Let’s learn more about the Windows Autopilot Hybrid Domain Join Step-by-Step Implementation guide. This post will learn details about the Windows Autopilot Hybrid Domain Join scenario.
In most Windows Autopilot deployments, a Windows 10 or Windows 11 machine is joined to Azure AD. However, most organizations still rely on On-premise, on-prem Active Directory.
Hybrid Azure AD is domain joined plus Azure AD registered devices. So you will need to have connectivity to the on-prem active directory, and you also will need to have additional components such as Intune Connector for Active Directory.
The following are some of the basic posts related to Windows Autopilot. Hopefully, these posts will help you start the Windows Autopilot journey.
1. Beginners Guide Setup Windows Autopilot Deployment
2. Dynamically Deploy Security Policies and Apps to Windows Autopilot Devices
3. Where is the Autopilot Assign Profile Button in the Intune Portal
4. Windows Autopilot End-to-End Process Guide
5. Repurpose/Reprovision Existing Devices to Windows Autopilot
6. Windows AutoPilot Profile AAD Dynamic Device Groups.
7. Windows Autopilot License Requirements
Windows Autopilot Hybrid Domain Join
Why are we talking about Hybrid Azure AD Join? Hybrid Azure AD Join is the same as Hybrid Domain Join when your on-prem Active Directory is synced with Azure AD using AAD Connect.
There are many dependencies to have on-prem Active Directory or domain join Windows 10 Devices.
NOTE! – In this post, Hybrid Azure AD Join is referred to as Hybrid Domain Join and Domain Join.
Dependencies are mainly for Group policy and Application authentication (Legacy – mainly NTLM). Many organizations want to adopt a new deployment using Autopilot. But at the same time, they also wish Windows 10 to be part of Active Directory.
Microsoft introduced the “Hybrid Azure AD or Hybrid Domain Join” deployment to meet the above criteria. You can deploy a Hybrid Autopilot profile from Intune. With this solution, we can provision Windows 10 using Intune, and the computer will be joined to the On-premise Active directory as well.
This is a series of posts, as listed below.
- Hybrid Azure AD join Architecture and How to set Windows Autopilot from Intune Portal (This Post)
- Hybrid Azure AD join Autopilot – Troubleshooting Tips
Windows Autopilot Hybrid Domain Join Setup Architecture
Following the high-level architecture flow of Windows, Autopilot Hybrid Domain Join setup architecture.
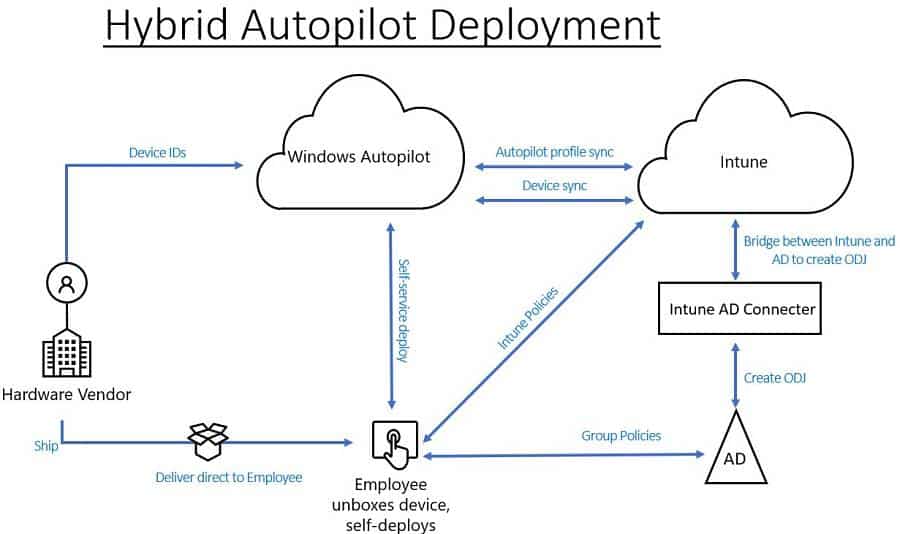
Windows Autopilot Workflow – Hybrid Azure AD Join
This section contains an easy-to-follow, 12-step workflow for the Windows Autopilot Hybrid Domain Join scenario. I hope it helps you!
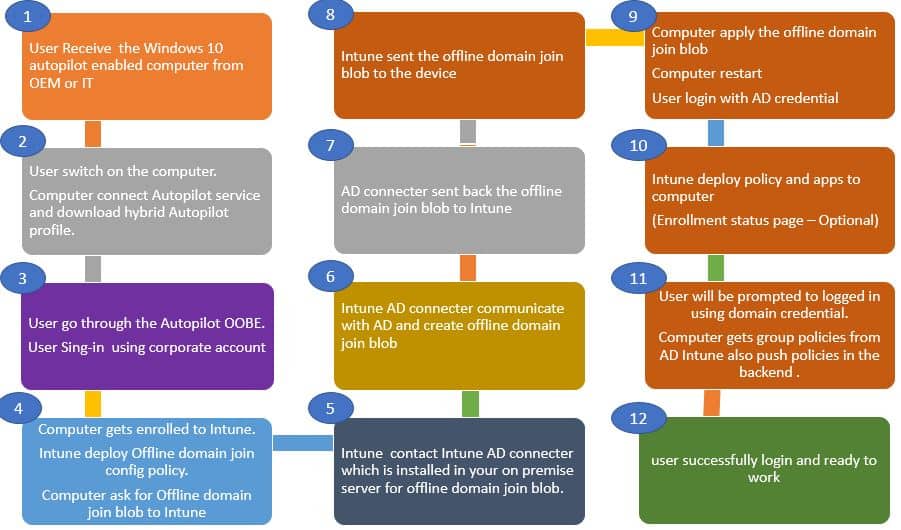
- The User Receives the Windows 10 Autopilot-enabled computer from OEM or IT.
- The user switches on the computer. The Computer connects to the Autopilot service and downloads a hybrid Autopilot profile (Windows Autopilot Hybrid Domain Join Profile).
- The user goes through the Autopilot OOBE and sign-in using the corporate account.
- The computer is enrolled in Intune. The offline domain join configuration profile is Deployed from Intune. Then, the Computer asks for an Offline domain to join the blob.
- Intune communicates with the Intune AD connector. Intune AD connector installed in your on-premise server for offline domain join blob.
- Intune AD connector communicates with AD and creates offline domain join blob.
