This post will take you through the creation of the Intune Audit Security State Change Policy. We’ll make use of Intune’s Settings Catalog to enforce this policy. Configuration Profiles of Intune will be used in performing this task.
Audit Security, State Change Policy configuration, permits the auditing of events arising from alterations in the security status of the computer, encompassing events such as the startup and shutdown of the computer, changes to the system time, and the recovery of the system from CrashOnAuditFail.
The latter is logged following a system restart when the security event log reaches full capacity and the CrashOnAuditFail registry entry is configured. The policy captures events related to the initiation and termination of the computer.
The mention of “CrashOnAuditFail” suggests that in situations where the security event log is full, the system might experience a crash, and this event is logged upon recovery. The configuration of the “CrashOnAuditFail” registry entry seems to play a role in determining how the system behaves in response to a full security event log.

Create Intune Audit Security State Change Policy
To Create Intune Audit Security State Change Policy, follow the steps stated below:
- Sign in to the Intune Admin Center portal https://intune.microsoft.com/.
- Select Devices > Windows > Configuration profiles > Create a profile.
In Create Profile, I select Windows 10 and later in Platform and select Profile Type as Settings catalog. Click on the Create button.
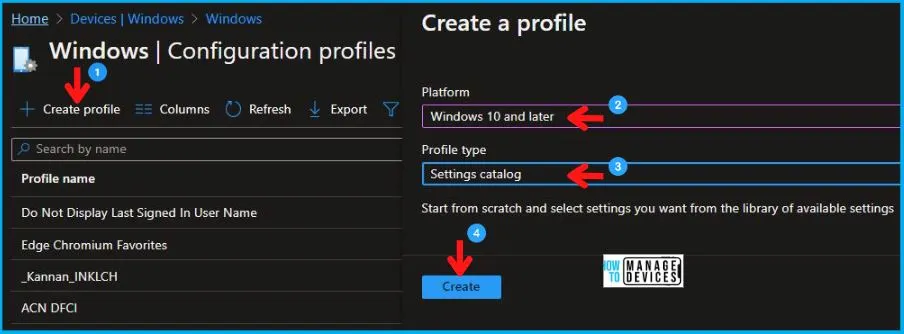
On the Basics tab pane, I provide a name for the policy as “Audit Security State Change Policy.”
- Optionally, if you want, you can enter a policy description and proceed by selecting “Next“.
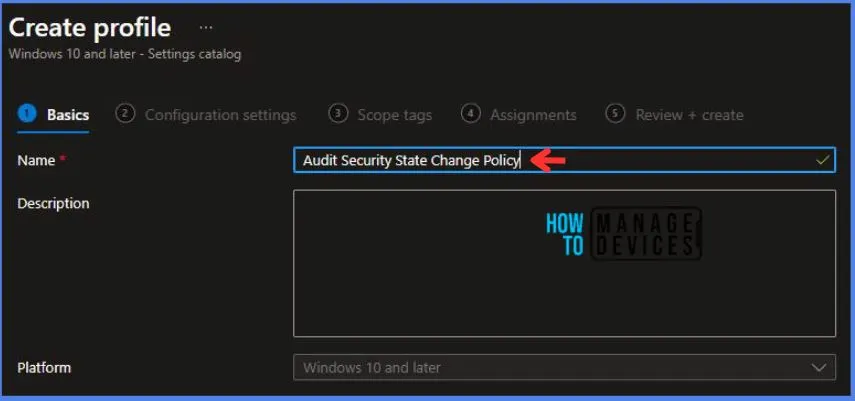
Now in Configuration Settings, Click Add Settings to browse or search the catalog for the settings I want to configure.
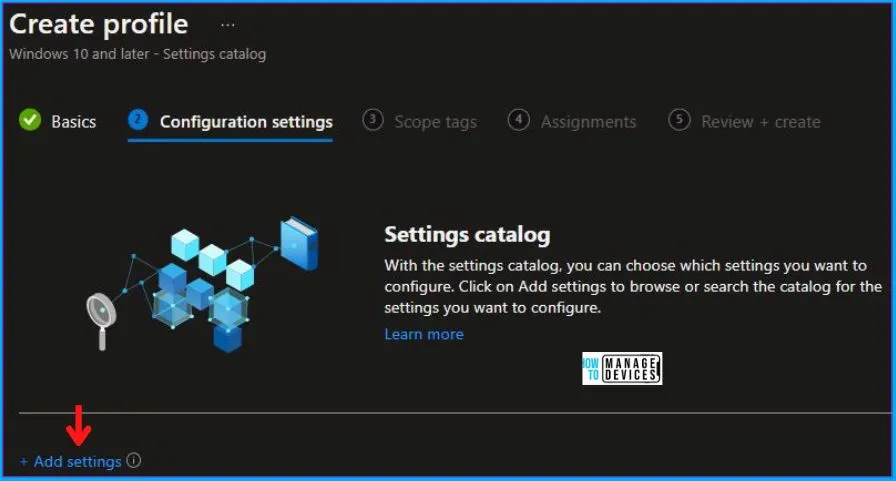
In the Settings Picker windows. I searched for the keyword Audit. I found the category Auditing and selected this.
