Hey everyone! In today’s post, let’s learn about all the various device restriction settings offered by Intune for Mac devices. Before we start this article, check out our previous article on Device Configuration settings to restrict built-in-apps usage, If you haven’t read it yet, we suggest you take a look before we proceed.
Our previous article focused solely on settings pertaining to a single device restriction category (built-in-apps usage). However, this post aims to provide a comprehensive overview of all the device restriction settings available in Intune for macOS devices. Our objective is to evaluate and explain each restriction and its effect on both the device and its end users.
As you may be aware, ensuring the security of any device enrolled in the organization is important. To maintain this security, it is recommended that end-users refrain from sharing any company data outside of the organization.
Additionally, IT admins should consider blocking all gaming-related apps to maximise productivity. It’s also important to be cautious and block usage of cloud storage and avoid uploading any organization files to such platform other than the standard cloud storage defined by the Organisation ( e.g., OneDrive). Intune’s device restriction settings enable IT admins to control which apps and policies are permitted or blocked, creating a secure and efficient device for end-users.
Lastly, Check out our previous blog post discussed How to Create Custom Attributes for macOS using Intune, where we explained the process of what custom attributes are. What is the purpose or requirement of using it in Production? How to implement it in end-user devices using Intune, Also, we reviewed the attributes after it deployed and monitored them in Intune Portal.

- Should you upgrade to Mac OS Ventura v13 managed using Intune
- New System Settings in macOS Ventura v13 and Intune Software Update Configs
What is a Configuration Profile
Let’s understand what configuration means exactly. Configuration management is maintaining computer systems and software in a desired state to ensure that it performs as expected to changes made over time.
With a configuration profile, we can manage settings from an MDM portal and deploy them to all organization-managed devices globally. This saves time and effort for IT admins by allowing them to update or modify multiple devices at once.
Intune has many templates to create configuration profiles. However, we will discuss the particular configuration profile type (Device restriction) in detail. Some configuration profile templates are :
- Device features
- Endpoint protection
- Extensions
- Preference file
- SCEP certificate
- Software updates
- Trusted certificate
- VPN etc.
How to Configure Device Restriction Settings for Intune-enrolled macOS Devices
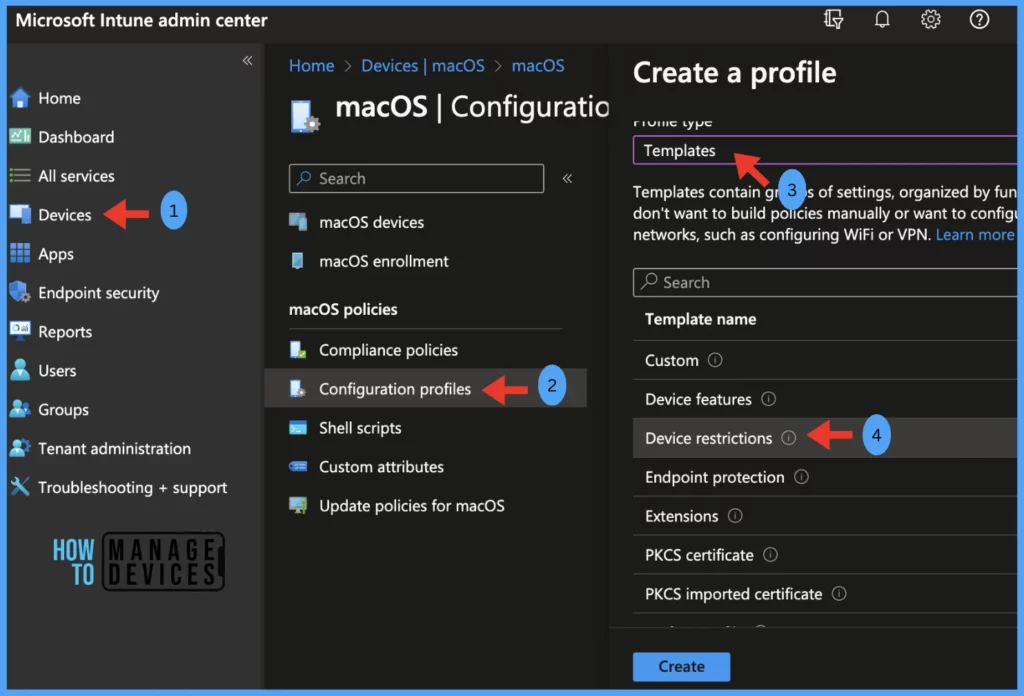
To create a configuration profile, we must ensure the required access to the Intune Portal. Let us check out the steps to be followed while creating a configuration profile in Intune portal for macOS devices.
- Sign in to the Microsoft Intune admin centre https://intune.microsoft.com/.
- On the left sidebar, select Devices > select macOS > Configuration profiles (under macOS policies)
- The list of existing configuration profiles will be reflected on the right side. To create a new profile, click on Create Profile.
- Select the correct categories for Profile creation,
- Platform – macOS
- Profile type – Templates and select Device Restriction from the available templates
- Click on Create.
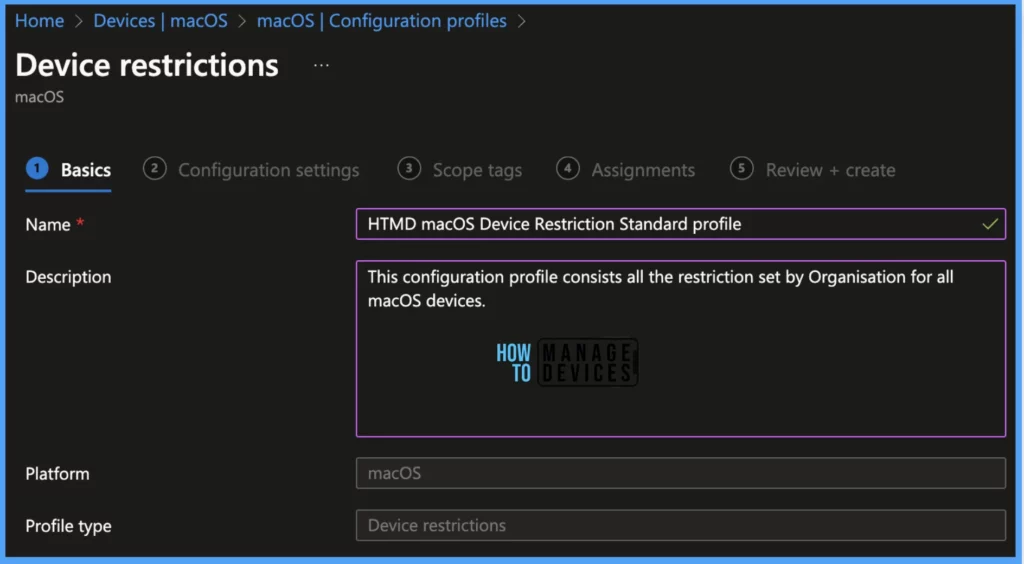
Under Basics, Provide the Name of the profile and a detailed Description and click Next.