- AD connector sent back the offline domain join blob to Intune.
- Intune sent the offline domain join blob to the device.
- The Computer applies the offline domain join blob and restarts—the user’s login with an AD credential.
- Intune deploy policies and apps to computers. (Enrollment status page – Optional).
- The user is prompted to log in using domain credentials—the Group policies deployed from Active Directory. Intune also pushes policies in the back end.
- User login and ready to work
Prerequisites for Hybrid Autopilot Setup
The Prerequisites for Windows Autopilot Hybrid Domain Join are divided into server and client-side.
Server-side Prerequisites
- Configured hybrid Azure Active Directory join.
- Windows 10 automatic MDM enrollment enabled
- Windows Server 2016 or above (To Install the Intune AD Connector)
- Internet connectivity on Intune Connector for Active Directory Server.
- If there are any Internet proxies, make sure you go through this article.
Note: It is recommended to configure the Intune AD connector to bypass the on-premises proxy.
Client-side Prerequisites
- Windows 10, version 1809 or later.
- Internet access. In the Windows Autopilot Hybrid Domain Join scenario, the proxy rule should apply to both the client and the server.
- Connectivity to Active Directory and domain controller during deployment.
NOTE! – VPN connection to On-prem AD is not supported. VPN connection to on Prem AD is Supported now.
Hybrid Autopilot Configuration Steps
Let’s check the configurations required for Windows Autopilot Hybrid Domain Join setup into two. In this post, we will go through these configurations in detail.
- On-premise configurations
- Cloud configurations (Intune)
1. On-premise configurations
There are two configurations required as part of on-premise configurations.
- Setup Intune AD Connector (Intune Connector for Active Directory)
- Delegate Permissions
Intune AD connector (Intune Connector for Active Directory)
Following are the Intune AD connector requirements. Make sure that you have all the needs in place before the implementation.
- The Intune Connector installation requires Windows Server 2016 or later.
- Intune Connector Server should be able to communicate with Active Directory.
- The Intune Connector Server must have access to the Internet. If you have a proxy in your environment, please follow the proxy recommendations.
- In production, For High availability, Consider multiple servers with connectors
- Consider a connector for each part if you have any Active Directory domains in your environment.
- Intune AD connector server system locale should be set to English US.
How to Configure Intune Connector for Active Directory
The following steps will help you complete the Intune AD connector configuration (Intune Connector for Active Directory) for Windows Autopilot Hybrid Domain Join scenarios.
- Login to Intune Console.
- Select Device enrollment > Windows enrollment > Intune Connector for Active Directory > Add connector > Click on the download Connector setup file.
ODJConnectorBootstrapper.exe will be downloaded.
- Copy the ODJConnectorBootstrapper.exe to the Server designated to host Intune Connector for Active Directory.
- Install the executable ODJConnectorBootstrapper.exe.
- Click Browse if you want to change the default installation path.
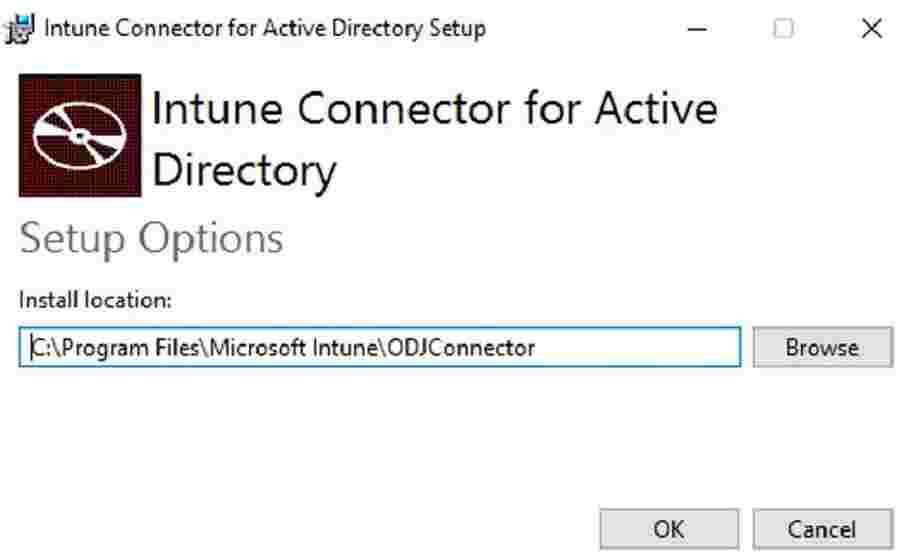
Windows Autopilot Hybrid Domain Join Step-by-Step Implementation Guide – Fig.5
Select Configure after a successful Intune AD connector installation
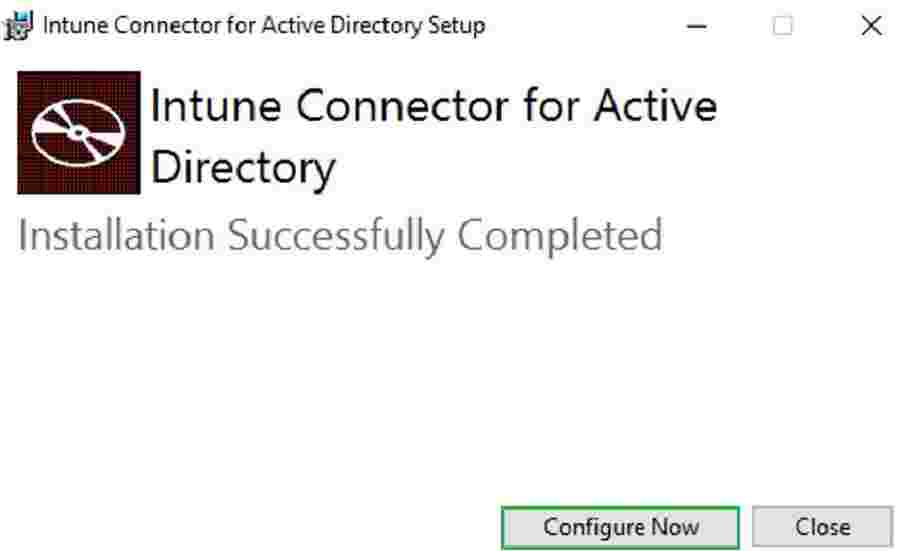
Select Sign In.
