Windows Autopilot Hybrid Azure AD Join troubleshooting is new to most of us. I thought of sharing my experience troubleshooting issues related to Hybrid Domain Join scenarios with Windows Autopilot.
[ Related Post – Windows Autopilot Hybrid Domain Join Step by Step Implementation Guide]
Introduction -Windows Autopilot Hybrid Azure AD Join
In a previous post (Windows Autopilot Hybrid Domain Join Step by Step Implementation Guide), we discussed Windows Autopilot Hybrid Azure AD Join Architecture and configured it.
Windows Autopilot Hybrid Azure AD Join scenario includes many puzzles.
- Active Directory
- Connectors
- Intune
- Autopilot
- AAD Connect
It’s essential to understand the workflow for troubleshooting Hybrid Windows Autopilot deployment. In this post, let’s discuss some common issues and critical troubleshooting areas of the Windows Autopilot Hybrid Azure AD Join scenario.
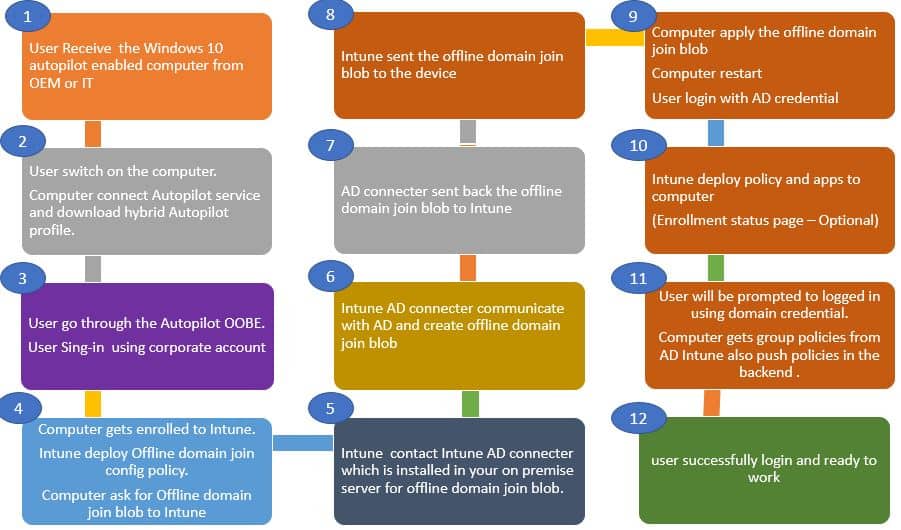
Multiple Computer Records | Windows Autopilot Hybrid Azure AD Join Troubleshooting Tips
Based on the Windows Autopilot deployment stage, you will see computer record changes in the Intune console.
You will also observe multiple records created for the same computer. This information helps to correlate at which stage autopilot deployment is getting failed. Let’s see some of the events.
Initially, a temp record is created when a Windows autopilot computer starts communicating with Intune cloud service. As shown below, the temp record will be in format.
If you don’t see this temp record created, perquisites are most likely not configured correctly. This issue should be because of any of the following reasons.
- EMS license assignment not done.
- The user doesn’t have permission for MDM Enrollment.
- Internet connectivity or proxy on your Windows 10 client
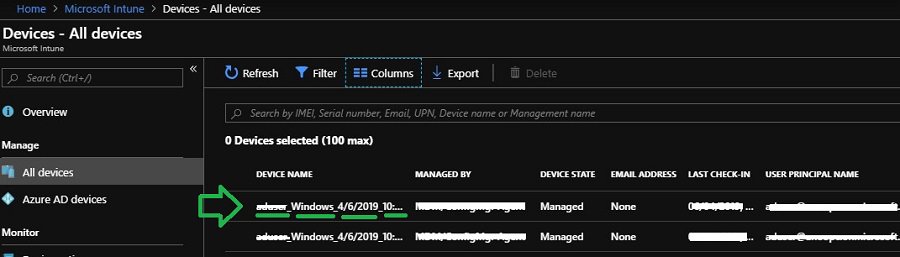
After some time, the temp record gets updated to the current name of the computer. Please note the laptop has not yet applied the offline domain join blob.
After a few minutes, Windows 10 machine gets an offline domain join blob from Intune.
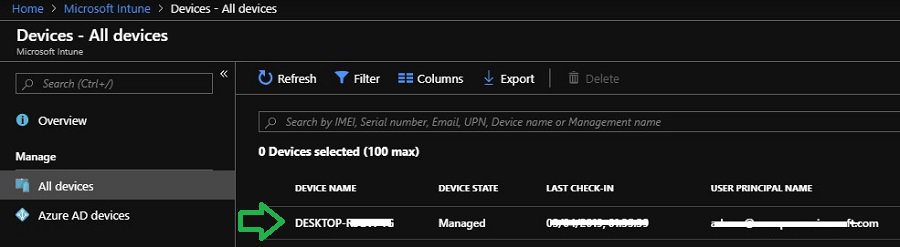
After offline domain join (in Windows Autopilot Hybrid Azure AD Join scenario), the computer record in Intune console gets updated as per the defined Computer naming template.
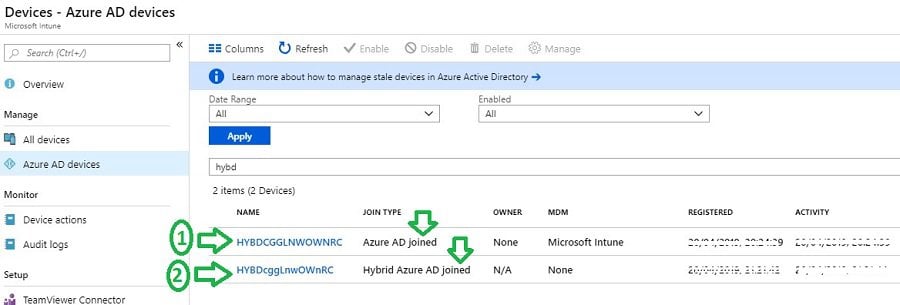
You may also observe multiple records for the same computer in the Intune console.
First, computer records get created as part of Intune communication. The second record is produced by AAD connect synced the new computer object from AD.
If you don’t see the record with the proper computer naming template, it states some issues. Most of the time, the problem lies within the Offline domain join blob deployment workflow.
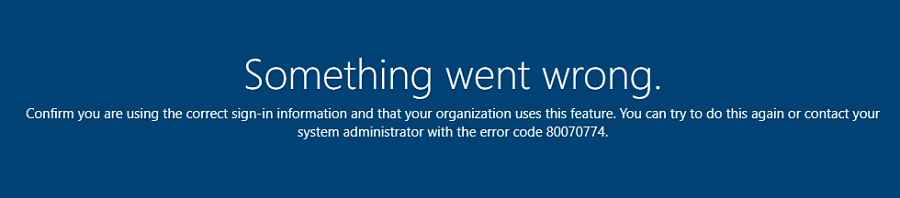
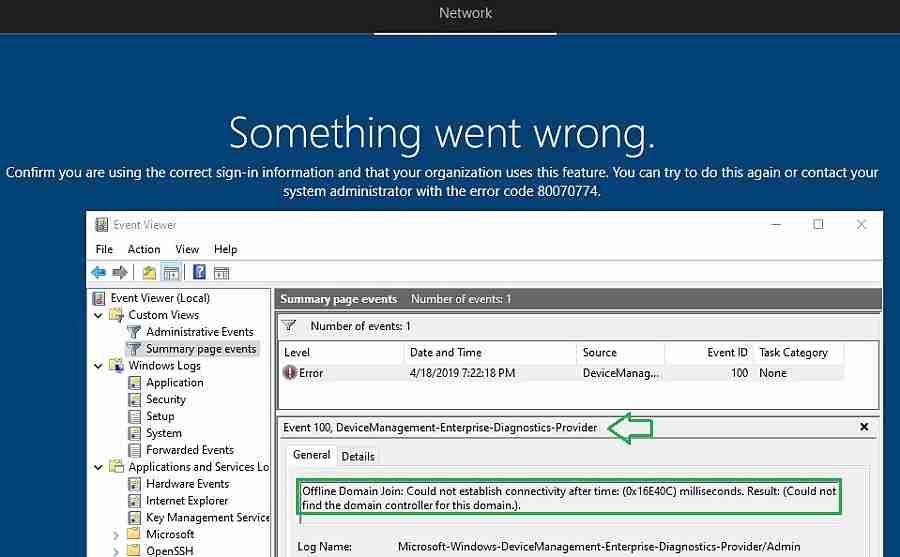
You may also encounter the below error.
To confirm you are using the correct sign-in information and that your organization uses this feature. You can try to do this again or contact your system administrator with the error code 80070774.
Server Side Troubleshooting
Let’s discuss common Offline domain join deployment (in Windows Autopilot Hybrid Azure AD Join scenario) issues and troubleshoot. Troubleshooting can be done from the server and client sides. Let’s talk about each one of them.
