In this post, let’s learn how to use the Windows 11 Account Lockout Policy Settings using Intune and Group Policy. Account lockout policy helps to protect your device from unauthorized login. There is a certain period to try login into the machine.
The Account lockout threshold policy settings determine the number of failed sign-in attempts that will cause a user account to be locked. The locked account cannot be used until you reset it or until the number of minutes specified by the Account lockout duration policy setting expires.
Brute force password attacks automatically try thousands or millions of password combinations for any or all user accounts. Limiting the number of failed sign-ins that can be performed nearly eliminates the effectiveness of such attacks, which helps users to prevent unauthorized users.
However, it’s important to note that a denial-of-service (DoS) attack could be performed on a domain that has an account lockout threshold configured. A malicious user could programmatically attempt multiple password attacks against all users. If the number of attempts is greater than the value of the Account lockout threshold, the attacker could potentially lock every account.
- 4 Windows 11 Safe Mode Options – How to Start Windows PC in Safe Mode
- 4 Methods to Enable Credential Guard on Windows Devices
What is Account Lockout Policy in Windows 11
The Account Lockout Policy is a process to protect your device from unauthorized forcefully login attempts. This policy helps to lock your system for some minutes from false login attempts. If someone repeatedly enters the wrong password, the account automatically locks down after.
The default lockout duration is 10 minutes. However, the administrator can modify the specific lockout duration. The Admins can change the time range between 1 to 99,999 minutes, and after the set time, the account is automatically unlocked for login using the correct password.

Group Policy Settings for Account Lockout Policy in Windows 11
You can, as an admin, change the account lockout policy in windows 11 by using the local or Domain group policy. The policy path navigates toward the account lockout policy settings.
Open the Local Group Policy Editor and follow the path “Computer Configuration/Windows Settings/Security Settings/Account Policies/Account Lockout Policy” to reach the proper location to perform the desired task.
You can open Run, type gpedit.msc, and press OK; the Local Group Policy Editor Opens. However, to open the Domain policy – open Run and type gpmc.msc and press OK. More details domain level group policy settings using ADMX are explained -> Microsoft Edge ADMX Group Policy Templates.
In the Account Lockout Policy, the Group Policy Editor has 4 policies for its security settings are listed below:
- Account Lockout Duration
- Account Lockout Threshold
- Allow Administrator Account
- Reset Account Lockout Counter After
Computer Configuration/Windows Settings/Security Settings/Account Policies/Account Lockout Policy
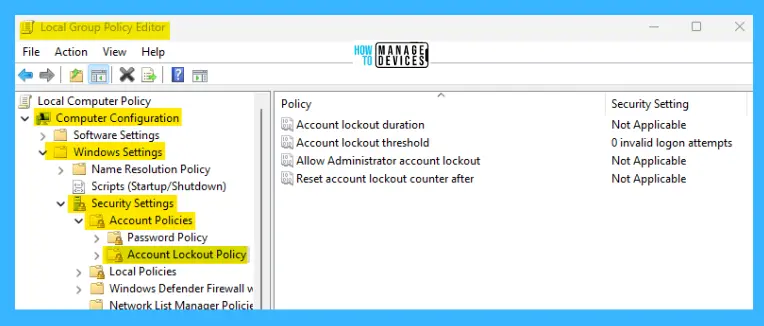
Windows 11 Account Lockout Duration
This security setting determines the number of minutes a locked-out account remains locked out before automatically becoming unlocked. The available range is from 0 minutes to 99,999 minutes. If you set the account lockout duration to 0, the account will be locked out until an administrator explicitly unlocks it.
If an account lockout threshold is defined, the account lockout duration must be greater than or equal to the reset time.
NOTE! This policy setting only has meaning when an Account lockout threshold is specified.
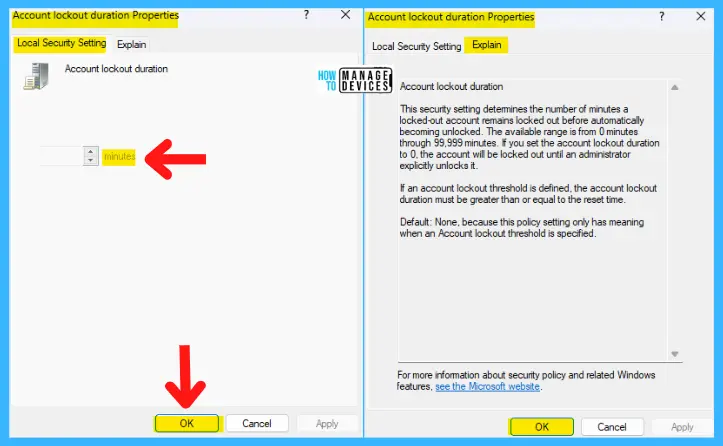
Configure Account Lockout Threshold Settings using Group Policy
This security setting determines the number of failed logon attempts that causes a user account to be locked out. A locked-out account cannot be used until it is reset by an administrator or until the lockout duration for the account has expired.
