Hello, everyone! In this post, I will guide you through setting up the Extensible Single Sign-On authentication method on Intune. We will provide an overview of SSO and the Microsoft Enterprise SSO plugin and explain the steps to configure the Extensible Single Sign-On SSO Authentication for Apple macOS devices in Intune.
Our previous blog post, Types of macOS Enrolment Methods in Intune, covered enrolling MacBooks using various enrolment methods. We thoroughly examined personal and company-owned enrolment methods and provided detailed steps for each method.
As we know, the Microsoft Enterprise SSO plug-in has been officially available for Apple devices (iOS, iPadOS, and macOS). This plug-in supports all applications previously supported by Apple’s built-in enterprise SSO feature.
Also, the Extensible SSO Authentication configuration has been recently added as part of Microsoft Intune service release 2306 in June 2023. Currently, the Enterprise SSO plug-in is a built-in feature in the Intune Company Portal app on macOS devices and the Microsoft Authenticator app on iOS and iPadOS devices.
- Setup Microsoft Enterprise SSO plug-in for Apple macOS Devices using Intune
- Types of MacOS Enrolment Methods in Microsoft Intune
What is an SSO
Single sign-on (SSO) is an identification method that allows users to smoothly sign in to multiple apps or websites with a single credential over the browser. This feature streamlines the authentication process for users.
So whenever a user is prompted for a login, it skips the step by automatically signing in to applications or websites, which enhances the end-user experience by minimizing the usage of multiple varieties of usernames and passwords across various accounts and services.
Organizations widely started using SSOs as they are more secure. However, there are multiple benefits to using an SSO.
- Stronger passwords
- Better password policy enforcement
- Single point for enforcing password re-entry
- Increased Productivity
- Less Shadow IT Risks
Let us discuss the Microsoft Enterprise SSO plug-in for Apple devices features,
- It provides SSO for Azure AD accounts across all apps which support the Apple Enterprise SSO feature.
- It can be enabled by any mobile device management (MDM) solution and is supported in both device and user enrollment.
- It extends SSO to apps that don’t yet use the Microsoft Authentication Library (MSAL)
- It extends SSO to applications that use Authentication methods such as OAuth 2, OpenID Connect, and SAML.
- It is integrated with the Microsoft Authentication Library (MSAL), which provides a smooth end-user experience when the Microsoft Enterprise SSO plug-in is enabled.
Pre-requisite to Enable Microsoft Enterprise SSO
To enable the Microsoft Enterprise SSO plug-in for Apple Mac devices, ensure the below steps :
- Intune manages the device.
- macOS should run on Catalina v10.15 or higher.
- Intune Company portal App should be installed on the device to enable the Microsoft Enterprise SSO plug-in.
Configure Extensible SSO from Intune
To create a configuration profile, we must ensure the required access to the Intune Portal. Follow the steps mentioned below to create a configuration profile in Intune portal for macOS devices:
- Sign in to the Microsoft Intune admin center https://intune.microsoft.com/.
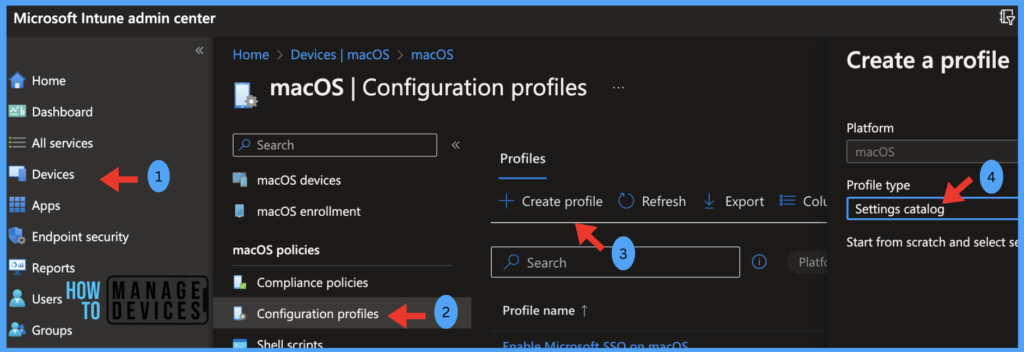
- On the left sidebar, select Devices > under Policy, select Configuration profiles.