- Server-side
- Client-side
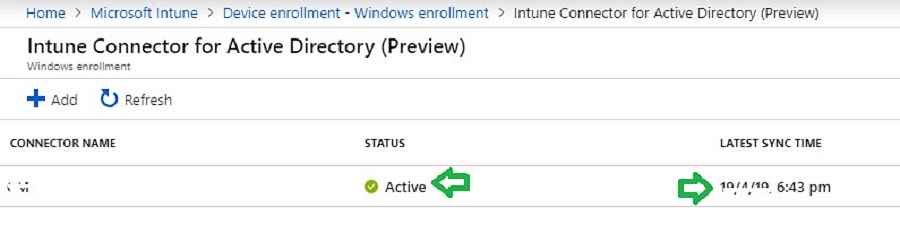
Intune AD connector connection health
Navigate to the below path to confirm the Intune AD connector connection health. Check whether your connector status is showing as Online and the latest sync time updated.
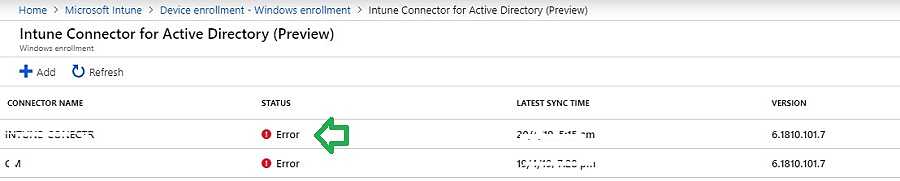
If you see any error shown below, your connector is not communicating with Intune.
Intune AD Connector Not Appearing
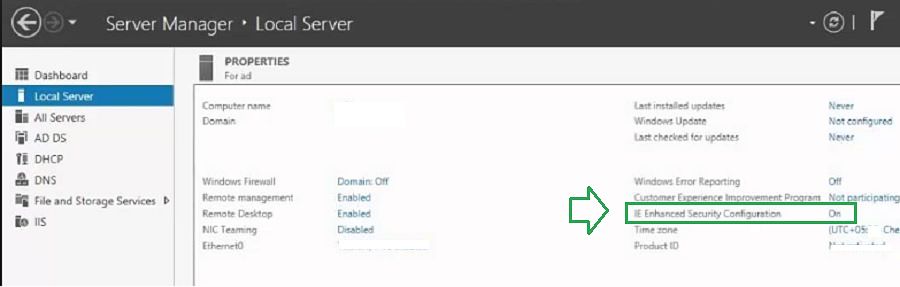
You have installed the console, and it got installed successfully. It gave the option to log in with ‘Global Admin’ credentials. You tried to log in with the credentials, but it does nothing.
It just shows the page of Microsoft, and the account status shows ‘Signed In.’
When you can’t see Intune Active Directory (AD) connector in the console, it might be due to IE Enhanced Security. IE Enhanced Security Configuration is defaulted on Windows Server 2016 or later. This security setting may block the website from displaying correctly during the Intune AD connector sign-in.
Chetan Sharma (in Intune professional Facebook Group) discusses a similar issue. You might have to temporarily turn off IE Enhanced Security mode to fix this issue.
You can turn it on after successful Intune AD connector enrollment.
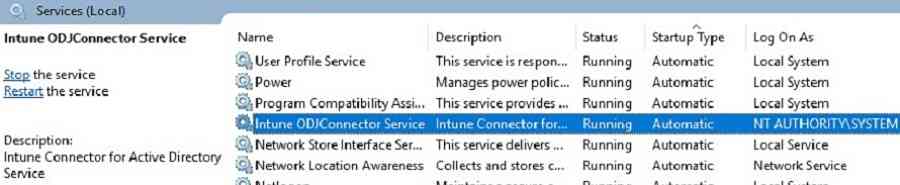
Intune ODJ connector service
If Intune ODJ Connector status shows offline, then verify connector service. It would help to make sure Intune ODJ connector service is “running” on your server.
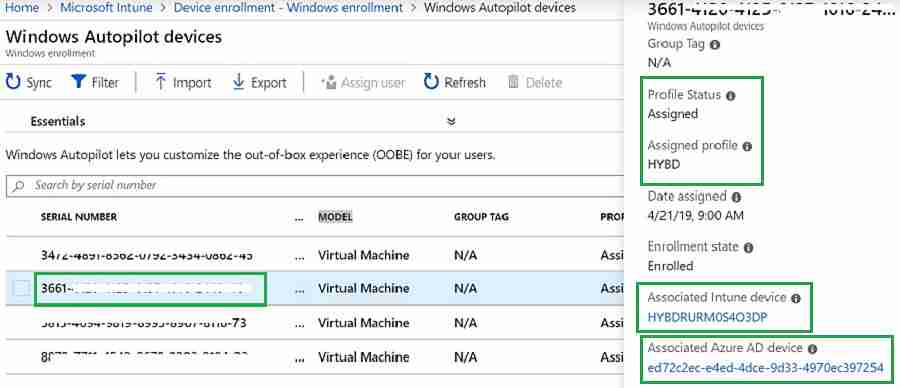
Association status | Windows Autopilot Hybrid Azure AD Join Troubleshooting Tips
For each imported autopilot serial number, a corresponding Intune record will be created when autopilot deployment starts, and a new record for that computer appears in the Intune console.
You can navigate the path below to find an association between hardware serial numbers and corresponding computer records.
I usually use this in troubleshooting to check the associated Azure device id, Intune device name, Autopilot profile assignment, and enrollment status.
Event Viewer – Hybrid Azure AD Join Troubleshooting Tips
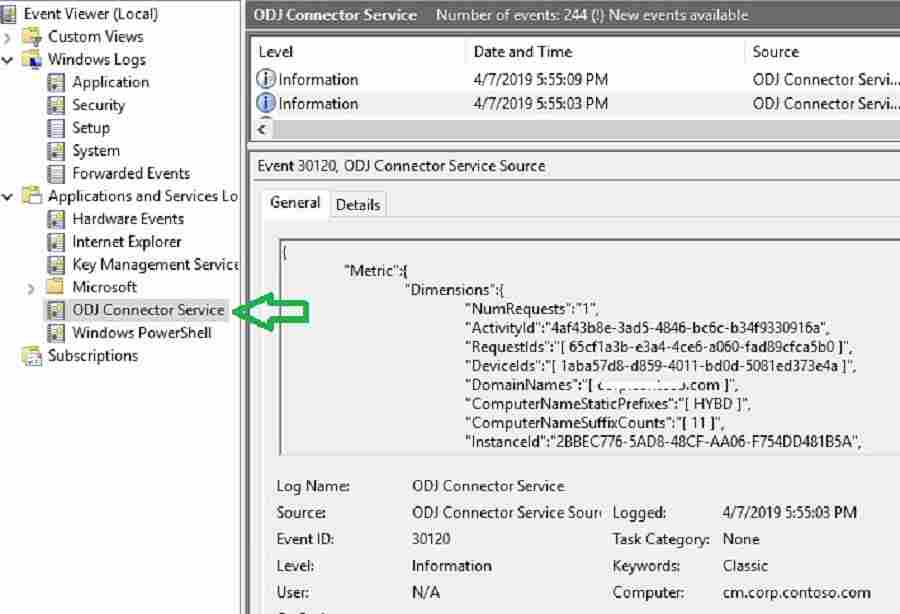
Let’s go through some of the events to track Intune, connector, and Domain controller communication. Activities related to Intune ODJ connector service logged in the Event Viewer. Launch the event viewer.
Navigate to the event log at “Application and Services Logs –> ODJ Connector Service.”
Below Event ID 30120 states Intune AD connector can download policy to generate Offline domain join blob.
