Let’s learn how you can disable UAC Secure Desktop Mode using Intune. User Account Control (UAC) helps prevent malware from damaging a PC and allows organizations to deploy a better-managed desktop.
When an executable file requests elevation, the interactive desktop, also called the user desktop, is switched to the secure desktop. The secure desktop dims the user desktop and displays an elevation prompt that must be responded to before continuing. When the user clicks Yes or No, the desktop switches back to the user desktop.
UAC is set to notify you whenever apps try to make changes to your PC by default, but you can change how often UAC notifies you. Here you can check more details, Change User Access Control (UAC) Settings in Windows 10
NOTE! – Disabling UAC prompts is NOT the best-recommended security practice. The CIS benchmark says this must be enabled (I guess). There could be some use cases with “special” security approval where you can implement this solution.
The User Account Control: Switch to the secure desktop when prompting for elevation policy setting is checked:
- All elevation requests go to the secure desktop regardless of prompt behavior policy settings for administrators and standard users if the secure desktop is enabled.
- If the secure desktop is not enabled, all elevation requests go to the interactive user’s desktop, and the per-user settings for administrators and standard users are used.
You can use security policies to configure how User Account Control works in your organization. They can be configured locally using the Intune, Local Security Policy snap-in (secpol.msc) or configured for the domain, OU, or specific groups by Group Policy.
- Intune User Policy Troubleshooting Tips For Prevent Changing Theme
- Intune Logs Event IDs IME Logs Details for Windows Client Side Troubleshooting
- Collect Intune Logs from MEM Portal Diagnostic Data
Disable UAC Secure Desktop Mode using Intune
The Intune Settings Catalog is the best place to go for all the policy settings in Intune (MEM). You will also get an option Duplicate to create a copy of an existing setting catalog profile in the settings catalog profile.
Let’s follow the step below to disable dimmed Secure Desktop using Intune –
- Sign in to Microsoft Endpoint Manager Admin Center https://endpoint.microsoft.com/
- Select Devices > Windows > Configuration profiles > Create profile.
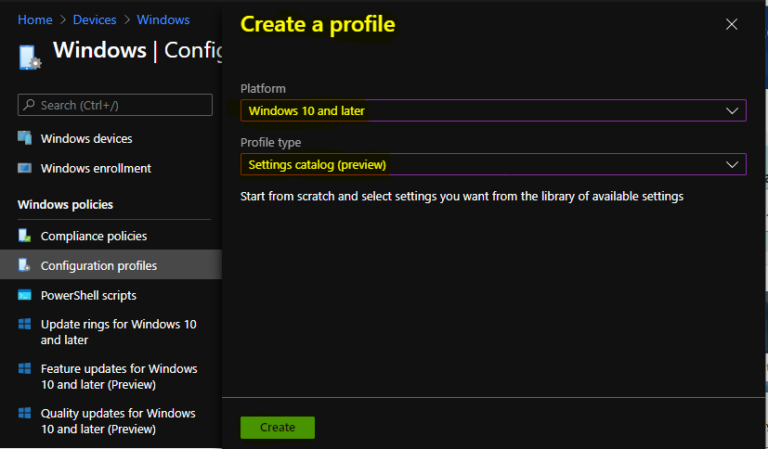
In Create Profile, Select Platform, Windows 10, and later and Profile, Select Profile Type as Settings catalog. Click on Create button.
