Block Untrusted and Unsigned Processes that Run from USB using Attack Surface Reduction Rules! Let’s discover how Attack Surface Reduction aka ASR rules can enhance your organization’s security posture by preventing untrusted or unsigned processes, especially those launched from USB devices from executing on endpoints.
This targeted control helps mitigate risks associated with portable media and strengthens defenses against malware and lateral movement. Microsoft Defender for Endpoint offers a comprehensive suite of capabilities designed to minimize attack surfaces and proactively safeguard your environment and business operation.
Security remains a top priority for every organization, no matter the size or sector. But ensuring that resources managed through Microsoft Intune are truly secure? Well, the answer is NO, It’s never easy to ensure that resources managed through Intune are truly secure.
As Intune administrators, it’s our core responsibility to safeguard every device and user across the enterprise. From enforcing compliance policies to mitigating threats, we play a critical role in maintaining a secure and resilient digital environment.
Table of Contents
What’s Attack Surface Reduction Rules
Attack Surface Reduction (ASR) is a proactive security strategy aimed at minimizing the number of potential entry points that attackers could exploit to compromise a system or network. By identifying and eliminating unnecessary components, software, and access pathways, ASR helps reduce the overall risk exposure and strengthens the organization’s security posture.

This approach includes measures such as disabling unused ports to prevent unauthorized device connections, removing redundant or vulnerable software, enforcing rules that block suspicious behaviors like the execution of unsigned scripts, and restricting access to sensitive system areas. Together, these controls form a robust defense mechanism that enhances endpoint protection and supports a resilient, threat-aware environment.
- Protect Unmanaged Android Devices with Microsoft Defender for Endpoint
- Microsoft Defender ASR Rules to Block Rebooting Machine in Safe Mode
- MDE Microsoft Defender for Endpoint Telemetry Issues
Attack Surface Reduction (ASR) begins by identifying all potential entry points, hardware, software, cloud services, and even human interactions that could be exploited. Once mapped, the attack surface is minimized by disabling unused ports, removing non-essential components, and eliminating redundant software to reduce exposure.
Next, security controls are implemented to block suspicious behaviors. ASR rules can prevent executable files and scripts from downloading or running unauthorized content, stop obfuscated or malicious scripts, and restrict abnormal application behaviors. ASR is not a one-time setup it requires continuous monitoring and refinement to stay ahead of emerging threats and maintain a resilient security posture.
USB Device Hardening with ASR Controls
Blocking untrusted and unsigned processes that run from USB devices is a critical security measure to prevent malware, ransomware, and other malicious payloads from infiltrating corporate networks. USB drives are often used as vectors for attacks because they can bypass network-based defenses and deliver executable content directly to endpoints.
- Block Vulnerable Signed Drivers Using Intune ASR Rules
- Microsoft Cloud LAPS Password Management Solution
- Configure Attack Surface Reduction ASR Rules in Intune
When processes launched from USBs are not validated or signed, they pose a significant risk, especially in environments where users have elevated privileges or access to sensitive data. By enforcing controls that block these processes, organizations can reduce the likelihood of unauthorized code execution, data exfiltration, and lateral movement across systems.
This approach aligns with zero-trust principles and strengthens endpoint resilience against social engineering, insider threats, and supply chain attacks. Integrating this control through solutions like Attack Surface Reduction (ASR) ensures that only trusted, verified processes are allowed to run, protecting both users and infrastructure from avoidable compromise.
