In this post, let’s see how to Block MacStealer Malware using Intune. We will also discuss in detail the MacStealer malware and how it is affecting users on Mac and how to be safe by implementing antivirus policies in Intune. and will check various settings while creating an antivirus profile for securing your macOS devices with Intune.
Our last blog post discussed, DaisyDisk App review in macOS using Intune. We have briefly discussed an overview of the Daisy disk app, the features provided by the app, and how to push the app using Intune. Also, we will discuss the different settings that can be configured while deploying the app in Intune.
Malware, or malicious software, is a term that describes any malicious program or codes harmful to Computer systems. Recently we have come across the MacStealer Malware, which is info-stealing malware targeting Mac users and stealing their credentials stored from the iCloud KeyChain.
Also, after the MacStealer malware was detected as explicitly active on the internet, apple released a fix with the latest version of macOS Ventura v13.3, which also protects Mac devices from malware other than the antivirus protection policies using MDM Platform.
What is MacStealer Malware
MacStealer malware has been discovered on dark web hacking forums where it is claimed as malware in an early development phase, which can infect on macOS Catalina, Big Sur, Monterey, and Ventura.
As per the malware developer, it can steal the data such as:
- Account Passwords
- Credit card details from Browsers (such as Brave, Chrome, and Firefox)
- File with extensions (TXT, DOC, DOCX, PDF, XLS, XLSX, PPT, PPTX, JPG, PNG, CSV, BMP, MP3, ZIP, RAR, PY, and DB files)
- Collect System information
- Collect Keychain password information
- It can also extract the Keychain database in base64 encoded form
Keychain database is a secure storage in macOS which stores your passwords, account information, private keys, and certificates, encrypting it with a Mac login password. Using this feature user automatically enters login credentials on web pages and apps.
- Enroll MacOS In Intune With Step By Step Guide
- New System Settings in macOS Ventura v13 and Intune Software Update Configs
How Users Get Infected with Malware
The most common ways to be infected by malware are by surfing the Internet or email. Malware can attack devices while users surf through hacked websites, view sites serving malicious ads, download infected files and install apps from unfamiliar sites to a device that lacks a quality anti-malware security application.
Also, malicious apps can hide legitimate apps, downloaded from third-party websites, instead of official vendor sites or app stores.
Ways to Avoid Getting Affected by Macstealer Malware
The best method to avoid getting affected by any malware is by upgrading the device to the latest version of macOS, which by default protect the device from any vulnerable environment. The fix for Macstealer malware has been provided by Apple on the latest patch (on 2018 and above models macOS Ventura v13.3, On 2017 and below models macOS Monterey v12.6.4).
Apple designs its hardware and software with advanced technologies, which work to run apps more securely, protect data, and help keep users safe on the web. Also, the best way to keep the Mac secure is by running on the latest macOS version. macOS work at the core to keep the whole system safe from malware.
However IT Admins, while managing multiple Mac devices in an organization, it is difficult to upgrade all the managed devices to the latest patch and ensure the security in the organization, which is why there should be an alternate plan for securing the devices from the exploited environment.
Configure Malware Block Policy Using Intune
To create a profile Endpoint security policy that should block all the malware explicitly active on the internet, we must follow the steps mentioned below.
- Sign in to the Microsoft Intune admin center https://endpoint.microsoft.com/.
- Select Endpoint Security > under Manage, and select Antivirus. Click on Create Policy.
- In Create a Profile window, Select Platform – macOS, Profile – Antivirus, and Click on Create.