- The list of existing configuration profiles will be reflected on the right side. To create a new profile, click on Create Profile.
- Select the correct categories for Profile creation,
- Platform – macOS
- Profile type – Settings Catalog
- Click on Create.
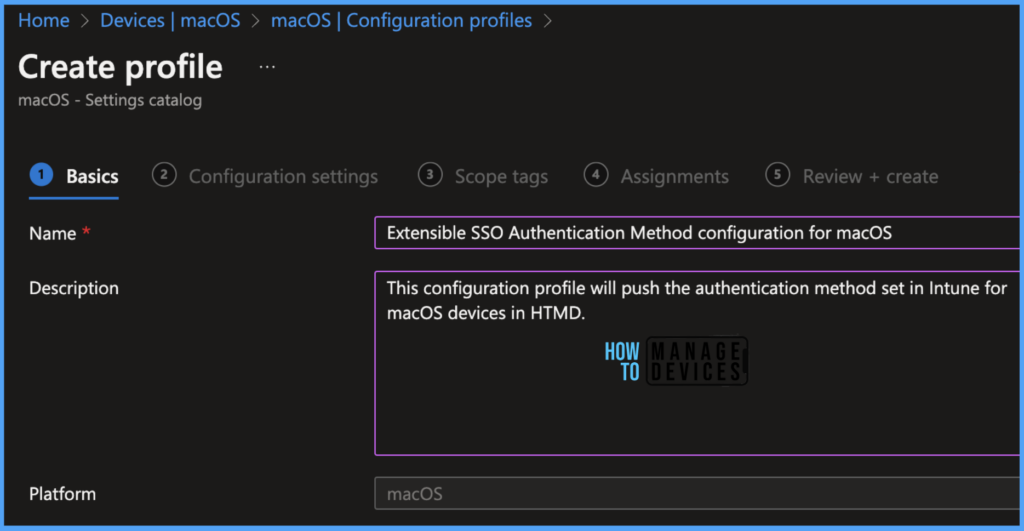
Once you click on Create button from the above page, Provide the Name and Description and click on Next.
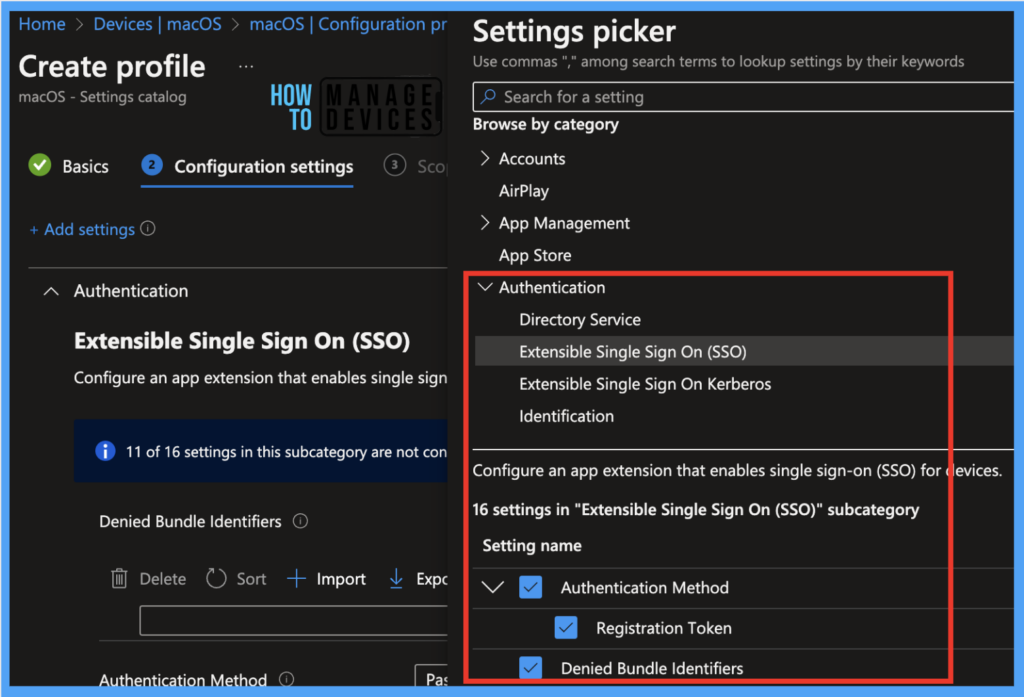
Under the Configuration settings tab, click on Add settings and browse by category Authentication > click on Extensible Single Sign On (SSO). Once it loads all the 16 features below. Select the below properties:
- Authentication Method: Platform SSO authentication only works with SSO Extension on macOS 13 or higher.