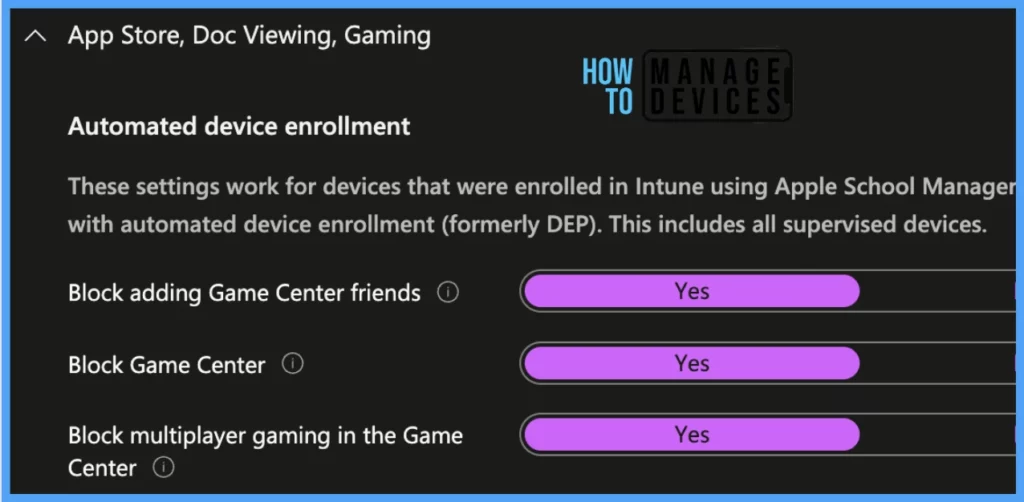
Let’s review the available restriction settings under Configuration settings. What are the criteria for their use? We can select and customize them as per our requirements for the enrolled Mac devices. Let’s go through the nine categories on this page. :
- App Store, Doc Viewing, Gaming
- Built-in apps
- Cloud and Storage
- Connected devices
- Domains
- General
- Password
- Privacy Preferences
- Restricted Apps
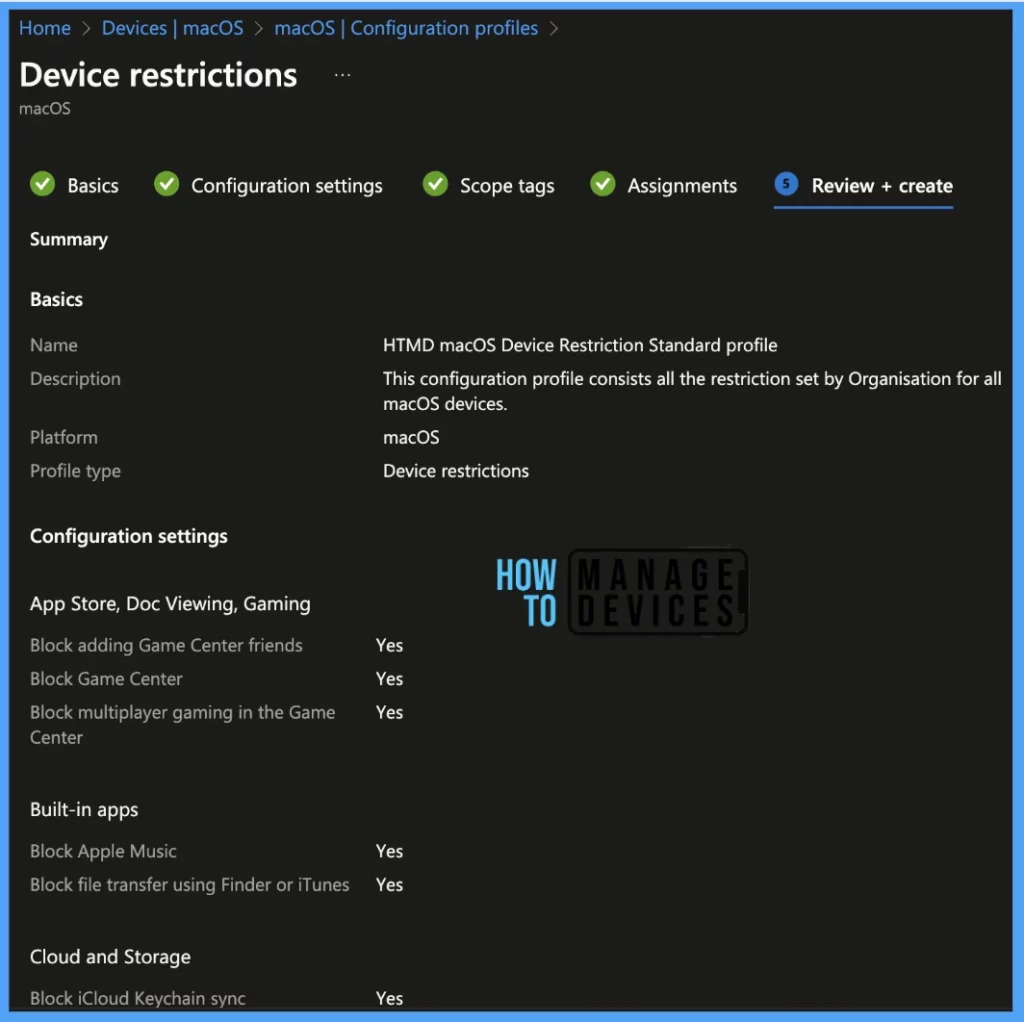
Under App Store, Doc Viewing, and Gaming, there are 3 settings.
- Block adding Game Center friends: This option prevents users from adding friends to Game Center.
- Block Game Center: This disables Game Center and removes the Game Center icon from the Home screen.
- Block multiplayer gaming in the Game Center: This prevents multiplayer gaming when using Game Center.
Note! These settings are applicable only for devices enrolled using automated device enrollment. This includes all supervised devices. And applicable on macOS Version 10.13 or later.
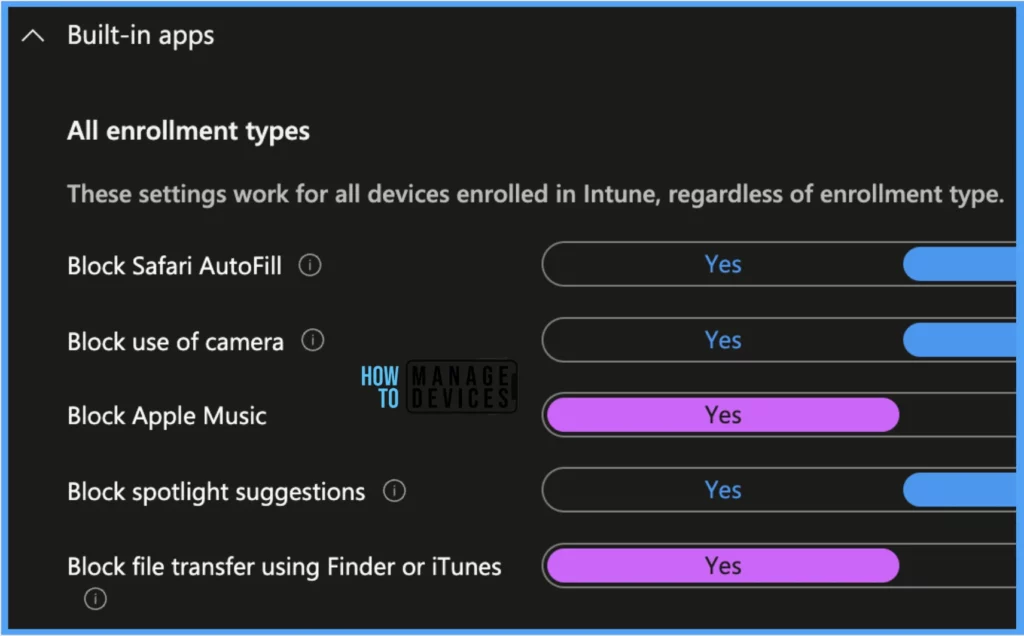
Under Built-in apps, you will able to find below 5 settings.
| Settings | Description |
|---|---|
| Block Safari AutoFill | This option can prevent Safari from storing information entered in web forms by using this option. |
| Block use of camera | This option can block users from taking photographs or videos, if org. doesn’t use the camera at all for Group calls or meetings, can apply this setting. |
| Block Apple Music | This option prevents using the Apple Music app on the device. |
| Block Spotlight suggestions | This option block Spotlight from returning any results from the Internet. |
| Block file transfer using Finder or iTunes | This option blocks files being transferred using iTunes. |
Note! These settings are applicable for all intune-enrolled Mac devices.
