Exciting News! Secure Microsoft 365 Office Apps using Intune Security Policies. Microsoft released a new security baseline that helps you to manage security configurations for M365 Office Apps. This is the new Security Policy that the Microsoft Intune team added as part of Intune 2305 release.
This new security baseline uses updated templates and experience that helps the unified settings platform featured in the Intune settings catalog. The new Intune security baseline format ensures consistency in the representation of settings, aligning them with the offerings present in the Intune settings catalog.
This alignment helps resolve previous challenges or issues for setting names and implementations for settings that could create conflicts. The new format introduces notable enhancements to the reporting capabilities for baselines within the Intune admin center.
These improvements provide a more robust and comprehensive reporting experience. The M365 Office Apps baseline offers rapidly deployed configurations to your Office Apps that meet the security recommendations of the Office and security teams at Microsoft. If you want to learn more about Intune security, We already have a video – Intune Security Baseline Decoded Easiest option to set up security policies for your organization.
What is Intune Security Policy?
Security baselines consist of pre-configured sets of Windows settings designed to facilitate the implementation of recommended configurations by the relevant security teams.
1. These baselines provide a convenient way to apply a standardized and trusted configuration that aligns with best practices for security.
2. By leveraging these pre-defined baselines, you can efficiently establish a robust and secure system environment, minimizing vulnerabilities and adhering to the guidance provided by esteemed security experts.
Video Office 365 App Security Policy Settings
Let’s check the following video to get more details about Office 365 App Security Policy Settings Recommended by Microsoft | Implement Policies using Intune.
Windows CSP Details Secure Microsoft 356 Office Apps using Intune Security Policies
Windows CSP Details Secure Microsoft 356 Office Apps using Intune Security Policies.
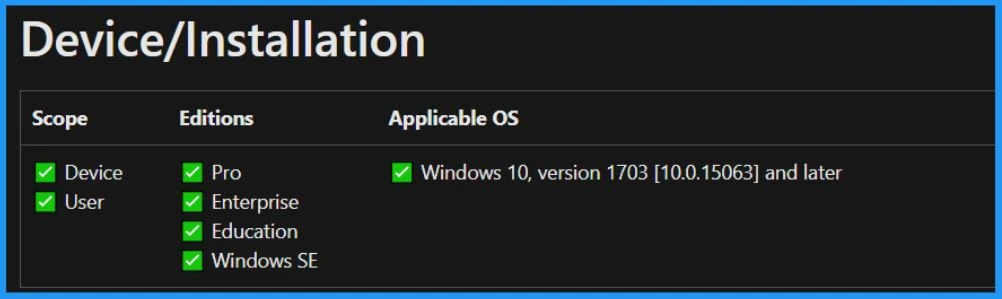
The Office configuration service provider (CSP) facilitates the installation of Microsoft Office clients on devices using the Office Deployment Tool (ODT). By leveraging the CSP, administrators can efficiently deploy and configure the Office client across various organizational devices.
CSP URI – ./Device/Vendor/MSFT/Office/Installation
Microsoft 356 Office Apps using Intune Security Policies
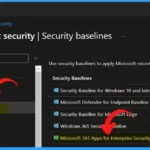
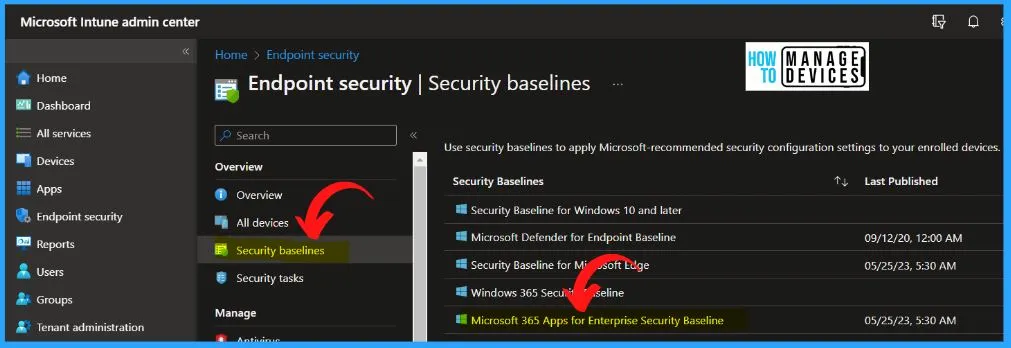
Sign in to the Microsoft Intune admin center with your Intune administrator account. On the left side of Intune admin center, select endpoint security. Select Security Baselines from Endpoint Security.