Learn More About ASR Control Settings
When configuring Attack Surface Reduction (ASR) rules, you’ll need to select one of the available control settings. The table below provides a clear explanation of each option to help demystify how ASR controls work. Keep in mind that, by default, all ASR rules are set to Not Configured until explicitly defined.
| ASR Settings | Description |
|---|---|
| Not configured | The state in which the ASR rule hasn’t been enabled or has been disabled. The code for this state = 0 |
| Block | The state in which the ASR rule is enabled. The code for this state is 1. |
| Audit | The state in which the ASR rule is evaluated for the effect it would have on the organization or environment if enabled (set to block or warn). The code for this state is 2. |
| Warn | The state in which the ASR rule is enabled and presents a notification to the end-user, but permits the end-user to bypass the block. The code for this state is 6. |
- 32 Privacy Settings for Windows 11 | 99 Intune Privacy Settings Policies
- Security Settings for Windows 11 Hardening options
ASR Rules Dependencies
There are couple of Attack surface reduction rules dependencies that you should keep in mind before you start creating the rule. Microsoft Defender Antivirus must be enabled and configured as primary anti-virus solution, and must be in the following mode:
- Primary antivirus/antimalware solution
- State: Active mode
Also, It’s critical to ensure that Microsoft Defender Antivirus is not operating in any of the following modes. Be sure to follow these configuration dependencies without exception to maintain proper functionality.
- Passive
- Passive Mode with Endpoint detection and response (EDR) in Block Mode
- Limited periodic scanning (LPS)
- Off
Read more : Cloud-delivered protection and Microsoft Defender AntivirusHow to Create an Attack Surface Reduction Rule
Let’s follow the steps to configure Attack Surface Reduction rule in Intune Portal and Block Untrusted and Unsigned Processes that Run from USB. Here are the processes for ASR rules deployment steps using Intune.
- Sign in to the Microsoft Intune Admin Portal with your credentials.
- Select Endpoint security> Attack surface reduction> Create Policy
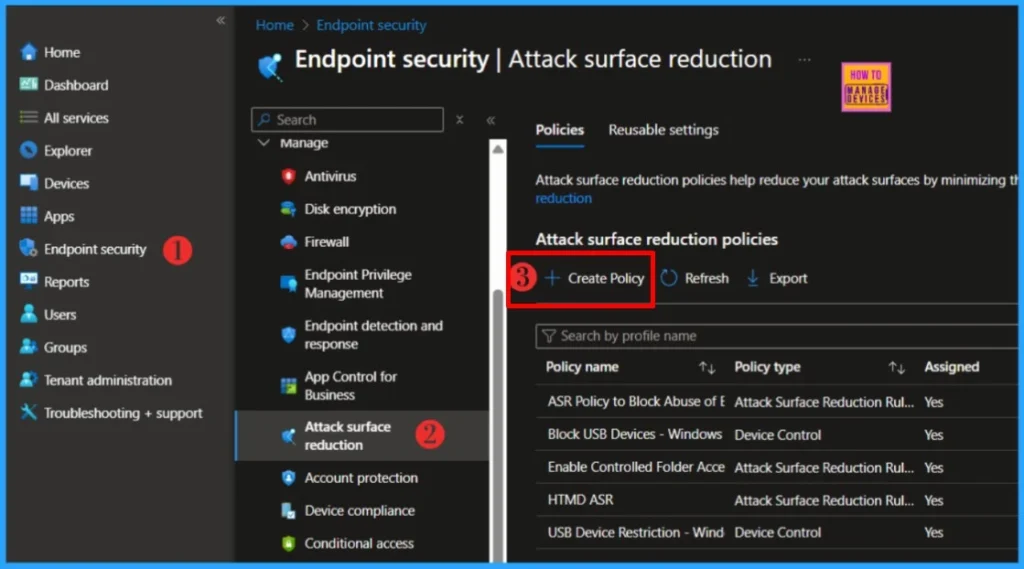
In Create Profile, Select Platform, Windows 10 and later, and Profile, Attack Surface Reduction Rules. Click on Create button to create Attack Surface Reduction Rule.