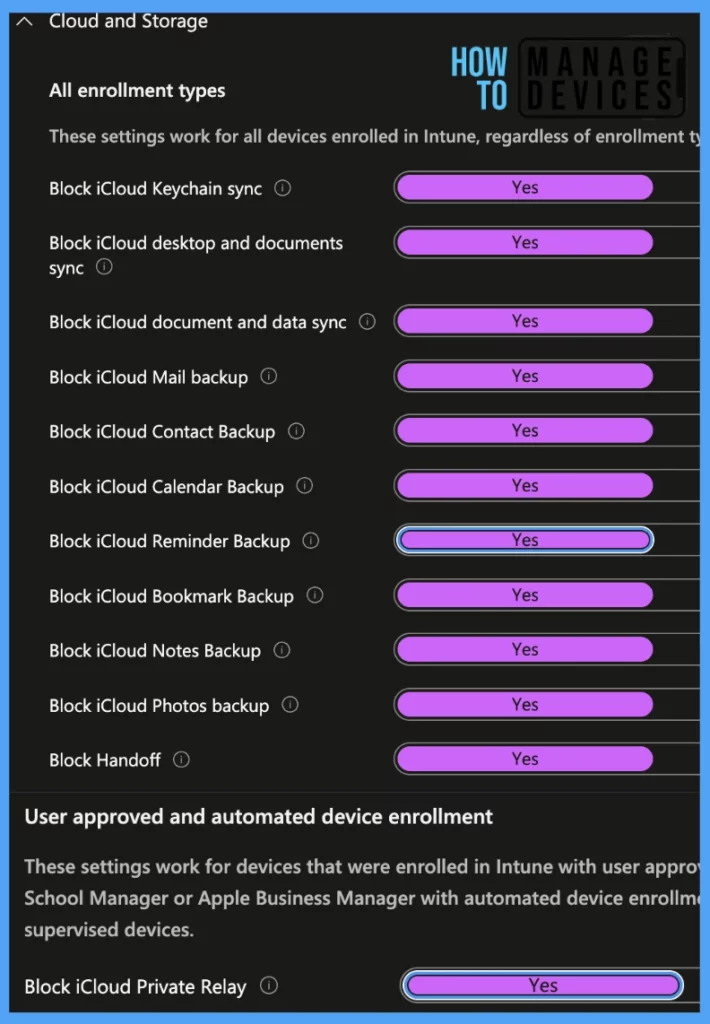
Under Cloud and Storage, there are 12 settings.
- Block iCloud Keychain sync: This option disables syncing credentials stored in the Keychain to iCloud.
- Block iCloud desktop and documents sync: This option blocks iCloud from syncing the Desktop and Documents folders to the cloud.
- Block iCloud document and data sync: This option blocks iCloud from syncing documents and data.
- Block iCloud Mail backup: This option blocks iCloud from syncing mail.
- Block iCloud Contact Backup: This option blocks iCloud from syncing contacts.
- Block iCloud Calendar Backup: This option blocks iCloud from syncing calendars.
- Block iCloud Reminder Backup: This option blocks iCloud from syncing reminders.
- Block iCloud Bookmark Backup: This option blocks iCloud from syncing bookmarks.
- Block iCloud Notes Backup: This option blocks iCloud from syncing notes.
- Block iCloud Photos backup: This setting will block any photos from being backed up to iCloud Photo Library.
- Block Handoff: This option blocks the Apple ecosystem feature that allows users to work on multiple Apple devices ( iPhone,iPad, and Mac), starting work on one device and continuing it on another.
- Block iCloud Private Relay: This option blocks tracking of users’ internet activity and encrypts outgoing traffic. Available for supervised macOS v12 or later devices.
Note! While all the settings are applicable for all intune-enrolled Mac devices, only the Block iCloud Private Relay setting is applicable only for devices enrolled using automated device enrollment supervised devices, and applicable on macOS Version v12 or later.
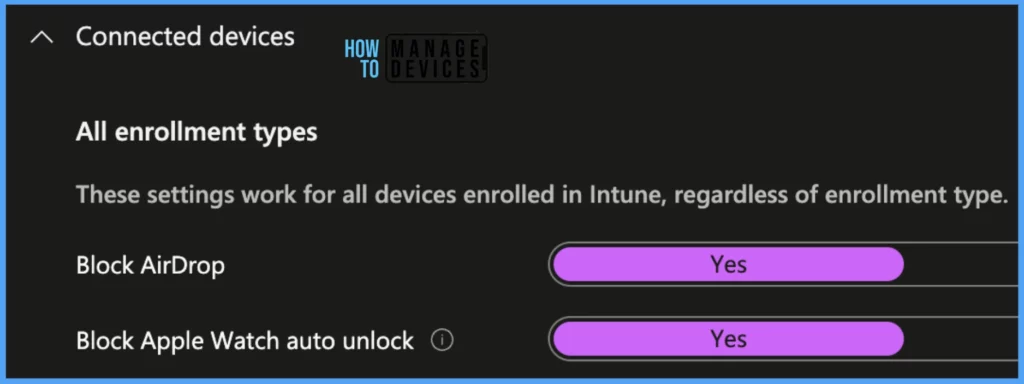
Under Connected Devices, there are 2 settings.
- Block AirDrop: This option usage of AirDrop on Mac devices.
- Block Apple Watch auto unlock: This option blocks users from unlocking their Mac with Apple Watch.
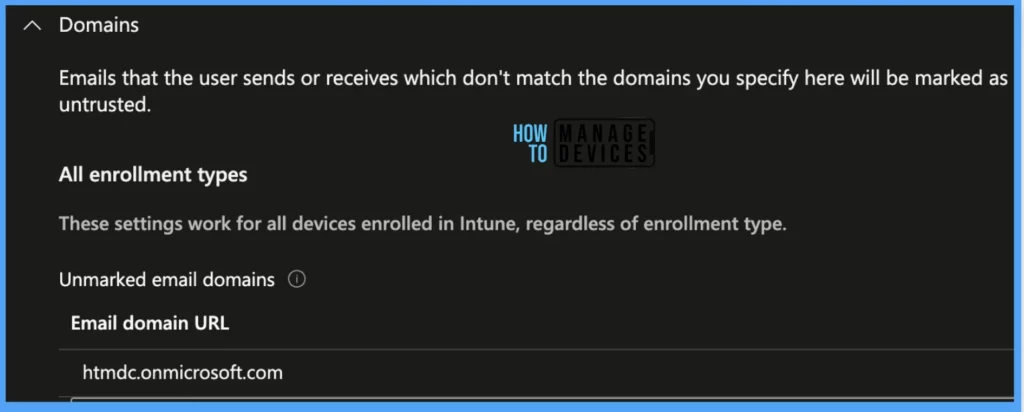
Under Domains, there is 1 setting.
- Unmarked email domains: This option Emails that the user sends or receives which don’t match the domains you specify here will be marked as untrusted.
