Here, this post will help you in the deployment of the Turn Off Shell Protocol Protected Mode Policy using Intune. We’ll make use of Intune’s Settings Catalog to install this policy. We are using configuration Profiles of Intune to deploy the Turn Off Shell Protocol Protected Mode Policy Using Intune.
This policy setting enables the configuration of the functionality level for the shell protocol. When utilizing the full functionality, applications have the capability to open folders and launch files. Alternatively, the protected mode restricts the functionality of the protocol, limiting applications to open only a predefined set of folders.
In this mode, applications cannot open files using the protocol, enhancing the security of Windows. It is recommended to keep the protocol in the protected mode to bolster Windows security. Enabling this policy setting grants full functionality to the protocol, allowing the opening of both folders and files.
Conversely, disabling the policy setting or leaving it unconfigured maintains the protected mode, where applications can only open a restricted set of folders. Restricting access to a limited set of files and folders minimizes the system’s potential attack surface.

- Create Intune Turn Off Heap Termination on Corruption Policy
- Prevent the Use of Security Questions for Local Accounts using Intune Policy
Turn Off Shell Protocol Protected Mode Policy Using Intune
To create a Turn Off Shell Protocol Protected Mode Policy, follow the steps stated below:
- Sign in to the Intune Admin Center portal https://intune.microsoft.com/.
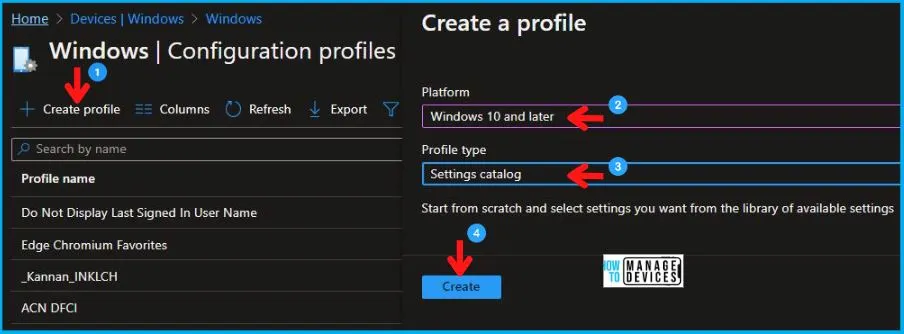
- Select Devices > Windows > Configuration profiles > Create a profile.
In Create Profile, I select Windows 10 and later in Platform and select Profile Type as Settings catalog. Click on the Create button.
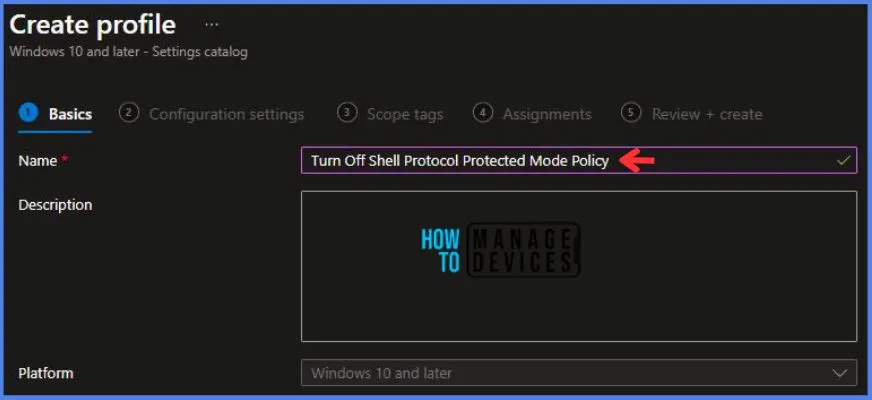
On the Basics tab pane, I provide a name for the policy “Turn Off Shell Protocol Protected Mode Policy.”
- Optionally, if you want, you can enter a policy description and proceed by selecting “Next”
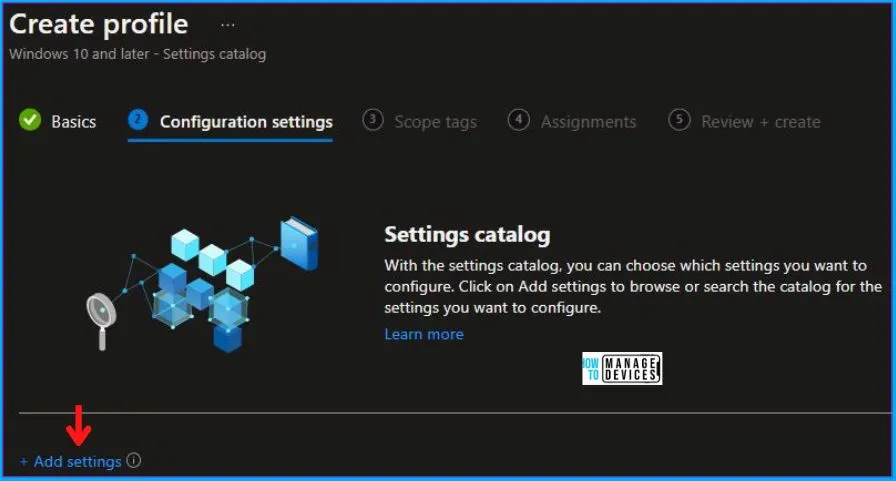
Now in Configuration Settings, Click Add Settings to browse or search the catalog for the settings I want to configure.