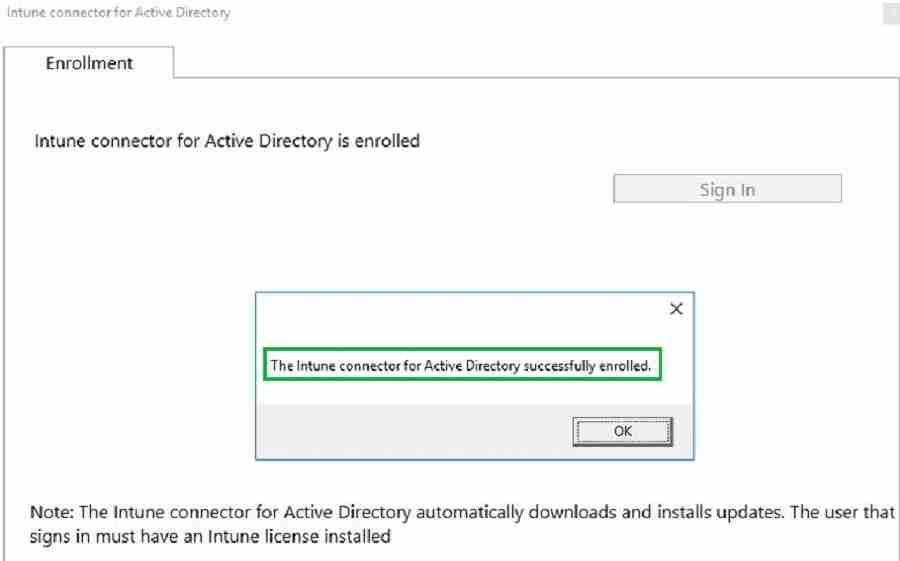
NOTE! – Sign in using Global Administrator or Intune Administrator user. Please ensure the admin has Intune license assigned.
Intune Connector for Active Directory gets enrolled. After a few minutes, Intune AD connector server starts communicating with Intune cloud service.
NOTE! – For Intune connector Installation logs, you can navigate to below path. C:\Users\userid\AppData\Local\Temp\Intune_connector_for_Active_Directory_<Year>
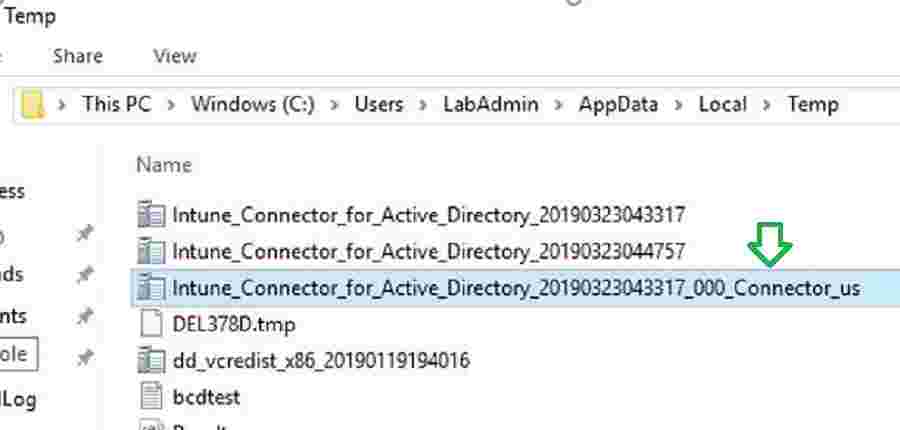
You can refer to the log below for more details on Installation.
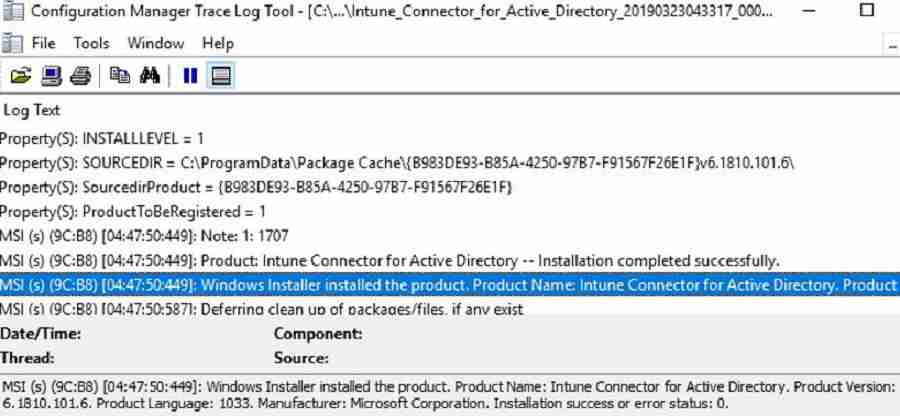
After Signing in, the Intune connector will start communicating with your Azure tenant. It takes less than 5 minutes for the connector to appear in the Intune console. Navigate to the path below to see all the connectors in your environment. You can also verify the latest Intune connector sync timestamp.
Delegate permission for Intune Connector for Active Directory
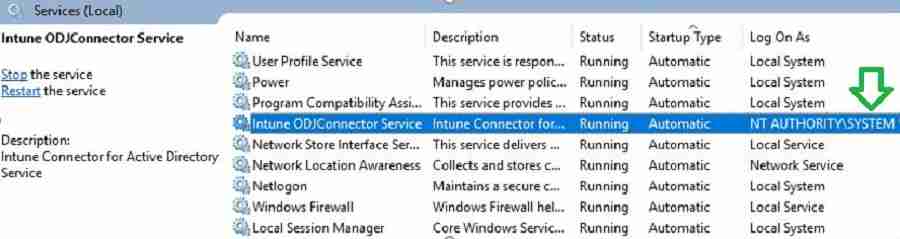
The Offline Domain Join Connector service is responsible for creating Computer Objects. Offline Domain join Connector acts as a mediator. Offline Domain join Connector service communicates with on-premise Active Directory and Intune cloud.
As shown in the picture below, the Connector service works with the local system account. Hence, the server computer object (SERVERNAME$) must have permission to create computer objects in AD.
By default, all domain accounts have permission to join a maximum of 10 computers to AD. To change this default behavior, you need to delegate permission. Let’s configure the permission.
- Launch Active Directory Users and Computers (DSA.msc).
- Right-click the organizational unit and then select Delegate Control.
