Let’s learn how to Prevent Users from importing Microsoft Edge Browsing History in Windows Machines using Intune Configuration profiles. This article will help you implement a policy restricting users from importing their Edge browsing history and deploying the configuration profiles to the Security group.
Certainly, you should implement security measures to enhance browsing safety in Microsoft Edge, such as blocking specific URLs, disabling password saving, and blocking automatic downloads. As Intune administrators and security professionals, it’s important to take care of your corporate device security measures as part of your responsibilities.
Many corporate companies would recommend blocking their users from Importing their browsing history and securing their corporate data on the Internet. Restricting history imports minimises the risk of unauthorized access and potential breaches.
To prevent users from importing Microsoft Edge browsing history, there are several methods you can use. You can prevent users from altering the settings by using the Group Policy Editor or Registry Editor to block importing Microsoft Edge browsing history. However, to use either method, you must have administrative access to the computer to make changes. This article will guide you on how to prevent users from importing Microsoft Edge browsing history using Intune Configuration profiles.
Reason for Blocking Users From Importing Browsing History
Blocking users from importing browsing history into Microsoft Edge is essential for maintaining data security in a corporate environment. Here are some key reasons behind blocking users from importing browsing history into Microsoft Edge.

- Data Privacy: Microsoft Edge for Business provides a customized browsing environment specifically tailored for professional use. By restricting users from importing personal browsing history, the browser safeguards individual privacy while ensuring the security of work-related data.
- Zero Trust Security: Microsoft Edge for Business is designed using the Zero Trust methodology. The browser minimizes the risk of unauthorized access and potential breaches by restricting history imports.
- Streamlined IT Operations: Managing Edge policies via Microsoft Intune contributes to streamlining operations, ultimately saving time and resources. By enforcing these policies, unauthorized data imports are curtailed, consequently guaranteeing secure access to enterprise applications.
As mentioned earlier, you can prevent users from modifying the settings by using the Group Policy Editor or Registry Editor to block the import of Microsoft Edge browsing history.
- How to Configure Microsoft Edge Favorites using Intune Configuration Profile Step-by-Step Guide
- Microsoft Edge Tabs Detailed Review
- Download Microsoft Edge ADMX Group Policy Templates
- Enable Edge Mini Menu Feature on Text Selection
Prevent Users from Importing Microsoft Edge Browsing History
Let’s learn how to Prevent Users from Importing Microsoft Edge Browsing History in Windows Machines using Intune Configuration profiles. Follow these steps meticulously.
- Sign in to the Microsoft Intune Admin Portal.
- Select Devices > Windows > Configuration Profiles > Create > New Policy.
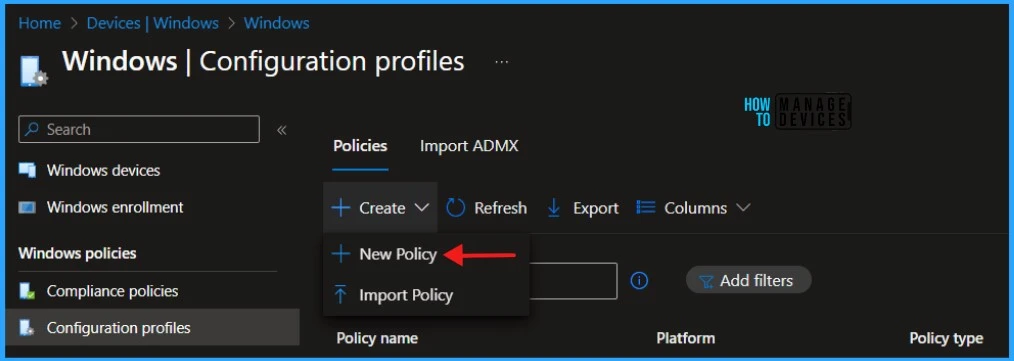
When you click Create and New Policy, a new window will open. In Platform, select Windows 10 and later, Select Profile Type as Templates and Device restrictions. Click on Create.