If you click on the security baseline, that will take you to where you can create security baseline profiles using the templates that Microsoft recommends.
- Here in the below window, you can see the 5 Security Baseline products
- And it also shows the last published dates
- Select Microsoft 365 Apps for Enterprise Security Baseline from the below window.
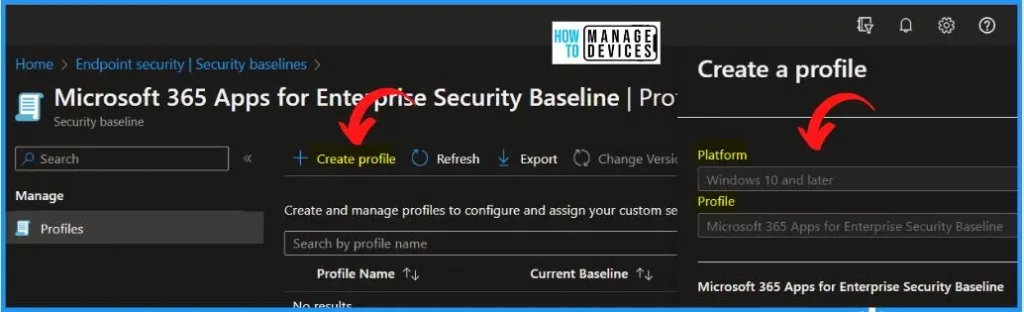
The below window helps you create a new Microsoft 365 Apps for Enterprise Security Baseline available in Intune portal, which will be updated on the 25th of May, 2023. Select Create Profile from the profiles. Under the Create a profile window, select the following.
- Platform – Windows 10 and later
- Profile – Microsoft 365 Apps for Enterprise Security Baseline
- Click Create
Under the Basic tab, enter the name and description as Microsoft 365 Apps for Enterprise Security Baseline and also select the platform as Windows 10 and later. Select the Next button from the Basic tab.
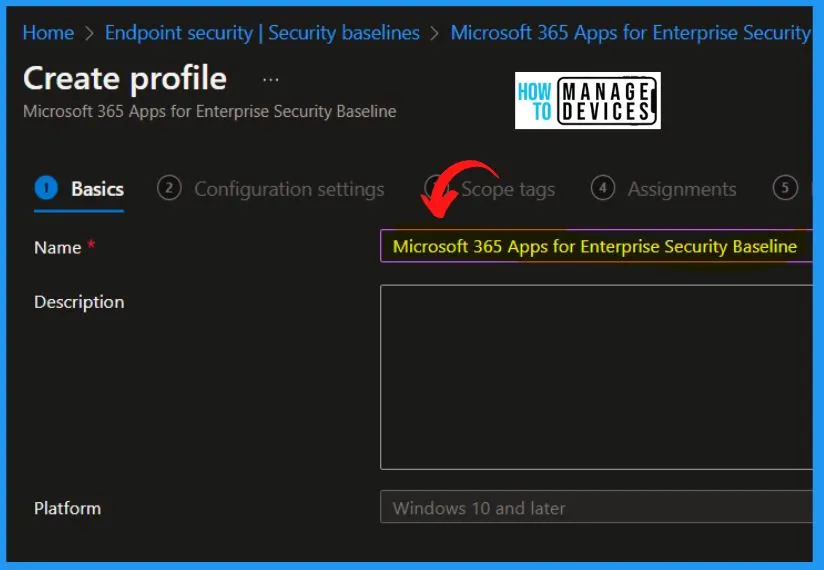
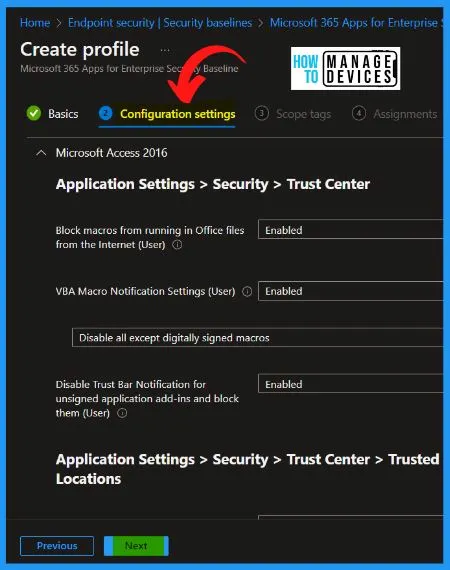
The following tables give you the exact details of the Microsoft 365 Office Apps security baseline template as per Microsoft Engineering Teams recommendations. These recommendations might not match with CIS recommendations for Office 365 Apps
Microsoft Access 2016 Intune Security Policies
Let’s check the following table to get more details about the recommendation from the Microsoft engineering team on Microsoft Access 2016 Intune Security Policies.