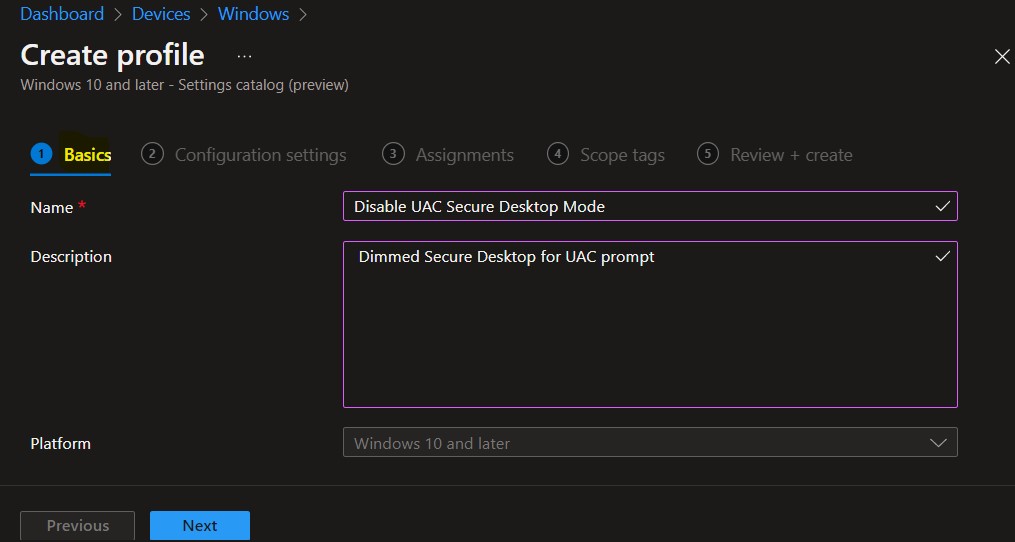
On the Basics tab, enter a descriptive name, such as Disable UAC Secure Desktop Mode or Manage Secure Desktop for UAC Prompt. Optionally, enter a Description for the policy, then select Next.
In Configuration settings, click Add settings to browse or search the catalog for the settings you want to configure.
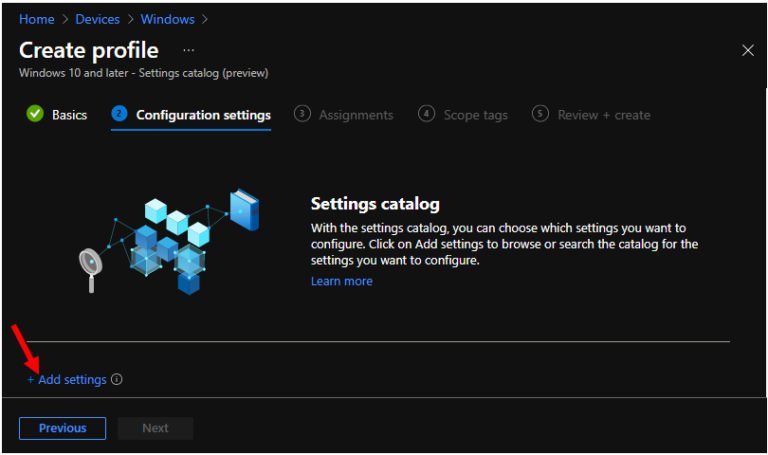
On the Settings Picker window, use the search box and type User Account Control, and click Search. Now select Local Policies Security Options. This will display all the available User Account Control (UAC) prompt settings.
Selected the below settings from category –
- User Account Control Behavior Of The Elevation Prompt For Standard Users
- User Account Control Switch To The Secure Desktop When Prompting For Elevation
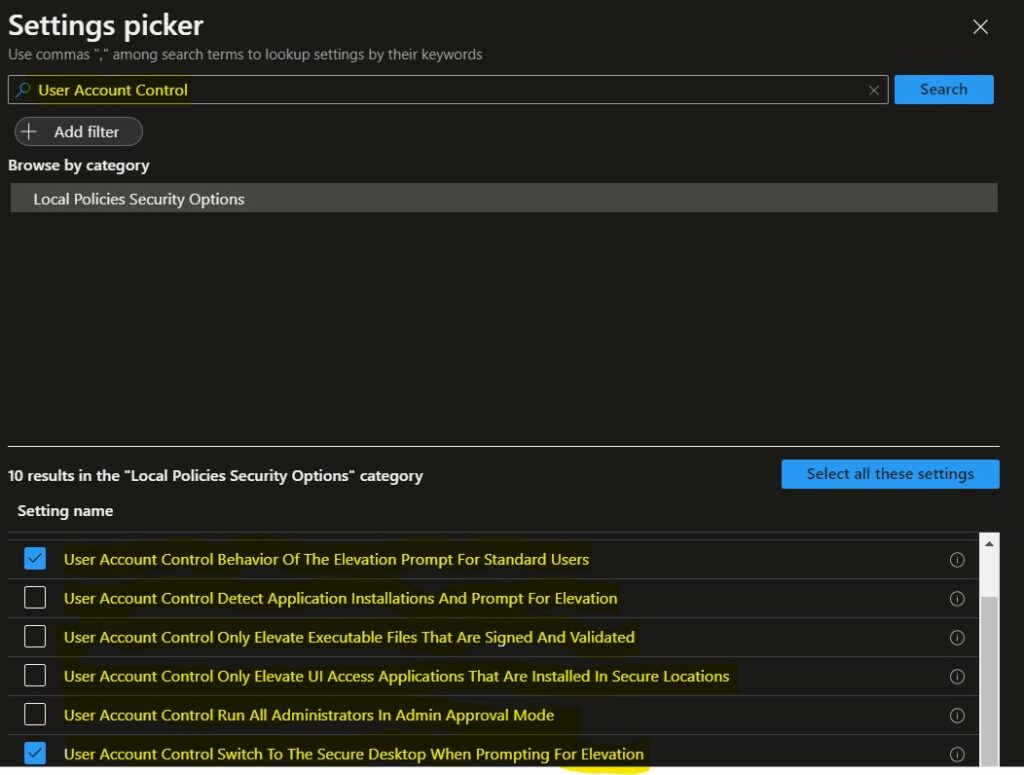
The setting is shown and configured with a default value. Here, I selected the below settings and Clicked Next.