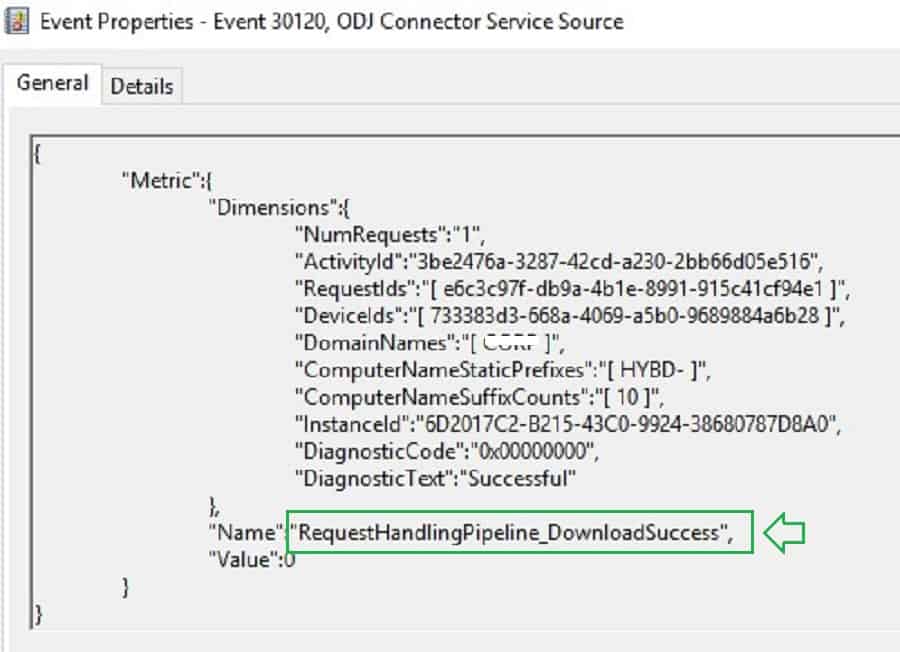
{
"Metric":{
"Dimensions":{
"NumRequests":"1",
"ActivityId":"c12037fe-52ed-4924-9898-08cdea7c48c8",
"RequestIds":"[ d302cfe6-b60f-4d56-9f3a-2abbd89c6882 ]",
"DeviceIds":"[ 59c1b762-1852-46e0-9ebe-439aab2d17f0 ]",
"DomainNames":"[ XXXXXXXX.com ]",
"ComputerNameStaticPrefixes":"[ HYBD ]",
"ComputerNameSuffixCounts":"[ 11 ]",
"InstanceId":"3B530FA1-F32B-4D61-BAD4-D7211D8603B3",
"DiagnosticCode":"0x00000000",
"DiagnosticText":"Successful"
},
"Name":"RequestHandlingPipeline_DownloadSuccess",
"Value":0
}Below, Event ID 30130 states Intune connector service can successfully create an offline domain join blob. You can also see the computer name generated.
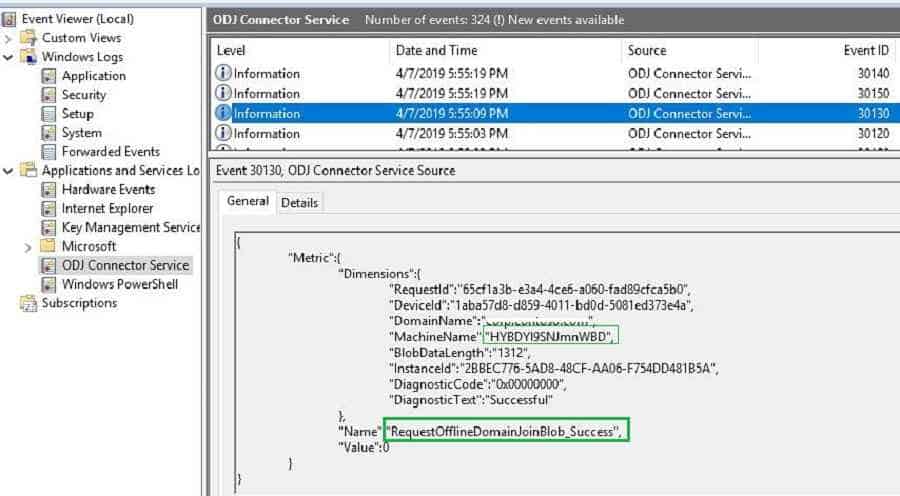
{
"Metric":{
"Dimensions":{
"RequestId":"d302cfe6-b60f-4d56-9f3a-2abbd89c6882",
"DeviceId":"59c1b762-1852-46e0-9ebe-439aab2d17f0",
"DomainName":"XXXXXX",
"MachineName":"HYBDcggLnwOWnRC",
"BlobDataLength":"1312",
"InstanceId":"3B530FA1-F32B-4D61-BAD4-D7211D8603B3",
"DiagnosticCode":"0x00000000",
"DiagnosticText":"Successful"
},
"Name":"RequestOfflineDomainJoinBlob_Success",
"Value":0
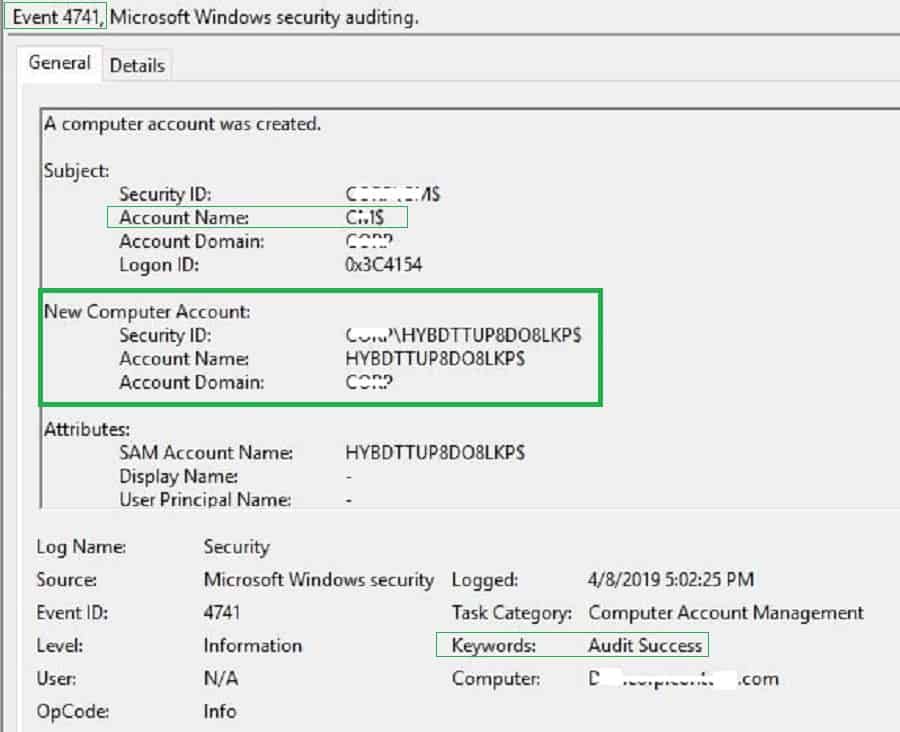
}If auditing is enabled, you can see the below event in the domain controller. A new computer object got created using the connector server (SERVER$) permission. So make sure Intune Connector Server has enough rights, as explained in the first post.
A computer account was created.
Subject:
Security ID: Domain\XXXX$
Account Name: SERVER$
Account Domain: Domain
Logon ID: 0x11ADCC4
New Computer Account:
Security ID: Domain\HYBDCGGLNWOWNRC$
Account Name: HYBDCGGLNWOWNRC$
Account Domain: Domain
Attributes:
SAM Account Name: HYBDCGGLNWOWNRC$
Display Name: -
User Principal Name: -
Home Directory: -
Home Drive: -
Script Path: -
Profile Path: -
User Workstations: -
Password Last Set: 4/20/2019 12:57:35 PM
Account Expires:
Primary Group ID: 515
AllowedToDelegateTo: -
Old UAC Value: 0x0
New UAC Value: 0x80
User Account Control:
'Workstation Trust Account' - Enabled
User Parameters: -
SID History: -
Logon Hours:
DNS Host Name: HYBDcggLnwOWnRC.XXXXXX.com
Service Principal Names:
HOST/HYBDcggLnwOWnRC.XXXXX.com
RestrictedKrbHost/HYBDcggLnwOWnRC.XXXX.com
HOST/HYBDCGGLNWOWNRC
RestrictedKrbHost/HYBDCGGLNWOWNRC
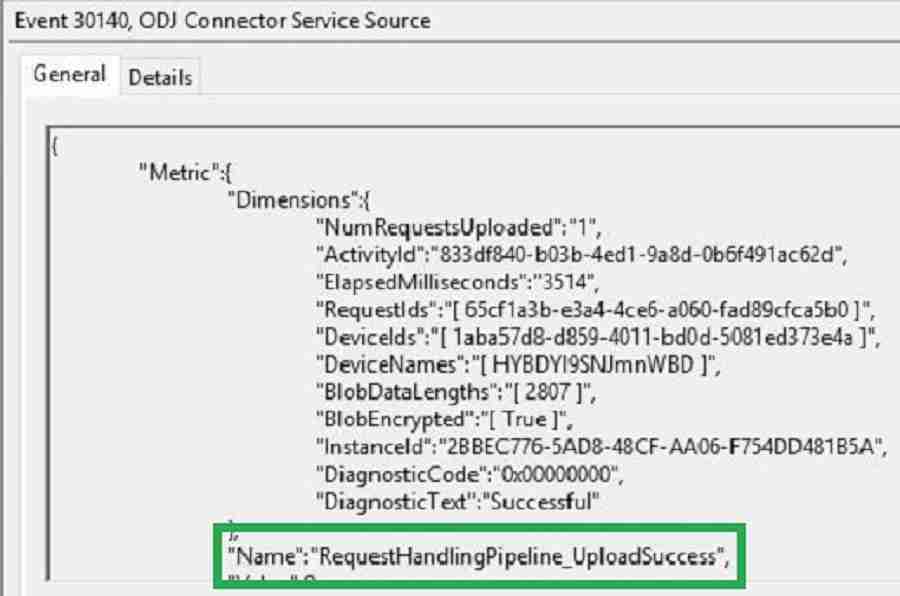
After successful offline Domain Join blob creation, Intune Active Directory connector uploads the blob to Intune. Below Event ID 30140, the state connector service can upload the Offline blob to Intune. Intune connector acts as a mediator between Intune and Domain controller.