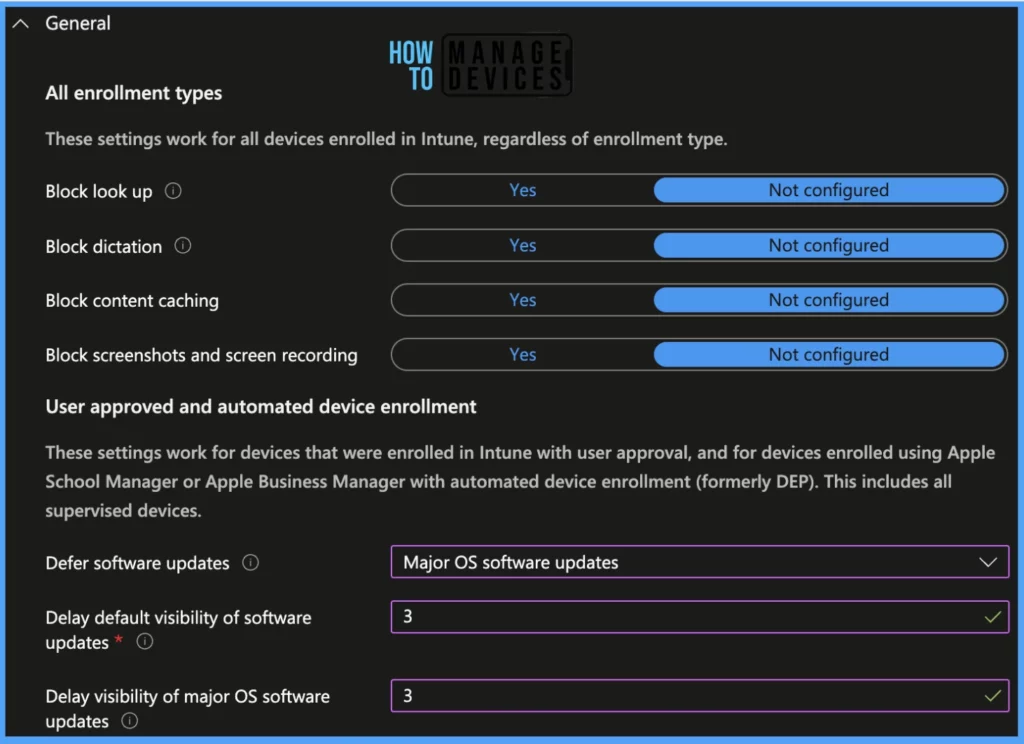
Under General, there are 13 settings.
Note! These settings are applicable for all intune-enrolled Mac devices.
- Block lookup: This option blocks the look-up feature (looks up the definition of a highlighted word) for users.
- Block dictation: This option blocks the dictation feature (converts the user’s voice to text).
- Block content caching: This option will block the content caching feature(This speeds up downloads and saves previously downloaded content on a local device).
- Block screenshots and screen recording: This option will block the user from taking any screenshots on the device or recording screens.
Note! The below setting is applicable for user-approved enrollment and automated device enrollment supervised devices
- Defer software updates: This option will let users allow software updates even if they are unavailable at the time and can upgrade or update the macOS version or latest patches later.
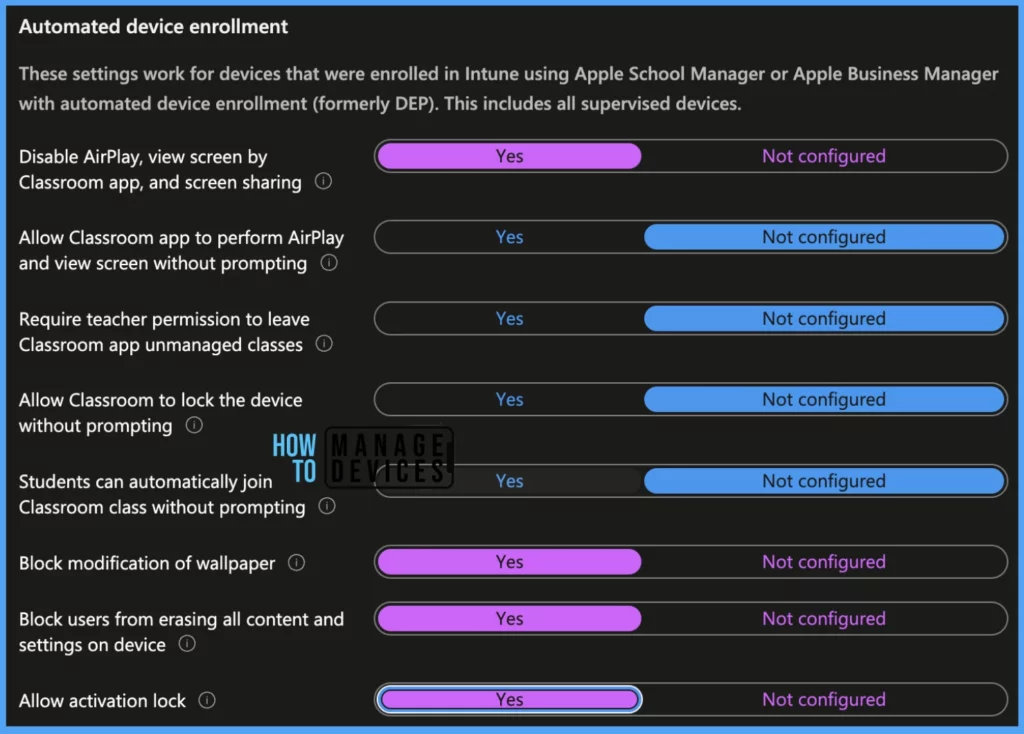
Note! These settings are applicable only for devices enrolled using automated device enrollment.
- Disable AirPlay, view screen by Classroom app, and screen sharing: This option Blocks AirPlay, screen sharing to other devices, and a Classroom app feature used by teachers to view their students’ screens. This setting isn’t available if you’ve blocked screenshots.
- Allow Classroom app to perform AirPlay and view screen without prompting: This option
allow to view screens without warning students. (not available if Block screenshots and screen recording is Yes). - Require teacher permission to leave Classroom app unmanaged classes: This option gives permission to teacher to give consent to Students before leaving the classroom.
- Allow Classroom to lock the device without prompting: This option permits Teachers to lock a student’s device or app without the student’s approval.
- Students can automatically join Classroom class without prompting: This option permits students to join a class without prompting the teacher.
- Block modification of wallpaper: This option prevents users from changing wallpaper for devices running macOS versions 10.13 or later.
- Block users from erasing all content and settings on the device: This setting grey out the reset option on supervised devices for users. ( only for devices running on macOS v12 or later)
- Allow activation lock: This option makes the Activation Lock mandatory which makes it harder for a lost or stolen device to be reactivated by ensuring organisation data to be safe.