In the Settings Picker windows, I searched for the keyword File Explorer. I found the category Administrative Templates\System\File Explorer and selected this.
- When I select that option as stated above, I see the sub-category Turn off shell protocol protected mode. After selecting that, click the cross mark at the right-hand corner, as shown below.
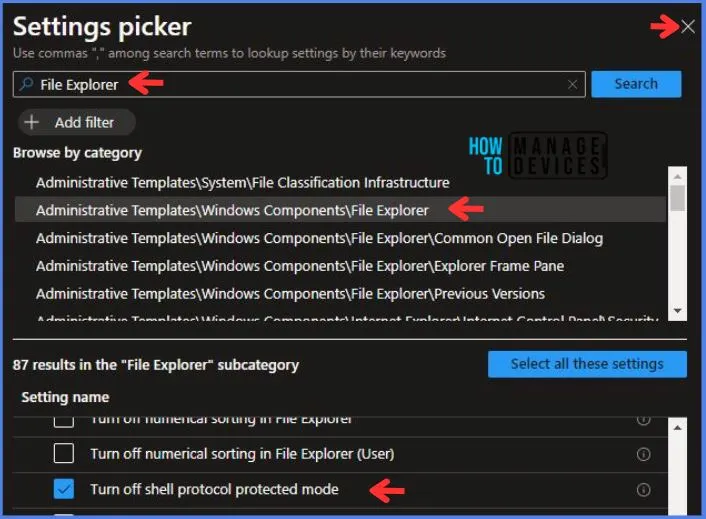
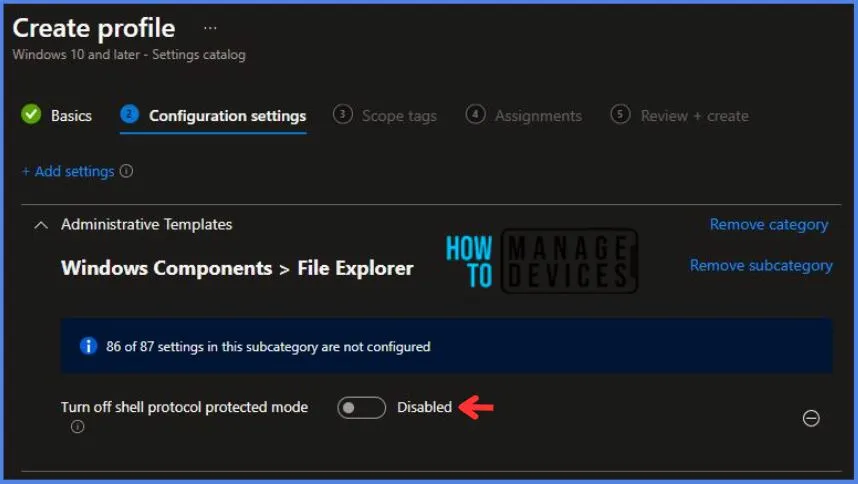
Here in Administrative Templates, I have Disabled the Turn off shell protocol protected mode.
Using Scope tags, you can assign a tag to filter the profile to specific IT groups. One can add scope tags (if required). More details on Intune Scope Tags Implementation Guide.
- Click Next to continue.
Now in Assignments, in Included Groups, you need to click on Add Groups and choose Select Groups to include one or more groups. Click Next to continue.
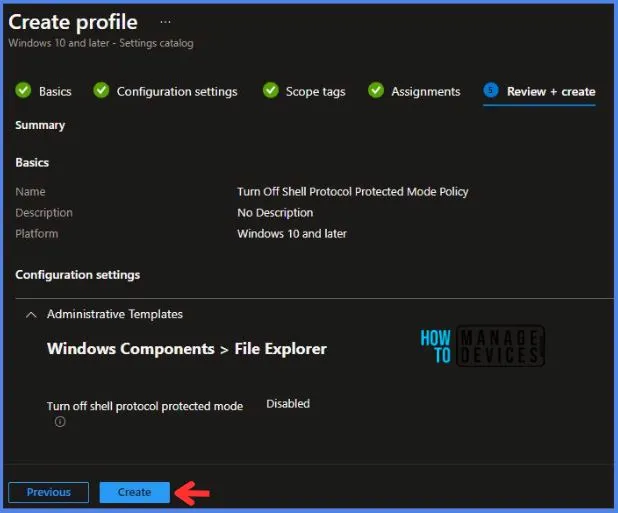
In the Review + Create tab, I review settings. After clicking on Create, changes are saved, and the profile is assigned.