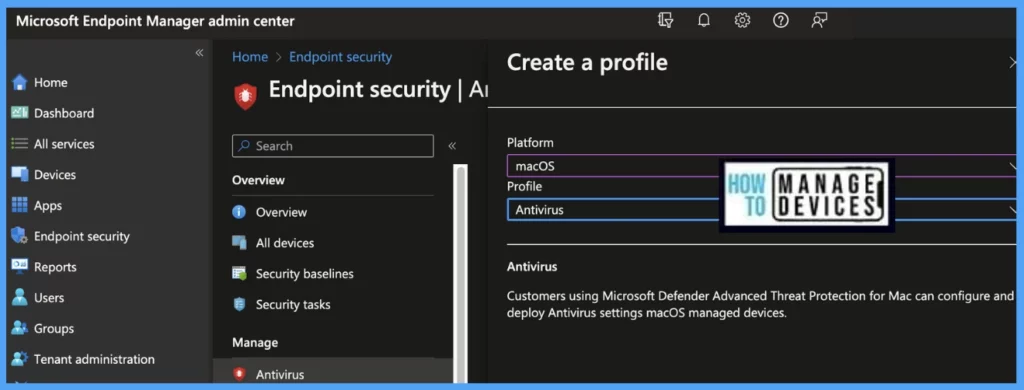
Once you click on Create button from the above page, Provide the Name and Description and click on Next.
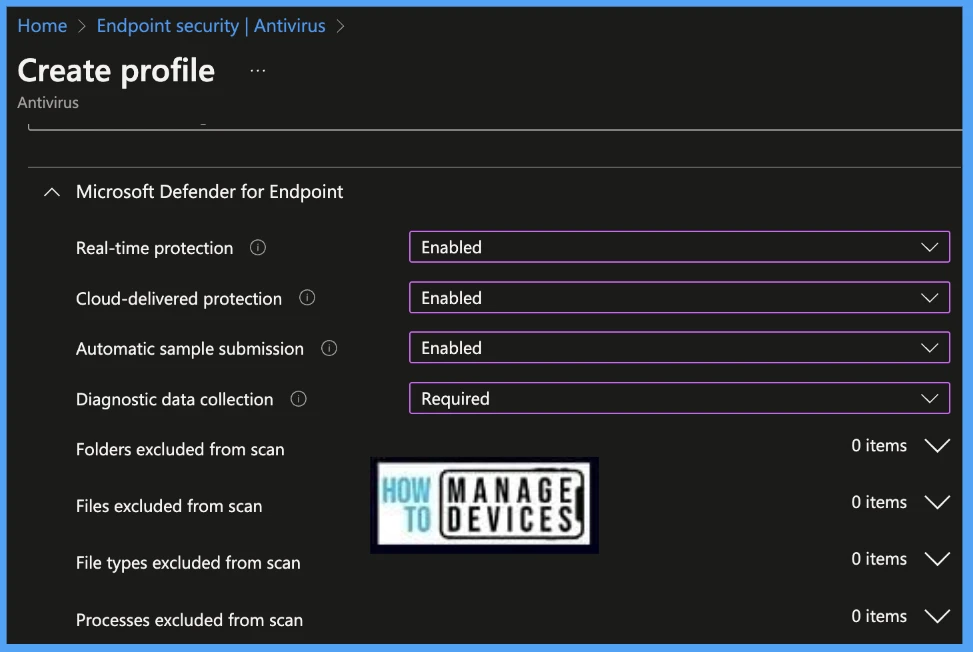
Under the Configuration settings tab, select settings to be used as defined by the organization.
| Microsoft Defender for Endpoints | Value |
|---|---|
| Real-time protection | Enabled |
| Cloud-delivered Protection | Enabled |
| Automatic Sample Submission | Enabled |
| Diagnostic Data collection | Required |
- Real-time protection (Require Microsoft Defender on macOS devices to use real-time Monitoring. It locates and stops malware from installing/ running. This setting can be turned off for a short time before it turns back on automatically)
- Cloud-delivered protection (By default, Microsoft Defender sends information to Microsoft about any problems it finds. Microsoft analyzes it to learn more about problems and to offer improved solutions. It works best when Automatic sample submission is set on.