- Denied Bundle Identifiers: This macOS extension lists app bundle IDs which don’t support SSO for user authentication.
- Registration Token: This token enables silent registration with the Identity Provider on macOS 13 and later.
- Extension Identifier: The bundle identifier handles the app extension’s responsibility to process SO for the URLs.
- Type: Choose Redirect to use Microsoft Enterprise SSO in macOS.
Under the Authentication method, 2 types can be chosen. Password is the simple method, the same as configured for Windows devices, however, UserSecureEnclaveKey is the new method supported by Apple on Apple Silicon MacBooks or Intel-based MacBooks with T2 security chips.
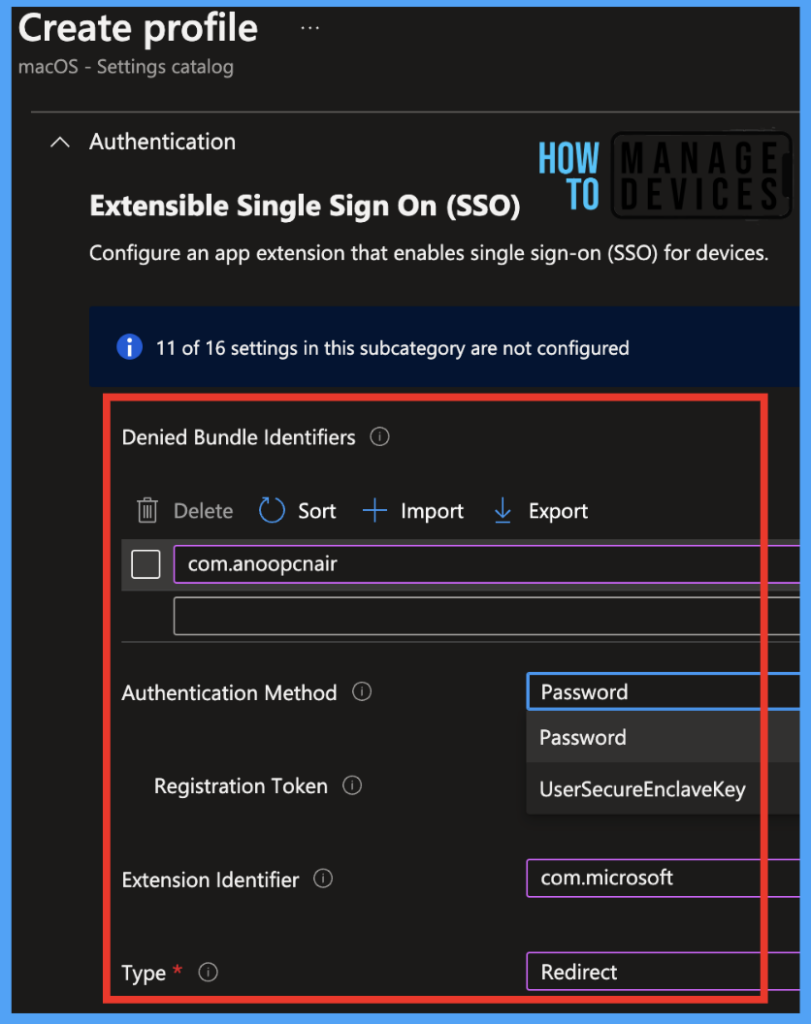
Under the Authentication method, we have provided the values shown in the screenshot below.