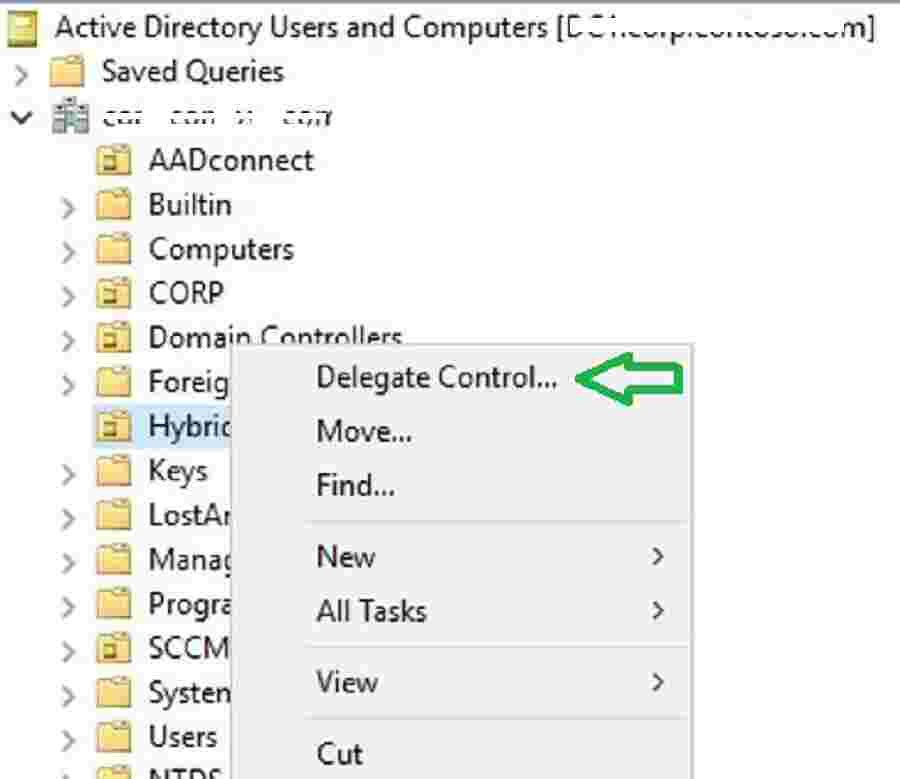
Select “Next” to continue.
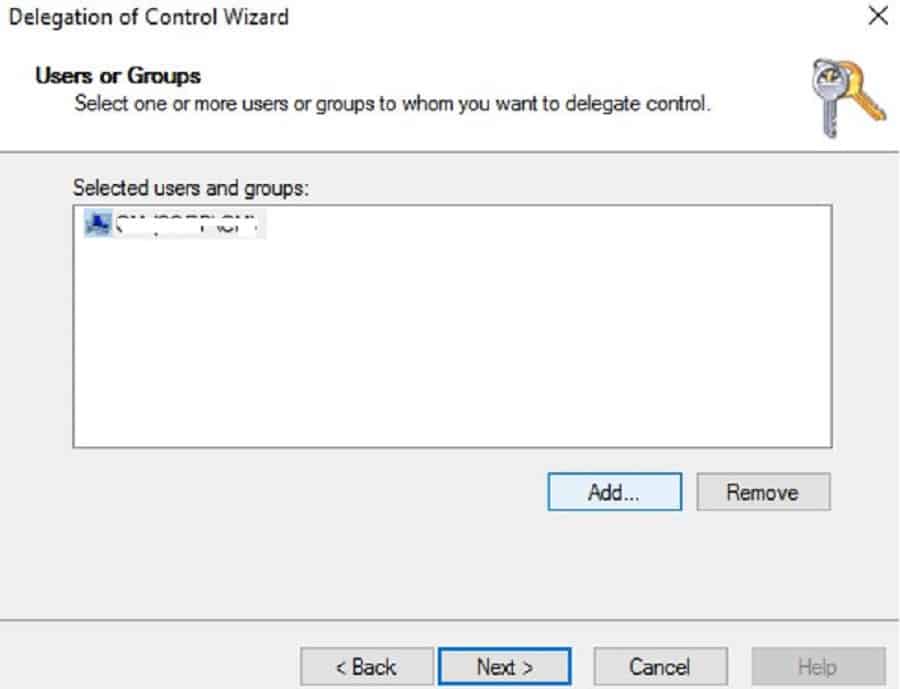
In the Delegation of Control wizard, add your Intune connector server computer object. Select Create a custom task to delegate > Next.
Select the Computer objects, Create selected objects in this folder, Delete selected objects in this folder checkboxes, and select the Next button to continue.
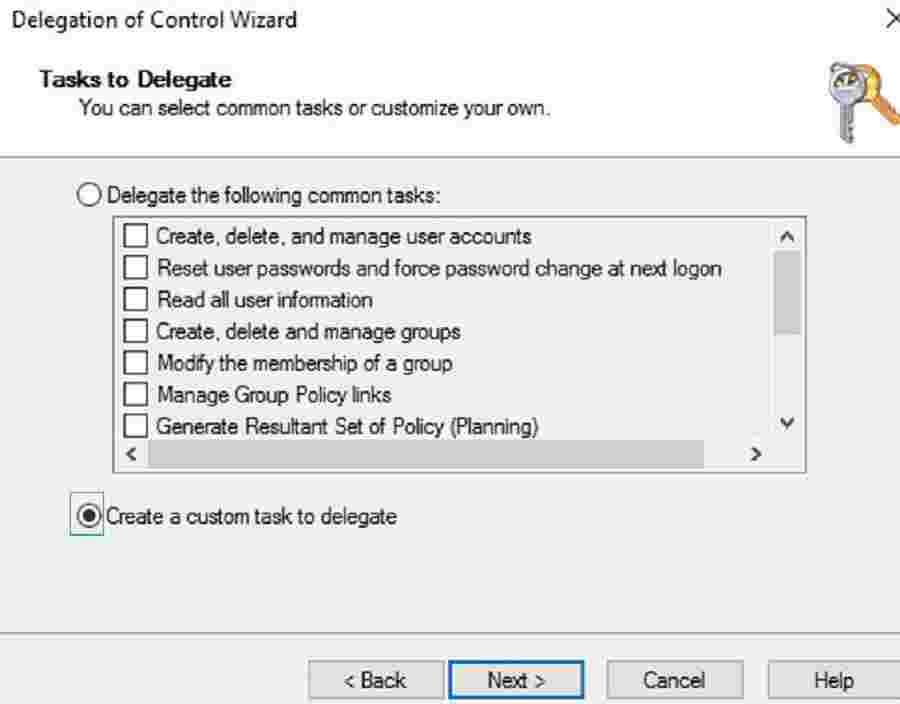
Under Permissions, select the Full Control check box, as shown below.