| Platform | Profile Type |
|---|---|
| Windows 10 and later | Templates |
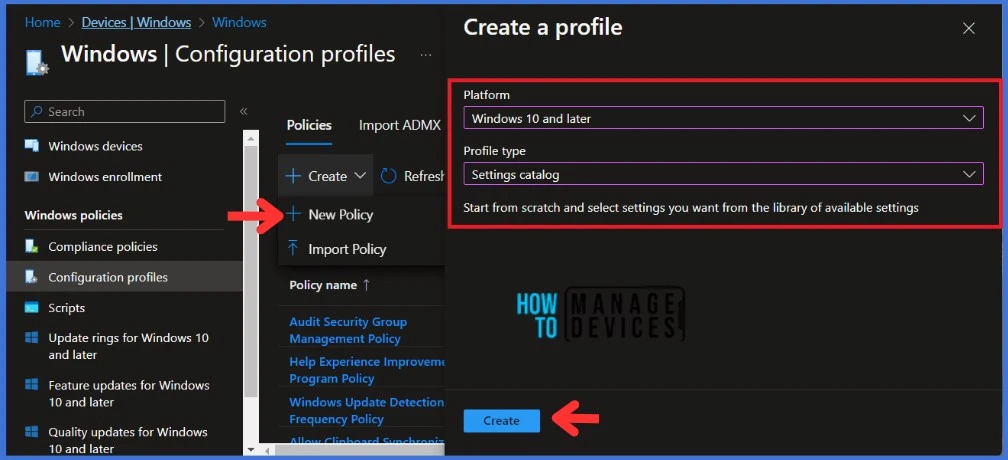
Navigate to the Basics tab and input the Name and Description for the profile.
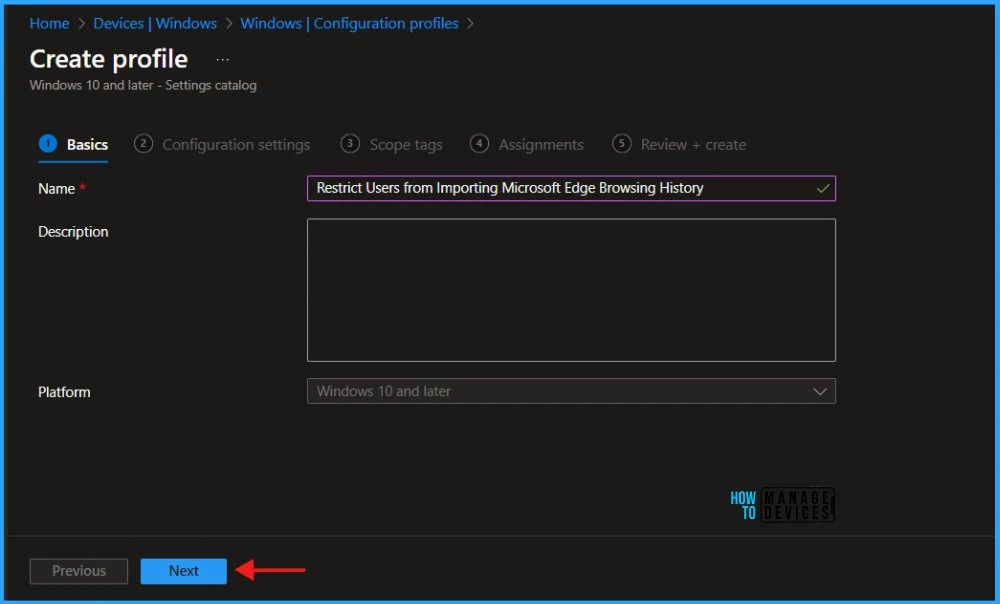
In the Configuration Settings section, under Settings Catalog, click Add Settings.
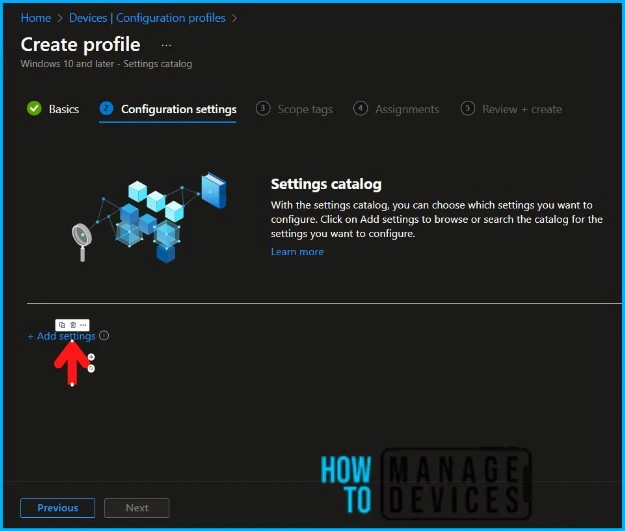
In the next tab, type “Allow importing of browsing history” in the search box and click Search. Select Microsoft Edge and Allow the importing of browsing history from the search results. You’ll see two settings here.