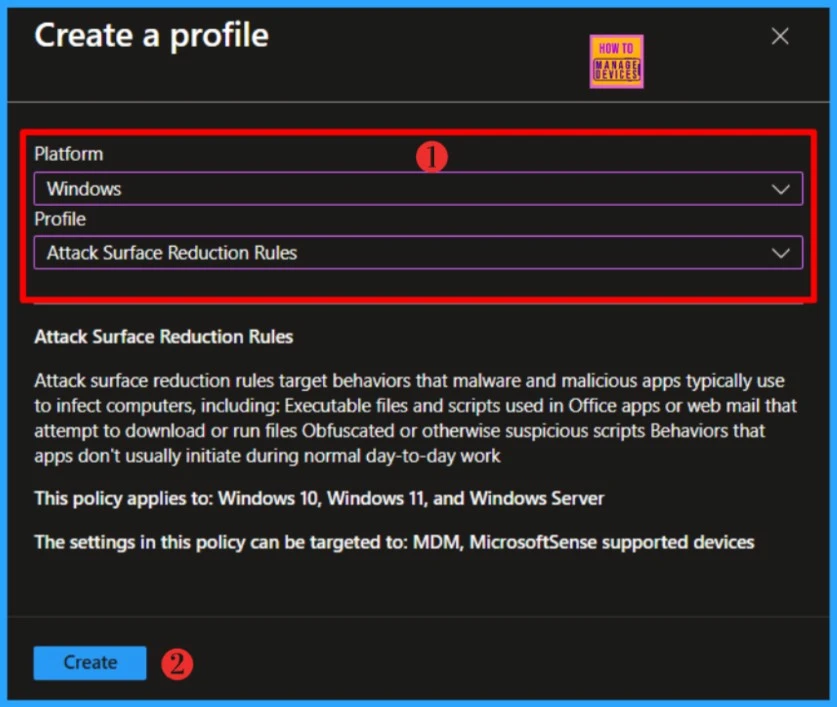
On the Basics tab, enter a descriptive name, such as Block Untrusted and Unsigned Processes that Run from USB. Enter a Description for the policy as well, then select Next.
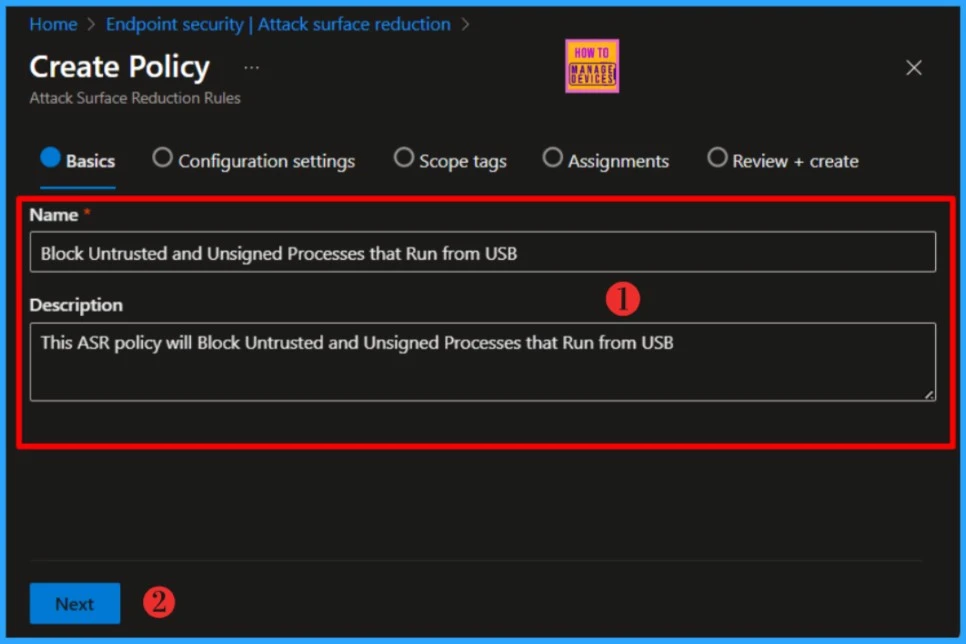
On the Configuration Settings page, review and adjust the required settings, then click Next to proceed. By default, all rules are initially set to Not Configured. Check the above table to learn more about ASR Control Settings.