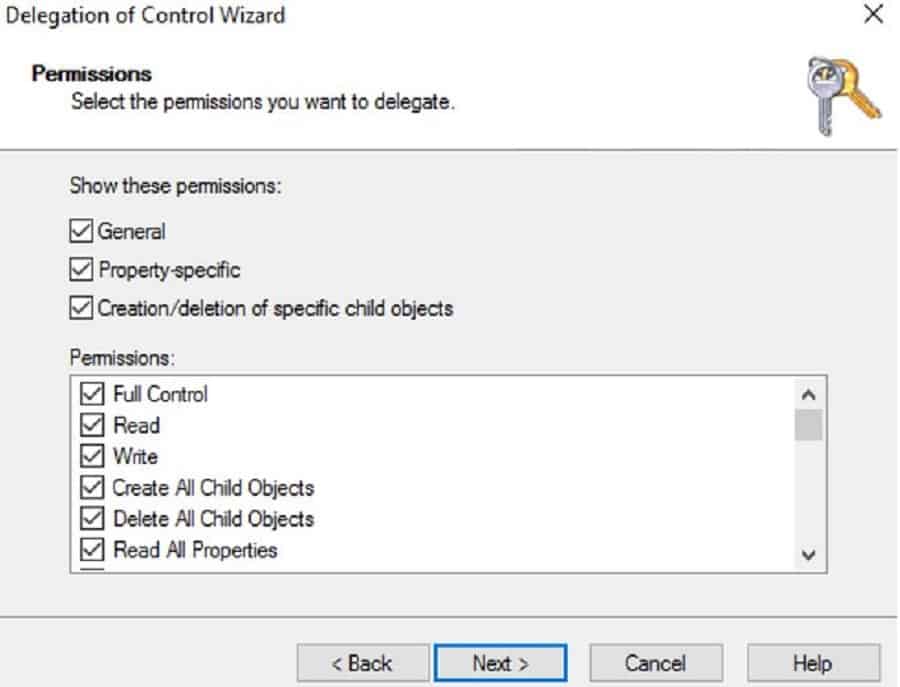
You have completed the permission delegation for the Intune AD connector to create an Offline Domain join blob for the Windows Autopilot Hybrid Domain Join Scenario.
Intune Cloud Side Configurations
This section will go through different configurations required within the Intune console for Windows Autopilot Hybrid Azure AD Join (Windows Autopilot Hybrid Domain Join) scenario.
Intune Autopilot Profile Configuration
The following configurations will help you configure the Windows Autopilot hybrid domain join scenario.
- Login to Intune, select Device enrollment > Windows enrollment > Deployment Profiles > Create Profile.
- Type a Name and, optionally, a Description.
- For Deployment mode, select User-driven.
- In the Join to Azure AD box, select Hybrid Azure AD joined
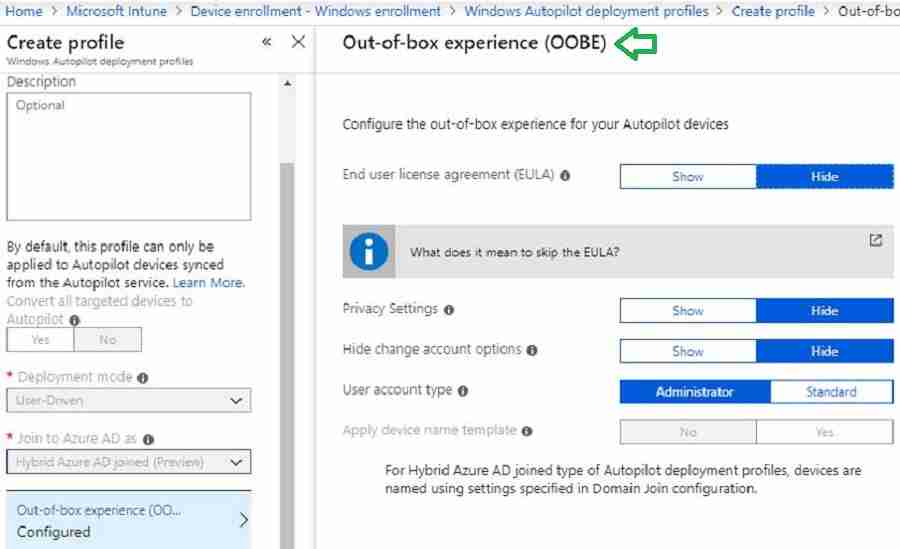
- Select Out-of-box experience (OOBE). Configure the OOBE options as needed and create a profile.
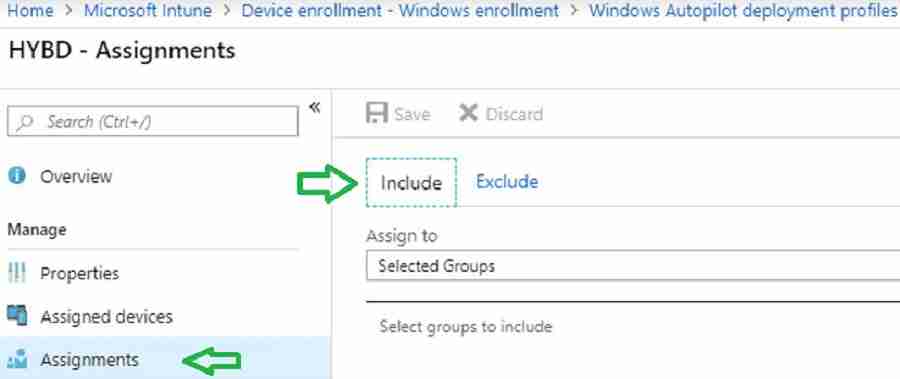
On the profile page, select Assignments. And Select groups.
In the Select Group pane, select your device group. Please make the Autopilot computer hardware ID imported and added to the device group.
Intune Configuration Profile – Hybrid Domain Join
This section will describe three(3) configurations for Windows Autopilot Hybrid Domain Join, which are defined in three(3) settings.
- Computer naming template
- Domain name
- Organization Unit path
- In Intune, select Device Configuration> Profiles > Create Profile.
- Select Windows 10 and later.