You can set a value between 0 and 999 failed logon attempts. The account will never be locked out if you set the value to 0.
It has failed password attempts against workstations or member servers that have been locked using CTRL+ALT+DELETE or password-protected screen savers count as failed logon attempts. The default value is set to 0.
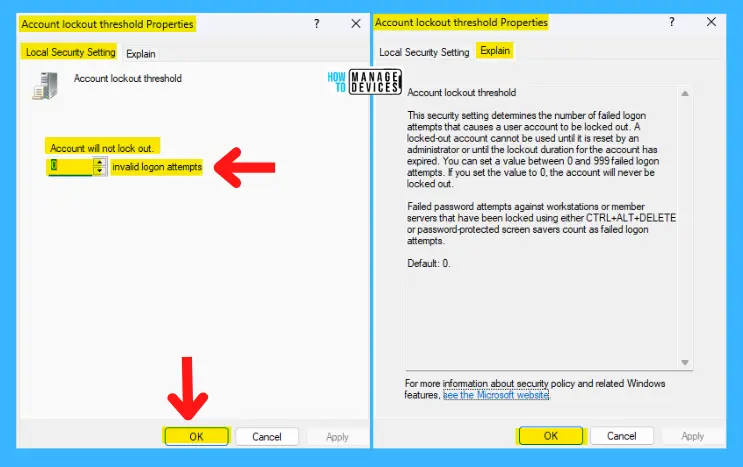
Allow Administrator Account Lockout
This security setting determines whether the built-in Administrator account is subject to the account lockout policy.
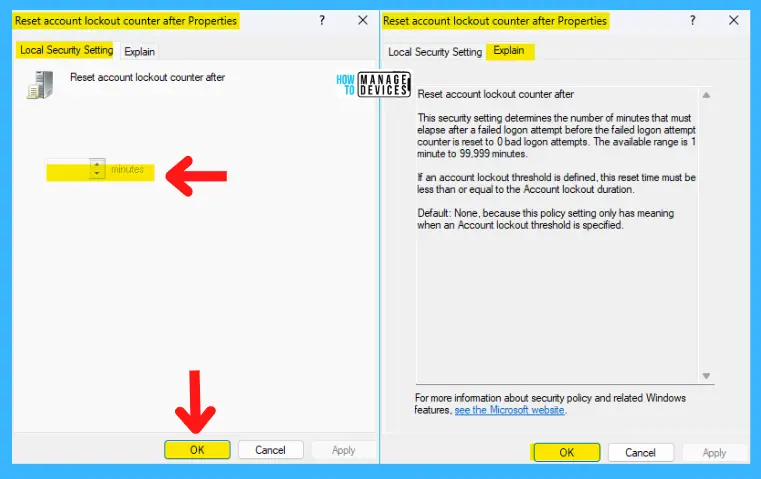
Reset Account Lockout Counter After
This security setting determines the number of minutes that must elapse after a failed logon attempt before the failed logon attempt counter is reset to 0 bad logon attempts. The available range is 1 minute to 99,999 minutes.
If an account lockout threshold is defined, this reset time must be less than or equal to the Account lockout duration.
NOTE! The default value is none because this policy setting only has meaning when an Account lockout threshold is specified.
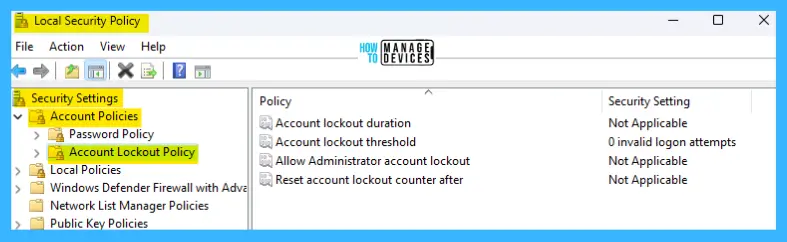
Local Security Policy Settings for Account Lockout Policy in Windows 11
To open the Local Security Policy, open the Run command and type secpol.msc, press OK. The Local Security Policy window opens, similar to the Local Group Policy settings; follow the procedures described above.