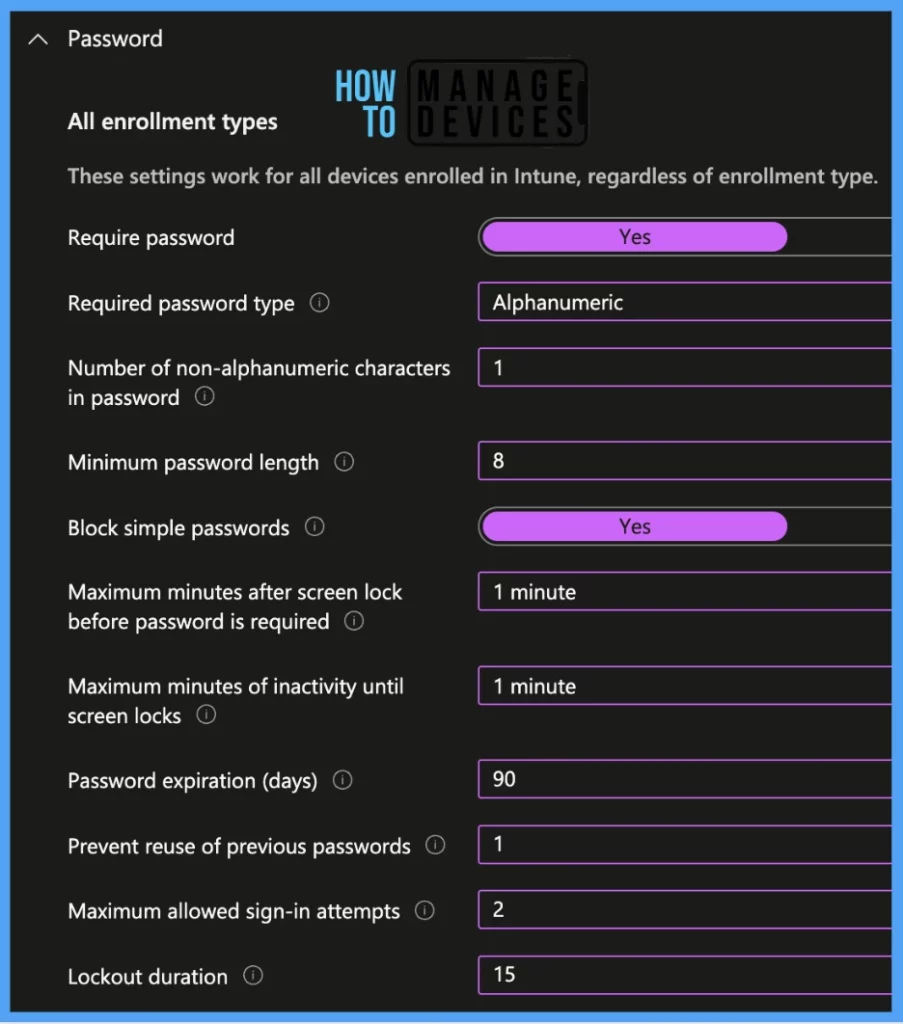
Under Password, there are 17 settings. We will discuss all these settings one by one.
Note! These settings are applicable for all intune-enrolled Mac devices.
| Settings | Description |
|---|---|
| Require Password | This option will make it mandatory for the user to set a password to use a device. |
| Required password type | This option specifies the type of password required (numeric or alphanumeric). |
| Number of non-alphanumeric characters in password | This option specifies the minimum number of non-alphanumeric characters (like #, %, !, etc.) the password must contain. |
| Minimum password length | This option specifies the minimum number of digits or characters in the password. |
| Block simple password | This option blocks simple password usage ( eg., 1234) |
| Maximum minutes after screen lock before password is required | This option specifies the maximum minutes allowed for the user after screen lock before the password is required. |
| Maximum minutes of inactivity until screen locks | This option specifies the maximum minutes of inactivity until screen locks. |
| Password expiration (days) | This option sets the number of days for the password to be changed as a must by the user. |
| Prevent reuse of previous passwords | This option prevents users from using the previous password. |
| Maximum allowed sign-in attempts | This option specifies the maximum number of times that users can try to sign in before their device locks them out. |
| Lockout duration | This option specifies how long the lockout should last. During a device lockout, the sign-in screen becomes inactive so that the user can’t sign in. |
I have used below setings for the configurations. You can choose according to your convinient.
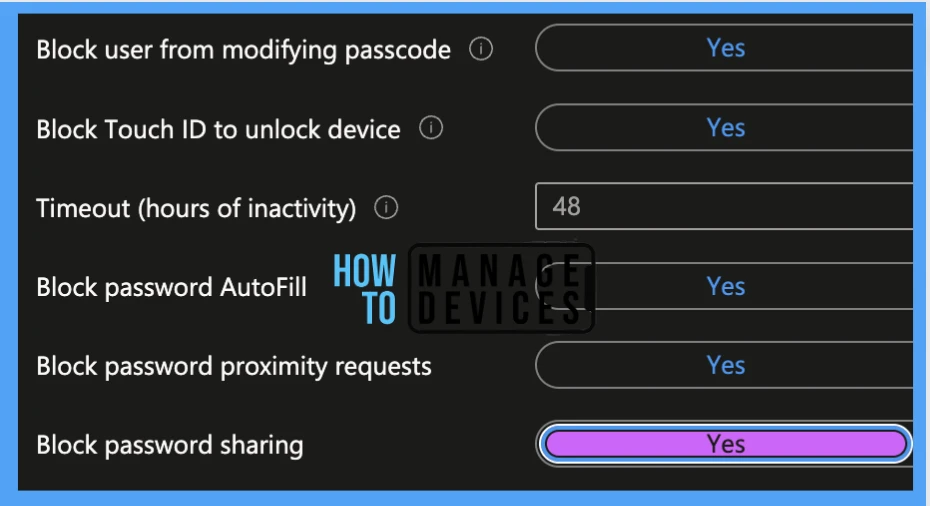
Block user from modifying passcode: This option blocks the user from changing the set numeric passcode.
Block Touch ID to unlock the device: This option blocks the user to set non-biometric passcode ( fingerprint) or password to unlock the device.
Timeout (hours of inactivity): This option specifies the maximum hours after which the user must enter their password to unlock the device instead of using Touch ID.
Block password AutoFill: This option blocks autofill passwords saved in the device.
Block password proximity requests: This option prevents devices from requesting passwords from nearby devices.
Block password sharing: This option prevents sharing passwords between devices using AirDrop.
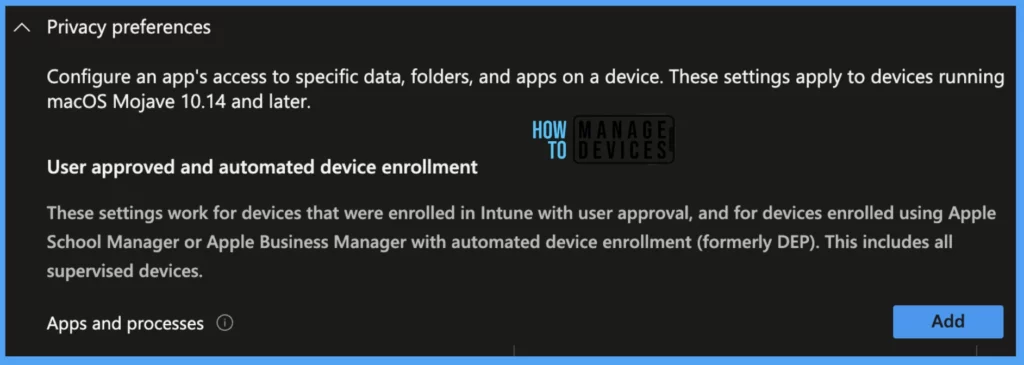
Under Privacy Preferences, there is 1 setting.
- Apps and Processes: This option configures an app’s access to specific data, folders, and apps on a device. These settings apply to devices running macOS v10.14 and later.
Note! These settings are applicable for user-approved and Automated device enrollment devices.
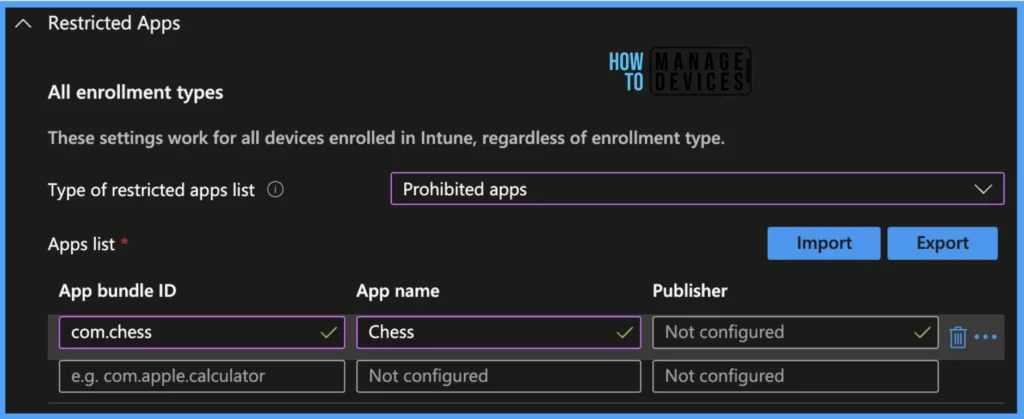
Under Restricted Apps, there is 1 setting.