- Profile type: Select Domain Join.
- Provide a Computer name prefix, Domain name, and (optional) Organizational unit in DN format.
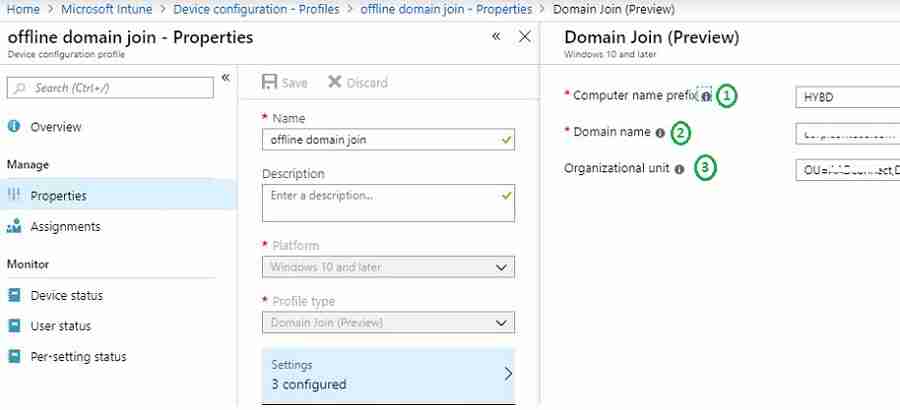
Notes from the Field:
#1 – Please ensure the Organization unit is in DN format. If there is any typo, your computer will be stuck with the message “Please wait while we set up your device.” I will cover this in my second post. The default computer container is used if you don’t update the Organization unit.
#2 – Hybrid Autopilot supports computer naming using the prefix. You cannot use variables such as %SERIAL%. If you do, you will get the error message “Something went wrong” with code “80180005” or “80070774.“ I will explain this in my second post (Windows Autopilot Hybrid Azure AD Join Troubleshooting Tips).
- Assign the profile to the Autopilot device group.
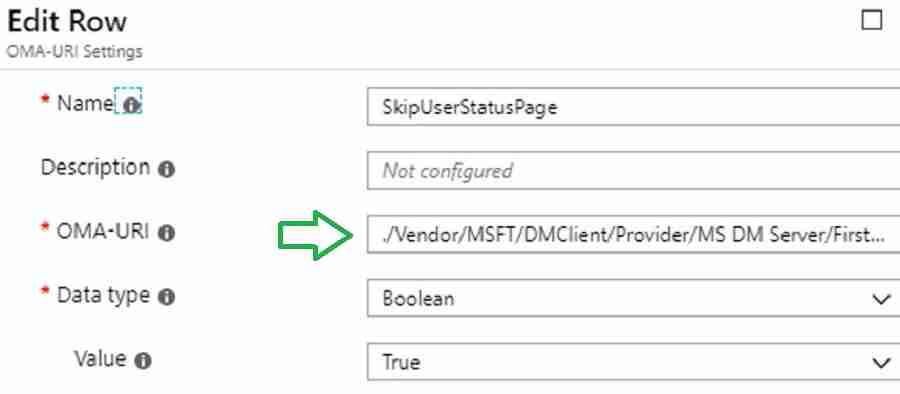
CSP to Disable User Setting in ESP
You may observe an error in the enrollment status page (ESP) in the Windows Autopilot Hybrid Domain Join profile scenario. This error is because of the timeout mentioned in Michael Niehaus’s post.
Below CSP configuration will prevent this timeout error. Let’s go through the steps to configure this CSP.
./Vendor/MSFT/DMClient/Provider/MS DM Server/FirstSyncStatus/SkipUserStatusPage
Navigate via Intune blade – Create a profile – Settings – Configure – Custom OMA-URI Settings – Windows 10 and later – Add OMA-URI settings.
Assign the CSP to the Autopilot device group.
(Optional) Turn on the Enrollment Status Page
It is recommended to enable the Enrollment status page. For more details, refer here.
Results – Windows Autopilot Hybrid Domain Join
You will get the login screen below after completing Windows 10 deployment using Hybrid Autopilot. As seen below, you can log in to the computer using an AD Domain user account.
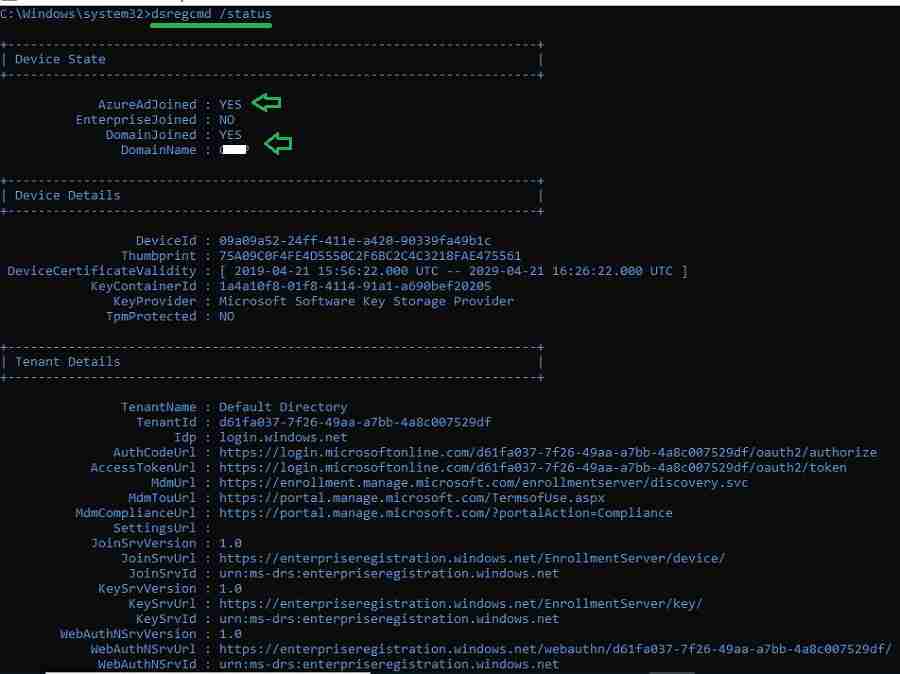
After logging in, you can verify whether your machine is a Hybrid domain join by executing the below command.
dsregcmd /status
In my second post, we will go through events and logs that help troubleshoot.