NOTE: Use audit mode to evaluate how attack surface reduction rules would affect your organization if enabled. Run all rules in audit mode first so you can understand how they affect your line-of-business applications.In this example, I’ll select the Block untrusted and unsigned processes that run from USB rule. This setting allows administrators to prevent the execution of unsigned or untrusted scripts (e.g., VBScript, JavaScript) and executables (such as .exe, .dll, .scr files ) from removable USB devices, including connected SD cards.
The ASR Only Per Rule Exclusions option becomes visible once you set the rule to Block. The “ASR Only Per Rule Exclusions” option allows administrators to define granular exclusions for specific Attack Surface Reduction (ASR) rules, rather than applying exclusions globally across all ASR rules. This is an optional settings.
Instead of disabling an ASR rule entirely, you can exclude specific files, folders, or processes from just one rule. This helps maintain security posture while allowing trusted apps or scripts to function without being blocked. If you enable Per Rule Exclusions for this rule, you can allow specific .exe or .dll files from trusted vendors to run from USB devices, and exclude designated folder paths used by your organization’s deployment tools.
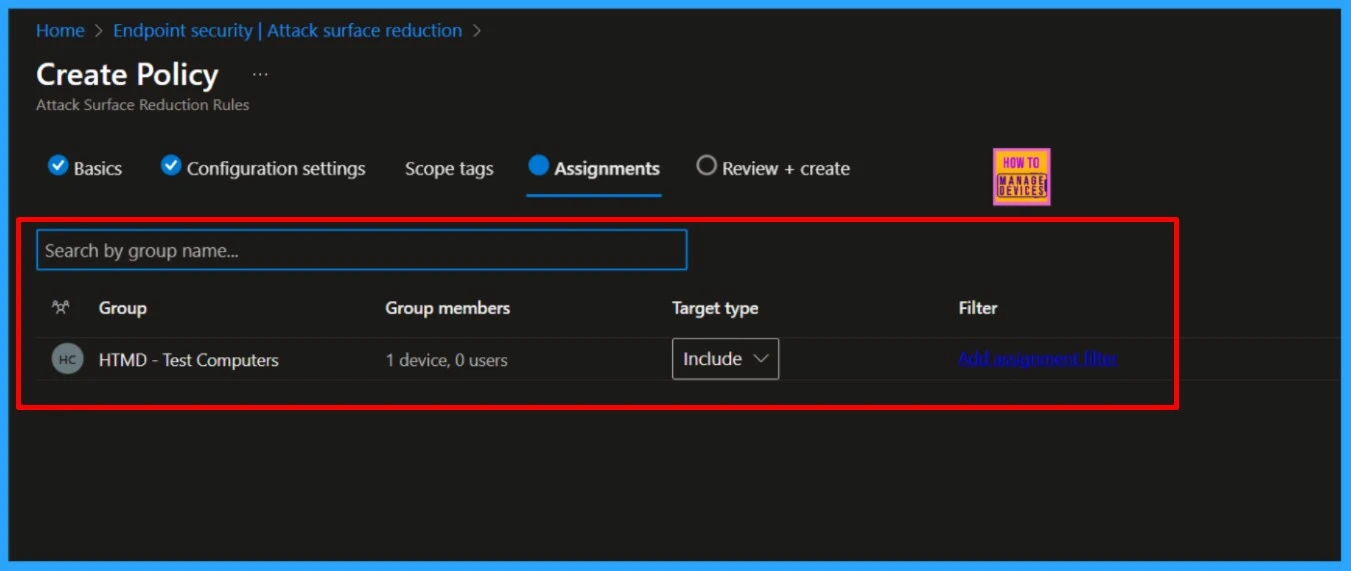
Scope tags are filtering options provided in Intune to ease the admin jobs. In the scope tag section, you will get an option to configure scope tags for the rules. Click on Next. Under Assignments, search for the group that you would to include or exclude and select it . Click on Next to continue.