- Restricted App List: This option specifies the list of apps prohibited from being used in the organisation.
Note! These settings are applicable for all intune-enrolled Mac devices.
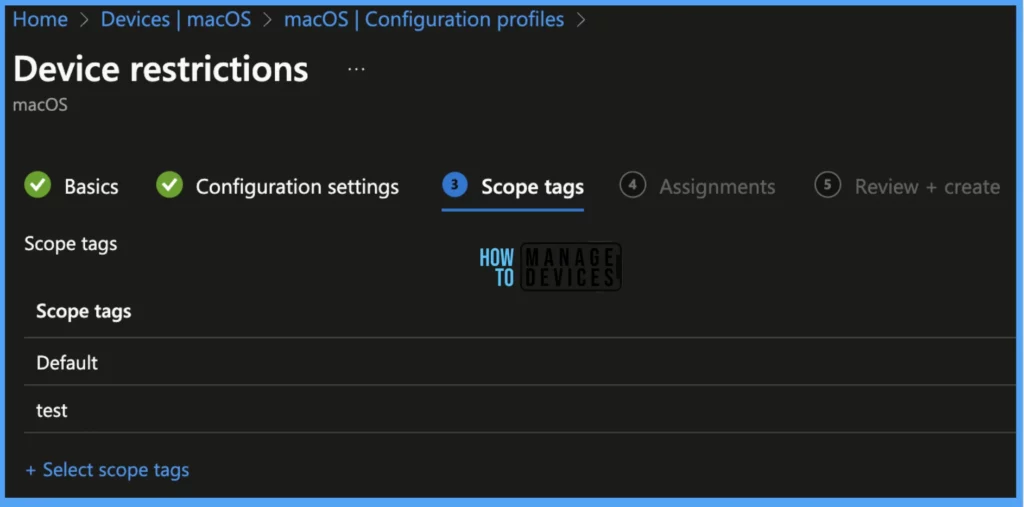
Scope tags are filtering options provided in Intune to ease the admin jobs. In the scope tag section, you will get an option to configure scope tags for the policy. Click on Next.
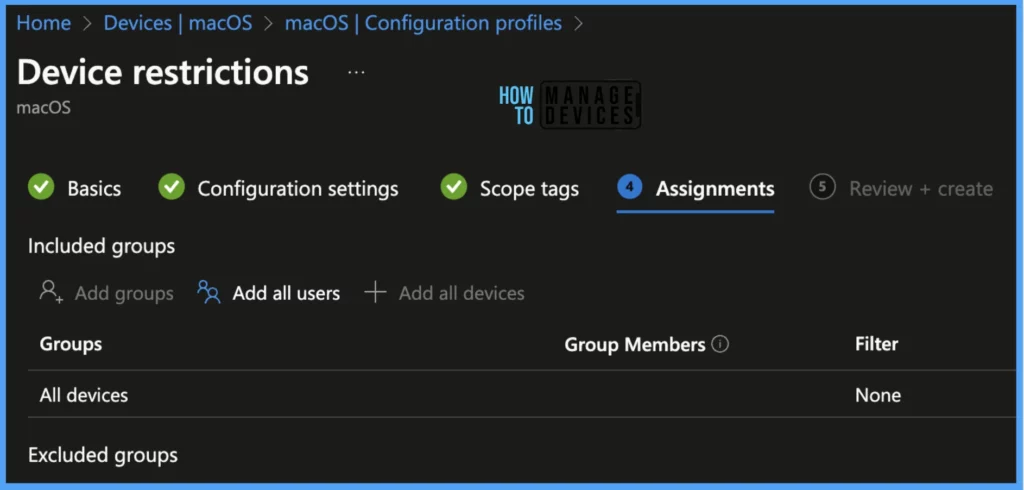
The assignment Group determines who has access to any app, policy, or configuration profile by assigning groups of users to include and exclude. Select Assignments group (Included groups and Excluded groups) and click Next.
On the Review+create page, please review if any settings need to be changed, or else go ahead and click on create button.
Once the Configuration Profile is created, it will take a few minutes to get pushed to the targeted devices in the selected group; also, to view the deployment status on the list of targeted devices, we can check by the below ways.