- Automatic sample submission (Sends sample files to Microsoft to help protect device users and your organization from potential threats)
- Diagnostic Data Collection (Configure how diagnostic and usage data is shared with Microsoft)
- Folders excluded from scan (With this feature, we can exclude folders from Antivirus scan)
- Files excluded from scan (With this feature, we can exclude files from Antivirus scan)
- File types excluded from scan (With this feature, we can exclude types of files ( .app, .txt, etc.) from Antivirus scan)
- Processes excluded from scan (With this feature, we can exclude processes from Antivirus scan)
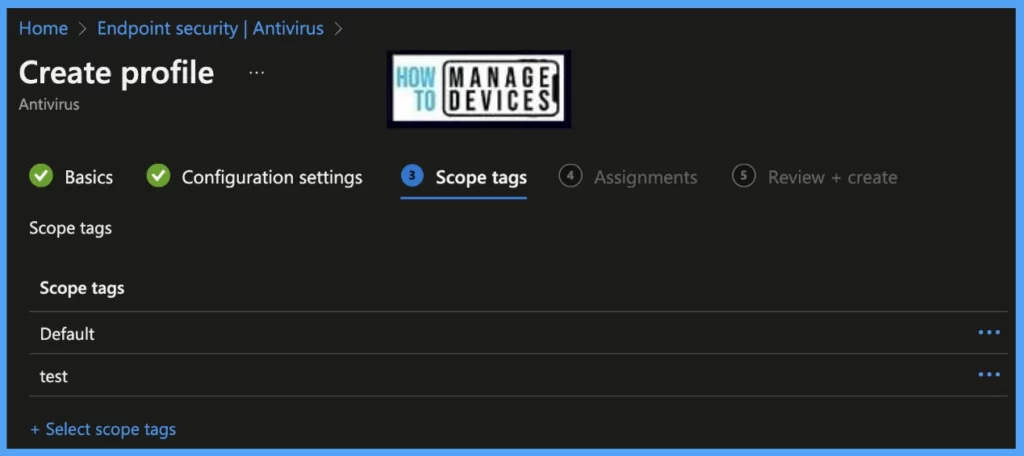
On the next page, Scope tags are filtering options provided in Intune to ease the admin jobs. In the Scope Tag section, you will get an option to configure scope tags for the policy. Click on Next.
On the next page, select Assignments group (Included groups and Excluded groups) and click Next.
Assignment Group: It determines who has access to any app, policy, or configuration profile by assigning groups of users to include and exclude.
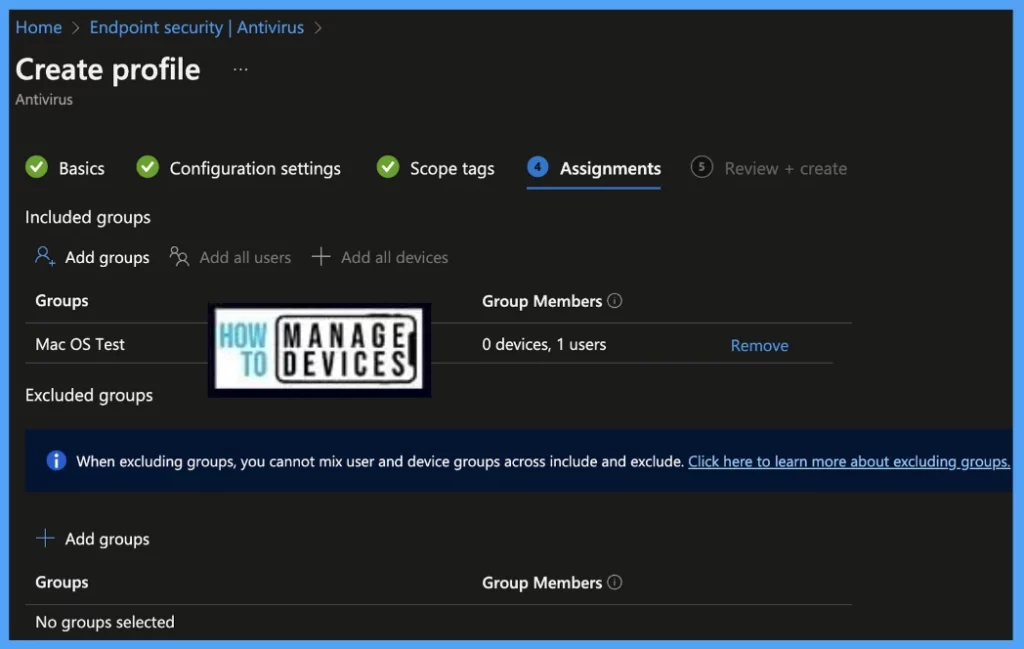
On the Review+Create page, please review if any settings need to be changed, or else go ahead and Create the policy.