| Settings | Description |
|---|---|
| Allow importing of browsing history | This applies to the device |
| Allow importing of browsing history (User) | This applies to the users |
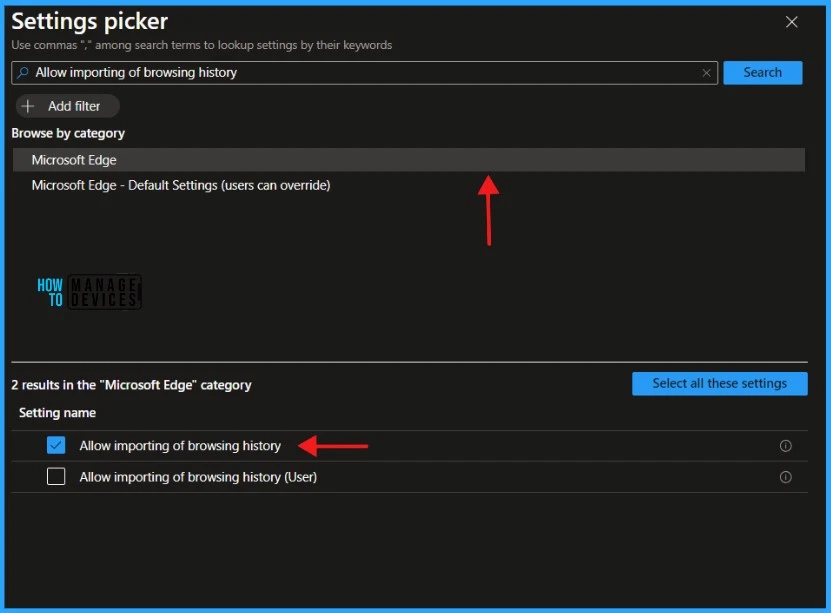
By default, Allow importing of browsing history is disabled. You must Disable it to Restrict Users from Importing Microsoft Edge Browsing History. Click Next to continue.
NOTE ! Allows users to import their browsing history from another browser into Microsoft Edge. If you enable this policy, the **Browsing history** check box is automatically selected in the **Import browser data** dialog box. If you disable this policy, browsing history data isn't imported at first run, and users can’t import this data manually. If you don’t configure this policy, browsing history data is imported at first run, and users can choose whether to import it manually during later browsing sessions. You can also set this policy as a recommendation. This means that Microsoft Edge imports browsing history on first run, but users can select or clear the **history** option during manual import. **Note**: This policy currently manages importing from Internet Explorer (on Windows 7, 8, and 10), Google Chrome (on Windows 7, 8, and 10 and on macOS), Mozilla Firefox (on Windows 7, 8, and 10 and on macOS), and Apple Safari (macOS) browsers.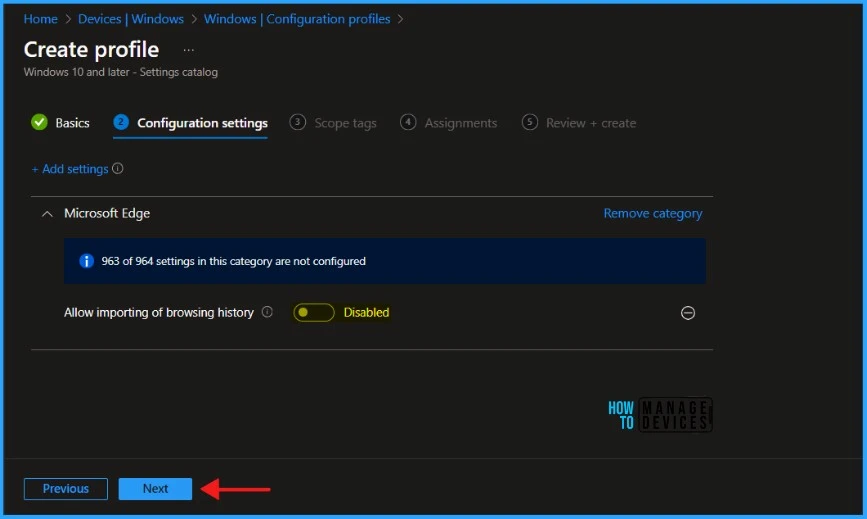
Click Next to display the Scope tags page. Add the Scope tags if you wish and click Next to assign the policy to computers. I will deploy it to the HTMD – Test Computers Group.