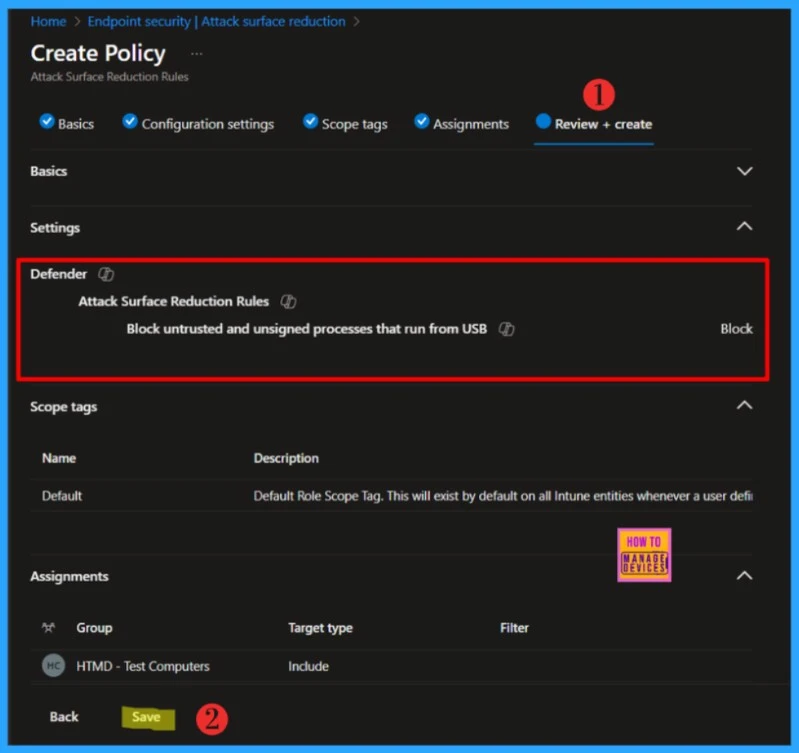
In Review + create, carefully review your settings. When you select Save, your changes are saved, and the profile is assigned.
- Intune Scope Tags Implementation Guide
- Intune Role-Based Administration RBAC
- Intune Read the Only Experience to Create Read-Only Operators
Monitor the Attack Surface Reduction Rule Deployment
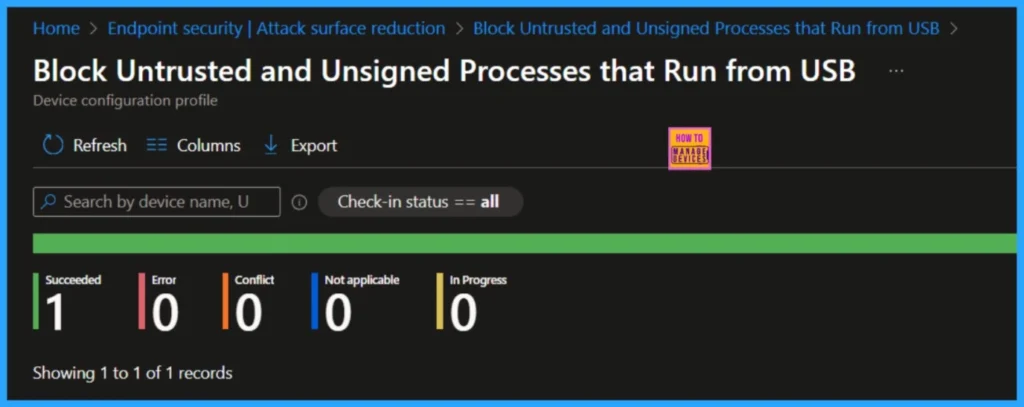
You should have received a pop-up confirming that the Attack Surface Reduction (ASR) rule was created successfully. Let’s now monitor the assignment from the Intune portal. Double-click the rule you just created, then click View Report to review its deployment status.