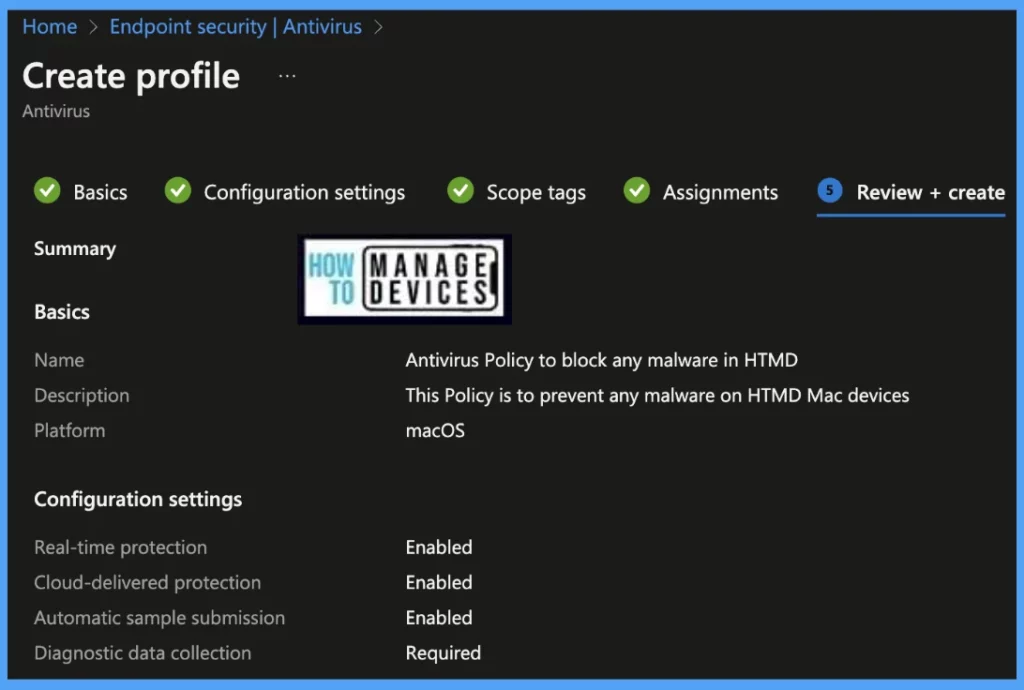
Once the policy is created, it will take a few minutes to get deployed to all the Mac devices. Also, to view the status of the deployed policy, we can check as per the below steps.
To see all the device statuses, Navigate to Endpoint Security > under Manage, and select Antivirus. Click on the selected policy, and on the Overview page, you may see the Profile deployment status.