Elevated Command Line for Account Lockout Policy in Windows 11
You can also customize the Password Policy by using the elevated command prompt. Open the Run command, type CMD, and press Ctrl + Shift + Enter. When the elevated command prompt/Administrative Command Prompt opens, type the command shown below and press ENTER:
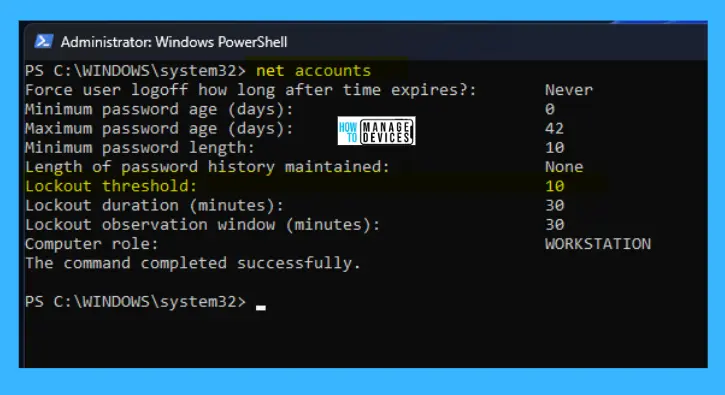
net accounts
After executing the above command, some options are available to make changes in the security settings. Here the Lockout threshold default value is Never.
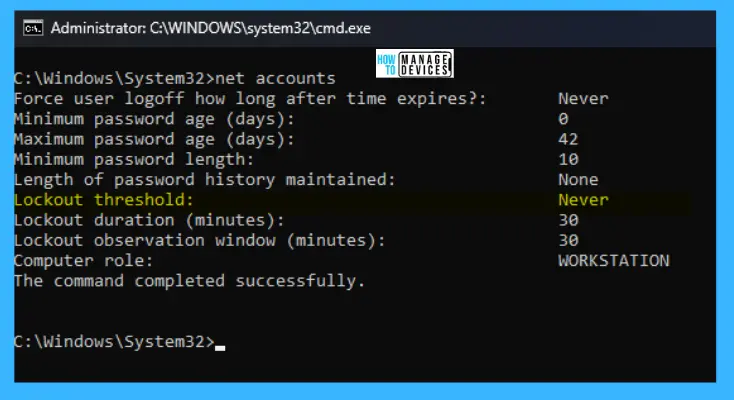
The details of the command prompt settings are illustrated in the table below for better appreciation.
| Security Policies | Default Value |
|---|---|
| Force the user logoff how long after the time expires | Never |
| Minimum Password age (days) | 0 |
| Maximum Password age (days) | 42 |
| Minimum Password Length | 10 |
| Length of password history maintained | None |
| Lockout threshold | Never |
| Lockout duration (minutes) | 30 |
| Lockout observation window (minutes) | 30 |
| Computer Role | WORKSTATION |
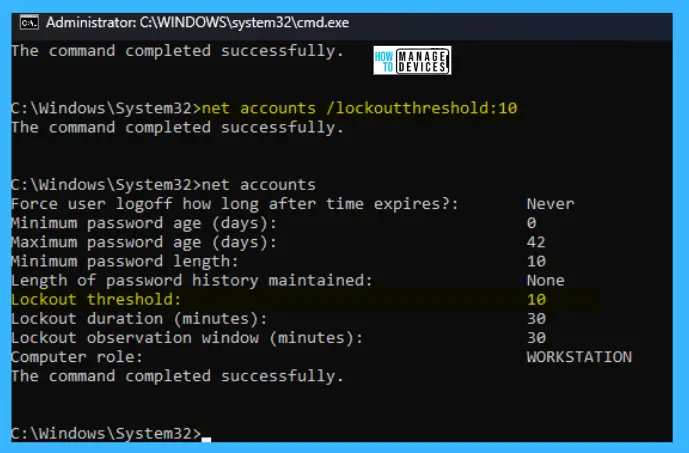
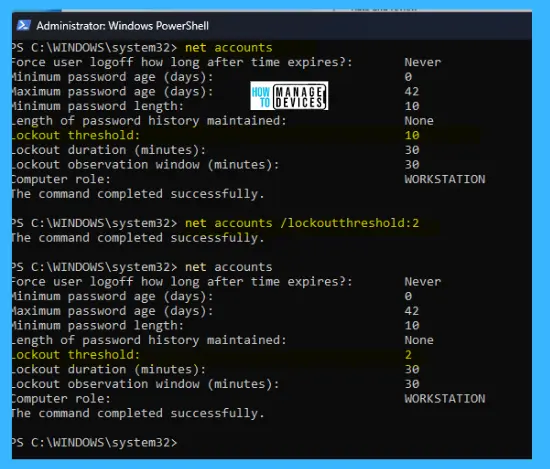
To change the threshold value from NEVER to some value, there is a command below to set the value.