Source: ODJ Connector Service Source
Date: 4/20/2019 12:57:41 PM
Event ID: 30140
Keywords: Classic
User: N/A
Computer: XXXXXXXX.com
Description:
{
"Metric":{
"Dimensions":{
"NumRequestsUploaded":"1",
"ActivityId":"69d8506b-e352-42d1-a457-76e43e2a2d21",
"ElapsedMilliseconds":"1706",
"RequestIds":"[ d302cfe6-b60f-4d56-9f3a-2abbd89c6882 ]",
"DeviceIds":"[ 59c1b762-1852-46e0-9ebe-439aab2d17f0 ]",
"DeviceNames":"[ HYBDcggLnwOWnRC ]",
"BlobDataLengths":"[ 2807 ]",
"BlobEncrypted":"[ True ]",
"InstanceId":"3B530FA1-F32B-4D61-BAD4-D7211D8603B3",
"DiagnosticCode":"0x00000000",
"DiagnosticText":"Successful"
},
"Name":"RequestHandlingPipeline_UploadSuccess",
"Value":0
}
If you see any errors during offline blob upload, make sure there is no firewall or proxy blocking communication between the connector and Intune service.
If you have a proxy in your environment, you need to ensure it’s configured as mentioned in the pre-requisites.
Client-side Troubleshooting
I have explained the basics of Autopilot troubleshooting in one of my previous posts.
Event Viewer
Launch the event viewer and navigate to the below path. You will find some useful information logged in Diagnostics provider logs for troubleshooting.
Error 1 – 80070774 –Something Went Wrong
"Confirm you are using the correct sign-in information and that your organization uses this feature.you can try to do this again or contact system administrator with error code 80070774."
The error results from time out during offline domain join blob deployment workflow. As basic troubleshooting, you need to verify whether the connector server is healthy and active, as explained earlier.
Also, it would help if you verified whether you could ping your domain controller and connector server from the client. After offline domain join computer requires a reboot. But the machine will not reboot until it can establish communication with the Domain controller.
NOTE! – Another possibility for this error is when the computer name “prefix” is not configured correctly.
Error 2 – 80180005
"There was an error communicating with server.you can try to do this again or contact your system administrator with the error code 80180005."
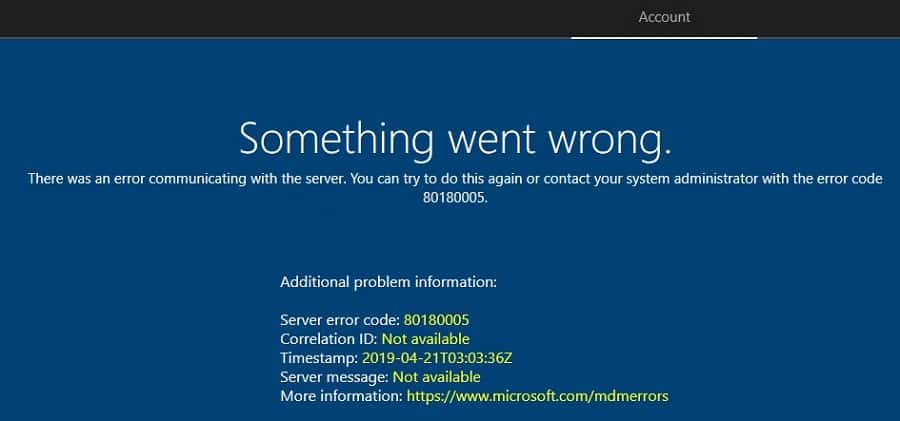
There can be many reasons for the above error. In most cases, this occurs if the computer name prefix is not configured correctly. In previews Post 1, we configured the computer naming template.
Make sure you don’t use any variables in the computer naming template. An unsupported computer name will result in an “80180005” or “80070774” error code.
In the computer, naming templates use simple prefixes such as HYBD and ABC.
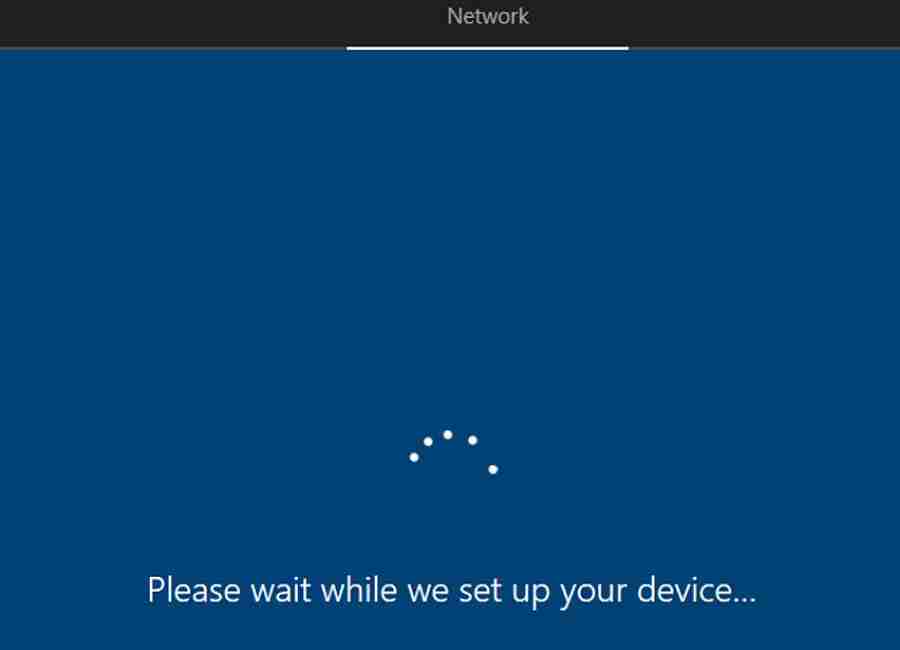
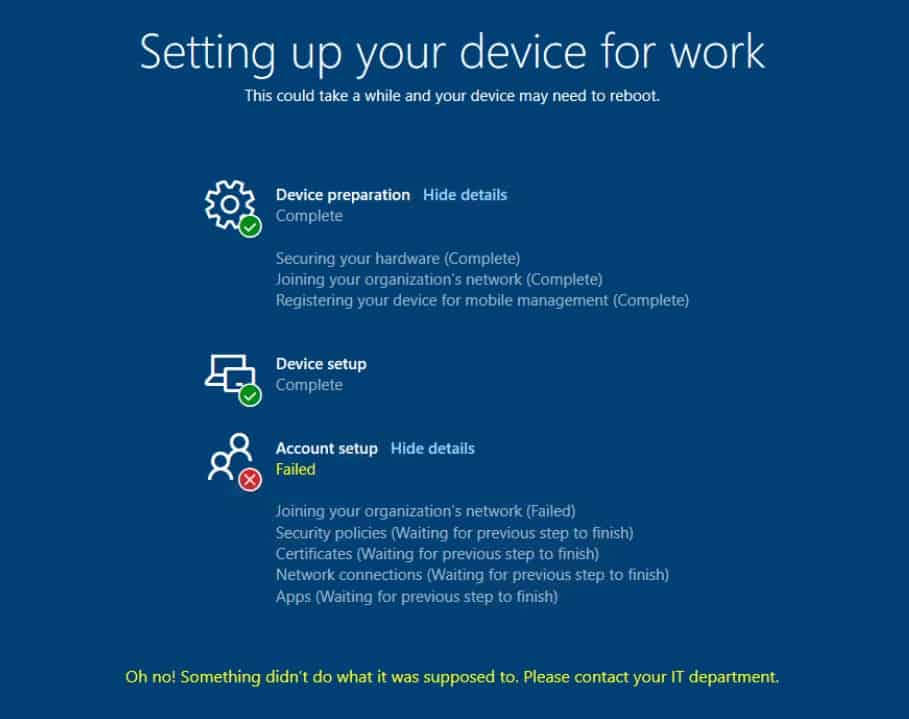
Windows Autopilot Error 3 – Please wait while we set up your device
During Windows Autopilot Azure AD Join profile deployment, it’s reasonable that the computer takes a bit more time on the below screen.
But if there are any issues, the computer will get stuck at the below screen and finally timeout with an error.