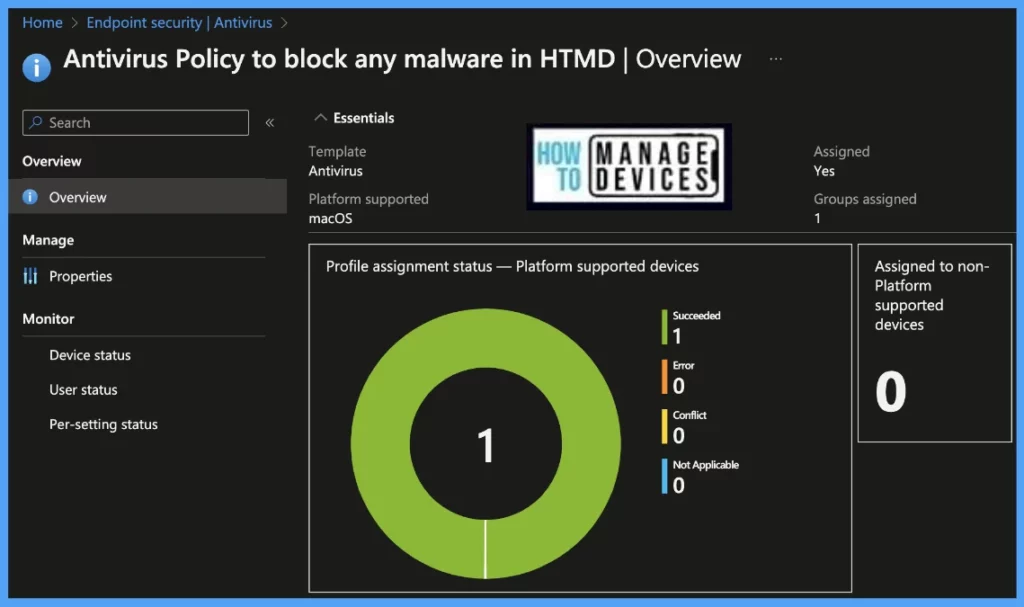
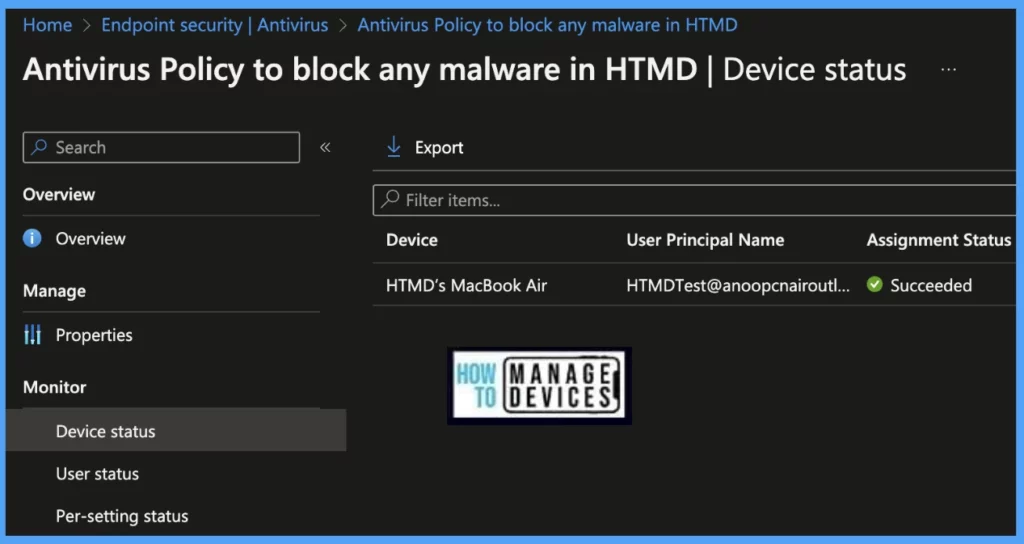
Also, we can view the per user, per device, and per setting status under every Antivirus policy.
Device Status: On this page, we can see a list of devices that the Antivirus policy has been pushed and how many of them are shown as Succeeded, Conflict, Error, and Not-Applicable.
User Status: On this page, we can see a list of users associated under Intune and push with the Antivirus setting policy and how many of them are showing as Succeeded, Conflict, Error, and Not-Applicable.