Denied bundle identifiers: com.anoopcnair
Authentication Method: Password
Extension Identifier: com.microsoft
Type: Redirect
Scope tags are filtering options provided in Intune to ease the admin jobs. In the scope tag section, you will get an option to configure scope tags for the policy. Click on Next.
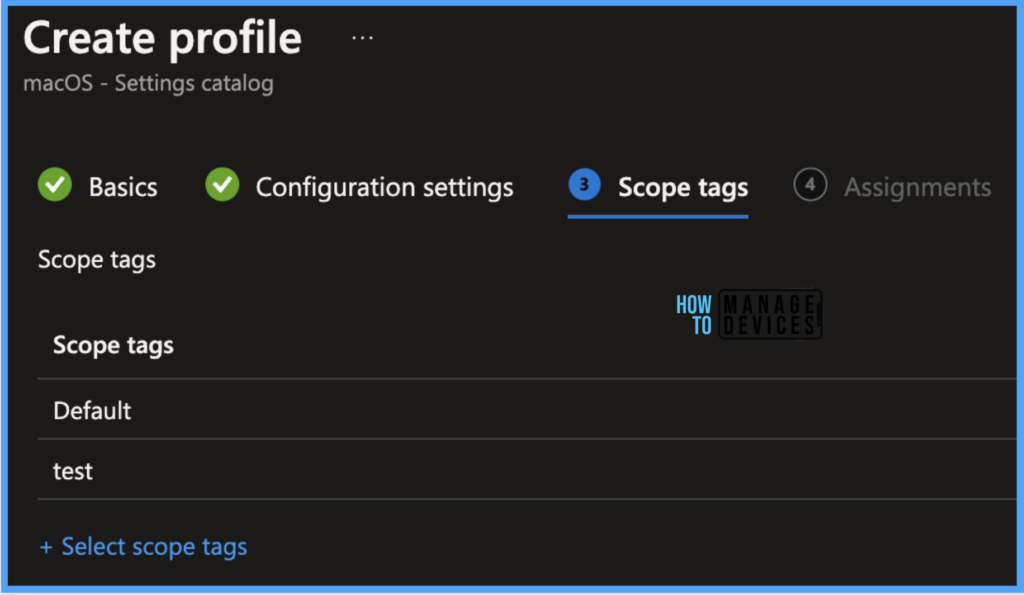
The assignment Group determines who has access to the profile by assigning groups of users to include and exclude. Select