| Microsoft Access 2016 Settings Options | Enabled/Disabled |
|---|---|
| Block macros from running in Office files from the Internet (User) | enabled |
| VBA Macro Notification Settings (User) | Enabled |
| Disable all except digitally signed macros | |
| Disable Trust Bar Notification for unsigned application add-ins and block them (User) | Enabled |
| Allow Trusted Locations on the network (User) | Disabled |
Microsoft Excel 2016 Intune Security Policies
The following table is to get more details about the recommendation from the Microsoft engineering team on Microsoft Excel 2016 Intune Security Policies.
| Microsoft Excel 2016 Settings Options | Enabled/Disabled |
|---|---|
| Do not show data extraction options when opening corrupt workbooks (User) | Enabled |
| Ask to update automatic links (User) | Enabled |
| Load pictures from Web pages not created in Excel (User) | Disabled |
| Disable AutoRepublish (User) | Enabled |
| Do not show AutoRepublish warning alert (User) | Disabled |
| Force file extension to match file type (User) | Enabled |
| Scan encrypted macros in Excel Open XML workbooks (User) | Enabled |
| Turn off file validation (User) | Disabled |
| WEBSERVICE Function Notification Settings (User) | Enabled |
| Block macros from running in Office files from the Internet (User) | Enabled |
| Prevent Excel from running XLM macros (User) | Enabled |
| Require that application add-ins are signed by Trusted Publisher (User) | Enabled |
| Disable Trust Bar Notification for unsigned application add-ins and block them (User) | Enabled |
| VBA Macro Notification Settings (User) | Enabled |
| Always prevent untrusted Microsoft Query files from opening (User) | Enabled |
| Don’t allow Dynamic Data Exchange (DDE) server launch in Excel (User) | Enabled |
| Don’t allow Dynamic Data Exchange (DDE) server lookup in Excel (User) | Enabled |
| dBase III / IV files (User) | Enabled |
| Dif and Sylk files (User) | Enabled |
| Excel 2 macrosheets and add-in files (User) | Enabled |
| Excel 2 worksheets (User) | Enabled |
| Excel 3 macrosheets and add-in files (User) | Enabled |
| Excel 3 worksheets (User) | Enabled |
| Excel 4 macrosheets and add-in files (User) | Enabled |
| Excel 4 workbooks (User) | Enabled |
| Excel 4 worksheets (User) | Enabled |
| Excel 95 workbooks (User) | Enabled |
| Excel 95-97 workbooks and templates (User) | Enabled |
| Excel 97-2003 workbooks and templates (User) | Enabled |
| Set default file block behavior (User) | Enabled |
| Web pages and Excel 2003 XML spreadsheets (User) | Enabled |
| Always open untrusted database files in Protected View (User) | Enabled |
| Do not open files from the Internet zone in Protected View (User) | Disabled |
| Do not open files in unsafe locations in Protected View (User) | Disabled |
| Set document behavior if file validation fails (User) | Enabled |
| Checked: Allow edit. Unchecked: Do not allow edit. (User) | False |
| Turn off Protected View for attachments opened from Outlook (User) | Disabled |
| Allow Trusted Locations on the network (User) | Disabled |
Microsoft Lync Feature Policies (Deprecated?)