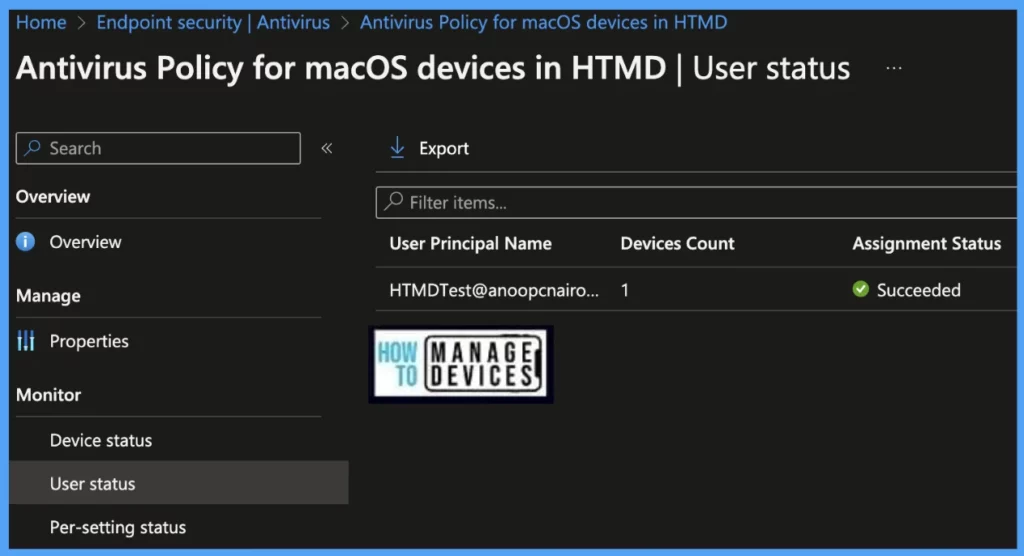
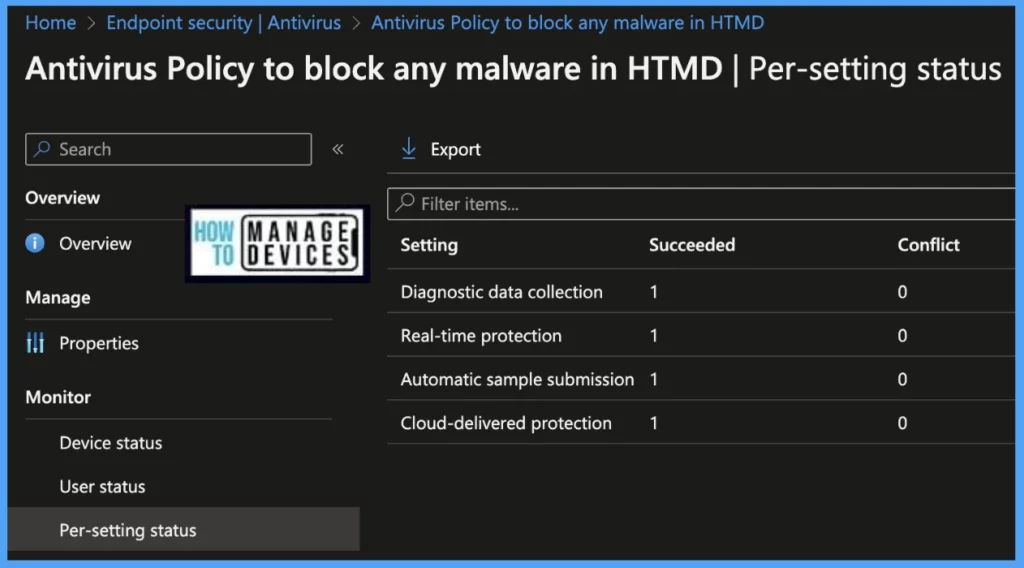
Per Setting Status: On this page, we can see a list of Antivirus Settings pushed to a list of devices; we can view the status as Succeeded, Conflict, Error, and Not-Applicable for each of the settings.
- Configure FileVault Encryption For MacOS Devices Using Intune
- Configure macOS Compliance Policy in Intune for Devices
Review Malware Block Policy on MacOS
Once the Policy gets pushed to the list of macOS devices as part of the assignment group, it may take a few minutes to reflect on the end user’s device. Also, we can manually run the check status, by launching the Company Portal, sign in with user’s credentials and click on Check status.
