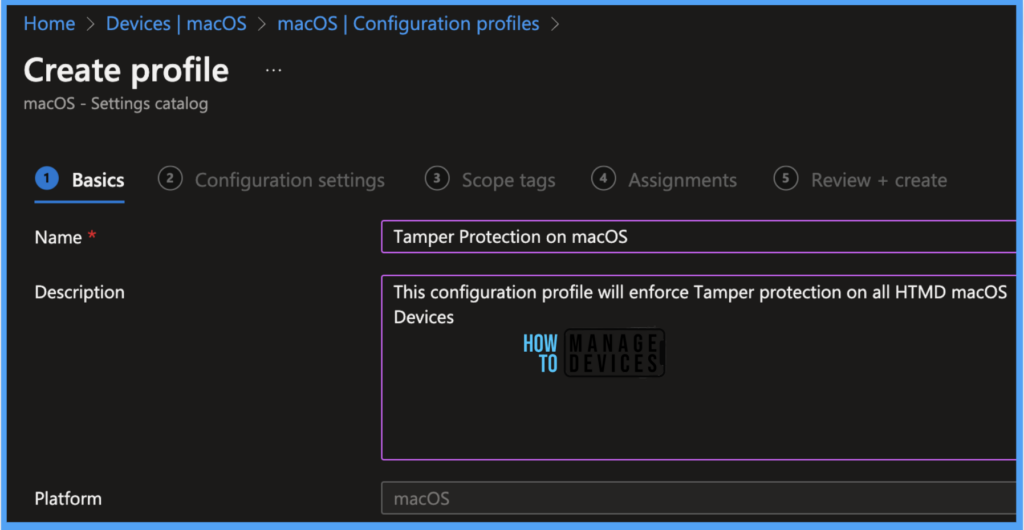
Once you click on Create button from the above page, Provide the Name and Description and click on Next.
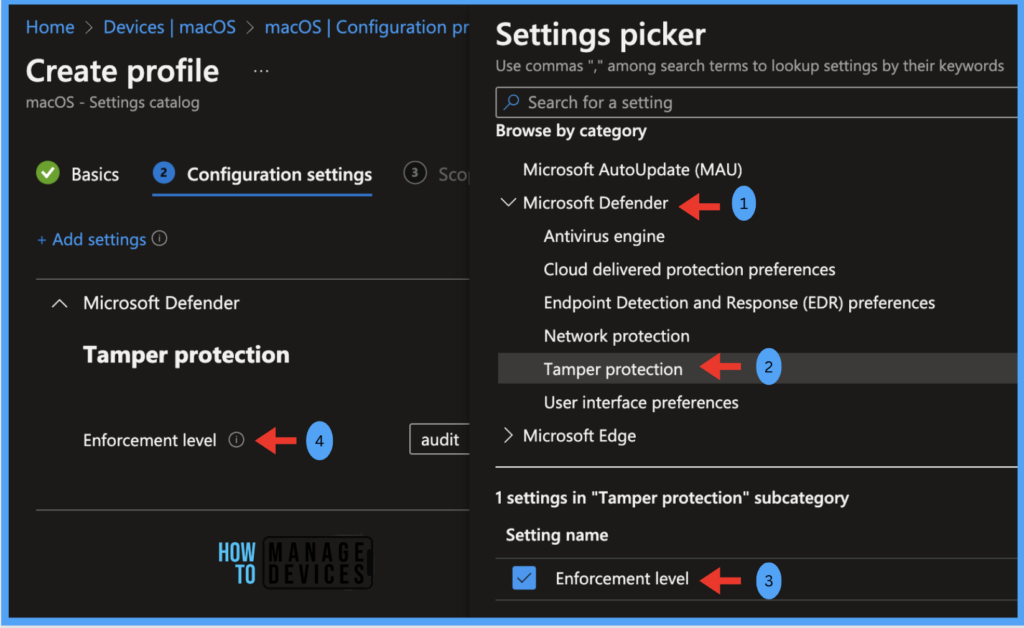
Under the Configuration settings tab, click Add settings and browse by Microsoft Defender > Tamper Protection category. Once it loads, select the Enforcement level, and select the enforcement level as { Disabled | Block | Audit }
Scope tags are filtering options provided in Intune to ease the admin jobs. In the scope tag section, you will get an option to configure scope tags for the policy. Click on Next.