Resources
- Windows Autopilot Video Starter Kit
- Beginners Guide Setup Windows AutoPilot Deployment
- Dynamically Deploy Security Policies and Apps to Windows AutoPilot Devices
- Where is the AutoPilot Assign Profile Button in the Intune Portal
- Windows AutoPilot End-to-End Process Guide
- Windows Autopilot Deployment Scenarios – On-Prem Hybrid Domain Join
We are on WhatsApp. To get the latest step-by-step guides and news updates, Join our Channel. Click here –HTMD WhatsApp.
Author
Vimal Das has more than ten years of experience in SCCM device management solutions. His main focus is on Device Management technologies like Microsoft Intune, ConfigMgr (SCCM), OS Deployment, and Patch Management. He writes about technologies like SCCM, Windows 10, Microsoft Intune, and MDT.

Great work..
Thank you Salakshi from Vimal’s side 😉
I keep having errors the whole day, “Please wait while we set up your device” but I have configed everything correctly and it has been working for months until today
Some of the troubleshooting steps is covered in this post … https://www.anoopcnair.com/windows-autopilot-hybrid-azure-ad-join-trouble/
I get “Error 1 – 80070774 –Something Went Wrong” but unfortunately there is no way to repair it at the moment. It worked up until this week, and everything from deleting all instances and re-enrolling in intune has not worked
0x80070774 = domain controller not found
Are you able to ping your Domain controller from the client ?
Hi Erik – Are you still facing the issue ?
What solved this for me was:
It seems that Microsoft now has released ESP out of preview. I had to revert
./Vendor/MSFT/DMClient/Provider/MS DM Server/FirstSyncStatus/SkipUserStatusPage
As in remove this policy completely to get the system working again.
I am confused, when i am first set this up for a customer. I have to be onprem with the domain controller? maybe I assumed I could go thourgh the steps and do an offline domain join, reseal the device send it to the customer domain joined with all of their apps needed to run.
Hybrid Autopilot profile require domain controller reachable during setup
Hi Vimal. Thanks for the article, finally got some better documentation for this. Dtill, I have two problems:
1. As per Derek’s question, I am also confused. My understanding was that Intune is a way to manage devices that are not inside the local network. And a hybrid deployment will mix the local AD control ( policy, software deployment) with Azure control. I have people both in the main office, with computers joined to AD and people in remote offices that do not have a DC and their computers are not joined to the domain. I was hoping I can add this remote group to Azure and have them managed from there, while still having the local users joined both to the local Domain and Azure ( I am also using AAD connect). From the previous answer it looks like I cannot do that, because the user has to be in my office. Is this true?
2. I tried to install the connector on a 2016 server that I have just installed and promoted as a DC. AAD connect is running on a different, 2008R2 server. In the end, when I tried to sign up using my account ( I am global admin in Azure and have a Microsoft E3 license assign, which includes Intune) it asked for the username and password, but it did not finish the installation. It is still asking me to pick a user, if I select is it gets back there. Any advice on how to deal with this? The connector service shows as working, but it is not showing in the Intune admin page.
Thanks
1, As part of Hybrid autopilot provisioning user login is required. And User authentication will happen against on premise domain controller. Hence Hybrid autopilot require Device to be on corporate network.
There’s a section regarding delegate control:
1. Launch Active Directory Users and Computers (DSA.msc).
2. Right-click the organizational unit and then select Delegate Control.
—
Step 2 says right-click the OU. What OU? Is this the OU that administrators put machines into if they want the machines to be hybrid joined and managed by autopilot/intune mdm?
Yes , The OU where you want machine to be placed
hi.
thanks for you post – very helpful.
just a quick one.
the delegated OU (hold the on perm computer object created by the connector) need to be synced as well ?
the sync refer to the ad connect of course – as device sync is a requirements for “hybrid join” scenario.
or maybe we move the device to “already synced” OU after the object created on the Local AD (delegate OU).
thanks in advance!
AADconnect Synch needs to be configured for the OU
The “NOTE! – VPN connection to On-prem AD is not supported.” isn’t true. I am able to perform remote Autopilot enrollment with Hybrid AD Join by pushing Always On VPN and SCEP Certificate policies.
I agree. Now, it might not be true. But, while writing this post it was true 🙂 Check out the latest updates of Autopilot https://www.anoopcnair.com/windows-autopilot-updates-timelines/
No worries. I don’t think it’s officially supported by Microsoft yet. I just found a workaround.
I am using also such an workaround to use a Cisco management tunnel with limited connection to DC and ODJ server, but the issue which i am facing is, you cant force the SCEP push during the ESP, so it is more random will the device get it in time or not. do you found an solution for this?
Preparing your device for mobile management failed (Failed:0x800705b40
Hey Anoop,
Is VPN infra necessary for the device to pick up GPO? Always on VPN required?
Regards,
Shashank
Connectivity to on prem DC is required isn’t it ?
Good information.
Can you please suggest how auto pilot will work if i have ping federation.
I have not tested this scenario. PING and OCTA work differently. Are you using a separate client from Ping to facilitate the compliance of the device?
Great article. Question is Device write back needed. Not ADConnect sync, I have thins configured already. I mean Device wrote back.
Thanks again.
How the Device write back works without AAD connect?
Can you tell me if the Autopilot Hybrid join over VPN process is supported with Azure ADDS. Azure AD connector is not required with Azure ADDS. I am testing at the minute and it is not working, it is not getting an ODJ blob and the ODJ server event logs show no events related to the process. I don’t know if there is an issue with ADDS being not supported or if I have set it up wrong. My settings look good.
I am not sure which exactly connector you mean, do you mean the AD connect to sync the device from AD to AAD, I think those connectors are required. Also the intune connector is very important.
If you set up everything and are sure that it is exactly like described in all those guides, then you could check some ODJ server proxy setting guides.
https://oofhours.com/2019/07/27/configuring-the-intune-connector-for-ad-to-use-a-proxy-server/
What i am doing currently to troubleshoot issues, is to use the autopilot diagnostics powershell script from Niehaus and also the network tool fiddler to check which network traffic is going on and which traffic will be blocked.
Hello,
thank you very much for this great article, as I am currently looking at the theory of the scenario to Hybrid Join via VPN. One thing confuses me if I look at the 12 Steps workflow in the beginning.
In Step 9 you describe that the Offline Domain Join Blob is applied, the computer is restarted and the user has to logon with AD credentials.
In Step 10 you describe that Intune Apps and policies are applied.