Assignments group (Included groups and Excluded groups) and click Next.
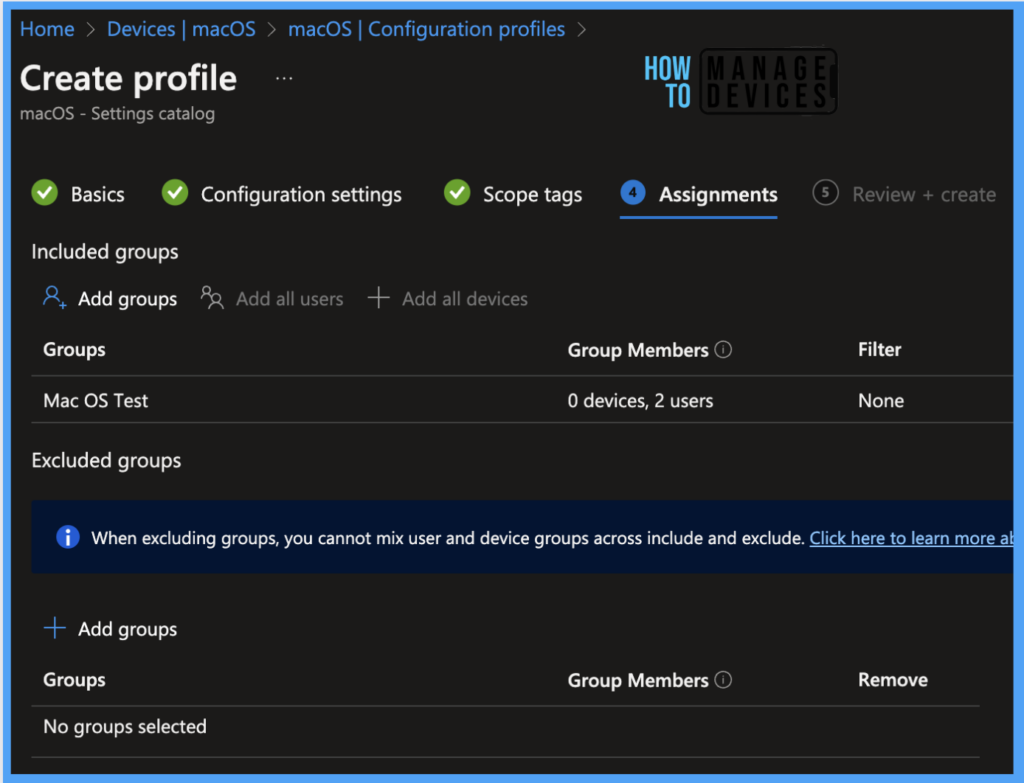
On the Review+create page, please review if any settings need to be changed, or else go ahead and click on Create button.
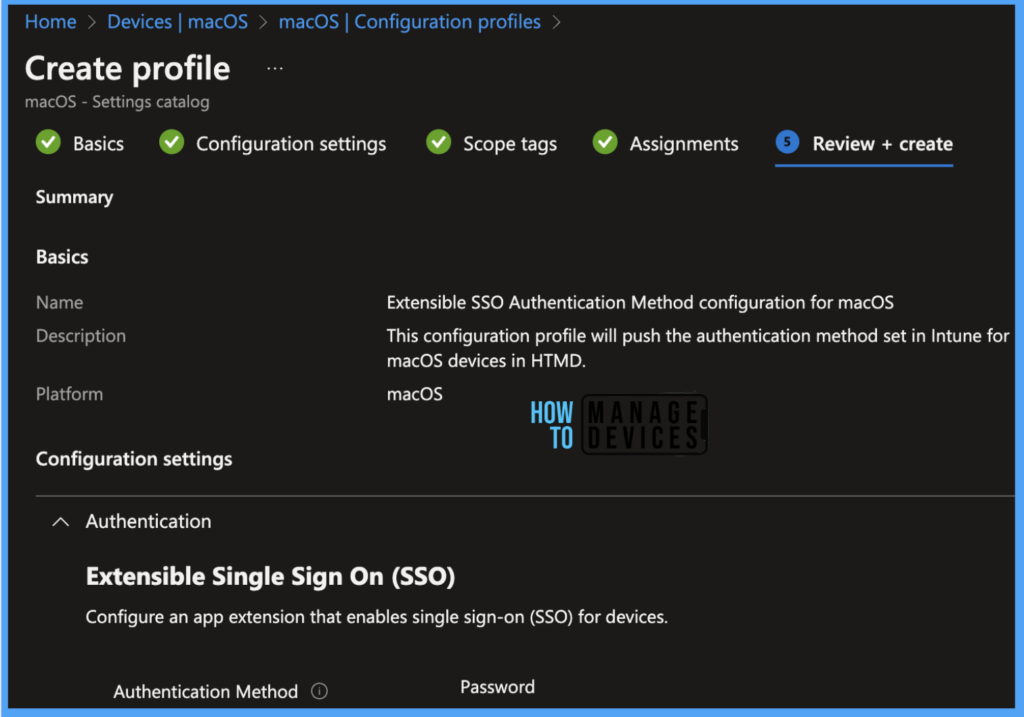
Once the Configuration Profile is created, it will take a few minutes to get pushed to all devices. Also, to view the deployment status on the list of devices, we can check by the below ways.