Let’s check the following table to get more details about the recommendation from the Microsoft engineering team on Microsoft Lync Intune Security Policies.
| Microsoft Lync Feature Policies Setting Options | Enabled/Disabled |
|---|---|
| Configure SIP security mode | Enabled |
| Disable HTTP fallback for SIP connection | Enabled |
Microsoft Office 2016 Intune Security Policies
Let’s check the following table to get more details about the recommendation from the Microsoft engineering team on Microsoft Office 2016 Intune Security Policies.
| Microsoft Office 2016 Settings Options | Enabled/Disabled |
|---|---|
| Disable UI extending from documents and templates (User) | Enabled |
| ActiveX Control Initialization (User) | Enabled |
| Allow VBA to load typelib references by path from untrusted intranet locations (User) | Disabled |
| Automation Security (User) | Enabled |
| Control how Office handles form-based sign-in prompts (User) | Enabled |
| Disable additional security checks on VBA library references that may refer to unsafe locations on the local machine (User) | Disabled |
| Disable all Trust Bar notifications for security issues (User) | Disabled |
| Encryption type for password protected Office 97-2003 files (User) | Enabled |
| Encryption type for password protected Office Open XML files (User) | Enabled |
| Load Controls in Forms3 (User) | Enabled |
| Macro Runtime Scan Scope (User) | Enabled |
| Protect document metadata for rights managed Office Open XML Files (User) | Enabled |
| Allow mix of policy and user locations (User) | Disabled |
| Disable the Office client from polling the SharePoint Server for published links (User) | Enabled |
| Smart Documents (Word, Excel) Disable Smart Document’s use of manifests (User) | Enabled |
Microsoft Office 2016 (Machine)
Let’s check the following table to get more details about the recommendation from the Microsoft engineering team on Microsoft Office 2016 (machine) Intune Security Policies.
| Microsoft Office 2016 (Machine) Settings Options | Enabled/Disabled |
|---|---|
| Add-on Management | Enabled |
| Consistent Mime Handling | Enabled |
| Disable user name and password | Enabled |
| Information Bar | Enabled |
| Local Machine Zone Lockdown Security | Enabled |
| Mime Sniffing Safety Feature | Enabled |
| Navigate URL | Enabled |
| Object Caching Protection | Enabled |
| Protection From Zone Elevation | Enabled |
| Restrict ActiveX Install | Enabled |
| Restrict File Download | Enabled |
| Saved from URL | Enabled |
| Scripted Window Security Restrictions | Enabled |
Microsoft Outlook 2016 Intune Security Policies
Let’s check the following table to get more details about the recommendation from the Microsoft engineering team on Microsoft Outlook 2016 Intune Security Policies.
| Microsoft Outlook 2016 Settings Options | Enabled/Disabled |
|---|---|
| Outlook Security Mode (User) | Enabled |
| Allow users to demote attachments to Level 2 (User) | Disabled |
| Allow Active X One Off Forms (User) | Enabled |
| Configure Outlook object model prompt when sending mail (User) | Enabled |
| Allow scripts in one-off Outlook forms (User) | Disabled |
| Prevent users from customizing attachment security settings (User) | Enabled |
| Remove file extensions blocked as Level 2 (User) | Enabled |
| Retrieving CRLs (Certificate Revocation Lists) (User) | Enabled |
| Configure Outlook object model prompt When accessing the Formula property of a UserProperty object (User) | Enabled |
| Authentication with Exchange Server (User) | Enabled |
| Display Level 1 attachments (User) | Disabled |
| Use Unicode format when dragging e-mail message to file system (User) | Disabled |
| Set Outlook object model custom actions execution prompt (User) | Enabled |
| Minimum encryption settings (User) | Enabled |
| Do not allow Outlook object model scripts to run for shared folders (User) | Enabled |
| Configure Outlook object model prompt when executing Save As (User) | Enabled |
| Do not allow Outlook object model scripts to run for public folders (User) | Enabled |
| Include Internet in Safe Zones for Automatic Picture Download (User) | Disabled |
| Security setting for macros (User) | Enabled |
| Remove file extensions blocked as Level 1 (User) | Enabled |
| Signature Warning (User) | Enabled |
| Junk E-mail protection level (User) | Disabled |
| Configure Outlook object model prompt when reading address information (User) | Enabled |
| Enable RPC encryption (User) | Enabled |
| Allow hyperlinks in suspected phishing e-mail messages (User) | Disabled |
| Configure Outlook object model prompt when accessing an address book (User) | Enabled |
| Configure Outlook object model prompt when responding to meeting and task requests (User) | Enabled |
Microsoft PowerPoint 2016
The following table gives you more details about the recommendation from the Microsoft engineering team on Microsoft PowerPoint 2016 Intune Security Policies.