- User Account Control Behavior Of The Elevation Prompt For Standard Users – You can also change the prompt behavior policy settings for standard users. By default, it sets for prompt for credentials.
- User Account Control Switch To The Secure Desktop When Prompting For Elevation – This policy setting controls whether the elevation request prompt is displayed on the interactive user’s desktop or the secure desktop. Set to Disabled.
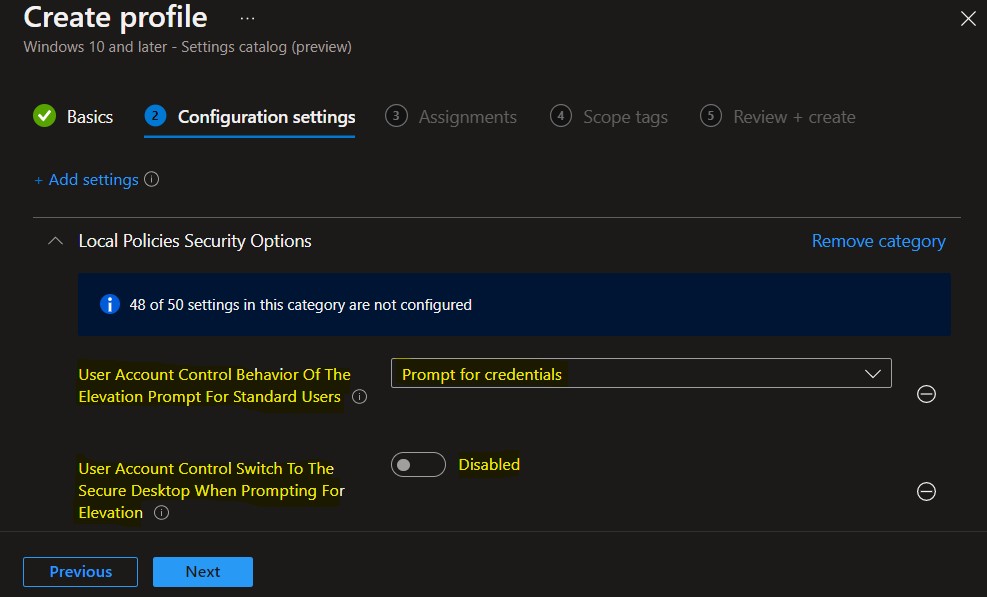
Under Assignments, In Included groups, click Add groups and then choose Select groups to include one or more groups to which you want to deploy the UAC settings. Click Next to continue.
In Scope tags, you can assign a tag to filter the profile to specific IT groups. Add scope tags (if required) and click Next.
In Review + create, review your settings. When you select Create, your changes are saved, and the profile is assigned.