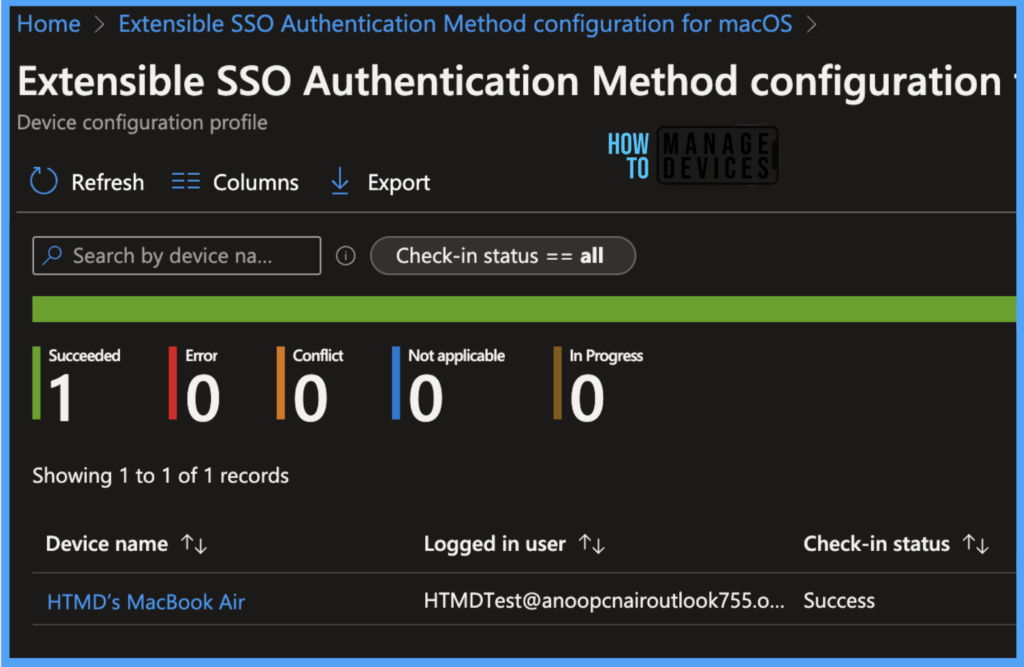
The report reflects successfully deploying pushed configuration profiles on assigned macOS devices. To see all the device statuses, Navigate to Devices > Configuration Profiles > Select the Profile, and you can find the list of devices under categories such as below.
- Succeeded
- Error
- Conflict
- Not Applicable
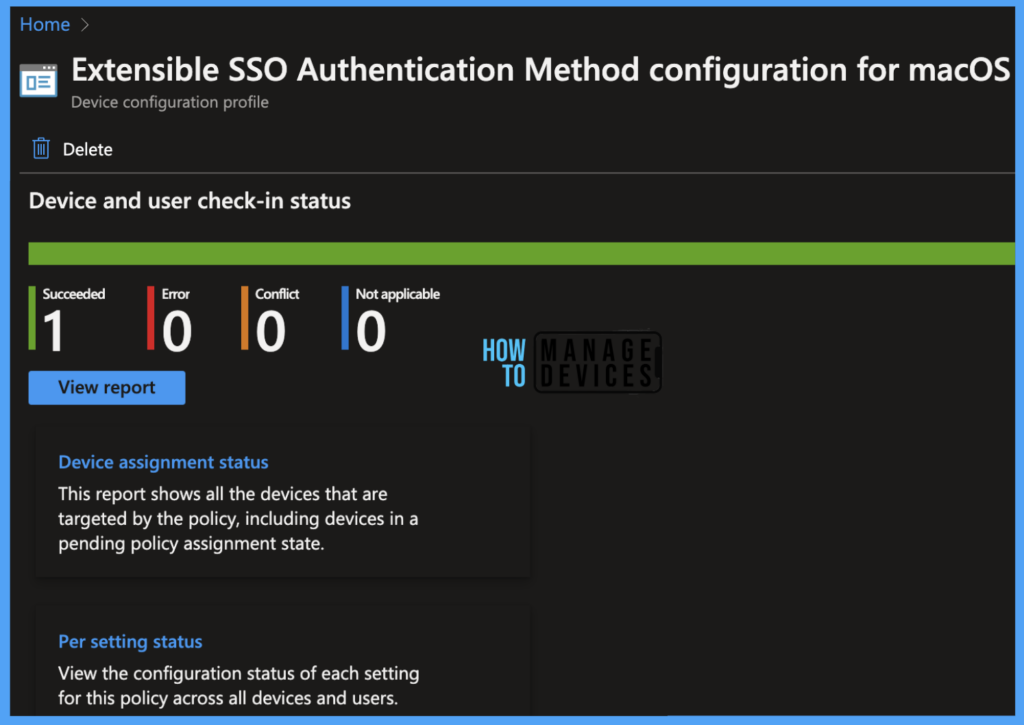
To see the report on the Intune console, you click on the view report button, you can see the list of devices along with their details below :
- Device name
- Logged in User
- Check-in Status
- Last check-in time
Also, we can view the two different types of reports, you can quickly check the update as devices/users check-in status reports.