Read more : Intune Scope Tags Implementation Guide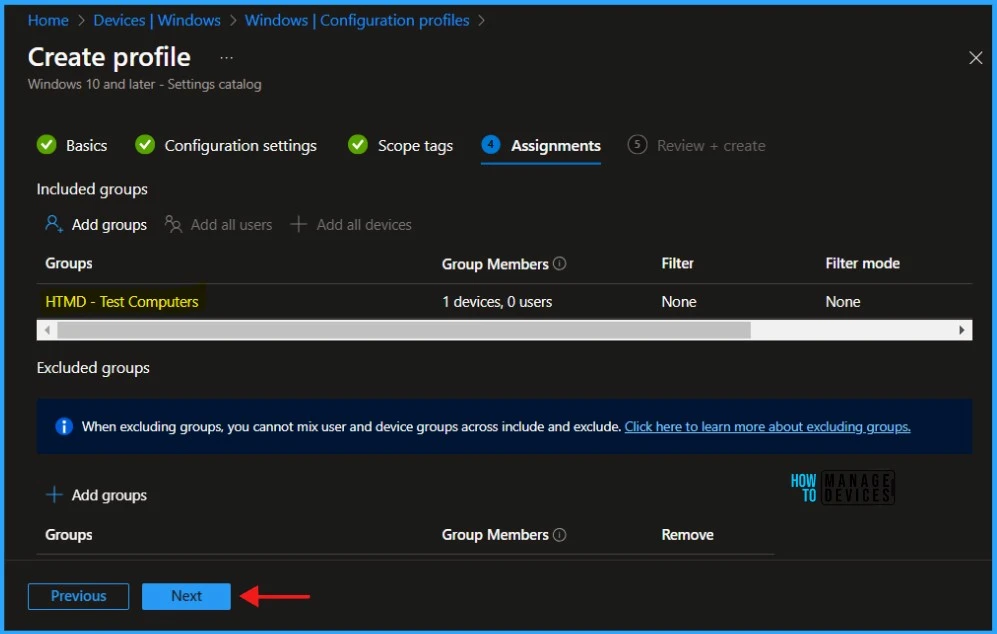
On the Review + Create page, carefully review all the settings you’ve defined to Restrict Users from Importing Microsoft Edge Browsing History. Once you’ve confirmed that everything is correct, select Create to implement the changes.
Monitor Configuration Profile Deployment in Microsoft Intune
The Configuration Profile is deployed to Microsoft Entra groups. Let’s see how we can monitor the deployment and status of installation from the Intune portal. To monitor the Intune policy assignment, follow these steps:
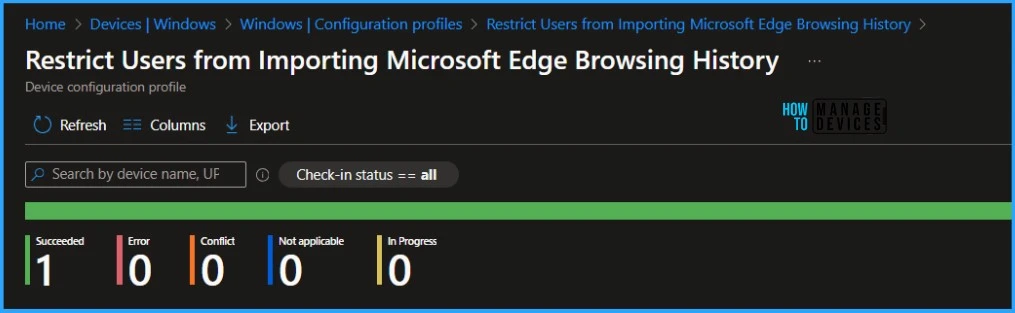
- Navigate to the list of Configuration Profiles and select the policy you targeted.
- Check the device and user check-in status from here.
- If you click “View Report,” you can see additional details.
- Monitor Intune App Protection Policy Status
- Monitor Device Enrollment Profile Deployment Report in Intune
Event Log to Verify Intune Policy Deployment Status
To verify the successful implementation of String or integer policies on Windows 10 or 11 devices through Intune, you can leverage event IDs 813 and 814. These event IDs provide valuable insights into the application status of the policy as well as the specific value assigned to the policy on those devices.
In the case of this particular policy, the value is String and is linked to the event ID 813. Analyzing these event IDs lets you understand the policy’s application status and corresponding value on the devices in question.