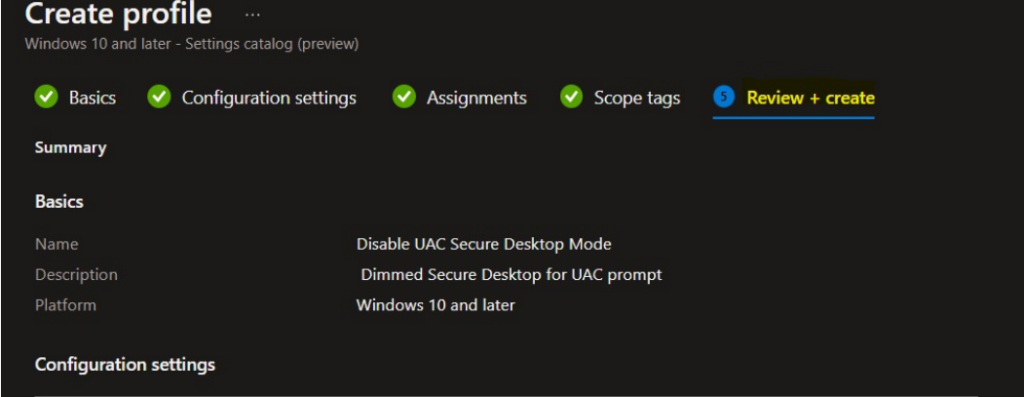
A notification will appear automatically in the top right-hand corner with a message. The Policy “Disable UAC Secure Desktop Mode” created successfully. The policy is also shown in the Configuration profiles list.
Your groups will receive your profile settings when the devices check in with the Intune service the policy applies to the devices.
Intune Reporting – Disable UAC Secure Desktop Mode
You can check Intune settings catalog profile report from Intune Portal, which provides an overall view of device configuration policies deployment status.
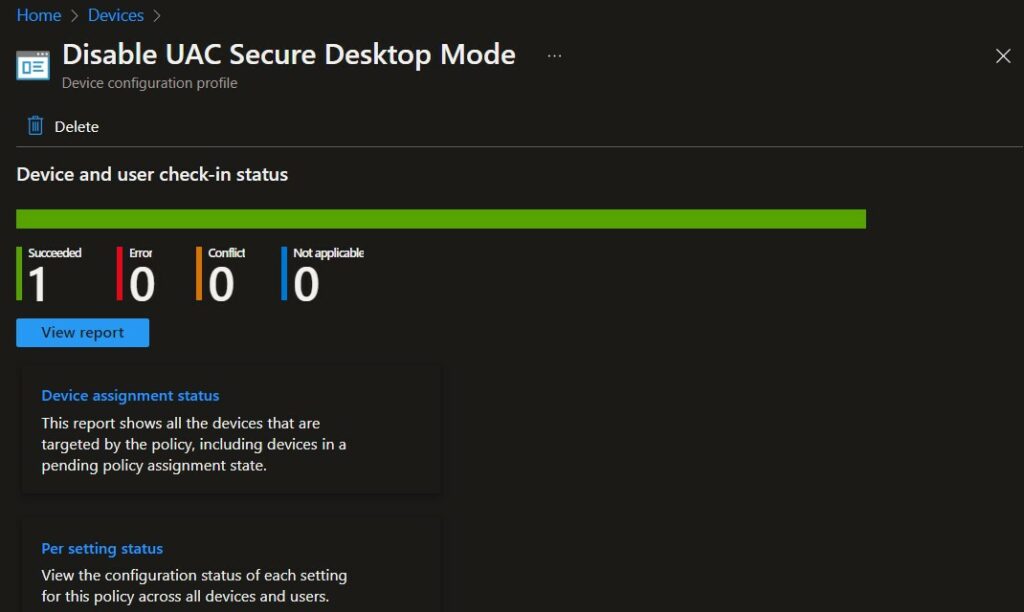
To monitor the policy assignment, from the list of Configuration Profiles, select the policy, and here you can check the device and user check-in status. If you click View Report, additional details are displayed.