| Microsoft PowerPoint 2016 Settings Options | Enabled/Disabled |
|---|---|
| Run Programs (User) | Enabled |
| Scan encrypted macros in PowerPoint Open XML presentations (User) | Enabled |
| Turn off file validation (User) | Disabled |
| Block macros from running in Office files from the Internet (User) | Enabled |
| Require that application add-ins are signed by Trusted Publisher (User) | Enabled |
| Disable Trust Bar Notification for unsigned application add-ins and block them (User) | Enabled |
| VBA Macro Notification Settings (User) | Enabled |
| PowerPoint 97-2003 presentations, shows, templates and add-in files (User) | Enabled |
| Set default file block behavior (User) | Enabled |
| Do not open files from the Internet zone in Protected View (User) | Disabled |
| Set document behavior if file validation fails (User) | Enabled |
| Turn off Protected View for attachments opened from Outlook (User) | Disabled |
| Allow Trusted Locations on the network (User) | Disabled |
Microsoft Project 2016
Let’s check the following table to get more details about the recommendation from the Microsoft engineering team on Microsoft Project 2016 Intune Security Policies.
| Microsoft Project 2016 Settings Options | Enabled/Disabled |
|---|---|
| Allow Trusted Locations on the network (User) | Disabled |
| Require that application add-ins are signed by Trusted Publisher (User) | Enabled |
| Disable Trust Bar Notification for unsigned application add-ins and block them (User) | Enabled |
| VBA Macro Notification Settings (User) | Enabled |
Microsoft Publisher 2016
Let’s check the following table to get more details about the recommendation from the Microsoft engineering team on Microsoft Publisher 2016 Intune Security Policies.
| Microsoft Publisher 2016 Settings Options | Enabled/Disabled |
|---|---|
| Publisher Automation Security Level (User) | Enabled |
| Require that application add-ins are signed by Trusted Publisher (User) | Enabled |
| Disable Trust Bar Notification for unsigned application add-ins (User) | Enabled |
| VBA Macro Notification Settings (User) | Enabled |
Microsoft Visio 2016
Let’s check the following table to get more details about the recommendation from the Microsoft engineering team on Microsoft Visio 2016 Intune Security Policies.
| Microsoft Visio 2016 Settings Options | Enabled/Disabed |
|---|---|
| Allow Trusted Locations on the network (User) | Disabled |
| Block macros from running in Office files from the Internet (User) | Enabled |
| Require that application add-ins are signed by Trusted Publisher (User) | Enabled |
| Disable Trust Bar Notification for unsigned application add-ins and block them (User) | Enabled |
| VBA Macro Notification Settings (User) | Enabled |
| Visio 2000-2002 Binary Drawings, Templates and Stencils (User) | Enabled |
| Visio 2003-2010 Binary Drawings, Templates and Stencils (User) | Enabled |
| Visio 5.0 or earlier Binary Drawings, Templates and Stencils (User) | Enabled |
Microsoft Word 2016 Intune Security Policies
Let’s check the following table to get more details about the recommendation from the Microsoft engineering team on Microsoft Word 2016 Intune Security Policies.
| Microsoft Word 2016 Settings Options | Enabled/Disabled |
|---|---|
| Block macros from running in Office files from the Internet (User) | Enabled |
| Dynamic Data Exchange (User) | Disabled |
| Require that application add-ins are signed by Trusted Publisher (User) | Enabled |
| Disable Trust Bar Notification for unsigned application add-ins and block them (User) | Enabled |
| Scan encrypted macros in Word Open XML documents (User) | Enabled |
| VBA Macro Notification Settings (User) | Enabled |
| Set default file block behavior (User) | Enabled |
| Word 2 and earlier binary documents and templates (User) | Enabled |
| Word 2000 binary documents and templates (User) | Enabled |
| Allow Trusted Locations on the network (User) | Disabled |
| Turn off file validation (User) | Disabled |
| Word 97 binary documents and templates (User) | Enabled |
| Word XP binary documents and templates (User) | Enabled |
| Do not open files from the Internet zone in Protected View (User) | Disabled |
| Set document behavior if file validation fails (User) | Enabled |
| Turn off Protected View for attachments opened from Outlook (User) | Disabled |
| Do not open files in unsafe locations in Protected View (User) | Disabled |
| Set document behavior if file validation fails (User) | Enabled |
| Turn off Protected View for attachments opened from Outlook (User) | Disabled |
| Allow Trusted Locations on the network (User) | Disabled |
| Turn off file validation (User) | Disabled |
This is the main Configuration page. You can easily use the search box in the below window to search for some particular configuration. The configuration page shows all the templates and their default value
Once you are fine with all the security policy settings for Microsoft 365 Office Applications, you can click on the Next button from the below screen.