In this scenario, press Shift + F10 to get command prompt support. Then try to ping the DC and internet URLs from the machine.
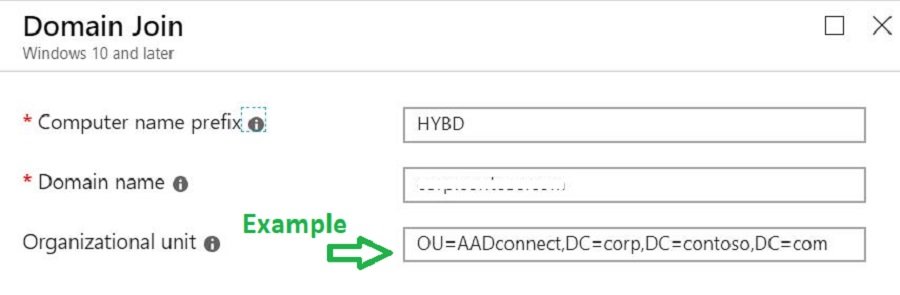
The other timeout error is when the OU path is not set correctly. Please make sure you configure the Domain Join profile correctly, as explained in the previous post.
Note: You should set the organization unit in the correct format, as shown below.
Domain Join Logs
Check the netsetup.log to check whether the computer received an offline domain join blob from Intune or not. You can navigate to the below location and analyze the log while troubleshooting.
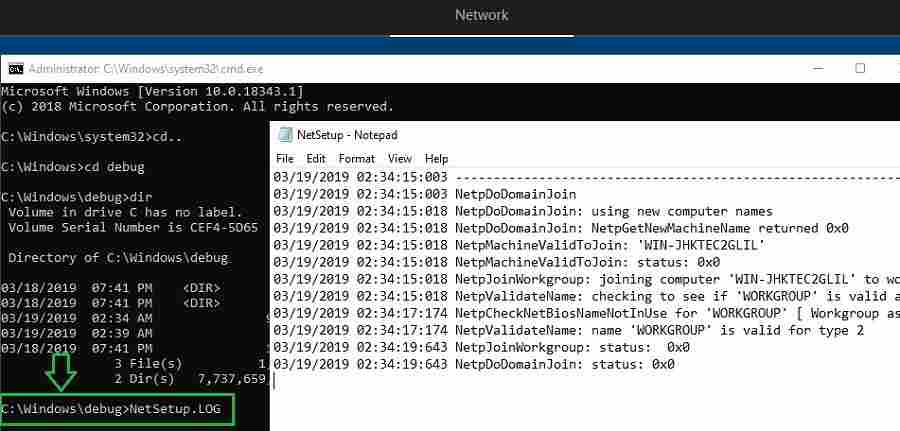
Netsetup.log records Domain join events before and after applying offline domain join blob.
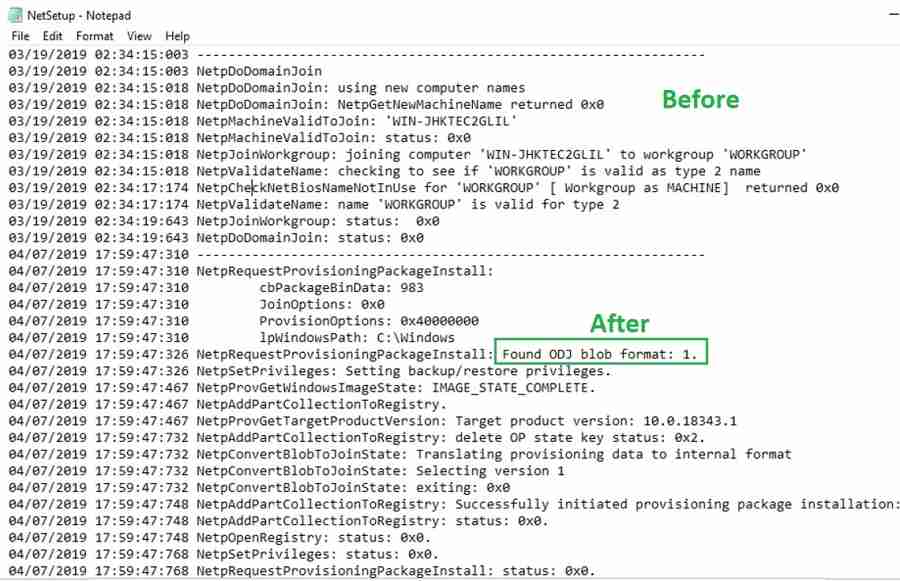
After a few minutes, the offline domain join blob gets applied successfully.
03/19/2019 02:34:15:003 -----------------------------------------------------------------
03/19/2019 02:34:15:003 NetpDoDomainJoin
03/19/2019 02:34:15:018 NetpDoDomainJoin: using new computer names
03/19/2019 02:34:15:018 NetpDoDomainJoin: NetpGetNewMachineName returned 0x0
03/19/2019 02:34:15:018 NetpMachineValidToJoin: 'WIN-JHKTEC2GLIL'
03/19/2019 02:34:15:018 NetpMachineValidToJoin: status: 0x0
03/19/2019 02:34:15:018 NetpJoinWorkgroup: joining computer 'WIN-JHKTEC2GLIL' to workgroup 'WORKGROUP'
03/19/2019 02:34:15:018 NetpValidateName: checking to see if 'WORKGROUP' is valid as type 2 name
03/19/2019 02:34:17:174 NetpCheckNetBiosNameNotInUse for 'WORKGROUP' [ Workgroup as MACHINE] returned 0x0
03/19/2019 02:34:17:174 NetpValidateName: name 'WORKGROUP' is valid for type 2
03/19/2019 02:34:19:643 NetpJoinWorkgroup: status: 0x0
03/19/2019 02:34:19:643 NetpDoDomainJoin: status: 0x0
04/21/2019 08:50:40:808 -----------------------------------------------------------------
04/21/2019 08:50:40:808 NetpRequestProvisioningPackageInstall:
04/21/2019 08:50:40:808 cbPackageBinData: 983
04/21/2019 08:50:40:808 JoinOptions: 0x0
04/21/2019 08:50:40:808 ProvisionOptions: 0x40000000
04/21/2019 08:50:40:808 lpWindowsPath: C:\Windows
04/21/2019 08:50:40:808 NetpRequestProvisioningPackageInstall: Found ODJ blob format: 1.
04/21/2019 08:50:40:808 NetpSetPrivileges: Setting backup/restore privileges.
04/21/2019 08:50:40:982 NetpProvGetWindowsImageState: IMAGE_STATE_COMPLETE.
04/21/2019 08:50:40:982 NetpAddPartCollectionToRegistry.
04/21/2019 08:50:40:982 NetpProvGetTargetProductVersion: Target product version: 10.0.18343.1
04/21/2019 08:50:41:152 NetpAddPartCollectionToRegistry: delete OP state key status: 0x2.
04/21/2019 08:50:41:152 NetpConvertBlobToJoinState: Translating provisioning data to internal format
04/21/2019 08:50:41:152 NetpConvertBlobToJoinState: Selecting version 1
04/21/2019 08:50:41:152 NetpConvertBlobToJoinState: exiting: 0x0
04/21/2019 08:50:41:168 NetpAddPartCollectionToRegistry: Successfully initiated provisioning package installation: 1/1 part(s) installed.
04/21/2019 08:50:41:168 NetpAddPartCollectionToRegistry: status: 0x0.
04/21/2019 08:50:41:168 NetpOpenRegistry: status: 0x0.
04/21/2019 08:50:41:168 NetpSetPrivileges: status: 0x0.
04/21/2019 08:50:41:168 NetpRequestProvisioningPackageInstall: status: 0x0.
04/21/2019 08:54:12:726 -----------------------------------------------------------------
04/21/2019 08:54:12:726 NetpProvCheckOfflineLsaPolicyUpdate
04/21/2019 08:54:12:726 NetpMachineValidToJoinPhase3: 'HYBD6T03Oyzzs8P'
04/21/2019 08:54:12:741 NetpMachineValidToJoinPhase3: status: 0x0
04/21/2019 08:54:12:741 NetpProvCheckOfflineLsaPolicyUpdate: status: 0x0
04/21/2019 08:54:20:164 -----------------------------------------------------------------
04/21/2019 08:54:20:164 NetpProvContinueProvisioningPackageInstall:
04/21/2019 08:54:20:164 Context: 1
04/21/2019 08:54:20:164 NetpProvGetWindowsImageState: IMAGE_STATE_COMPLETE.
04/21/2019 08:54:21:227 NetpCreatePartListFromRegistry: status: 0x0.
04/21/2019 08:54:21:227 NetpCompleteOfflineDomainJoin
04/21/2019 08:54:21:227 fBootTimeCaller: TRUE
04/21/2019 08:54:21:227 fSetLocalGroups: FALSE
04/21/2019 08:54:21:321 NetpJoinDomainLocal: NetpHandleJoinedStateInfo returned: 0x0
04/21/2019 08:54:21:652 NetpJoinDomainLocal: NetpManageMachineSecret returned: 0x0.