Additionally, you can quickly check the update as devices/users check-in status reports –
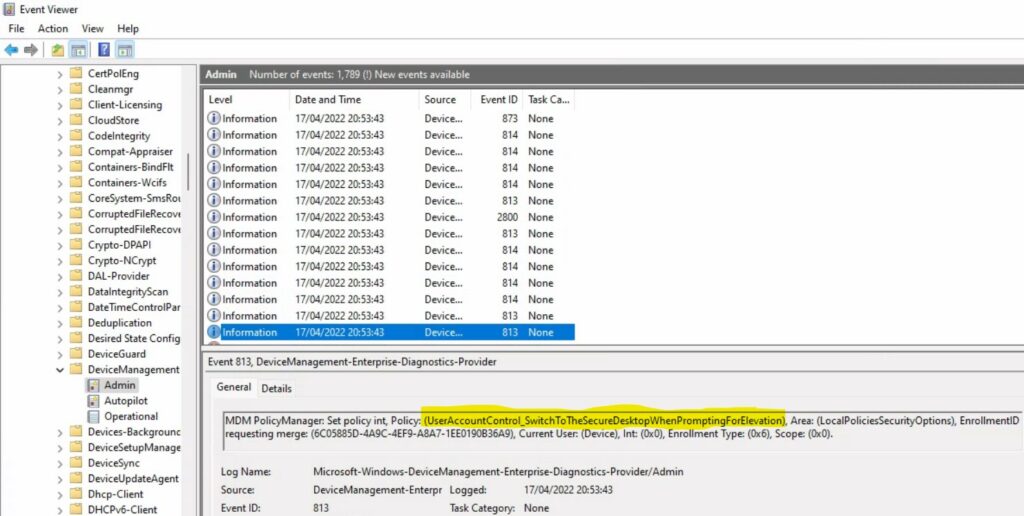
Intune Client-Side Event Log
Event logs are the extended type of Intune Logs in Windows. The Intune event ID 813 indicates that a string policy is applied on Windows 11 or 10 devices. You can also see the exact value of the policy being applied on those devices.
MDM PolicyManager: Set policy int, Policy: (UserAccountControl_SwitchToTheSecureDesktopWhenPromptingForElevation), Area: (LocalPoliciesSecurityOptions), EnrollmentID requesting merge: (6C05885D-4A9C-4EF9-A8A7-1EE0190B36A9), Current User: (Device), Int: (0x0), Enrollment Type: (0x6), Scope: (0x0).
Registry – Disable UAC Secure Desktop Mode
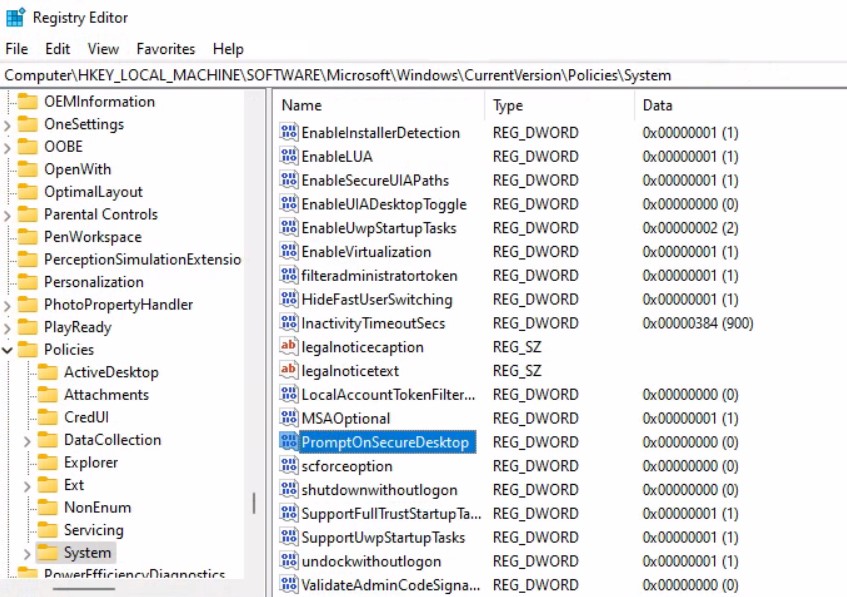
You can use REGEDIT.exe on a target computer to view the registry settings that store group policy settings. These settings are located at the registry path –
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System DWORD value PromptOnSecureDesktop set to 0.