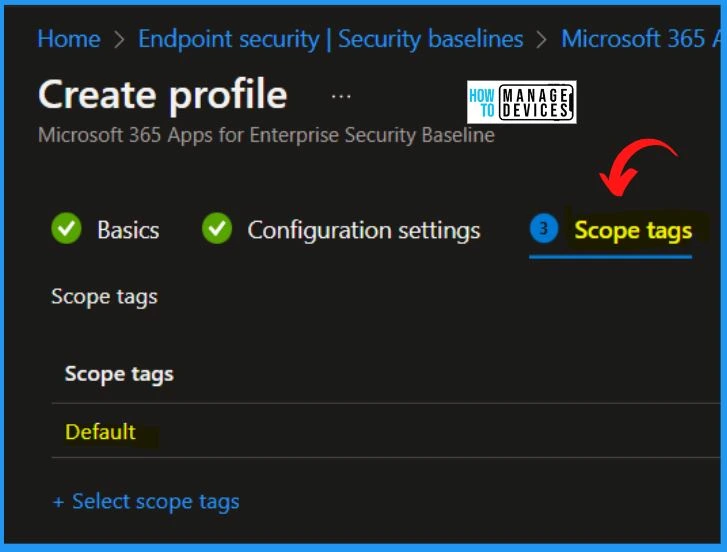
Scope tags within Microsoft Intune enable administrators to categorize devices within their organization into distinct logical groups. These groups, called tags, are crucial in restricting the availability of specific settings, applications, and policies to designated users or devices.
- Select the Scope tags as Default.
- Select the Next button in the Scope tags window.
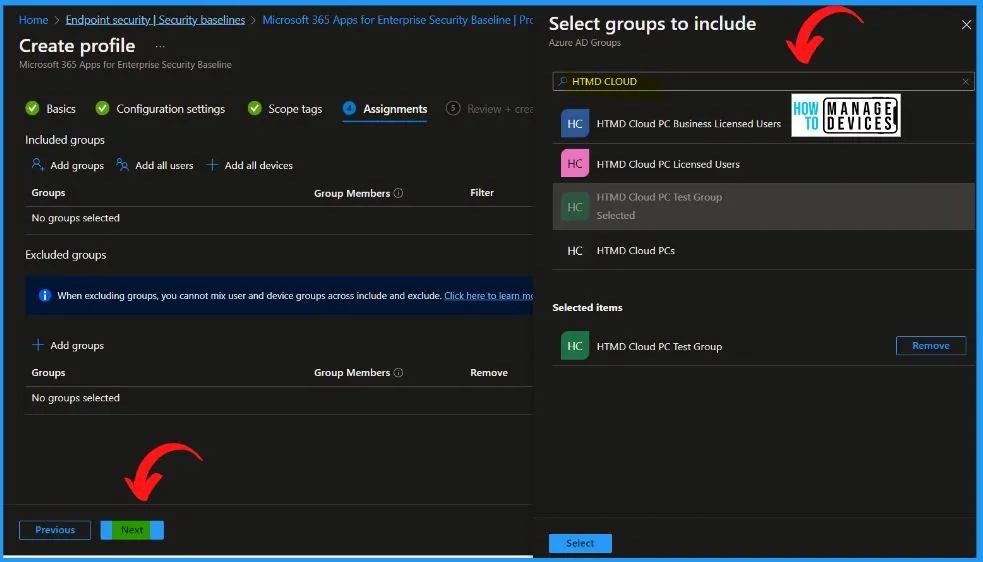
The Assignments tab shows the included groups and excluded groups. You can easily add a group by clicking the Add Groups button from the below Create profile window. Select the groups from the select groups to include the widow; here, we select the HTMD Cloud PC Test Group.
- Click Select and Next from the below window.
The Review + Create window helps you to show the Name, Description, Platform, Configuration settings, Scope tags, Assignments, etc. Selecting the Create button from the below window enables you to create a new Microsoft 365 Apps for Enterprise Security Baseline available in Intune portal.