04/21/2019 08:54:22:074 NetpJoinDomainLocal: status of setting LSA pri. domain: 0x0
04/21/2019 08:54:22:074 NetpJoinDomainLocal: Updating W32TimeConfig
04/21/2019 08:54:22:324 NetpCompleteOfflineDomainJoin: status: 0x0
04/21/2019 08:54:22:324 NetpProvContinueProvisioningPackageInstall: status: 0x0.
04/21/2019 08:54:22:921 -----------------------------------------------------------------
04/21/2019 08:54:22:921 NetpProvContinueProvisioningPackageInstall:
04/21/2019 08:54:22:921 Context: 2
04/21/2019 08:54:22:921 NetpProvGetWindowsImageState: IMAGE_STATE_COMPLETE.
04/21/2019 08:54:22:921 NetpCreatePartListFromRegistry: status: 0x0.
04/21/2019 08:54:22:921 NetpCompleteOfflineDomainJoin
04/21/2019 08:54:22:921 fBootTimeCaller: TRUE
04/21/2019 08:54:22:921 fSetLocalGroups: TRUE
04/21/2019 08:54:22:937 NetpManageLocalGroupsForJoin: Adding groups for new domain, removing groups from old domain, if any.
04/21/2019 08:54:24:234 NetpManageLocalGroupsForJoin: status of modifying groups related to domain 'XXX' to local groups: 0x0
04/21/2019 08:54:24:234 NetpManageLocalGroupsForJoin: INFO: No old domain groups to process.
04/21/2019 08:54:24:234 NetpCompleteOfflineDomainJoin: NetpManageLocalGroupsForJoin returned code: 0x0.
04/21/2019 08:54:24:234 NetpCompleteOfflineDomainJoin: status: 0x0
04/21/2019 08:54:24:234 NetpProvContinueProvisioningPackageInstall: Provisioning package installation completed successfully.
04/21/2019 08:54:24:234 NetpProvContinueProvisioningPackageInstall: delete OP state key status: 0x0.
04/21/2019 08:54:24:234 NetpProvContinueProvisioningPackageInstall: status: 0x0.
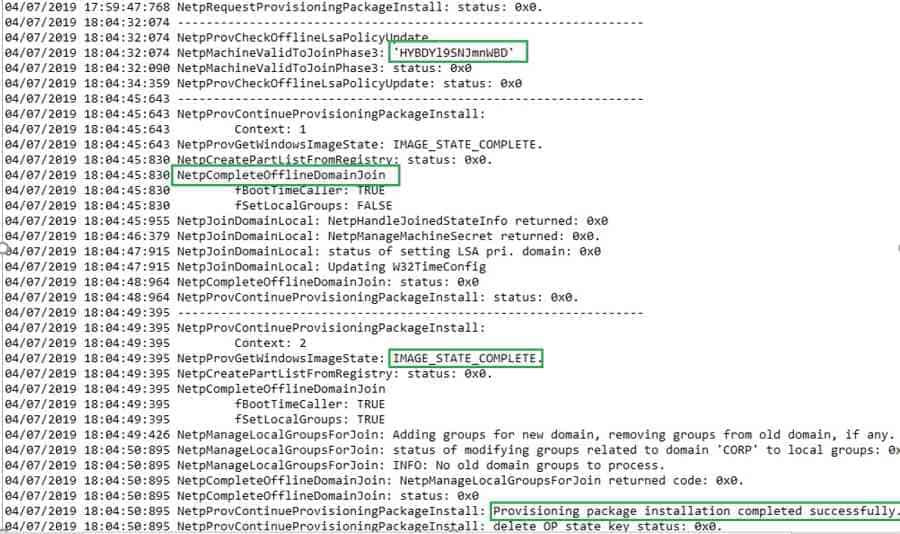
After applying the offline domain join blob, the computer will restart. At this point, Windows 10 computer should have AD connectivity; after computer, restart user can log in with Domain credentials.
Enrollment Status Page (ESP)
After the user signs in, there will be an enrollment status screen whenever your tenant’s Intune enrollment status page (ESP) is configured.
Ensure you configure the below CSP to skip the user policy during the ESP screen.
- OMA-URI: ./Vendor/MSFT/DMClient/Provider/MS DM Server/FirstSyncStatus/SkipUserStatusPage
- Data type: Boolean
- Value: True
If the CSP policy is not configured, you may get an error, as shown below.
NOTE! – Why CSP configuration is required to skip the user policy during the ESP screen?
As we know, during Autopilot deployment computer is first joined to AD Domain. The machine is still not yet marked as Hybrid Azure AD joined. AAD Connect is responsible for the computer object in AD syncing to Azure AD.
The AAD connect usually takes at least 30 minutes to process the computer object and sync to Azure AD. Because of this delay, you may encounter a timeout error on the Enrollment Status page.
Intune will not deploy any user-targeted policies until the computer object is synced to Azure and authenticated.
At this point, the workaround is to skip user-targeted policies during the Enrollment status page. However, Intune will start deploying User policies once the computer receives the user token(typically 30 min). It is recommended to go through Michael Niehaus’s blog for more details.
Additional Tips
All credits to Michael Niehaus and Sandys (presented during MMS). Also, thank you, Daniel Ratliff, for sharing this information on Twitter.
8007 Window Autopilot Errors are Win32 Errors (Network or related errors).
0x800705B4 = timeout
0x80070774 = domain controller not found
801C Windows Autopilot Errors are Azure AD Join / Device Registration related issues.
0x801C0003 = Device Authorization error (not authorized to join Azure AD, exceeded device limit).
8018 Windows Autopilot errors are MDM Enrollment related issues.
0x80180003 = authorization (user not authorized to enroll).
0x80180005 = Server error (enrollment rejected, scenario not enabled, etc.).
0x80180014 = Device not supported (enrollment restrictions rules).
0x80180018 = No user license (Azure AD premium or Intune licenses are NOT assigned).
8000 Windows Autopilot errors are mostly due to Windows-related Errors.
0x80004005 = Generic error (fail).

Resources
- 1. Beginners Guide Setup Windows Autopilot Deployment
- 2. Dynamically Deploy Security Policies and Apps to Windows Autopilot Devices
- 3. Where is Autopilot Assign Profile Button in Intune Portal
- 4. Windows Autopilot End to End Process Guide
- 5. Repurpose/Reprovision Existing Devices to Windows Autopilot
- 6. Windows AutoPilot Profile AAD Dynamic Device Groups.
- 7. Windows Autopilot License Requirements

Hello,
Great article. I have a question.
I perform a Hybrid Azure AD join via Autopilot, but many of my devices are duplicated twice.
One is Azure AD Joined and one will be blank.
How do we prevent duplicate entries?
There will be multiple records and cannot be prevented as of now. I have not came across any official statement on this.
has there been any update with this dual state? I too have Hybrid AD joined devices, as well as Azure AD joined devices in Azure AD. Is there any reason why there are two records, they have seperate GUIDs. As soon as I add the device to Autopilot using the HWID, it Azure AD joins.
this behavior still exist as per my knowledge…
Hello, I am having issues with the Hybrid Join. This article is great and I should have everything setup as per this article, however we cannot get it working.
I did the following:
– ensured server w/ Intune ODJ connector has been delegated full rights to the OU
– Intune ODJ Connector showing active in Intune
– I used generic hostname e.g. TEST rather that consist of variables and ensured DN
Issue that is occurring is it gets stuck on setting up device for 20 minutes or so then errors out to 80070774. This happens on multiple devices and have tried various user accounts. We have also tried to enroll manually on a non-domain joined Win 10 1809 PC and it fails so it seems somehow the Intune ODJ Connector is not communicating at all during the setup. The “domain join” profile doesn’t seem to be working at all and devices would sit in not applicable.
I currently have a ticket open with Microsoft but it’s been 2 weeks and their technicians are unable to resolve this issue. They verified our setup and confirmed it is correct. I read on technet forums other users are experiencing the exact same problem.
If you or anyone here can shed some light on what else we can check.
Thanks
Just for testing please dont mention any OU path. Let Intune create object in be default computers OU. Please delegate the permission to default “computer” OU
Also As mentioned in the post , please check Association status between hardware serial number and corresponding computer record is correct.
Please let me know
Thanks for the response Vimal. Still no go. I left OU blank, granted full control to Computers OU, also no errors/change in Intune ODJ Connector event viewer.
I did a quick test, while it’s stuck on configuring. If I run powershell command to join to AD, it restarts and autopilot completes after 10 minutes. Hybrid join is successful if I do that cheat.
Definitely something is not working with the workplacejoin profile and Intune ODJ Connector. It shows actively syncing on Intune w the Connector. Let me know what else I should check.
