RDP Port 3389 is Disabled by Default for All Newly Provisioned Windows 365 Cloud PCs! When you create a new Windows 365 Cloud PC, the Remote Desktop Protocol (RDP) port (Port 3389) is turned off by default.
If you need to use Remote Desktop, you must manually (better via Intune) enable the port in specific cases. Port 3389 is used for Remote Desktop connections. To keep new Windows 365 Cloud PCs secure, this port is turned off by default.
Microsoft advises keeping it closed to protect your PCs from potential security risks. However, if you need to use Remote Desktop and your Cloud PCs are on your company’s Azure network, you can open the port with specific settings.
This post explains why Remote Desktop Port 3389 is disabled by default for all newly provisioned Windows 365 Cloud PCs. More details are described below.
Table of Contents
What is Port 3389?
Port 3389 is the default network port used by the Remote Desktop Protocol (RDP), which allows users to connect remotely to another computer or server over a network. More details RDP Remote Desktop Protocol Investments to Improve Windows 365 and AVD Experience.
RDP Port 3389 is Disabled by Default for All Newly Provisioned Windows 365 Cloud PCs
Port 3389 is disabled by default for all newly provisioned Cloud PCs. Microsoft confirms this settings change is to enhance the security of Windows 365 Cloud OC.
If you need to open Port 3389 for Remote Desktop access on Windows 365 Cloud PCs that are reconfigured using the Azure Network Connection (ANC) deployment option, you have two main choices.
| Azure Network Connection (ANC) Deployment Option |
|---|
| Windows 365 Security Baselines |
| Create a custom Firewall rule in Microsoft Intune |
NOTE! – These options aren’t applicable for customers using a Microsoft-hosted network for Windows 365 Cloud PCs.
- How to Create Cloud PC Maintenance Windows using Microsoft Intune
- New 7 Windows 365 Graph API Queries for CloudPC Management
- Troubleshoot Windows 365 Cloud PC Connectivity Check
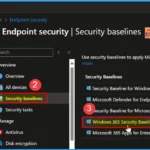
Windows 365 Security Baselines
You can easily use Windows 365 Security Baselines to manage port 3389 for Windows 365 Cloud PCs. These baselines offer a range of tools and configurations designed to enhance security. To configure port 3389, follow these steps.
- Modify your Firewall settings to allow traffic through port 3389.
- Setting the Default Inbound Action for Public Profile to Allow
- These changes help you to ensure that port 3389 is appropriately configured to meet your organization’s operational needs.
- Sign in to the Microsoft Intune admin center > Select Endpoint Security > Security Baselines.
- The Security Baseline shows the Windows 365 Security Baseline
NOTE! – After selecting the Windows 365 Security Baseline, you must review all the settings required for this scenario. Select the appropriate configurations from the baseline and deploy them to all the relevant Cloud PCS.
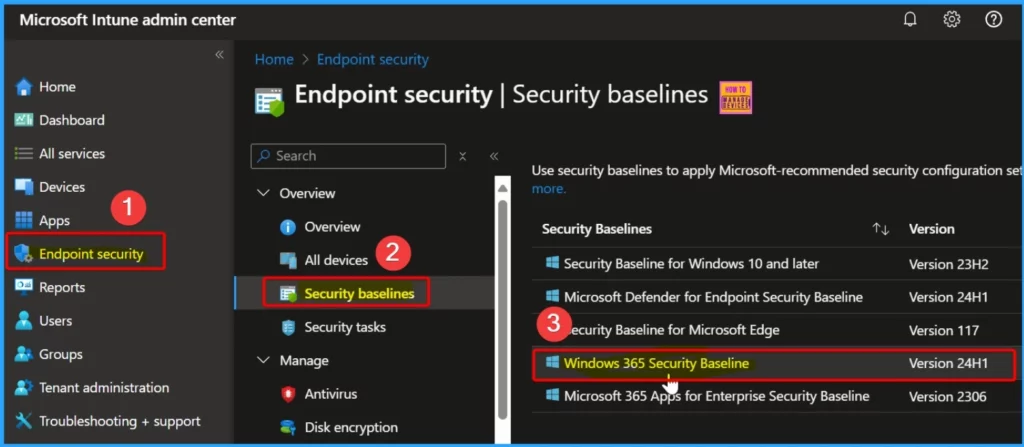
Create a Custom Firewall Rule in Microsoft Intune
In Intune, you can use the Endpoint Security Firewall policy to configure the built-in firewall for Windows devices. While similar settings can be configured through Endpoint Protection profiles under device configuration, those profiles include additional non-firewall settings, which may complicate the process if you only want to focus on firewall configurations.