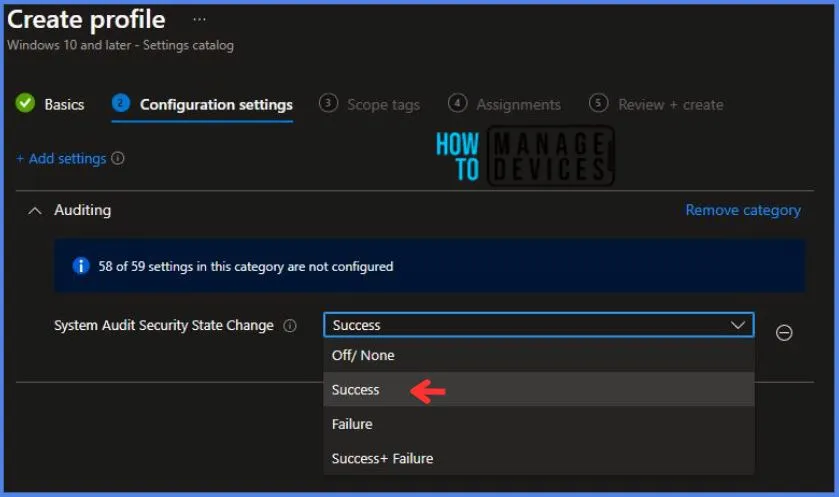
- When I select that option as stated above, I see the sub-category System Audit Security State Change. After selecting that, click the cross mark at the right-hand corner, as shown below.
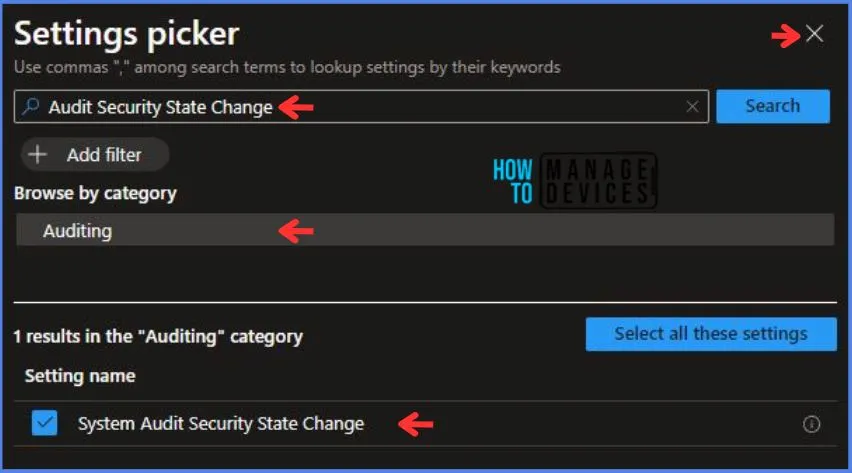
Here in System Audit I Psec Driver, there are multiple options to select, which are:
- Off/ None
- Success
- Failure
- Success + Failure
Here I choose Success for this policy.
Using Scope tags, you can assign a tag to filter the profile to specific IT groups. One can add scope tags (if required). More details on Intune Scope Tags Implementation Guide.
- Click Next to continue.
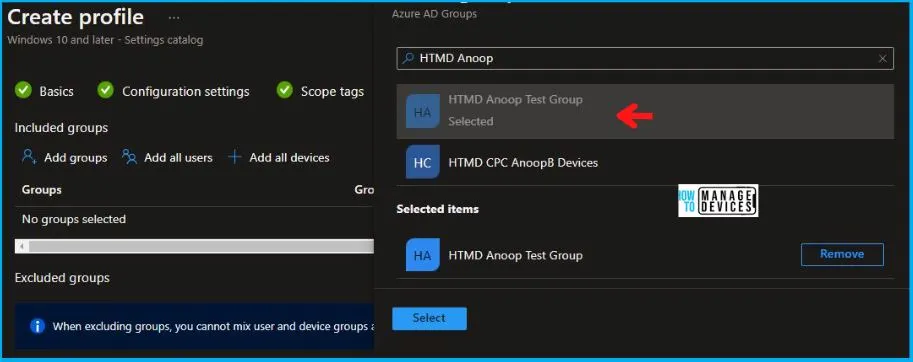
Now in Assignments, in Included Groups, you need to click on Add Groups and choose Select Groups to include one or more groups. Click Next to continue.