net accounts /lockoutthreshold:10
PowerShell Scripts for Account Lockout Policy in Windows 11
Open the PowerShell in Administrator mode, then type the command net accounts and press ENTER to check the settings where users can easily change the settings.
In the terminal, enter the command net accounts /lockoutthreshold:2 (You can change the value as per your requirement) and press ENTER; the value of the lockout threshold has now changed; the process illustrates in the image below:
Intune Settings for Windows 11 Account Lockout Policies
Let’s look at Intune policy options to check the settings of the Account Lockout Policy. We have already seen 4 methods to do this in this post and the Intune settings catalog method to implement the same.
Go through Intune Settings Catalog Guide (linked below) to create the policy in detail. However, search with the following keyboard for this context: Account Lockout. This is what is explained in the following section.
NOTE! – More details on Intune settings catalog guide – Create Intune Settings Catalog Policy.
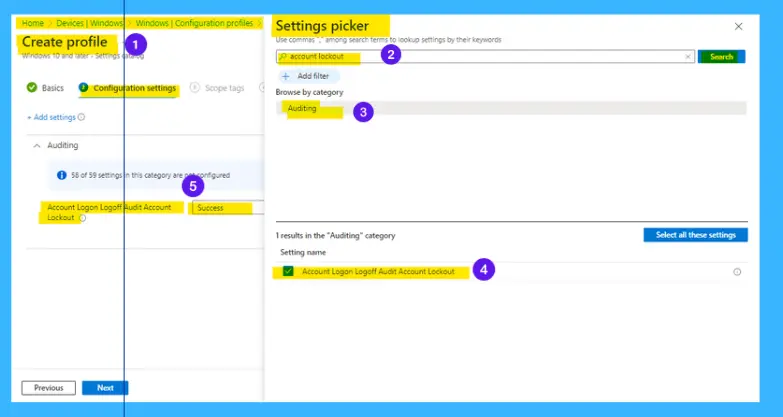
This policy setting allows you to audit events generated by a failed attempt to log on to an account locked out. If you configure this policy setting, an audit event is generated when an account cannot log on to a computer because the account is locked out.
Success audits record successful attempts and Failure audits record unsuccessful attempts. Logon events are essential for understanding user activity and detecting potential attacks. Note that this Intune policy is not really the account lockout policy. Rather, it’s the Audit Account lockout policy.
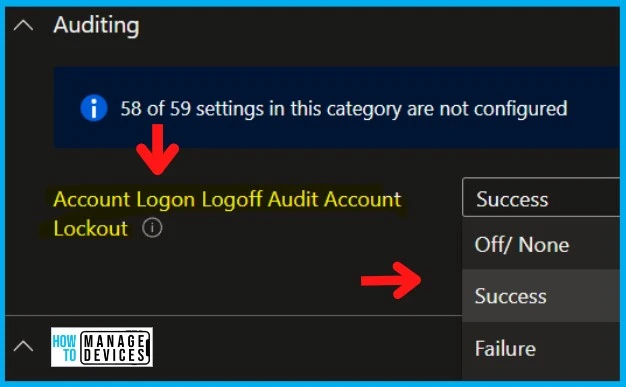
The Auditing policy available in Intune is Account Logon Logoff Audit Account Lockout, and this allows the admin to audit even logs during the Account Logon Logoff Audit Account Lockout. The following are the drop-down options:
- Off/None
- Success
- Failure
- Success + Failure
I hope the information about Windows Account Lockout Policy Settings using Intune and Group Policy is helpful. Please follow us on HTMD Community and visit our website HTMD Forum if you like our content.
Author
Alok is a Master of Computer Applications (MCA) graduate. He loves writing on Windows 11 and related technologies. He likes to share his knowledge, quick tips, and tricks with Windows 11 or Windows 10 with the community.