Hey Vismal and everyone,
just an update, Microsoft suggested I try this on build 1903 and voila it worked. I tried again another 1809 system, it failed. I am asking them to confirm if 1903 is the minimum build for hybrid join. They said they found some bugs on 1809 which was fixed in 1903!
I have the same problem. Do I need to enable the device to write back within Azure AD Connect?
Hi Vimal
Great Post. I would like to know, is it possible to join a new computer to Hybrid Azure AD without the Premium Intune license that allows auto device enrollment.
I’m running a lab environment with Server 2016 and W10 1903 and my screen is stuck at ” Please wait we are setting up”. I can ping the domain and google.com, but not microsoft.com.
Hey
I am getting error 80004005, ours is hybrid azure AD. It was working and suddenly it stopped.What could be the reason?
Jino
Thank you. I have doing a lot of testing with Autopilot SelfDeploy profile.
But after som re-testing the devices are getting.
“801C Windows Autopilot Errors are Azure AD Join / Device Registration related issues.
0x801C0003 = Device Authorization error (not authorized to join Azure AD, exceeded device limit).”
Devices use to work on alle Autopilot SelfDeploy attempts. But after some retries (same device’s) they wont work anymore (Failed 3, 0x801C0003 during “Registering your device for mobile Managements”.
What device limit, and how duo i fix this ?
i dont think it is due to device limit. Selfdeploy profile joins Azure AD without putting credentials.however to check the device limit open Azure Active Directory service and click on Devices then click on Device Settings. you can find the setting “Maximum number of devices per user”.
since its a selfdeploy profile please check the troubleshooting steps mentioned below
https://oofhours.com/2019/07/09/tpm-attestation-what-can-possibly-go-wrong/
https://docs.microsoft.com/en-us/intune/enrollment/troubleshoot-windows-enrollment-errors#this-user-is-not-authorized-to-enroll
” Error 0x801c003: “This user is not authorized to enroll. You can try to do this again or contact your system administrator with the error code (0x801c0003).” Error 80180003: “Something went wrong. This user is not authorized to enroll. You can try to do this again or contact your system administrator with error code 80180003.”
Cause: Any of the following conditions:
The user has already enrolled the maximum number of devices allowed in Intune.
The device is blocked by the device type restrictions.
The computer is running Windows 10 Home. However, enrolling in Intune or joining Azure AD is only supported on Windows 10 Pro and higher editions. “
Hi Roar,
Did you finally resolve this issue. I am currently experiencing the same problem after a series of successful tests of autopilot in self-deploying mode. Autopilot fails during the device preparation phase giving the error 0x801c0003 at device registrations step. I have tried to register a different device manually and that seems to be working. Any ideas as to how to resolve this would be appreciated.Thanks.
I’m having an issue with a test machine I’m attempting to autopilot and Hybrid Azure AD Join. It seems to get through nearly all of the setup without a problem, installs the requested applications but on the last step when it looks like its going to reboot it just hangs at a black screen. I can still see the mouse cursor moving but nothing I do will bring up a window or anything. I’ve left it this way for about an hour or so and it still hasn’t done anything new. I’d hate to shut it down or reboot it but I don’t think its doing anything anymore.
Has anyone seen this problem?
Are you observing this on multiple machine ?
How can i delete offline domain join connector
using Graph explorer or powershell
Basics are here https://www.anoopcnair.com/fetch-azure-ad-details-microsoft-graph-api-via-web-browsers/ but you can explore more here https://github.com/microsoftgraph/powershell-intune-samples
I am having odd issues with Hybrid Azure AD Join devices. When I go through the process, the AAD/Intune associated object name is DESKTOP-xxxxx but the AD object has the correct name from the domain join profile. However, during the process, the device will eventually time out with the 80070774 error and never reboots. I don’t understand this as the AD object is created correctly which should indicate that the communication between connector and AD is happening. Right? The other confusing thing is that the associated Intune/AAD name is incorrect (DESKTOP-). This was working last week. The only thing that changed is the person who installed the connector, left the company.
do you see any error in Diagnostics provider eventviewer on your windows 10 . Are you able to login using local admin account and check eventviewr on Win 10 ?
is there a updated list of URL to be bypassed in client proxy to go through Hybrid AAD process. we have whitelisted almost 100 MS link , still the testing ended with error code 0x80070774. also observed there are blocked traffic from MS public IP’s before the failure, so there might be more URL to be whitelisted? we are using 1909 version for testing. Please let know on any advise on this case.
Hi,
We have followed all the steps and it seems that we have everything as shown in your publication, the only issue is that the laptop enrolled for hybrid is stuck in the last part in the account configuration and I wonder if this has something to do, in the ODJ Connector Service I have an event with this message:
{
“Metric”: {
“Dimensions”: {
“InstanceId”: “8B56CD7F-4C33-431A-AEBE-4CD1FE2B9961”,
“DiagnosticCode”: “0x00000000”,
“DiagnosticText”: “Successful”
},
“Name”: “RequestHandlingPipeline_Download_NoWork”,
“Value”: 0
}
}
Hello
We have the same problem currently… in the event viewer also same message. Have you found out what the error was causing?
Thanks
Niklas
I think the resolution or fix has been provided in the post itself. Have you already tried this pls
H
Unfortunately not… my autopiloted devices are DomainJoined but there are no events for the Intune Connector ODJ (nothing in event viewer). Always ends in a red error screen with error 0x80070002. Already tried to reinstall the ODJ on an other server, switched network for device to setup, have newest Win 2004 but still always red. May you have an idea?
Have you enabled the ping option from the autopilot profile configuration? Hopefully, you have opened required communication flow towards Domain controllers as per the documentation.
0x80070002 translates to The system cannot find the file specified.
Source: Windows
—–
%1
Source: Winhttp
—–
In the deployment profile I have set it to “Skip AD connectivity check”, and this should also work out for this scenario (White Glove no user login) so no connectivity to dc is required. Although even on the corporate network with direct ping it is still failing.
I think my main problem is really that the Intune Connector has no events for any offline domain join events. (never recieves anything) Do you may know if the server with the connector needs any open ports?
Thanks for your help!
Getting error “confirm you are using the correct sign-in information and that your organisation use this feature.you can try to do this again or contact your system administrator with the error code 80070774”
Computer object getting created as specified in OU in domain join profileas per name given.
Getting below error in event Id ODJ connector.
“Metric”:{
“Dimensions”:{
“InstanceId”:”7C568A09-40B8-439C-9F3F-32760FF8C7CE”,
“DiagnosticCode”:”0x0000040F”,
“DiagnosticText”:”HTTP request is unsuccessful. [Exception Message: \”DiagnosticException: 0x0000040F. HTTP request is unsuccessful.\”] [Exception Message: \”odjHttp.Call failed. activityId=13cf79a1-609a-4b89-9685-ef444fa6fc8a parameters={
\”options\”:{
\”batchSize\”:null,
\”connectorBuildVersion\”:\”6.1810.101.7\”,
\”connectorName\”:\”WIN-6VTK4QAL43Q\”
}
}\”] [Exception Message: \”Expected:OK Responded:401 (Unauthorized)\”] [Exception Message: \”{
\”ErrorCode\”:\”Forbidden\”,
\”Message\”:\”{\\r\\n \\\”_version\\\”: 3,\\r\\n \\\”Message\\\”: \\\”An error has occurred – Operation ID (for customer support): 00000000-0000-0000-0000-000000000000 – Activity ID: 13cf79a1-609a-4b89-9685-ef444fa6fc8a – Url: https:\/\/fef.msuc02.manage.microsoft.com\/RAODJPlus\/StatelessODJService\/34893bcc-ffff-1253-0605-061200594025\/odjConnector\/acquirePendingRequests\\\”,\\r\\n \\\”CustomApiErrorPhrase\\\”: \\\”\\\”,\\r\\n \\\”RetryAfter\\\”: null,\\r\\n \\\”ErrorSourceService\\\”: \\\”\\\”,\\r\\n \\\”HttpHeaders\\\”: \\\”{
\\\\\\\”WWW-Authenticate\\\\\\\”:\\\\\\\”Mutual realm=\\\\\\\\\\\\\\\”CN=SC_Online_Issuing,
CN=Microsoft Intune EAS Connector CA,
CN=Microsoft Intune NDES Connector CA,
CN=Microsoft Intune ConfigMgr Connector CA,
CN=Microsoft Intune ODJ Connector CA,
CN=Microsoft Intune ImportPFX Connector CA\\\\\\\\\\\\\\\”\\\\\\\”
}\\\”\\r\\n}\”,
\”Target\”:null,
\”Details\”:null,
\”InnerError\”:null,
\”InstanceAnnotations\”:[]
}\”]”
},
“Name”:”RequestHandlingPipeline_DownloadFailure”,
“Value”:0
}
{
“Metric”:{
“Dimensions”:{
“InstanceId”:”7C568A09-40B8-439C-9F3F-32760FF8C7CE”,
“DiagnosticCode”:”0x0000040F”,
“DiagnosticText”:”HTTP request is unsuccessful. [Exception Message: \”DiagnosticException: 0x0000040F. HTTP request is unsuccessful.\”] [Exception Message: \”odjHttp.Call failed. activityId=1e856a21-1a04-4e96-8b09-0e1add157829 parameters={
\”options\”:{
\”batchSize\”:null,
\”connectorBuildVersion\”:\”6.1810.101.7\”,
\”connectorName\”:\”WIN-6VTK4QAL43Q\”
}
}\”] [Exception Message: \”Expected:OK Responded:401 (Unauthorized)\”] [Exception Message: \”{
\”ErrorCode\”:\”Forbidden\”,
\”Message\”:\”{\\r\\n \\\”_version\\\”: 3,\\r\\n \\\”Message\\\”: \\\”An error has occurred – Operation ID (for customer support): 00000000-0000-0000-0000-000000000000 – Activity ID: 1e856a21-1a04-4e96-8b09-0e1add157829 – Url: https:\/\/fef.msuc02.manage.microsoft.com\/RAODJPlus\/StatelessODJService\/34893bcc-ffff-1253-0605-061200594025\/odjConnector\/acquirePendingRequests\\\”,\\r\\n \\\”CustomApiErrorPhrase\\\”: \\\”\\\”,\\r\\n \\\”RetryAfter\\\”: null,\\r\\n \\\”ErrorSourceService\\\”: \\\”\\\”,\\r\\n \\\”HttpHeaders\\\”: \\\”{
\\\\\\\”WWW-Authenticate\\\\\\\”:\\\\\\\”Mutual realm=\\\\\\\\\\\\\\\”CN=SC_Online_Issuing,
CN=Microsoft Intune EAS Connector CA,
CN=Microsoft Intune NDES Connector CA,
CN=Microsoft Intune ConfigMgr Connector CA,
CN=Microsoft Intune ODJ Connector CA,
CN=Microsoft Intune ImportPFX Connector CA\\\\\\\\\\\\\\\”\\\\\\\”
}\\\”\\r\\n}\”,
\”Target\”:null,
\”Details\”:null,
\”InnerError\”:null,
\”InstanceAnnotations\”:[]
}\”]”
},
“Name”:”RequestHandlingPipeline_DownloadFailure”,
“Value”:0
}
Hi. I have setup Intune Connector on a server. I have bypass outbound proxies as descreibed in here but still get issues. The connector won’t show up in Intune. Do you have any suggestions?