The report reflects the successful deployment of the block Safari Autofill and file transfer using iTunes policy to macOS devices. To see all the device statuses, Navigate to Devices > Configuration Profiles > Select the Profile, and you can find the list of devices under categories such as below.
- Succeeded
- Error
- Conflict
- Not Applicable
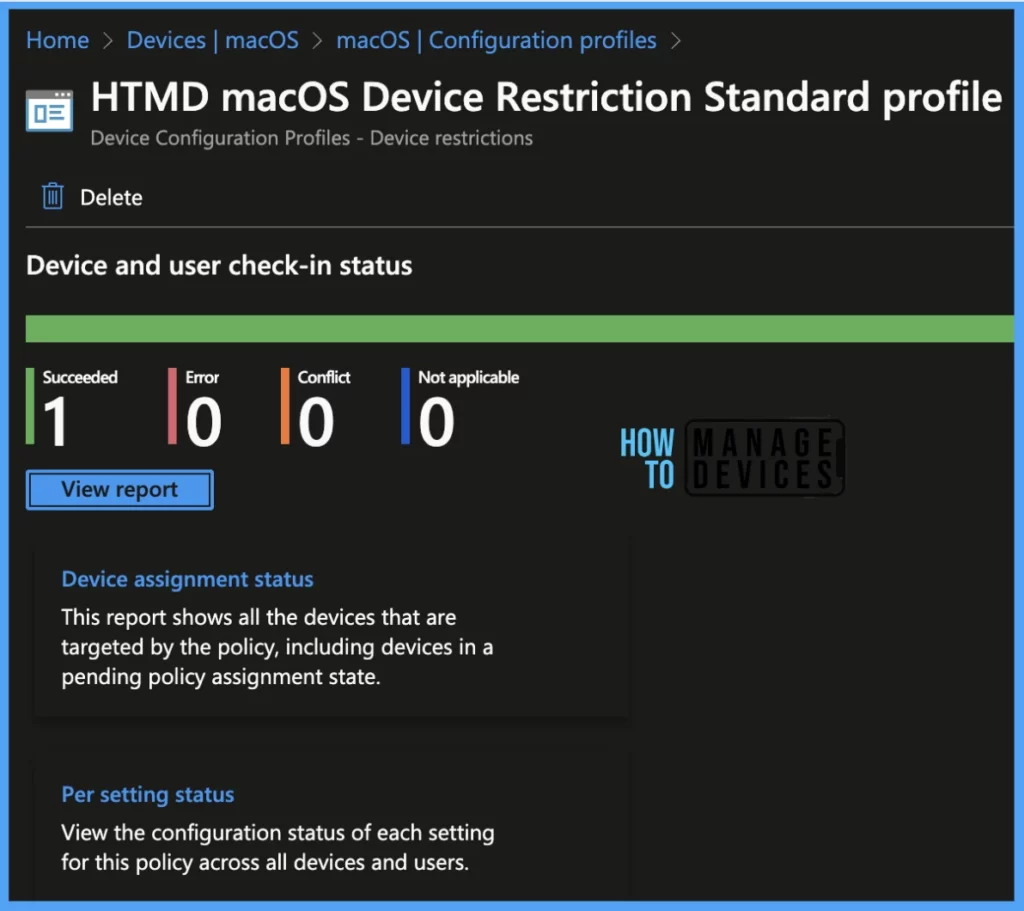
Once you click on the view report button, you can see the list of devices along with their details below :
- Device name
- Logged in User
- Check-in Status
- Last check-in time
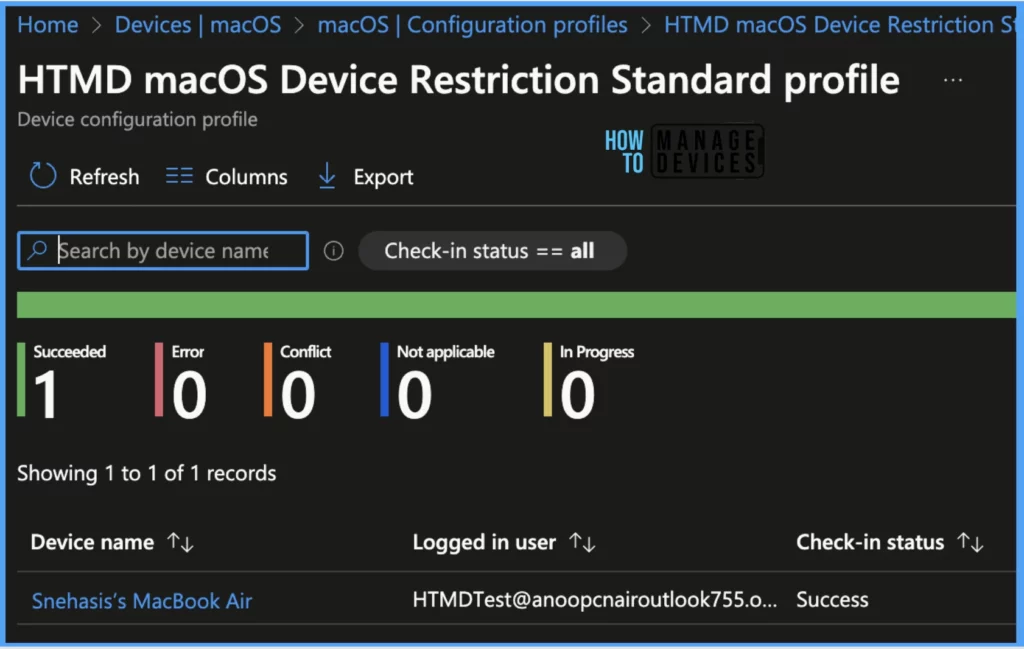
Also, we can view the two different types of reports, you can quickly check the update as devices/users check-in status reports.
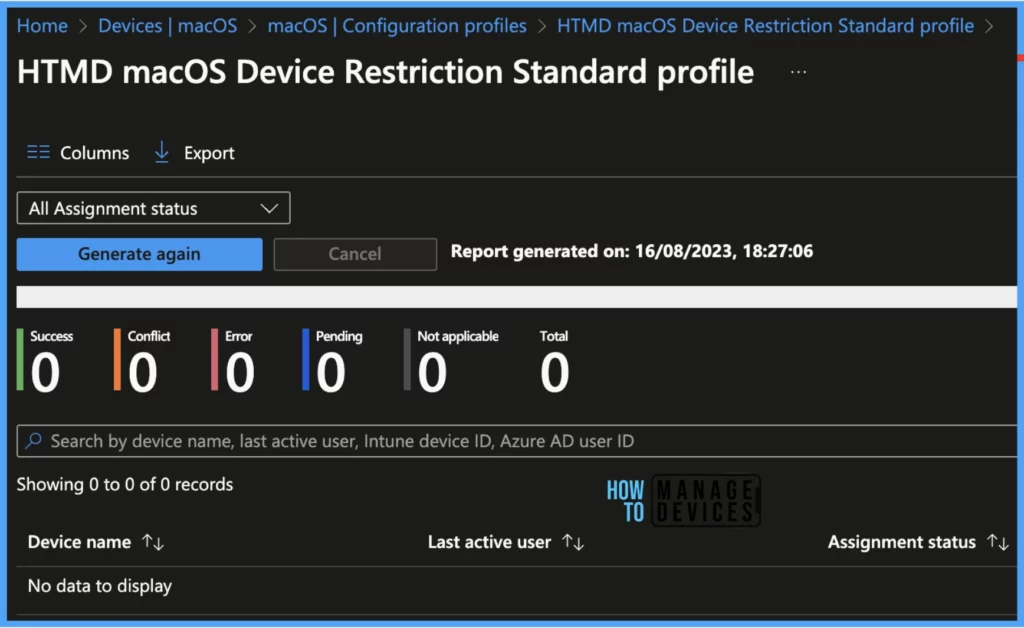
Device assignment status, This report will show the list of targeted devices under the configuration profile, including devices in pending policy assignment status.
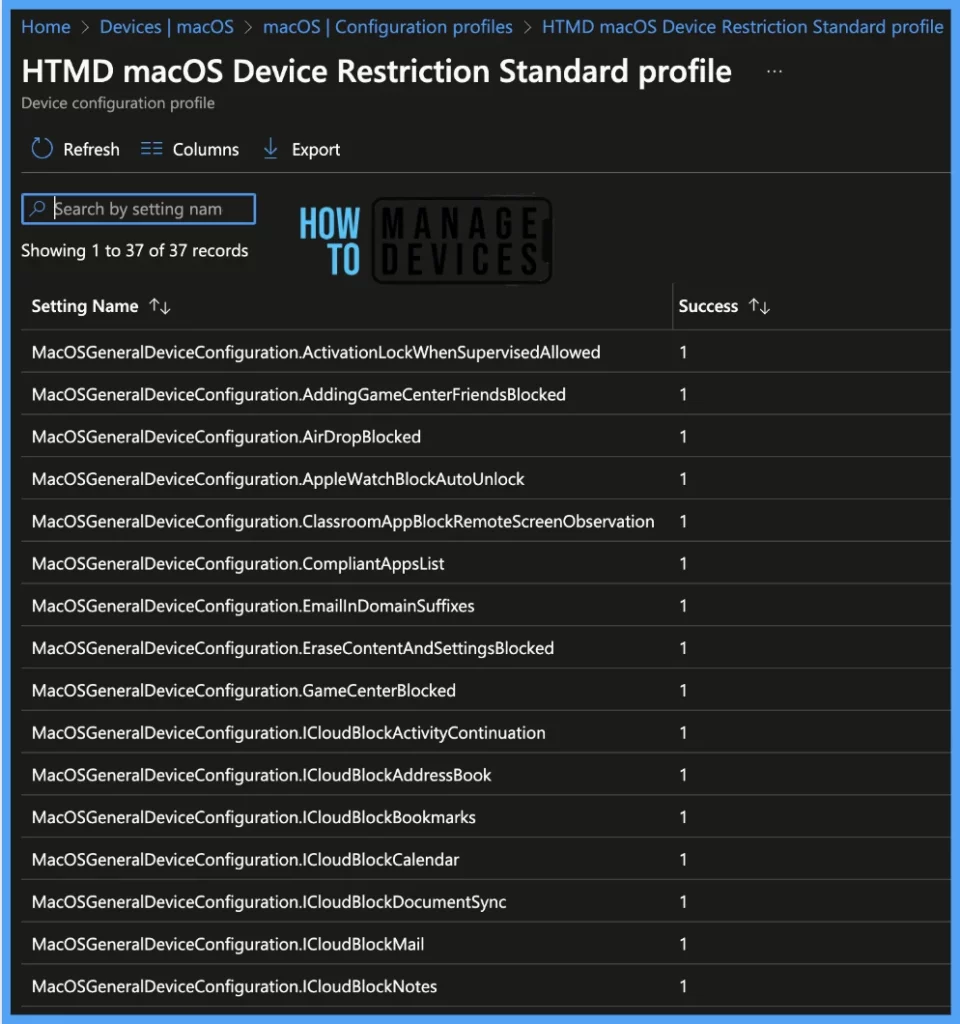
Per settings status, This report will show the configuration status of each set for this policy across all devices and users.