Since we think of an OEM device, how am I supposed to get VPN up and running if the user is supposed to logon with AD credentials in Step 9 before Intune installs apps in Step 10? I’d need Intune to install apps beforehand so VPN would be present before the user is able to logon. Is this a misunderstanding of the diagram or an error in the diagram? Or is the VPN client subject to be included in the image!?
Hi.
What is the impact to existing computer Windows Autopilot assigned group, if I want to change the organizational unit to new OU?
I realize this article is old but I just came across it. I have everything setup and working fine but have a few questions.
First, if I run “dsregcmd /status” when I first log in, it says AzureADJoined: NO, it will eventually change to YES. The errorcode is 0x801c03f3 and the server message is “THe device object by the given id is not found” Is this normal behavior?
Second, when I first log in, I get the message about “Work or school account problem” Has anyone run into this? Am I doing something wrong?
Third, I get two devices in Azure with the same name. Both have the Autopilot icon. One is Hybrid Azure AD joined and the other is Azure AD registered. How do I get rid of the Azure AD registered one since it is an Autopilot device? Better yet, how do I get it to not appear?
I think the initial delay is because of AAD Connect Sync. Normally it takes 20-25 minutes I guess after the domain join. You can check whether the device record is available in the AAD portal at the time of the first login or not. So the other errors are probably due to AAD Device registration issue?
I waited about an hour to sign in (after the “Setting up your device for work” screen) and deregcmd still showed as not joined. The duplicate computer names never go away either.
Thank you very much for this details instructions, it work well for me. I also have some questions for you:
We have different office locations and each location have their own user and devices OU in AD, also we have different naming convention for different location. How do I :
1. Joining the device to respective OU based on user account?
2. We define the device name based on our naming convention?
My idea is once the user enter it’s credential, based on user’s location (maybe in one of the user attributes), create device name in respective to the location’s naming convention and in the respective location OU.
Appreciate your 2cents 🙂
I have not tested this but Kannan has a blog post on this point I guess https://www.anoopcnair.com/computer-name-during-windows-autopilot-intune/. Worth a read?
Hi Anoop,
You mentioned in one of the requirement for Intune AD connector “Intune AD connector server system locale should be set to English US.”. Is it mandatory this to set English US even then connector server system local to English Australia?
Thank you,
Sheetal
You mention in one line “In the Select group pane, select your device group. Please make Autopilot computer hardware ID imported and added to the device group.” but I have no idea what this relates to. Do you have a separate article that goes through this specifically ?
Are you looking for this type of AAD dynamic group? https://www.anoopcnair.com/windows-autopilot-profile-aad-dynamic-device-groups/
hi, what would be the good way, when hybrid autopilot is completed and when we establish vpn to the company to login in to our AD first time, that computer would sync sccm latest policy?
I can`t login to my On-prem domain.
We can`t sign you in with this credential because your domain isn`t available!
Please Help
what is the best way and cost effective way to Manage Hybrid and AAD joined device – my Organization does not want to use Azure Arc or Admin center.
Do you have any ideas how to do this in a perspective of using Azure or Microsoft web services? or any third party
please Sir guide me on this
In AD DC there is a requirement – to add only devices that have a certificate. I need to install a certificate on the device at the time of deployment of the hybrid autopilot. how to implement it?
Dear Anoop,
We have multi provider concept (device providers) in our organization. So could you please help me to clarify following:
1. Every provider has its own OU in On-premises AD and due to segregation of duty providers should be able to manage (create/delete/modify) device object under thier respective OU only. Now in this case, can we have one connector installed and create delegation on multiple OUs (under different provider’s parent OU) and ask provider to create a configuration profile and make sure to direct thier device to thier respective OU in on-premises AD where delgation is granted. (https://learn.microsoft.com/en-us/mem/autopilot/windows-autopilot-hybrid#create-and-assign-a-domain-join-profile)
2. Its mentioned that during this connector installation we need to use an account either with GA or Intune Administrator Role with intune license. Now, as an an intune admin i do have an account with intune administrator role with license but it’s PIM enabled which has time limit of 2 hours. So, will that be sufficient or we need an account with permanet Intune administrator role assigned with Intune License ?
Sir,
When we upload CSV in autopilot portal in endpoint.
Then what is the join type of it at azure portal.
We are in the process of setting up Autopilot for our Organization. The enrollment profile and domain join profiles are created. After the enrollment the machine is attached to the workgroup but not to our domain.
The Domain join policy shows that is not applicable.
Any suggestions
I am using the Hybrid Domain join. all seems fine until i go to login. Here is what happens and i don’t remember when the option to “reseal” was turned on.
in my initial testing Everything worked great. the PC was on prem domain joined and AAD joined. I think it started when i started using the Windows Key 5 times to begin the enrollment.
The device provisions, sets the name to Autopilot-#####
all of the applications are installed.
updates done and then i am presented to reseal the device.
I reseal the device and it shuts down.
turning on the device i am presented with the AAD login. when i login with my AAD credentials the machine is immediately rebooted to the normal windows login screen and i can not log in with my domain credentials as there is no domain object.. the computer is now renamed to DESKTOP-####### and is not joined to the domain.
if i don’t do the pre-provision everything seems to proceed normally.
It was my understanding that if you had App install context set to “Device” or on some of them it is Install Behavior “System” the applications would install at first boot up out of the box with no intervention? I am either misunderstanding the process or I have configured something incorrectly.
I was hoping to take a pc out of the box turn it on and then be able to just give the PC to the end user to turn on and go. I had read were the pc prompts the user for the computer name and that causes the issue but that is not happening here.
I don’t want to log in to the device to begin the provisioning process as it should be setup for the user not ME. something in the reseal process and then first booting up after the reseal is causing the PC to be renamed breaking the domain join.
I was able to get this working and the machine was added to the on prem AD but it is not showing up as Hybrid joined in Entra. It shows as Entra joined.
I keep getting this on the workstation:
Failed to enroll MMP-C for dual enrollment mode. Result (The system cannot find the file specified.)
When I ran a manual sync on the laptop it prompted me for credentials and asked if I wanted to allow my org to manage the computer.
Hi Anoop
if during Autopilot device gets Entra joined, can we not use the Entra connect with device writeback to sync device to local AD ?
We like to use Autopilot and some Intune cloud features, but need the device later in local AD for group policies and SCCM etc.
I can’t see Intune Configuration Profile – Hybrid Domain Join
Why this happen? Anyone have a solution?
I’m Intune and Global Administrator