Device assignment status, This report will show the list of targeted devices under the configuration profile, including devices in pending policy assignment status. To get the status, click on Generate Report button.
Per settings status, This report will show the configuration status of this policy across all devices and users.
Here’s how to export the Intune setting catalog Profile report from the Intune portal. You have two options to navigate to the compliance policies node either you can navigate to the Devices node or Endpoint Security, Intune Settings Catalog Profile Report.
- Enroll macOS in Intune with Step by Step Guide
- Configure macOS Compliance Policy in Intune for Devices
Results – Check on macOS
Once the Profile gets pushed to the list of client macOS devices as part of the assignment group, it may take a few minutes to reflect on the end user’s device. Launch the company portal app and run check status to get the policy manually pushed on the macOS device.
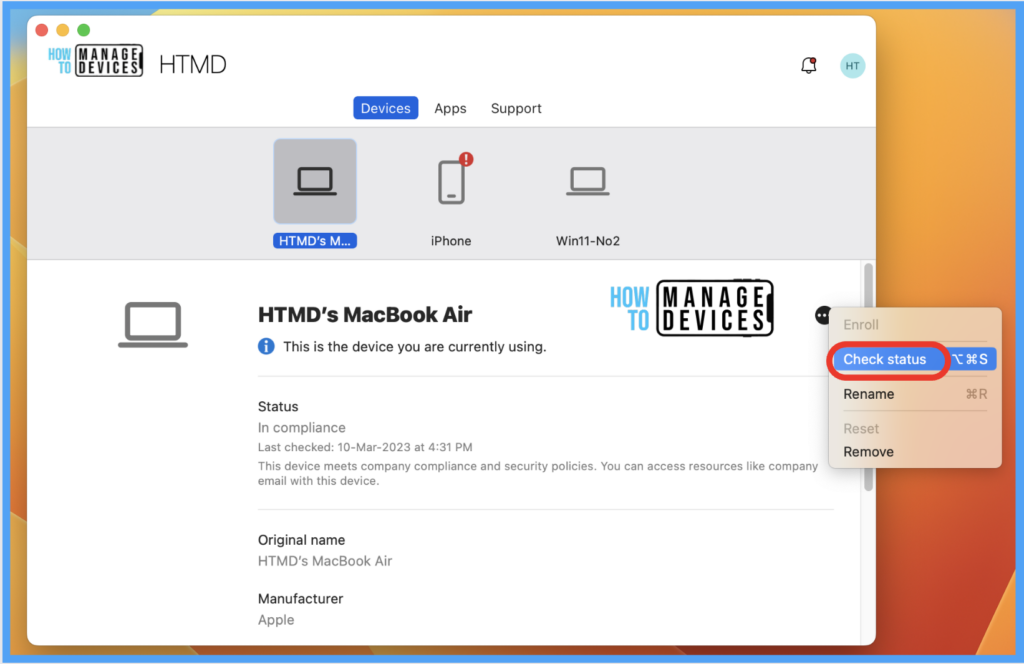
To check the profile status on the client device, Click on the Apple icon > Click on System Settings.