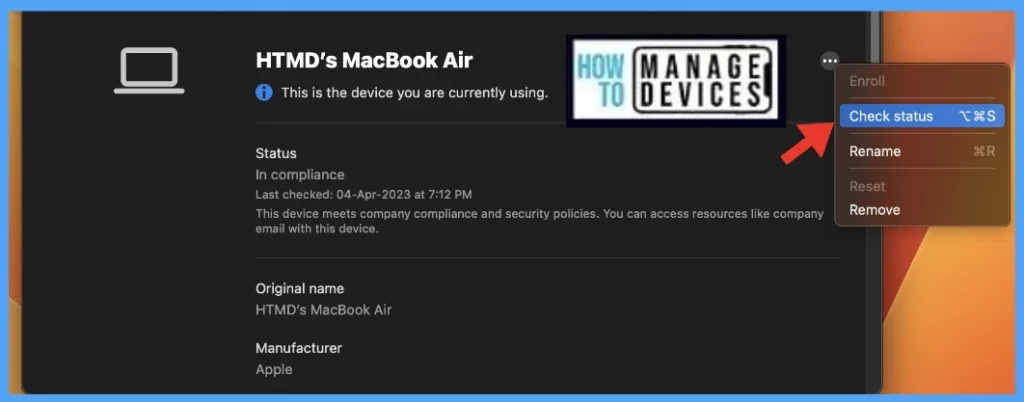
Once the user successfully logged into the device, we can follow the steps below to check the profile status.
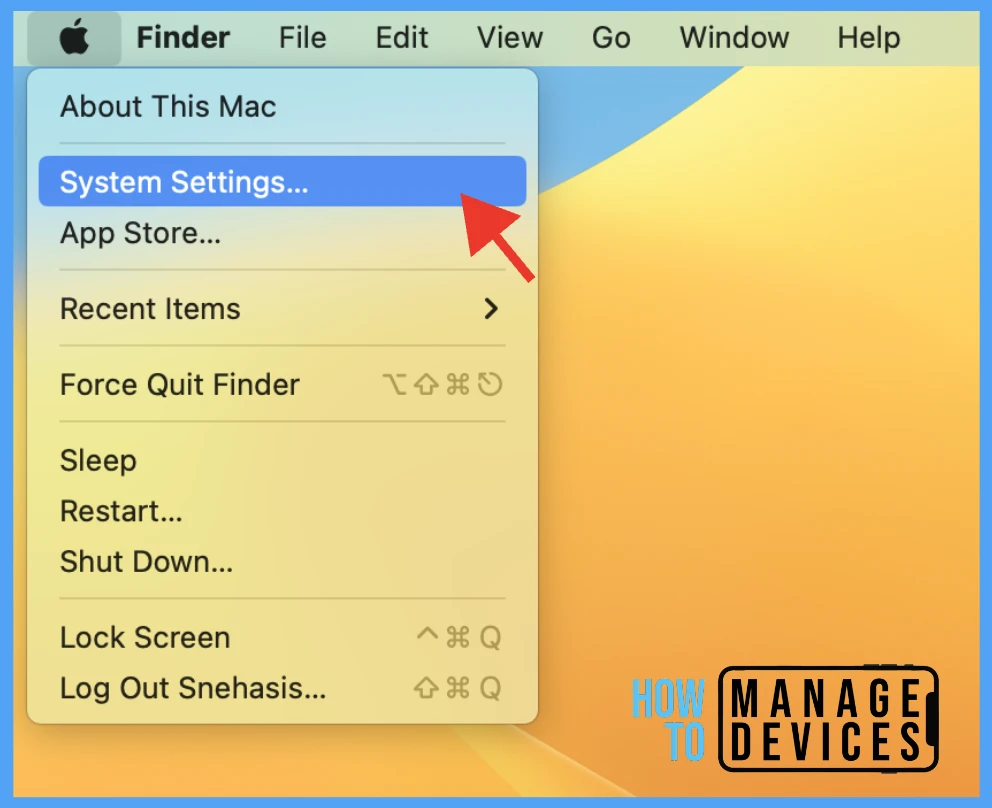
- Click on the Apple icon at the top-left corner.
- Select System Settings from the list of options.
Go to Privacy & Security > Profiles > double-click and open the profile to view the details. Here you can see the detailed status of the applied malware protection policy.