After successfully creating the “Turn Off Shell Protocol Protected Mode Policy,” a notification will appear in the top right-hand corner confirming the action. You can also verify the policy’s existence by navigating to the Configuration Profiles list, where it will be prominently displayed.
Your groups will receive your profile settings when the devices check in with the Intune service. The Policy applies to the device.
Intune Report for Turn Off Shell Protocol Protected Mode Policy
From the Intune Portal, you can view the Intune settings catalog profile report, which provides an overview of device configuration policies and deployment status.
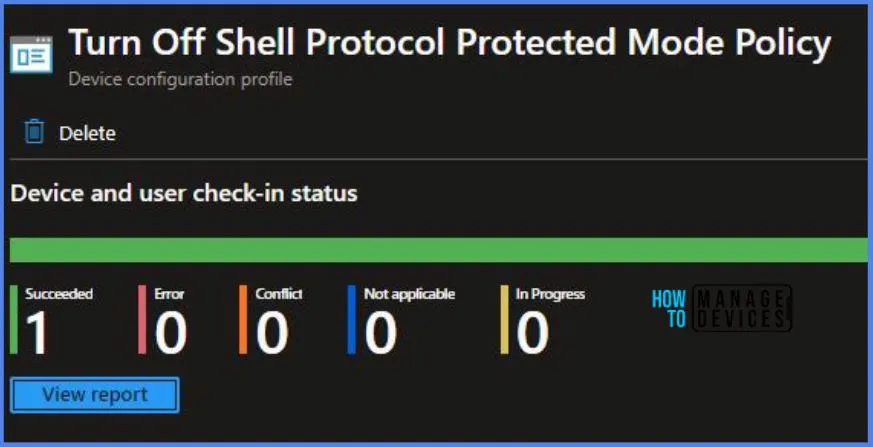
To track the assignment of the policy, you need to select the relevant policy from the Configuration Profiles list, which is the Turn Off Shell Protocol Protected Mode Policy. Then, you can review the device and user check-in status to determine whether the policy has been successfully applied.
- If you require more detailed information, you can click on “View Report” to access additional insights.
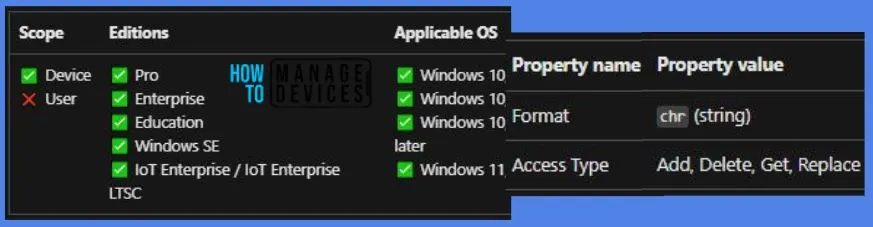
Windows CSP Details ShellProtocolProtectedModeTitle_2
We will see Windows CSP Details for this Policy setting ShellProtocolProtectedModeTitle_2. The configuration of the shell protocol’s functionality is a critical aspect of system security. The choice between full functionality and protected mode should be made thoughtfully, considering the operational needs and security requirements of the organization. It reflects a proactive approach to managing potential security risks within the Windows environment.
CSP URI – ./Device/Vendor/MSFT/Policy/Config/ADMX_WindowsExplorer/ShellProtocolProtectedModeTitle_2
Intune MDM Event Log – Turn Off Shell Protocol Protected Mode Policy
You can leverage event IDs 813 and 814 to verify the successful implementation of String or integer policies for the Turn Off Shell Protocol Protected Mode Policy Policy on Windows 10 or 11 devices through Intune.
These event IDs provide valuable insights into the Turn Off Shell Protocol Protected Mode Policy’s application status and the specific value assigned to the policy on those devices. In the case of this particular policy, the value is String and is linked to the event ID 814.
By analyzing these event IDs, you can clearly understand the policy’s application status and the corresponding value associated with it on the devices in question.
To confirm this, you can check the Event log path – Applications and Services Logs – Microsoft – Windows – Devicemanagement-Enterprise-Diagnostics-Provider – Admin.
MDM PolicyManager: Set policy string, Policy: (