More Details – 4 New Intune Firewall Logging Configuration Policies
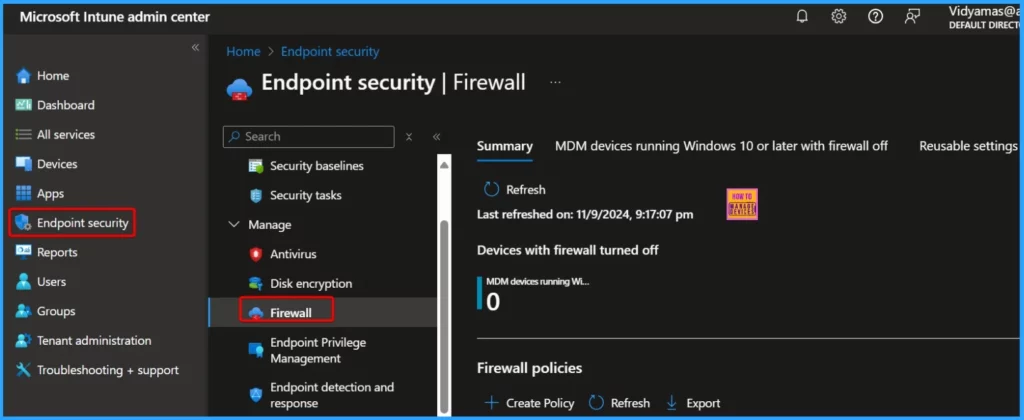
You can easily set up a custom Firewall rule in Microsoft Intune to manage Port 3389 for Windows 365 Cloud PCs. In Microsoft Intune, you can create a custom firewall rule to allow inbound traffic on port 3389, which connects remote desktops to Windows 365 Cloud PCs. This involves setting up a rule that specifies the following.
- Port number: 3389
- Protocol: TCP
- IP restrictions: Limit access to specific IP addresses or networks to ensure only authorized users can connect.
By creating this custom rule, you can easily control who can access port 3389 while maintaining security for your Cloud PCs.
- Azure Monitor Agent and Remote Session Lock Configuration Windows 365 Cloud PC August 2024 Update
- Windows365 Enterprise Introduces Disk Storage Resizing for Cloud PCs with Step-Up Licenses
- Power Of Dark Mode On Windows 365 Cloud PC Web Portal
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here. HTMD WhatsApp.
- Windows 365 Cloud PC 2309 September Service Release New Features Improvements
- Azure Monitor Agent and Remote Session Lock Configuration Windows 365 Cloud PC August 2024 Update
Author
Anoop C Nair has been Microsoft MVP from 2015 onwards for 10 consecutive years! He is a Workplace Solution Architect with more than 22+ years of experience in Workplace technologies. He is also a Blogger, Speaker, and Local User Group Community leader. His primary focus is on Device Management technologies like SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.

The Windows 365 Security Baselines solution seems to give some pretty bad advice as, its suggesting to Allow Default Inbound Action for Public Profile. Doesnt seem a very good idea to me. Plus, I tested this, and it doesnt get rid of the 2 Firewall policies that come with Windows 365 to block 3389.
The only way I could do this, was to write some powershell to delete the 2 Windows365 policies.
@R3trogam3r can you share your PS commands to do this? We’re battling this and it’s not going well.