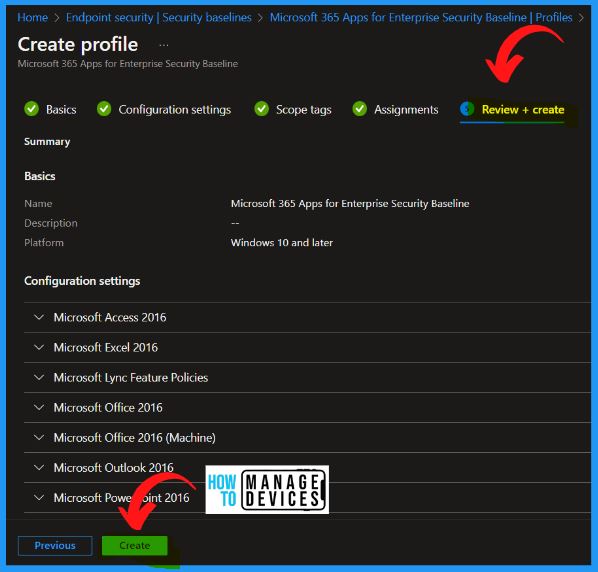
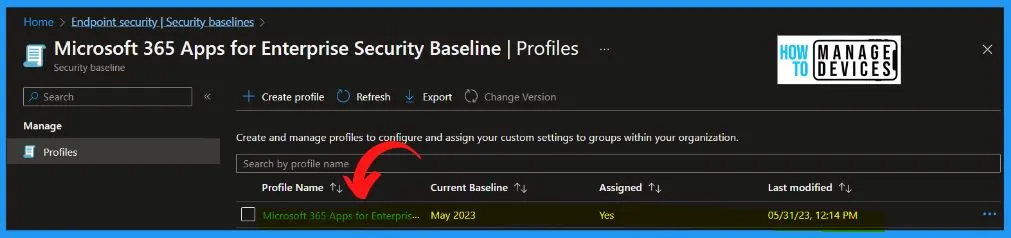
In the below window, you can see that the Profile has been created successfully. The Windows 365 security policy profile is made and deployed to Cloud PC using the security baseline. It also shows the details such as Profile name, Current Baseline, Assigned and Last modified, etc.
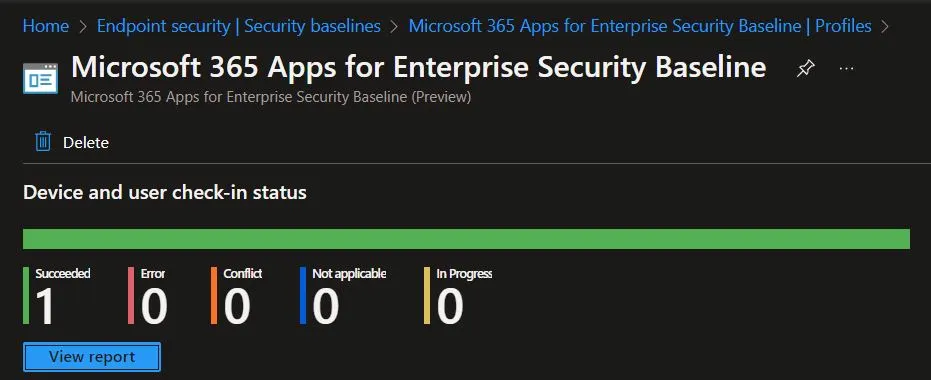
Intune Reports for Microsoft 365 Office Apps Security Policies
The Intune Portal offers a comprehensive Intune settings catalog profile report, granting administrators a holistic view of device configuration policies and their deployment status. This report provides a consolidated overview, allowing for easy monitoring and analysis of the applied policies across devices.
The default reports in Intune can be used to get details for Microsoft 365 Office Apps Security settings compliancy. You can also check the following post to Get Office Apps Inventory Report from Microsoft 365 Admin Center.
- Administrators must select the relevant policy from the Configuration Profiles list to monitor the policy assignment.
- By checking the device and user check-in status, they can verify the successful application of the policy.
- For a more comprehensive view, clicking on “View Report” provides access to additional details.
Reference Site – What’s new in Microsoft Intune | Microsoft Learn
Author
About Author – Vidya is a computer enthusiast. She is here to share quick tips and tricks with Windows 11 or Windows 10 users. She loves writing on Windows 11 and related technologies. She is also keen to find solutions and write about day-to-day tech problems.

after applying these on system i am not able to see Microsoft 365 office UI. is that normal. which policy here is blocking it.