On the next page, select Assignments group (Included groups and Excluded groups) and click Next.
Note! Assignment Group: It determines who has access to any app, policy, or configuration profile by assigning groups of users to include and exclude.
On the Review+create page, please review if any settings need to be changed, or else go ahead and create the Configuration Profile.
Once the Tamper Protection profile is created, it will take a few minutes to get pushed to all the devices in the organization; also, to view the push status on the list of targeted devices, we can check as per the below steps.
To see all the device statuses, Navigate to Devices > under macOS > Select Configuration Profiles, once you see the profile, click on the link to go to the Overview page, and you should be able to find the list of devices categorized as per the below list.
- Succeeded
- Error
- Conflict
- Not Applicable
- In Progress
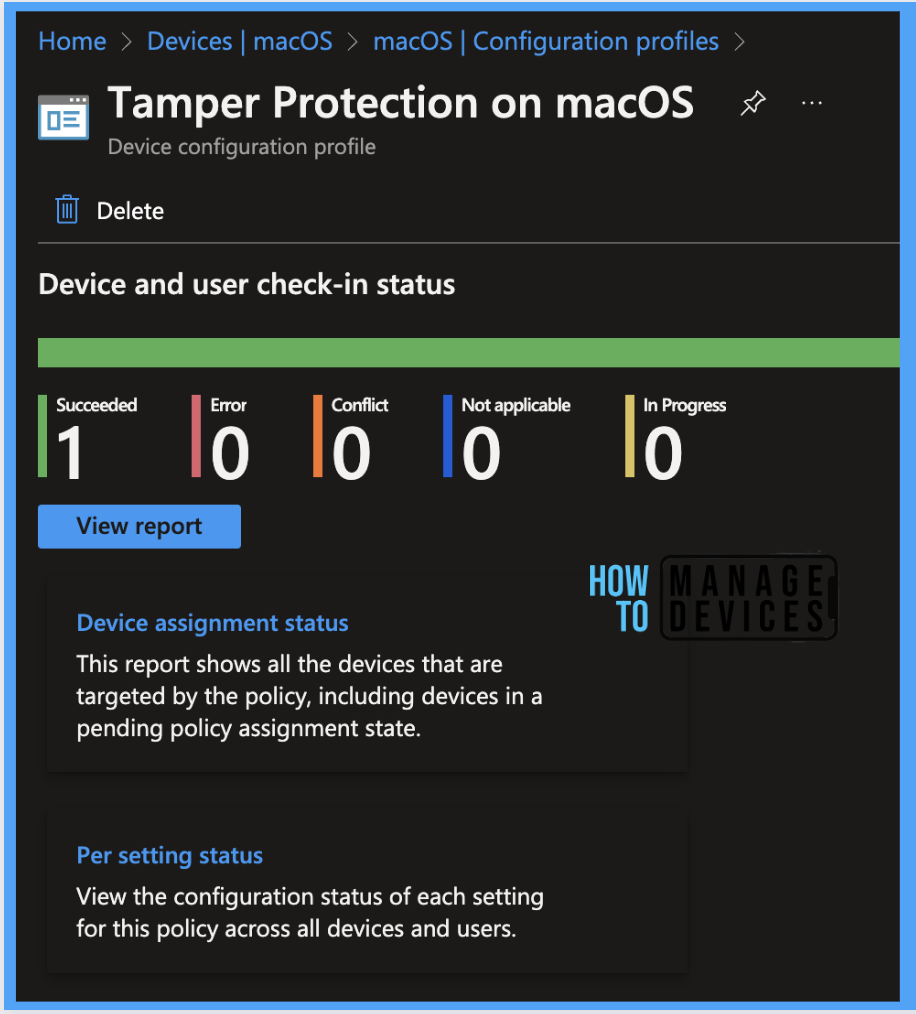
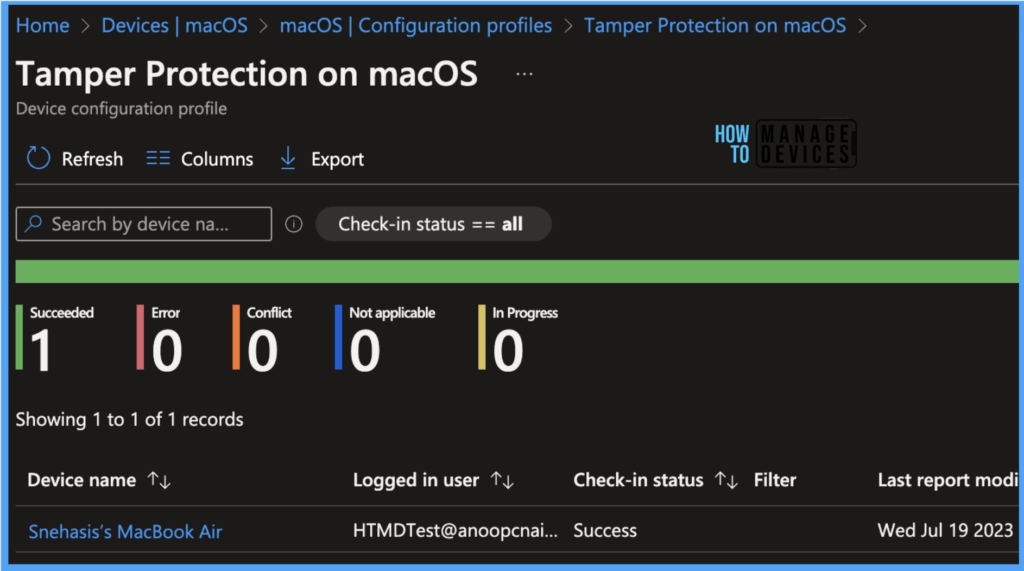
Once you click on the view report button, you can see the list of devices along with their details below:
- Device name
- Logged in User
- Check-in Status
- Last check-in time
Also, we can view the two different types of reports, you can quickly check the update as devices/users check-in status reports.
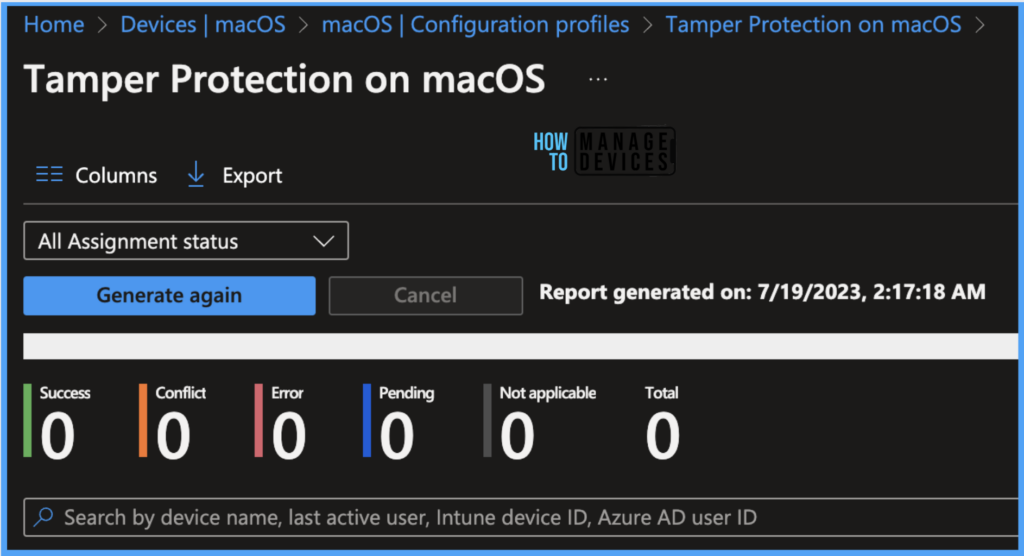
Device assignment status, This report will show the list of targeted devices under the configuration profile, including devices in pending policy assignment status. To generate a fresh report every time, click on Generate again.