Here’s how you can export Intune setting catalog Profile report from Intune portal. You have two options to navigate to the compliance policies node either you can navigate to the Devices node or Endpoint Security, Intune Settings Catalog Profile Report.
- Enroll macOS in Intune with Step by Step Guide
- Configure macOS Compliance Policy in Intune for Devices
Results – Check Deployed Profile on macOS
Once the Profile gets pushed to the list of client macOS devices as part of the assignment group, it may take a few minutes to reflect on the end user’s device. To check the profile status on the client device, we can follow the below steps.
- Click on the Apple icon at the top-left corner.
- Select System Settings from the list of options.
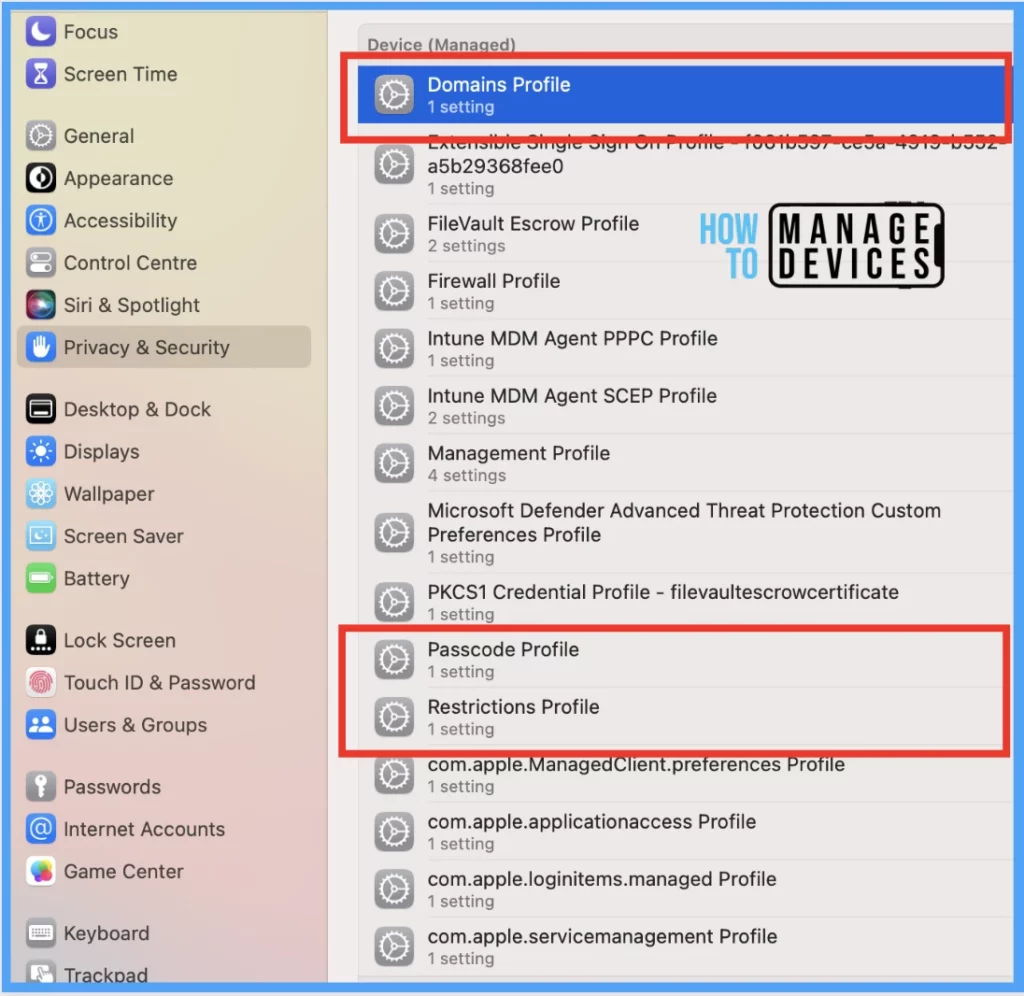
Go to Privacy & Security > Profiles > you can see the number of profiles deployed to the device.
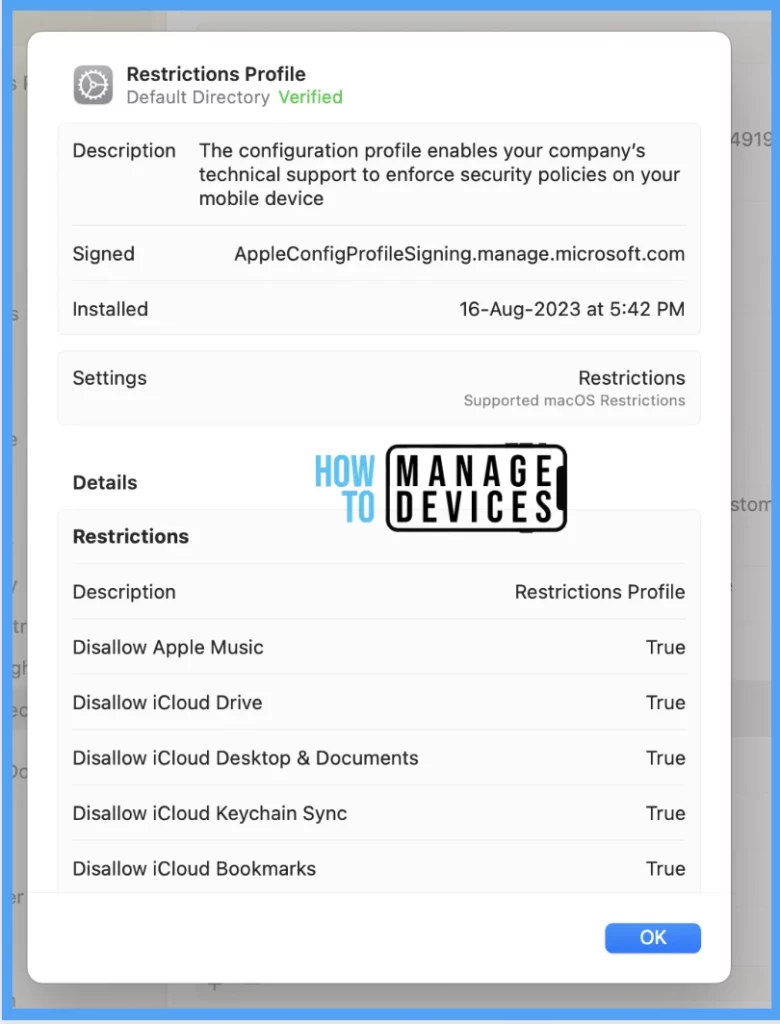
Also, to view the settings/restrictions in a profile, double-click on the Profile and open it to view the details.
Conclusion
As we know, organizations must push device restriction profiles to all the devices that exist in their environment to make them compliant with Organizations’ policies and standards and protect the company’s data and disable the device features usage such as Bluetooth, Public-Wifi or Airdrop, ensuring the data leakage while users to accessing company resources on internal domain sites.
Author
Snehasis Pani is currently working as a JAMF Admin. He loves to help the community by sharing his knowledge on Apple Mac Devices Support. He is an M.Tech graduate in System Engineering.