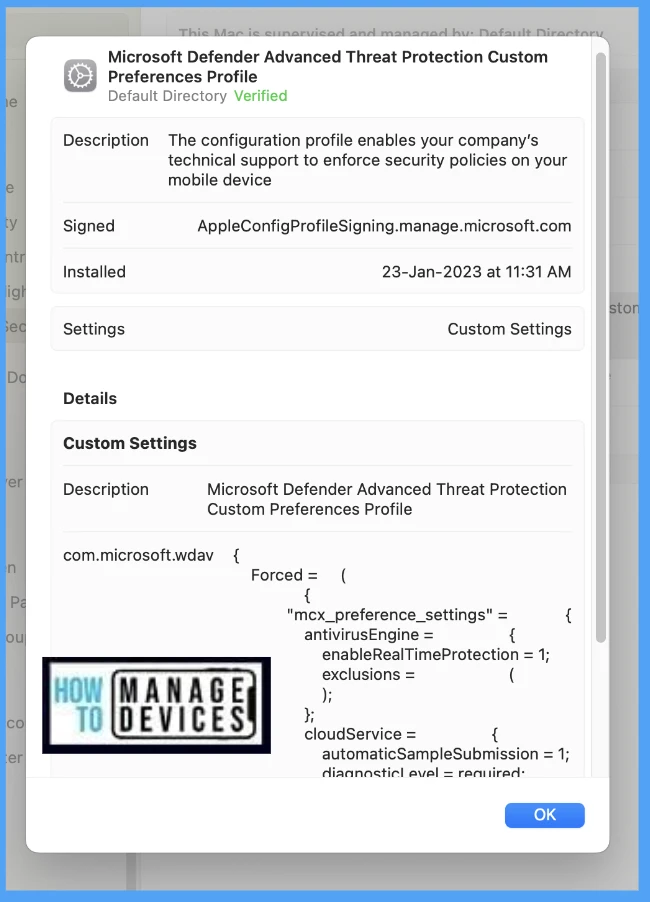
MacOS Compliance
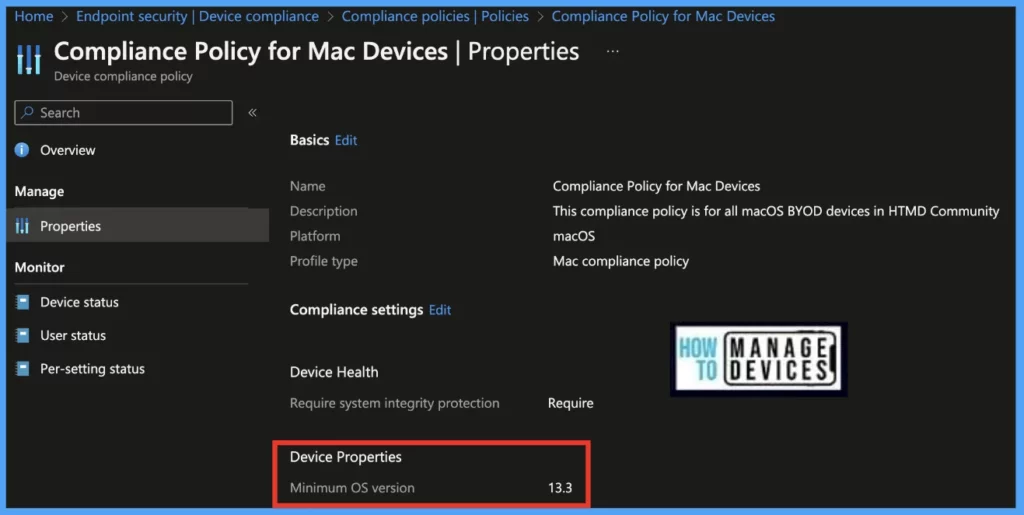
As discussed earlier, as we have 2018 and later models in HTMD, to ensure the devices are protected from both ways (running on macOS latest version and ensuring the Antivirus policy is deployed), we have also edited the macOS compliance policy from Minimum macOS version to v13.3 to ensure the users are compliant.
Conclusion
To ensure the protection of company resources from explicitly active viruses and malware, organizations must prioritize the implementation of a protection policy and also ensure devices are upgraded to the latest macOS version to ensure their compliance with organization standards.
Author
Snehasis Pani is currently working as a JAMF Admin. He loves to help the community by sharing his knowledge on Apple Mac Devices Support. He is an M.Tech graduate in System Engineering.