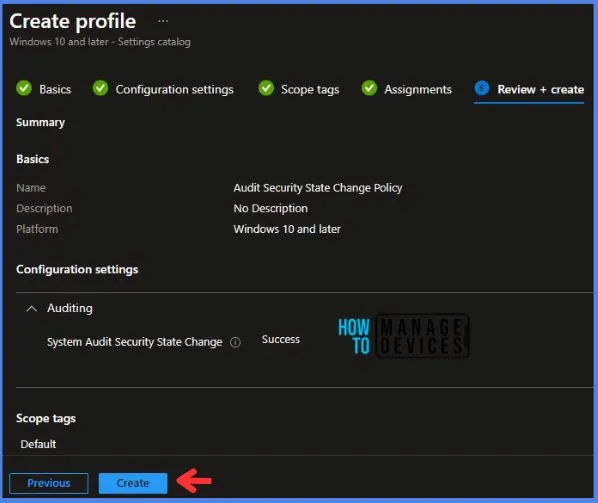
In the Review + Create tab, I review settings. After clicking on Create, changes are saved, and the profile is assigned.
After successfully creating the “Audit Security State Change Policy,” a notification will appear in the top right-hand corner confirming the action. You can also verify the policy’s existence by navigating to the Configuration Profiles list, where it will be prominently displayed.
Your groups will receive your profile settings when the devices check in with the Intune service. The Policy applies to the device.
Intune Report for Audit Security State Change Policy
From the Intune Portal, you can view the Intune settings catalog profile report, which provides an overview of device configuration policies and deployment status.
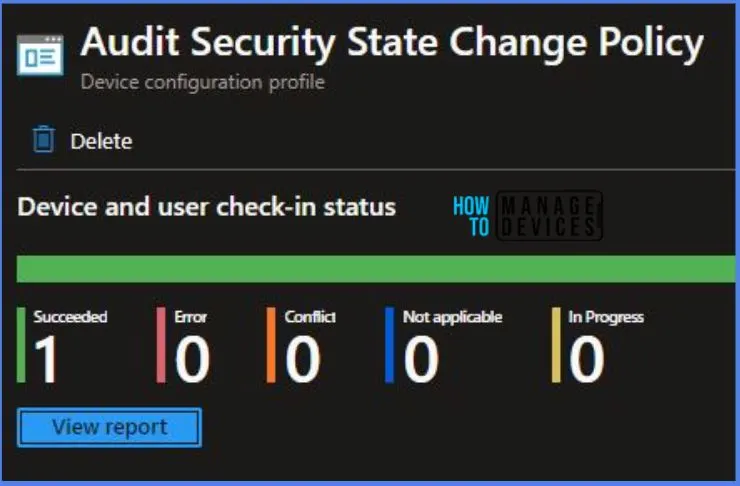
To track the assignment of the policy, you need to select the relevant policy from the Configuration Profiles list, which is the Audit Security State Change Policy. Then, you can review the device and user check-in status to determine whether the policy has been successfully applied.
- If you require more detailed information, you can click on “View Report” to access additional insights.
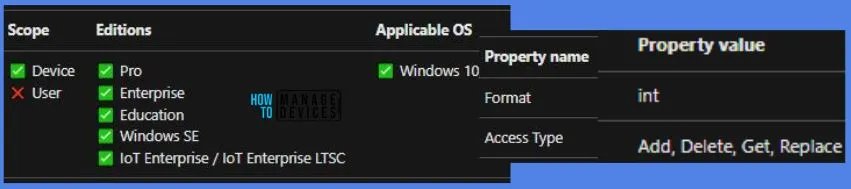
Windows CSP Details System_AuditSecurityStateChange
We will see Windows CSP Details for this Policy setting System_AuditSecurityStateChange. The policy distinguishes between different types of audit events, specifically “Success” and “Failure” audits. Success audits likely indicate successful occurrences of the audited events, while failure audits would point to unsuccessful attempts or issues.
Configuring this policy setting results in the generation of audit events for the specified security-related operations. Failure to configure it means that no audit events will be produced for these operations.
CSP URI – ./Device/Vendor/MSFT/Policy/Config/Audit/System_AuditSecurityStateChange
Registry Verification – Audit Security State Change Policy
To cross-check whether the policy is implemented on the target device or not, we need to access the registry settings that hold the group policy configurations on a specific computer. To accomplish this, you can execute “REGEDIT.exe” on the target computer and navigate to the precise registry path mentioned below, where these settings are stored.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\providers\5B88AEF1-09E8-43BB-B144-7254ACBBDF3E\default\Device\Audit
When you navigate the above path in the Registry Editor, you will find the registry key named