- Troubleshoot and Fix Devices not Visible in Defender for Business after Intune Onboarding
- How to Install Microsoft Defender Browser Protection Extension using Intune PowerShell Script
Review the Intune Deployment in Windows Event Viewer
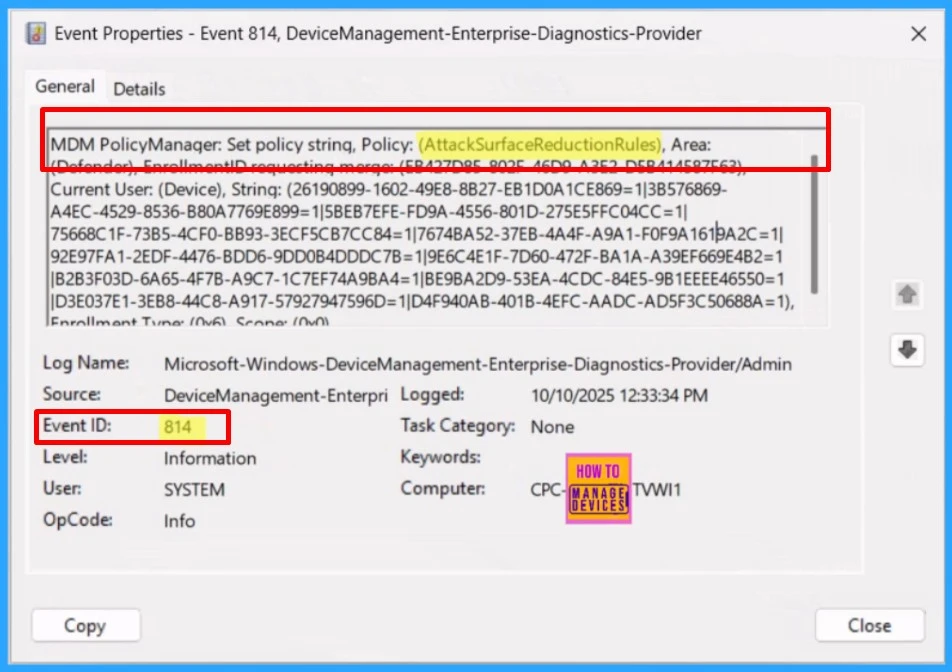
Intune Event ID 814 signifies that a string-based policy has been successfully applied to Windows 10 or Windows 11 devices. This event also provides visibility into the exact value of the policy deployed to each device. Assigned groups will receive the configured profile settings during their next check-in with the Intune service, at which point the policy is enforced on the device.
To confirm this, check the Event log path – Applications and Services Logs – Microsoft – Windows – Devicemanagement-Enterprise-Diagnostics-Provider – Admin.
You can review the Windows Event Log to examine events triggered by Attack Surface Reduction (ASR) rules. These details are available under Event Viewer – Applications and Services Logs – Microsoft – Windows Defender – Operational. The table below provides a reference for key Event IDs and their corresponding descriptions to help you interpret ASR-related activity.
| Event ID | Description |
|---|---|
| 5007 | Event when settings are changed |
| 1121 | Event when rule fires in Block-mode |
| 1122 | Event when rule fires in Audit-mode |
I trust that this article will significantly benefit you and your organization. I appreciate your patience in reading this post. I look forward to seeing you in the next post. Keep supporting the HTMD Community.
Need Further Assistance or Have Technical Questions?
Join the LinkedIn Page and Telegram group to get the latest step-by-step guides and news updates. Join our Meetup Page to participate in User group meetings. Also, Join the WhatsApp Community to get the latest news on Microsoft Technologies. We are there on Reddit as well.
Author
About the Author: Sujin Nelladath, a Microsoft Graph MVP with over 12 years of experience in SCCM device management and Automation solutions, writes and shares his experiences with Microsoft device management technologies, Azure, DevOps and PowerShell automation.