https://docs.microsoft.com/en-us/mem/intune/enrollment/autopilot-hybrid-connector-proxy
{
“Metric”:{
“Dimensions”:{
“InstanceId”:”67A4D658-5C1A-41CD-8F0C-56FA28774E8B”,
“DiagnosticCode”:”0x0FFFFFFF”,
“DiagnosticText”:”We are unable to complete your request because a server-side error occurred. Please try again. [Exception Message: \”DiagnosticException: 0x0FFFFFFF. We are unable to complete your request because a server-side error occurred. Please try again.\”] [Exception Message: \”Failed to get a value for Key: OdjServiceBaseUrl\”] [Exception Message: \”The given key was not present in the dictionary.\”]”
},
“Name”:”RequestHandlingPipeline_DownloadFailure”,
“Value”:0
}
}
What is the eventID for successful online domain join? I want to run few scripts based on successful online domain join.
Hi, I have a time out error at the devise setup step, however I could see the device joined in Intune and all the profiles are configured. I tried on 2 different machines and resulting the same error. Any suggestions pls?
More details like what is the error etc are required to help you more. Also, you can raise a question in our forum HTMDforum.com to get more detailed discussion about issues
One helpful note I ran into is that you have to assign your domain join profile to the same group you have your autopilot deployment profile deployed. I skipped that step and was getting the same error stating your organization doesn’t use this feature. Great article and so helpful! Thanks anoop!!!!
Hi sir, facing issues in deleting the autopilot hybrid azure ad joined device. Device is already deleted from Intune however unable to remove from azure ad. It still shows as autopilot device and cannot delete it . Even deleted from manage windows autopilot devices.
Please please assist, help me with a solution.
Hello, your articles are very helpful. I am facing an issue, I hope you can help or direct me in the right direction. We have 2 Deployment Profiles “AAD Joined” and “Hybrid AD Join”. We use Dynamic groups assigned to these profiles. Having Issues with Hybrid AD joined devices. If I get a brand new computer, add the Hash manually, and set the Group ID, it works fine and deploys the way we have configured it. But if we reset the Device or wipe it to assign it to another user. it keeps failing and throws an error 80070002. I see the ODJ connector logs and all three events are successful. I even see the device in OU and in Intunes Portal. I even tried deleting it from everywhere and adding it back with Manual Hash but does the same thing. Any help will be appreciated.
Hi, Anoop
First, thank you for all the incredibly useful documentation you provide about InTune AutoPilot.
I want to share what I hope is very useful information about error 80180005 that I have not found anywhere after a LOT of Google-ing – and even after opening a support case with Microsoft. We modernized from SCCM “imaging” to AutoPilot prep in late 2021/early 2022. Things went fairly well throughout 2022 as the team learned and fine-tuned the new machine prep process, then all of the sudden on Jan. 04 2023 we started getting the error 80180005 on – seemingly – every machine being fully “reset”.
At first I thought maybe the cause had something to do with Microsoft beginning to force tenants off of basic authentication and on to modern authentication, or maybe something else an Azure Global Admin changed our environment. We were almost certain it was not caused by machine naming syntax; that was one of the first things we looked at and tested and we knew that had not been changed since our original AutoPilot design.
For us the cause was our keeping our Dell laptop fleet updated via Dell | Command Update. Specifically, when firmware updates occur on various Dell components it causes AutoPilot enrollment to believe there has been a hardware change on a laptop. The way I figured it out was on one problematic laptop we had fully reset (but not on any others I examined), the AutoPilot enrollment page noted that there was problem it was trying to “fix” and to “wait”. The fix never happened automatically, so I ended up deleting that machine’s enrollment, re-running the enrollment PowerShell script to generate a new .csv with an updated hardware hash, and manually re-importing.
I understand this from a security standpoint especially being a CISSP, but this is a major consideration in the scenario of a remote machine being fully reset by the end user.
Thanks,
Cw.
Just wanted to add that our tech team ran into error 80180005 and it was resolved by removing the device s/n and computer name from azure. When it returned from the repair shop they replaced the motherboard, we believe this caused the error for us. Hope it helps someone.
This is no longer the location for the log file. It is found under Applications and Services Logs\Microsoft\Intune\ODJConnectorService
I have a really strange behavior going on when trying to do a Hybrid Domain Join. Sometimes the Server doesn’t get the request to do the Domain Join. However, the client thinks the process was successful and appears to be on the domain. No computer account was created in the on-prem AD, and no one can sign into the computer. The computer has the correct name scheme and if I enabled the local admin account before starting the Autopilot process and log in using that account, the computer thinks it joined the domain. When looking at the event viewer on the server Applications and Services Logs\
Microsoft\Intune\ODJConnectorService\Admin you won’t see any request for the domain join, but in the Operational logs, you will see it is polling. Has several logs a minute with ODJRequestHandlingPipelineDownload_NoWork: No requests pending to be downloaded. I thought the service was hanging so I restarted it and sometimes that worked and the computers completed the autopilot process successfully.
I’m having the same problem as @Jason. 1/3 of the time it works, but 2/3 of the time the devices aren’t added to AD. Server event logs show it didn’t receive the ODJ request, but the clients receive the ODJ blob and client event logs show regular pinging of the DC.
Connector is correclty updating itself and shows connected in Intune. I rebooted the server after confirming all Windows Updates were installed. I also ran a repair install on the Connector just in case.
No proxy. I tried different accounts; on-prem and over SBL VPN; different model machines and a VM.
Does anyone have suggestions? Jason, did you solve your issue?
Blog is great but ads are annoying,how to get rid of them.
Basically all the hard work goes
In dump due to ad revenue being ON
Ik get this during te hybrid autopilot installation after sign in with my Global Administrator user:
somethin went wrong
confirm you are using the correct sign-in information and that your organization uses this feature. You can try to do this again or contact your system administrator with the error code 80070002.
These are the settings for Autopilot:
Deployment mode: User-Driven
Join to Microsoft Entra ID as: Microsoft Entra hybrid joined
Skip AD connectivity check: Yes
Language (Region): English (United States)
Automatically configure keyboard: Yes
Microsoft Software License Terms: Hide
Privacy settings: Hide
Hide change account options: Hide
User account type: Standard
Allow pre-provisioned deployment: No
Apply device name template: No
I dont see any logs on the server where i installed the Intune Connector.. Is there anyone who knows the fix for this?