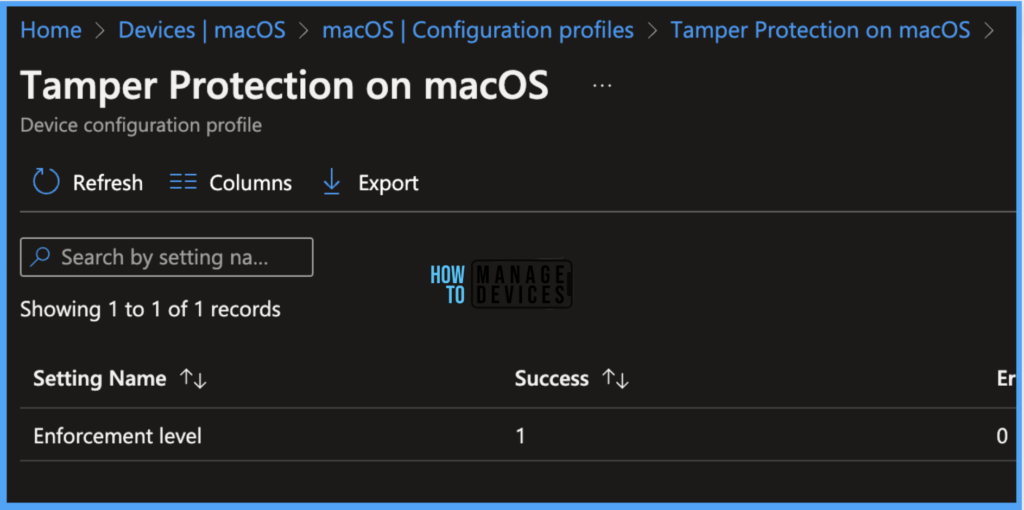
Per settings status, This report will show the configuration status of each set for this policy across all devices and users.
Here’s how you can export Intune setting catalog Profile report from Intune portal. You have two options to navigate to the compliance policies node either you can navigate to the Devices node or Endpoint Security, Intune Settings Catalog Profile Report.
- Enroll macOS in Intune with Step by Step Guide
- Configure macOS Compliance Policy in Intune for Devices
End User Experience
Now that we have pushed the configuration profile to all the macOS devices in the organization let us check from the end user perspective if it is reflecting under profiles in System settings. Once the user successfully logs in to the device, we can follow the steps below to check the profile status.
- Click on the Apple icon at the top-left corner
- Select System Settings from the list of options
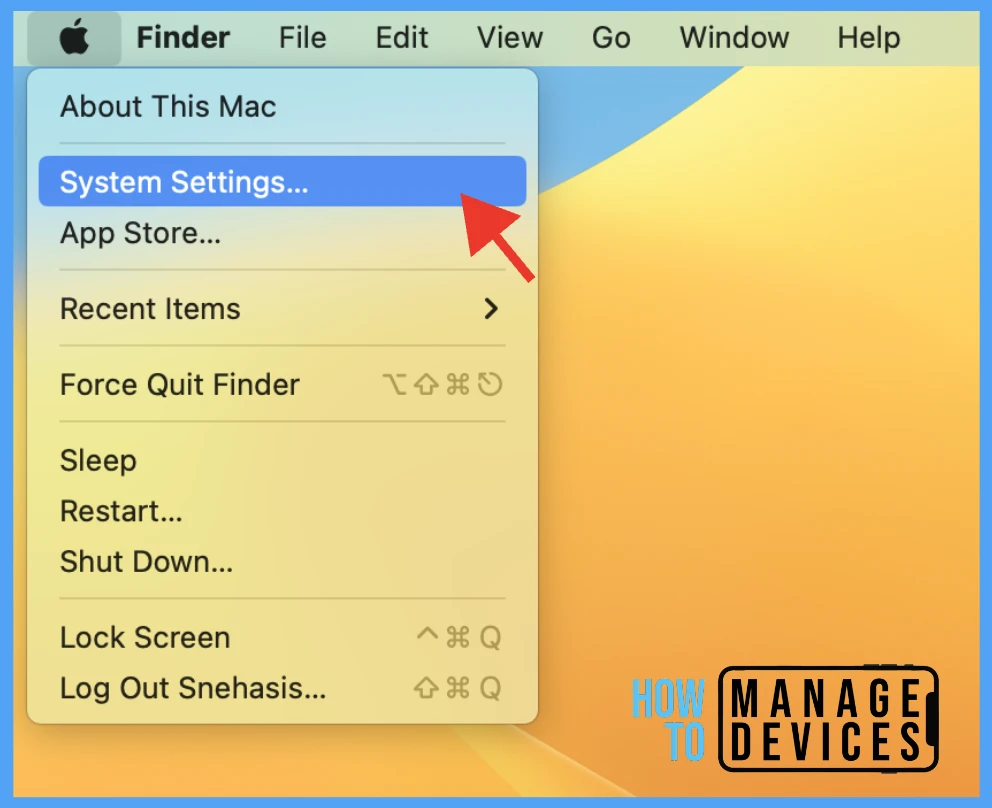
Under the Profiles section, Check if the profile is deployed. Also, we can check by running the command in the terminal: mdatp health –field tamper_protection.