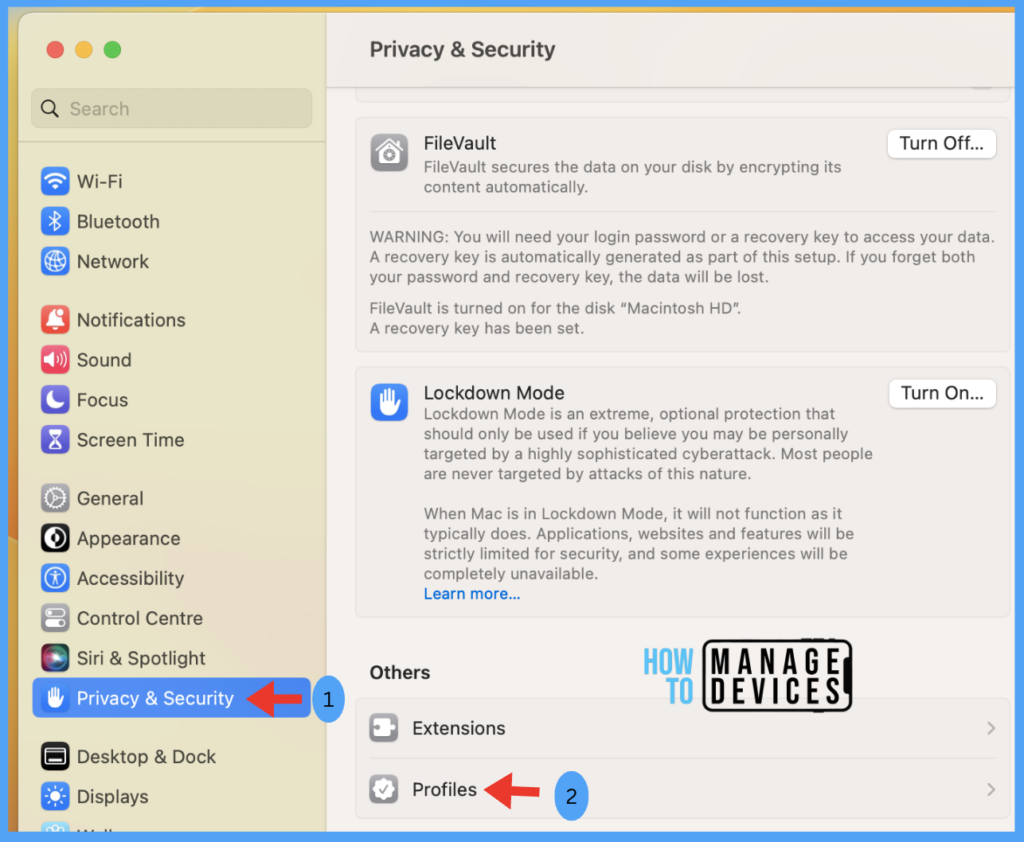
Go to Privacy & Security > Profiles > You can see the deployed profile on the device.
End User Experience
Now let us look at the end-user experience with the configured Microsoft Enterprise SSO plug-in. Below we have tried to share a sample video where I have tried to launch an Office website portal.office.com in Safari browser on a macOS device running on macOS Ventura, and it simply picks the required account.
Conclusion
As we know, organizations implement SSO on Windows devices to enhance the end-user experience, and now the Microsoft Enterprise SSO plug-in is also available on Apple macOS devices. And due to more enhancements, we have configured the authentication method as a configuration profile in Intune portal.
So IT Admins can configure all the features related to SSO directly from the Intune Admin Portal without any physical touch on the client devices.
Author
Snehasis Pani is currently working as a JAMF Admin. He loves to help the community by sharing his knowledge on Apple Mac Devices Support. He is an M.Tech graduate in System Engineering.

Thank you for sharing. Could you please confirm what you added in for the Registration Token? Entering the same values in the other fields (dummy bundle ID in the denied bundle identifier) did not deliver the profile to the device.
What goes in Registration Token? Would {{DEVICEREGISTRATION}} work?
I have an issue with this!
After complete the setup may of my end users are asked to log in many times at day.
Would please give me some ideas that what could be happening?