- How to Disable Microsoft Edge Workspaces using Intune
- How to Enable Disable Automatic Screenshots for Web Pages on Microsoft Edge
- Featured Themes in Microsoft Edge Browser
To confirm this, you can check the Event log path – Applications and Services Logs – Microsoft – Windows – Devicemanagement-Enterprise-Diagnostics-Provider – Admin.
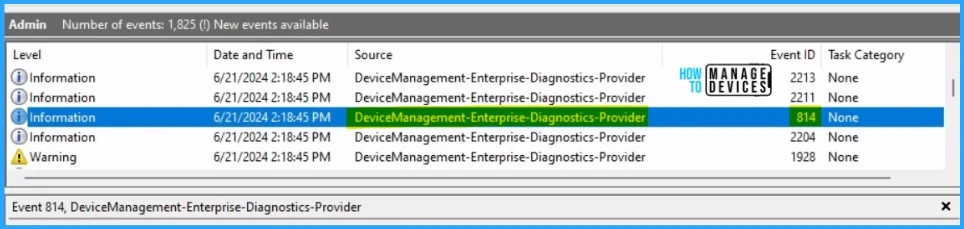
MDM PolicyManager: Set policy string, Policy: (ImportHistory), Area: (microsoft_edge~Policy~microsoft_edge), EnrollmentID requesting merge: (B1E9301C-8666-412A-BA2F-3BF8A55BFA62), Current User: (Device), String: (<disabled/>), Enrollment Type: (0x6), Scope: (0x0).End-user Experience
The Configuration Profile that we created was deployed to Microsoft Entra groups. I sync the machine manually to apply the policies immediately. Replicating the changes on the end-user device may take a while.
- Open the Microsoft Edge browser.
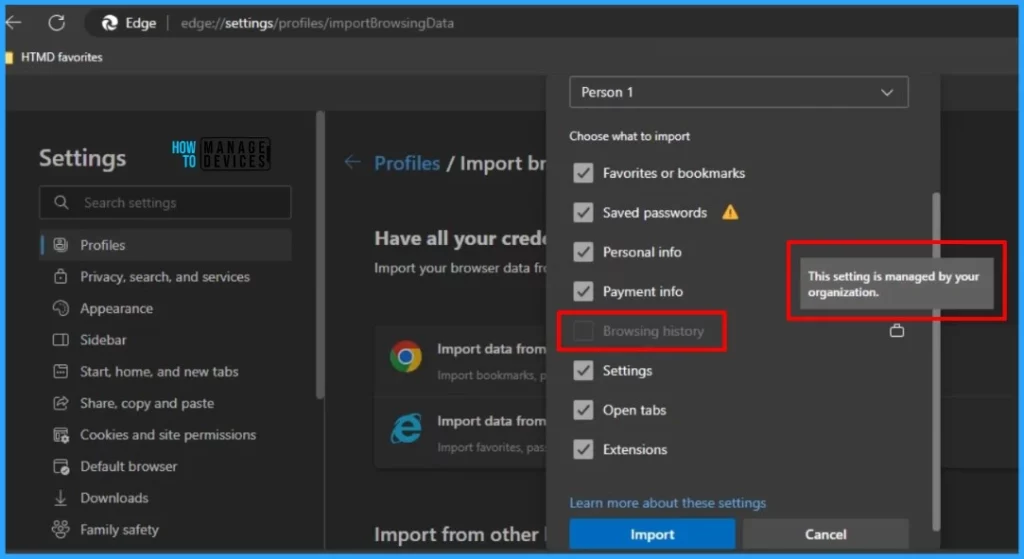
- Paste edge://settings/profiles/importBrowsingData in the searching tab
- You will be redirected to the browser’s Import browser data settings
- Click on Import
The screenshot below shows that the option to import browsing history is greyed out and cannot be changed. Except for browsing history, you can import various items such as Favorites or bookmarks, Saved Passwords, Settings, etc.
I believe that this article will be a valuable resource for you and your organization. Thank you for being so patient in reading this post. I look forward to seeing you in the next post. Keep supporting the HTMD Community.
We are on WhatsApp now. To get the latest step-by-step guides, news, and updates, Join our Channel. Click here. HTMD WhatsApp.
Author
About the Author – Sujin Nelladath has over 10 years of experience in SCCM device management and Automation solutions. He writes and shares his experiences with Microsoft device management technologies, Azure, and PowerShell automation.