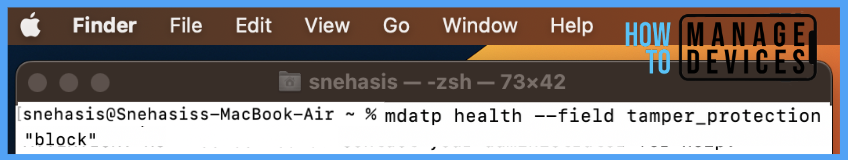
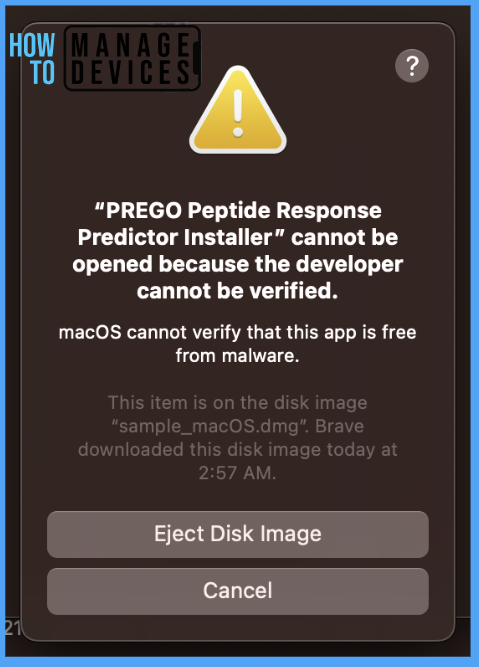
Also, if the Tamper protection mode is set as a block, Tamper Protection verifies the package’s authenticity. Hence it only allows the app installation from the app store and identified developers. Or else users might get errors like the one below.
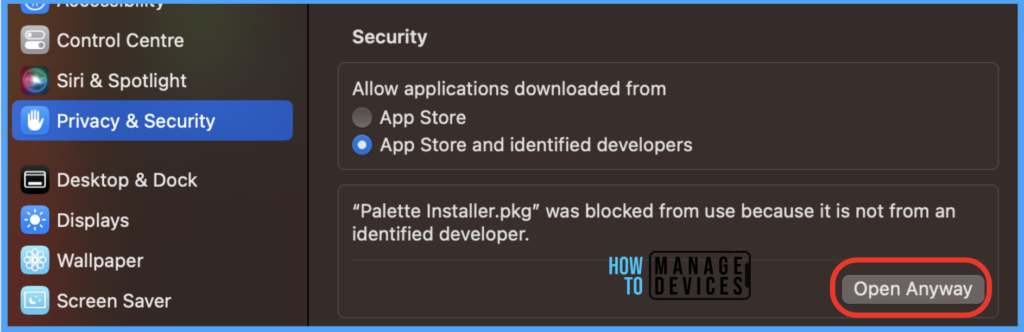
Suppose the app is authenticated by the Organisation’s IT security team, it can be fixed by allowing the app in System Settings> Privacy & Security > Under Security by clicking on Open anyway.
Conclusion
Organizations, as a mandate, should use Antivirus apps to prevent any cyberattacks on their environment. Also, tamper protection is an additional level of security to ensure that all the security settings don’t get tampered with by any hackers or by users, which ensures device protection and organization safety.
Author
Snehasis Pani is currently working as a JAMF Admin. He loves to help the community by sharing his knowledge on Apple Mac Devices Support. He is an M.Tech graduate in System Engineering.
